Netmon was an easy and fun Windows machine.
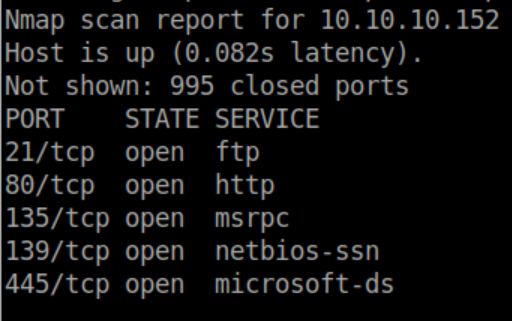
Nmap results:
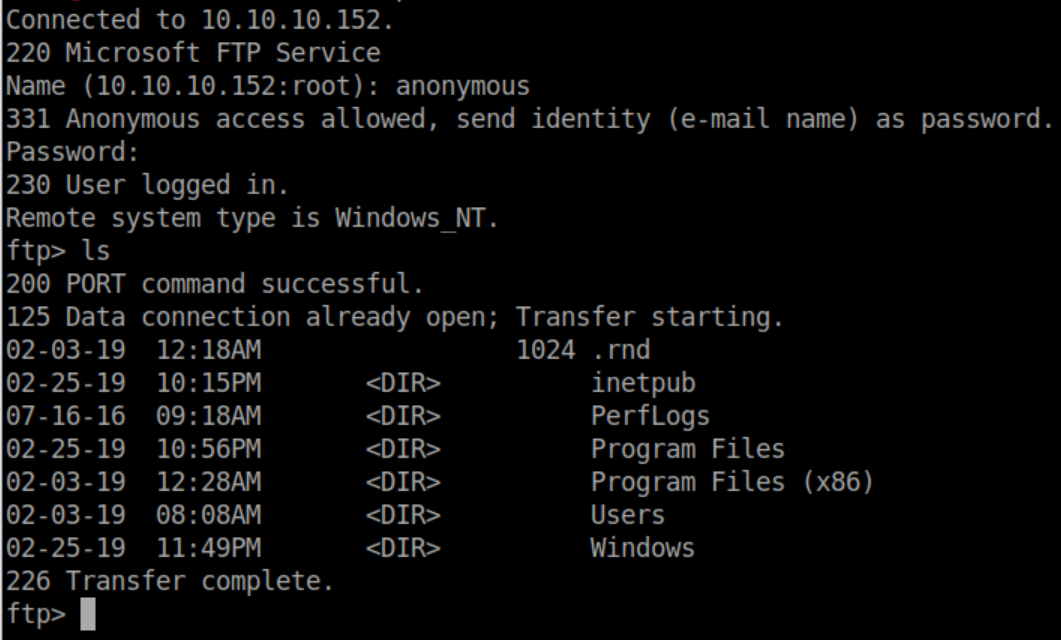
First thing I check is ftp to see if anonymous access is allowed. It is - with full access to the entire C: drive:

In C:\users\public\ we find user.txt:

Transfer it over for the user flag:

I check out http next and find PRTG Network Monitor:

A quick google search comes up with a reddit post detailing how PRTG stores passwords in plain text. Oops.
Using anonymous ftp again which has access to the entire C: drive, I downloaded c:\programdata\paessler\prtg network monitor\prtg configuration.*. Grepped for 'prtgadmin' and found this:

This password did not work on the PRTG website but knowing how lazy users can be, changing it to PrTG@dmin2019 let me in:

Some more googling and I come across a post on a command injection vulnerability in PRTG.
Under Setup, Account Settings, then Notifications:

The program allows you to execute a specified program if a notification is triggered. I selected one of existing objects here:

Scroll down after selecting it and you'll find an option to 'Execute Program'. Enable it and you see this:

That post points out that anything you put in the 'Parameter' field is passed directly to Powershell without any kind of input sanitization so you can do the classic 'exploit' where you give it what it expects, end the command string with a ';' then follow with your code. I used a reverse shell from here (also available in /usr/share/nishang/shells/Invoke-PowershellTcpOneLine.ps1 as part of the default Kali install):

Save the changes and send a test notification. With a netcat listener, a reverse shell is gained:

Root flag:
