While taking the PWK course, I immersed myself in the student labs for many hours a day just hacking away and learning. After passing the exam and finishing my lab time, there was a big hole in my life that the student labs had occupied. I filled up the space with HackTheBox which has been absolutely amazing but I still missed some aspects of the student labs: post-exploitation, pivoting, and multiple networks. A little while ago I came across a post on Reddit looking for people to test a vulnerable CTF (Capture The Flag) network consisting of 25+ machines in multiple networks that was designed to emulate a real life corporate network.

I responded to the poster and after a few emails exchanged, I was sent a VPN connection pack and a link to the information about the lab.
VPN Connection
Just like HackTheBox and the PWK labs, access is granted by using OpenVPN to connect. I never had any issues, everything was fast and stable during the 3 weeks I spent testing.
The Lab
The lab consists of 28 machines spread over 3 networks with operating systems ranging from Windows to different flavors of Linux and Unix. The initial corporate domain is called "Roadhouse" and the entire lab has an 80s theme. Each machine is named after a different 80s movie and in many cases you'll find things fitting the movie's theme as you explore each box.
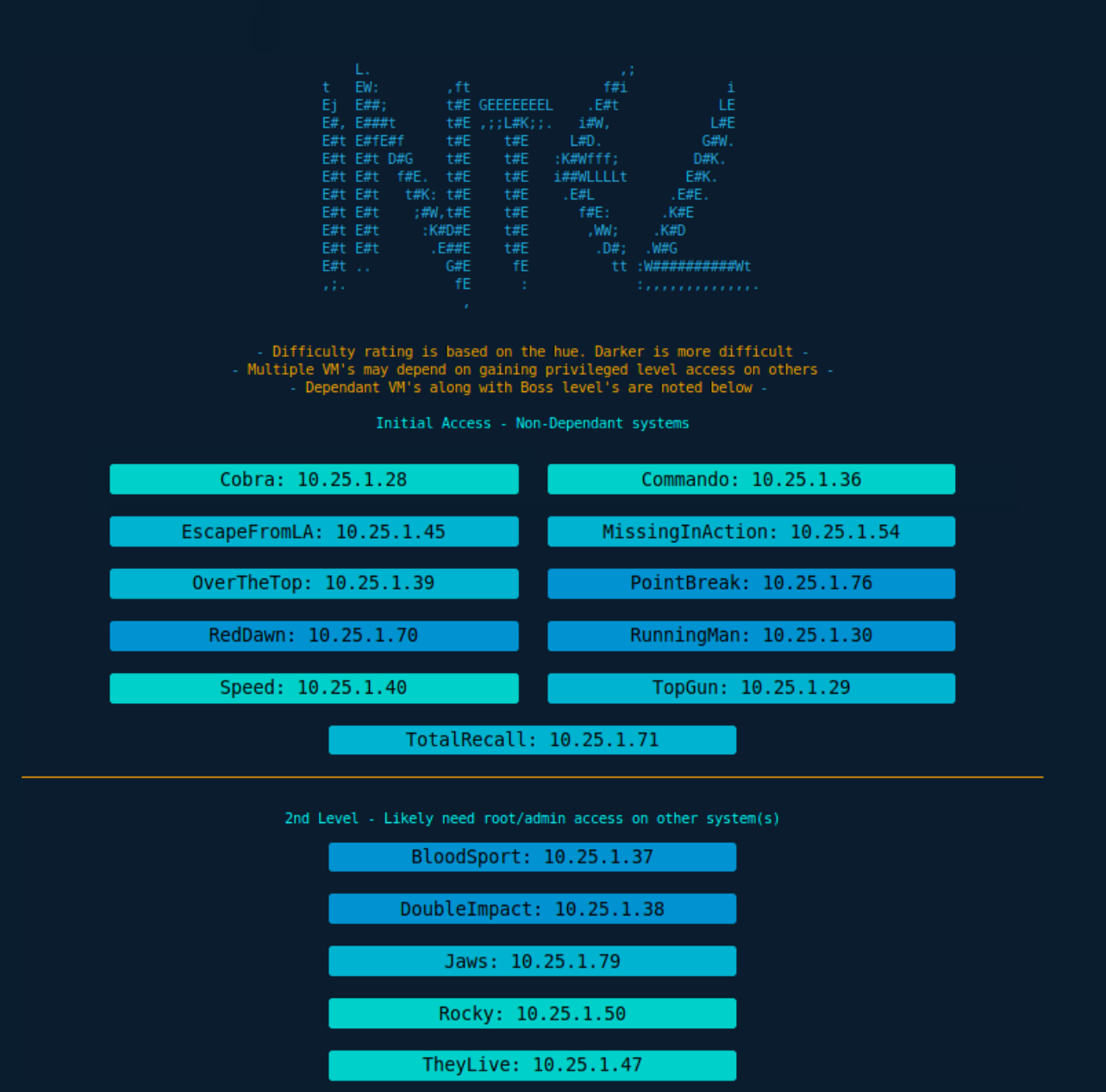
The creator's goal was to avoid it having too many CTF elements. What does this mean exactly? Sometimes in CTF style machines the path forward can involve puzzles or brain teasers. I personally don't enjoy those too much and prefer more real-world scenarios. Slayer Labs hit that goal as there aren't any crazy puzzles to solve, just vulnerabilities and misconfigurations a bad/lazy sysadmin might make. Also, any information you need to find during post-exploitation is in a place that your everyday user might put it.
Like the PWK labs, there are times when you need information from rooting one machine to get a foothold on another. Keeping good notes with everything you've found is critical or you will end up wasting time backtracking.
Difficulty Level
The difficulty level ranges from a handful of very easy ones to some that are a bit on the advanced side. For the easy ones, it's just a matter of finding the correct exploit and firing it off a la script kiddie. The more advanced ones require careful enumeration and an understanding of how the system works. I'd say the most advanced boxes here would be equivalent to the higher-end medium difficulty level on HackTheBox.
Who Should Sign Up?
I think this lab would be an excellent warmup for someone who has some CTF experience but is not sure they are ready for PWK/OSCP. My reasoning:
- There is no lab guide or instructional material included so you need to have some experience with CTF or pentesting to get anywhere.
- It's waaay cheaper than the PWK labs and you can practice pivoting, lateral movement, post-exploitation, and note taking skills affordably.
- When I took the course (this might have changed with their recent course update?), the PWK labs just drop you into the network and tell you 'go after the low hanging fruit first' which can be very overwhelming to a beginner who doesn't know what that low hanging fruit is! You also have no idea which machines need info/credentials from previous ones and it's quite easy to end up in rabbitholes without knowing it. With Slayer Labs, every machine has a difficulty rating and you are told which machines are dependent on having rooted and looted a different box. You won't find this attacking a real network so think of this as training wheels.
- No manual buffer overflows or exploit modifications needed, both of which can be difficult or intimidating to beginners. I know I had a hard time learning bufffer overflows.
- The difficulty level has a nice ramp up and completing the lab should give you a nice confidence boost to tackle the PWK/OSCP course. You'll get a chance to exploit some very well known vulnerabilities as well as common misconfigurations in both Linux and Windows. You will also spend some time evading and cursing at Windows Defender.
Requirements
In no particular order, some of the things I think you'll need to know to complete the labs:
- Intermediate Linux and Windows skills
- Intermediate networking knowledge and a basic understanding of pivoting
- How to use a web proxy like Burp or OWASP ZAP
- Good Google-Fu
- Basic PowerShell
- Common web application vulnerabilities
Conclusion
I had a blast testing out this lab. There are multiple paths to the end and a beautiful job was done of weaving hints, machines and the entire network together - I highly recommend taking the time to explore the entire lab instead of just rushing to the end.
In case it needs to be said - I did not get paid for this review. I truly enjoyed testing the lab out and think it's a great resource for anyone looking to learn or practice hacking in a multi-network environment. As of this writing, the cost is $19 for two weeks or $34 for 30 days of access - roughly 10% the cost of the PWK labs for a month.
Just because I can, click on Peter Griffin to check out Slayer Labs for yourself.
