
Forest was an easy rated Windows machine and was a great opportunity for me to practice attacks I had only read about up until now. The initial foothold was gained by enumerating user accounts then performing an ASREPRoast attack to get a user's hash. The hash was cracked and Evil-WinRM was used to gain a low privilege shell. Bloodhound was used to map out the shortest path to administrator access which involved Microsoft Exchange having higher privileges than needed. These permissions and privileges were used to create a new user with DCSync privileges which enabled dumping the admin hash. This hash is just as good as the password for our uses and yielded an admin shell.
Enumeration
nmap scan:
Nmap scan report for forest.htb (10.10.10.161)
Host is up (0.071s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-19 23:14:28Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Sit
e: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB
)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Sit
e: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
From these results we can see the the domain name is 'htb.local'. The ports make it pretty clear this is a domain controller.
I checked SMB shares first and that was a no-go. Enum4linux yielded some users:

I put the 'normal' looking usernames into a text file:

That pretty much did it for the initial enumeration.
Initial Foothold
I had this excellent article bookmarked and it had a section on ASREPRoast.
"The ASREPRoast attack looks for users without Kerberos pre-authentication required. That means that anyone can send an AS_REQ request to the KDC on behalf of any of those users, and receive an AS_REP message. This last kind of message contains a chunk of data encrypted with the original user key, derived from its password. Then, by using this message, the user password could be cracked offline."
GetNPUsers.py from the Impacket suite was run with the user list:

The user 'svc-alfredo' has UF_DONT_REQUIRE_PREAUTH set and I saved his hash to a file which was easily cracked:

With these creds, Evil-WinRM was used to get a shell:

User flag:

Privilege Escalation
BloodHound has been on my to-learn list for a while and this was a perfect opportunity to give it a whirl. Evil-WinRM was used to upload SharpHound.ps1 to svc-alfresco's download folder. The ps1 file was then imported:

It took a few tries to get the syntax below right:

The zip file was downloaded and imported into BloodHound. Having it show the shortest path to domain admin yielded this:

The graph tells us that svc-alfredo is a member of the 'service accounts' group, which is a member of the 'privileged IT accounts' group, which is in turn a member of the 'account operators' group. The 'account operators' group has GenericAll permissions for 'Exchange Windows Permissions' which has WriteDacl on the domain, which naturally contains the 'administrator' user.
I wasn't exactly sure how to take advantage of all this and googling around lead me to this article on abusing Exchange.
Rather than mess around with the svc-alfredo account, I decided to create a new one since we are part of the 'account operators' group:

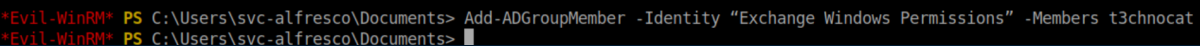
Now to add my new user to the 'Exchange Windows Permissions' group:
Let's set a horrible password:

Finally, enable the account:

Armed with this new account, it's time to run ntlmrelayx:

With ntlmrelayx ready and waiting, the Exchange article linked above uses a 'privexchange.py' script but we can get the same functionality by browsing to http://my attacking machine/privexchange and entering creds:

Shortly after, ntlmrelayx comes to life and does its job:

Now that we have DCSync privileges, we can run secretsdump.py and get a bunch of hashes, including the administrator's hash:

Finally, we can use psexec.py and the admin hash to get a system shell:

Root flag:
